** 本記事は、Keeping it real: Sophos and the 2024 MITRE ATT&CK Evaluations: Enterprise の翻訳です。最新の情報は英語記事をご覧ください。**
毎年、ソフォスを含む複数のセキュリティソリューションプロバイダーが MITRE の ATT&CK Evaluations: Enterpriseに参加しています。この評価は、実際の攻撃者とその戦術、ツール、手順に基づいて、1 つまたは複数のシナリオをカバーする本格的なサイバー攻撃のエミュレーションです。
この評価は初期アクセス、常駐化、ラテラルムーブメント、影響などエンドツーエンドの攻撃チェーンに基づき、セキュリティソリューションの性能を現実的かつ高い透明性で評価するように設計されています (結果は一般公開されています)。エミュレーションには通常、エンドポイント、サーバー、ドメインに接続されたデバイス、Active Directory で管理されたユーザーを含むマルチデバイスの「顧客」環境が用いられます。
2024 年は、ソフォスの 4 年目の参加年となりました。その記念として、今年の評価がどのような内容であったのか、また評価が実際にどの程度実際の攻撃に忠実だったのかをご紹介します。特に、ツールのリアルさ、テスト手法の詳細、ソフォスの保護および検出機能については詳述します。各シナリオには 20~40 のステップがあるため、すべてを網羅することはできませんが、エミュレーションの奥深さと正確さを浮き彫りにしながら、その一部をご紹介します。
2024 年の脅威カテゴリ
2024 年の評価では、MITRE はランサムウェアおよび朝鮮民主主義人民共和国 (北朝鮮) という 2 つの脅威カテゴリを選択しました。前者は、以前からそうであったように、業界最大のサイバーセキュリティ脅威の一つであり、進化し続けています (リモート暗号化の増加など)。後者も、この地域に関連する国家主導でのスパイ攻撃の拡散を考えると、非常に関連性が高くなっています。
MITRE はこれらのカテゴリを中心に 3 つのシナリオを構築しました。MacOS に焦点を当てた北朝鮮系の攻撃者による攻撃 (攻撃者が複数のキャンペーンで MacOS を標的にしていることに基づくもので、この傾向は今後も続きそうです)、および 2 組のランサムウェアグループ (Cl0p と LockBit) のアフィリエイトによる攻撃です。
DPRK
北朝鮮のシナリオは、JumpCloud のサプライチェーン侵害の流れに基づいた、単純かつ現実的なものでした。攻撃者がデバイスを侵害し、常駐化エージェントを確立し、認証情報を窃取します。北朝鮮と関連のある攻撃者は、攻撃を個別の段階に分け、将来的に攻撃を開始するためのバックドアを維持することで知られています。
初期アクセス
この評価はサプライチェーン攻撃を想定していますが、シナリオ自体は、ユーザーが悪意のある Ruby スクリプトをダウンロードして実行するというものです (ソフォスの分析では、Ruby のユーザー実行経路が示されています) 。現実のサプライチェーン攻撃では、プリインストールされたソフトウェアが自動的にスクリプトを実行する可能性が高いと考えられます。とはいえ、このアプローチはもっともらしく、意味があるものです。最近の事例が示しているように、北朝鮮系の攻撃者はソーシャルエンジニアリングを使ってユーザーにスクリプトを実行するように仕向けます。
JumpCloud 攻撃と同様に、MITRE の Ruby スクリプト (実際のスクリプトの名前である init.rb になぞらえて start.rb と名付けられています) は Docker 関連コンポーネントを装い、第一段階の C2 エージェント (Mach-O バイナリ) をダウンロードして実行します。本物の JumpCloud サンプルをリバースエンジニアリングすることは不可能であり、ソフォスの知る限り、実際のサンプルは公開されていません。他のすべての MITRE ATT&CK 評価と同様に、使用されたマルウェアは評価のためにカスタムビルドされたものです。
常駐化
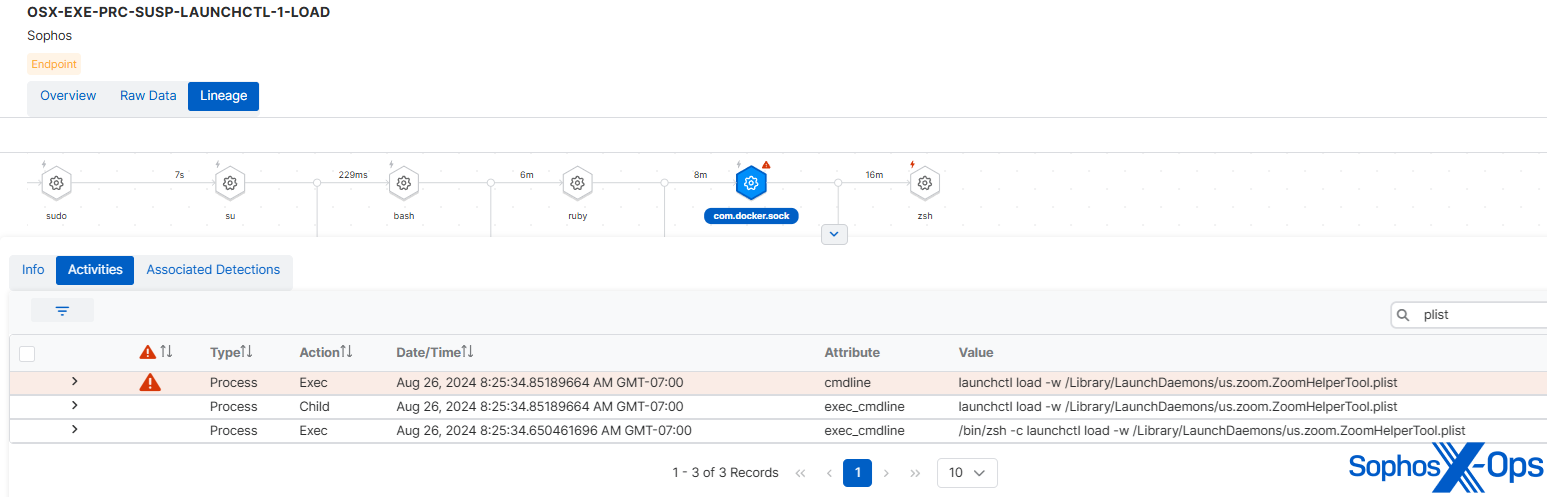
第一段階の C2 エージェントは、次に第二段階のバックドア (実際の JumpCloud 攻撃では「STRATOFEAR」として知られています) をダウンロードし、LaunchDaemons (/Library/LaunchDaemons/us.zoom.ZoomHelperTool.plist) を用いて本物と同じ方法で常駐化を確立しました。
図 1: ZoomHelperTool.plist による常駐化
初期アクセス段階の Ruby スクリプトと同様に、MITRE は本物を忠実にエミュレートするようにバックドアを設計しました。バックドアは本物と同じ場所 (/Library/Fonts) にドロップされ、非常によく似た名前がつけられていました (実際のバージョンが ArialUnicode.ttf.md5 という名前なのに対し、評価に用いられたバージョンは pingfang.ttf.md5 という名前でした。「Arial」と「pingfang」はのどちらも一般的なフォント名です)。
実際の JumpCloud 攻撃と同様、「攻撃者」はステルスかつ回避的に、システムから第一段階のインプラントファイルを非常に迅速に削除しました。エミュレーションでは、実行パスの分析結果と同様に、rm -f <ファイル名> コマンドが用いられました。このコマンドが JumpCloud グループによって使用された方法であったかどうかは不明ですが (プロセスの実行がログに記録される可能性が高いため、直接 API を使用する方法よりもノイズが多くなります)、前述の通り実際のサンプルが入手できないため、確認できません。
本物の STRATOFEAR と同様に、MITRE のバックドアも暗号化された構成ファイルを使用し、シェルアウトの openssl enc -d コマンドとハードコードされたパスワードを使用していました。くり返しになりますが、直接 API ベースの方法を使用する方がよりステルス性が高くなることは確実な一方で、JumpCloud の攻撃者が実際にそのようなアプローチを採用したかどうかは不明です。
テストの安全性についてのメモ: MITRE の C2 インフラストラクチャでは、テスト環境の範囲内で機能するドメインが使用されていますが、このドメインは DNS で一般に解決できるものではありません。ただし、パブリック IP アドレスには解決されます。つまり、ネットワークトラフィックは本物の C2 活動のように見えますが、ドメインはテスト環境の外からは到達できません。
影響
JumpCloud 攻撃と同様に、攻撃者の目的はシステム情報、認証情報、キーチェーンに保持されている機密情報などのデータを収集することです。MITRE の STRATOFEAR 再現バックドアは、窃取を実行するために C2 サーバーから追加モジュールをダウンロードして実行するという点で、オリジナルに忠実でした。本物の STRATOFEAR によってダウンロードされたモジュールと同様に、これらは /tmp ディレクトリの .tmp ファイルに書き込まれ、それぞれ 6 つのランダムな英数字からなる文字列を用いて命名されました。
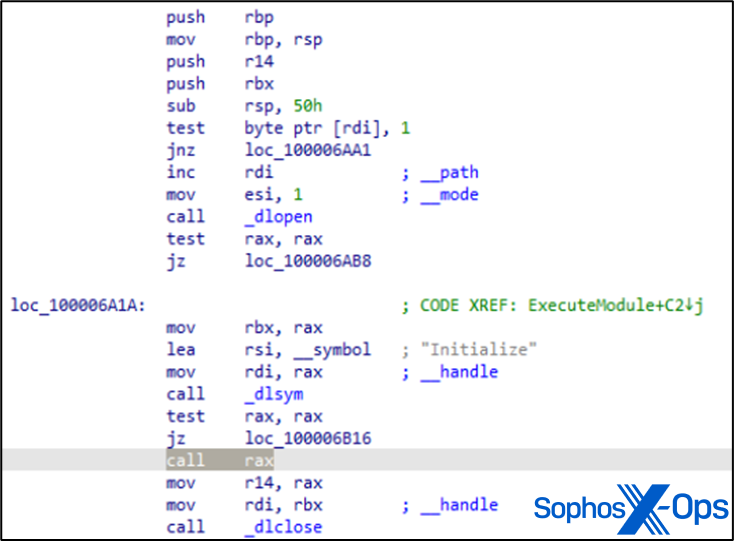
今回の評価では、MITRE の STRATOFEAR は MacOS のキーチェーンファイルを読み取る機能を持つモジュールである /private/tmp/rhkA2f.tmp をダウンロードしました。
図 2: MITRE の STRATOFEAR サンプルの ExecuteModule 関数。dlopen/dlsym を使って「Initialize」関数を呼び出しています。
このシナリオの最後では、バックドアがデータを収集しました。今回の評価では、実際のデータ窃取は行っていません。認証情報の多くは流出した場合にのみ有用であるため、この評価手法には問題があるとの指摘もありますが、ソフォスは些細な問題だと主張します。インシデント対応者として認証情報の窃取を観測できれば、潜在的な影響と関連する悪意のある活動を認識できるためです。
Cl0p
2 つ目のシナリオでは、活発な攻撃者である Cl0p ランサムウェアグループ (別名 TA505) による攻撃がエミュレートされました。このシナリオには、ダウンローダー、常駐 RAT、高度なプロセスインジェクション、信頼のあるプロセスの悪用が含まれ、最終的にランサムウェアのペイロードが実行されるという 2019 年の一般的なインシデントの流れを (ほとんどの部分で) 忠実に模倣していました。
初期アクセス
シナリオの大部分は 2019 年の実際の攻撃キャンペーンに忠実でしたが、初期アクセス段階はわずかに異なっていました。2019 年と同様に、攻撃者は DLL を使用して常駐 RAT をインストールしました。しかし、実際の攻撃では、埋め込まれた DLL を含む悪意のある Office ドキュメントが Office プロセスに動的にロードされたのに対し、MITRE のシナリオではユーザーが対話的に cmd.exe を実行し、rundll32.exe を介して DLL を実行しました。
この DLL は、RDP 経由での初期アクセスの後、別の対話型 cmd.exe から curl コマンド経由でダウンロードされ (このステップはシナリオに含まれていません)、ホスト上に既に存在していました。このような初期アクセス方法は、特に初期アクセスブローカー (IAB) を介して盗まれた認証情報やアクセス権を購入したランサムウェアグループやその他の攻撃者の間で非常に一般的であることは注目に値します。しかし、非常に特徴的な事例では、Cl0p は MOVEit ファイル転送アプリケーションのゼロデイ脆弱性 (CVE-2023-34362) も悪用していました。
攻撃者が侵害されたホストに直接リモートアクセスすることも非常に現実に即しています。さらに、このシナリオではおそらく、より完全なエミュレーションのための DLL ツールの侵入も実行されました。
常駐
2019 年のキャンペーンと同様に、MITRE の「攻撃者」は「VerifierDLL」キーを使用した Image File Execution Options (IFEO) インジェクションを使用して信頼ある winlogon.exe プロセスを侵害することで、常駐的な RAT SDBbot をロードしました。
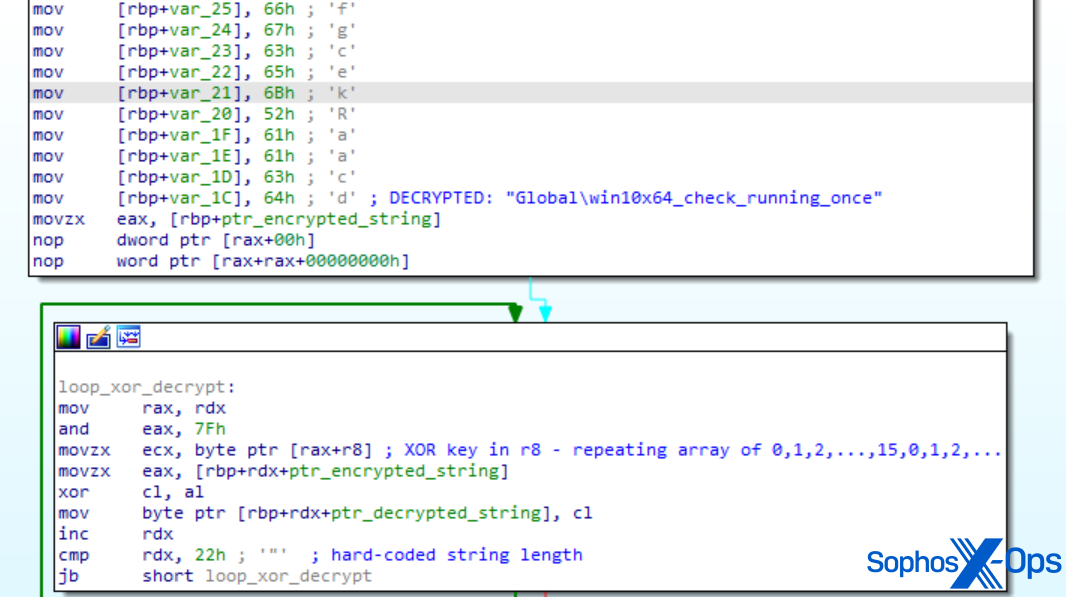
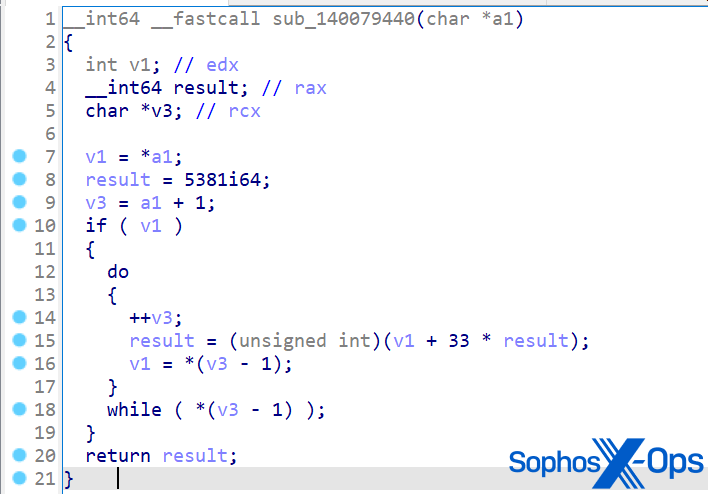
SDBbot は、暗号化された文字列とミューテックスを使用して起動を保護します。北朝鮮のシナリオと同様に、MITRE のサンプルは実際のミューテックスに類似しているものの異なる名前 (実際の攻撃では windows_7_windows_10_check_running_once_mutex、評価では win10x64_check_running_once) を使用しています。
図 3: MITRE の SDBbot サンプルの逆アセンブル。ミューテックス名と復号関数に注意してください。
MITRE の SDBbot の実装では、鍵は 0 から 15 までの同じ 16 バイトのくり返しです。この実装は完全にランダムな 128 バイト文字列ほど安全ではありませんが、API 名とデータフィールドを参照するための文字列を、単純な静的解析方法に対抗して難読化するには十分です。MITRE は Cl0p シナリオおよび後述する LockBit シナリオでこの文字列難読化方法を使用しました。
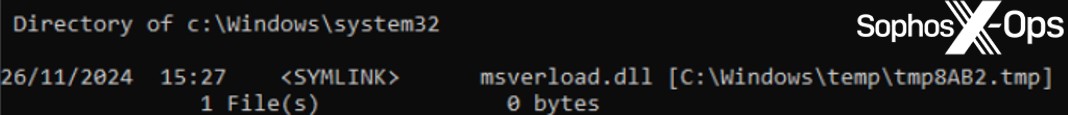
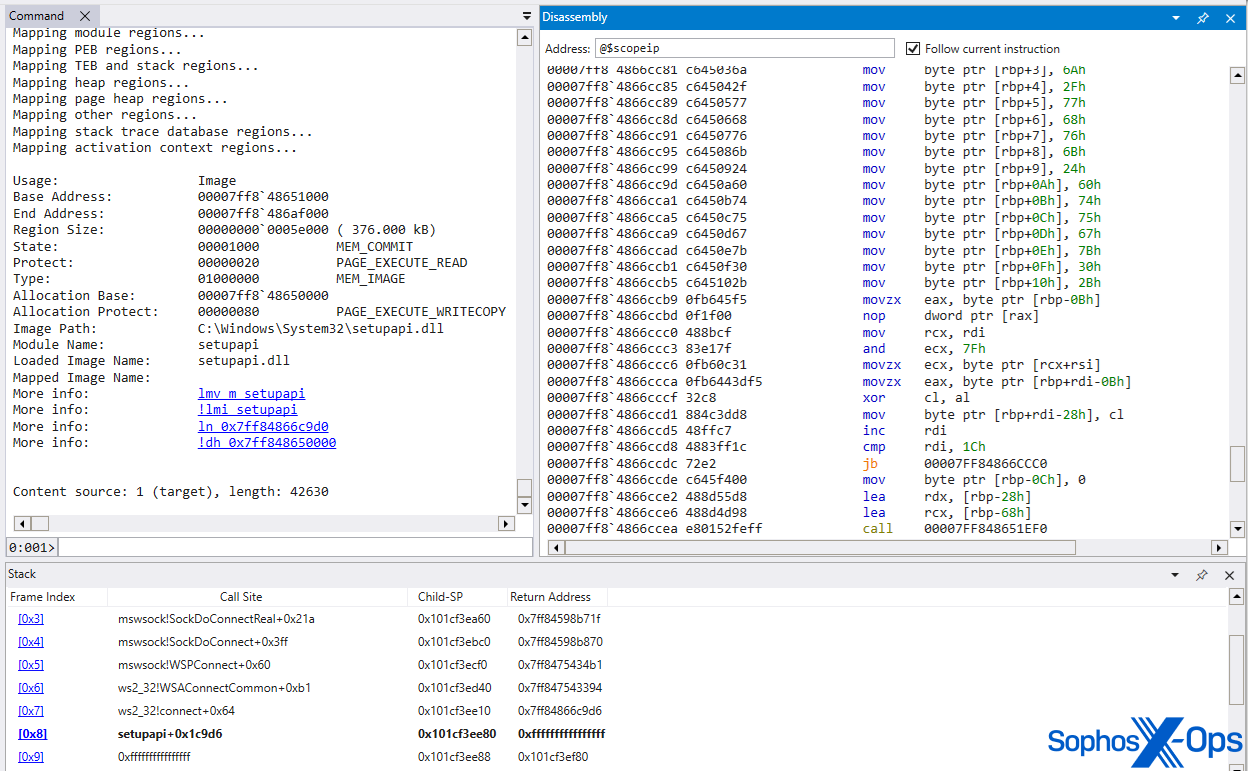
MITRE のサンプルは、setupapi.dll のイメージメモリを上書きするリフレクティブローダーを介してロードされました。RAT は標準的な「イメージ」メモリに存在するため、動的に割り当てられたヒープメモリに存在する場合よりも検出が難しくなります。この手法は高度なインジェクション手法であり、最新の防御を回避するように設計されています。MITRE のアプローチでは、インストーラ (rundll32 プロセス) が SDBbot ローダーコンポーネントをドロップする動作を検出する際に、別の課題が出現していました。インストーラはローダーを %TEMP% にドロップしますが、そのパスへのシンボリックリンクを SYSTEM フォルダに作成し、IFEO レジストリキーは SYSTEM フォルダのパスを指すように設定されていました。この操作により、ドロッパーと常駐 RAT の間に抽象化されたレイヤーが追加されます。
図 4: msverload.dll ローダーのシンボリックリンク
「VerifierDLLs」メソッドを使用することで、実行フローはさらに複雑になりました。ローダー (msverload.dll) は、プロセスの侵入口の前に winlogon.exe プロセス空間にロードされました。その後、VirtualAlloc を使用して埋め込みシェルコードを注入・実行し、VirtualProtect を使用して setupapi.dll の RX イメージメモリを書き込み可能にした後、SDBbot RAT でその内容を上書きしました。メモリパーミッションは後で RX にリセットされ、コードは DLL が直接ディスクからロードされた時と同じように見える「通常の」イメージメモリを装っていました。
図 X: MITRE の SDBbot がロードされ、メモリ保護が PAGE_EXECUTE_READ にリセットされた状態で、正規の setupapi.dll IMAGE メモリのモジュールが上書きされています。
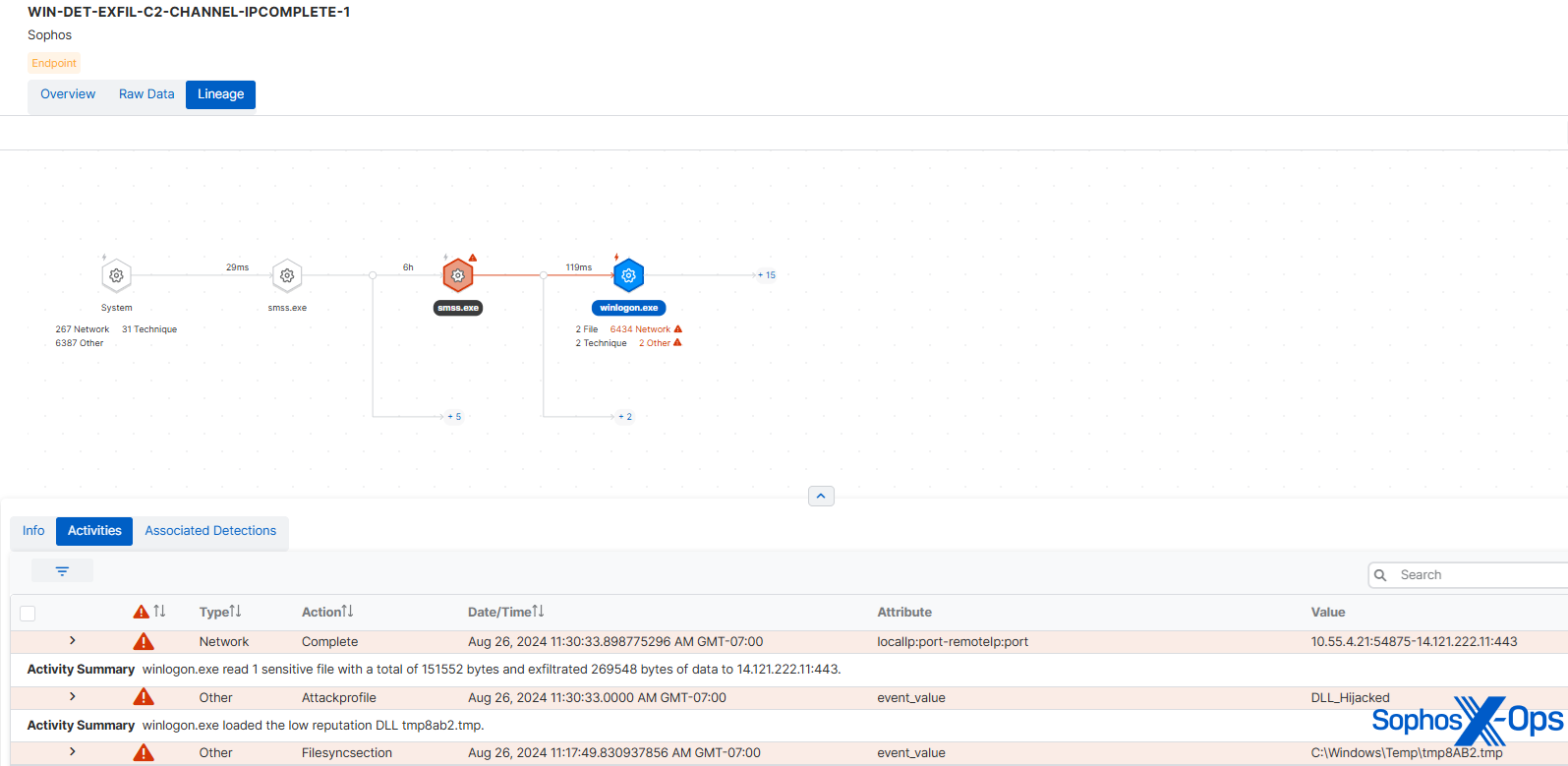
この場面でのソフォスの検出戦略にはいくつかの側面があります。C2 アクティビティが winlogon プロセスから発信されるのは疑わしいこと、および C2 アクティビティ自体が一般的なメモリスキャンのトリガーであること 2023 年にこのトピックに関する記事で説明した通り) です。メモリスキャンでも、シェルコードのパターンが検出されました。この不審な C2 イベントにより、Sophos Detection はデータ窃取活動を捕捉し、2020 年に SDBbot を使用して C2 チャネル経由でデータを外部に送信するという手法が Cl0p によって採用されたことを指摘しました。
図 6: Cl0p シナリオにおけるデータ窃取の検出
影響
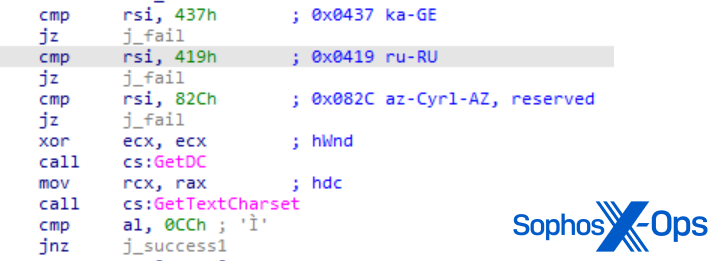
Cl0p ランサムウェアサンプル (sysmonitor.exe、SBDbot 経由でダウンロード) の MITRE の実装は、2019 年の実際のサンプルに非常に近い形でモデル化されていました。本物と同様に、MITRE のサンプルは GetKeyboardLayout を使用して、ロシア、ジョージア、アゼルバイジャンで使用されているレイアウトかどうかを確認しました (これらを使用しているシステムを標的にしないためです)。また、同じ目的を達成するのに使用される GetDC/GetTextCharset API についても同種の API を採用しました。
図 7: 感染したホストがロシア、ジョージア、アゼルバイジャンに位置するかどうかを確認するために GetDC と GetTextCharset を呼び出す MITRE の Cl0p サンプル
また、特にランサムウェアがシャドウボリュームをどのように扱うか、侵害されたホスト上のさまざまなサービスの停止を試みるかどうかといった点で、活動や手法が現実の攻撃とほぼ一致していることも確認しました。
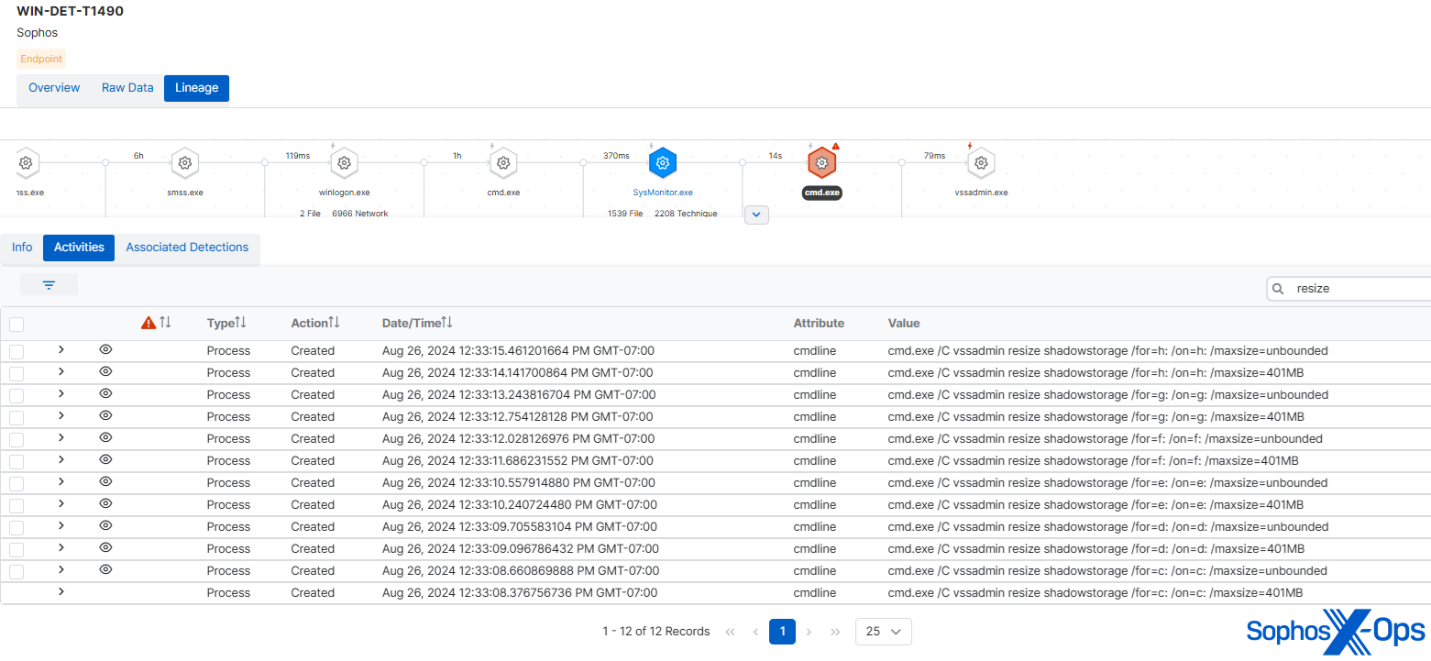
多くのランサムウェアファミリは標的がデータを復元できないようにシャドウボリュームを削除し、その後シャドウストレージのサイズを変更して、それ以上シャドウボリュームを作成できないようにしようとします。しかし、2019 年の Cl0p ランサムウェアは、ハードコードされたドライブのリスト (C から H まで) を巡回しながら、特定の方法で後者のステップを実行しました。MITRE のサンプルはこの動作を正確にエミュレートしていました。
図 8: シャドウストレージのサイズを変更するためにさまざまなドライブを巡回する MITRE 製 Cl0p の実装
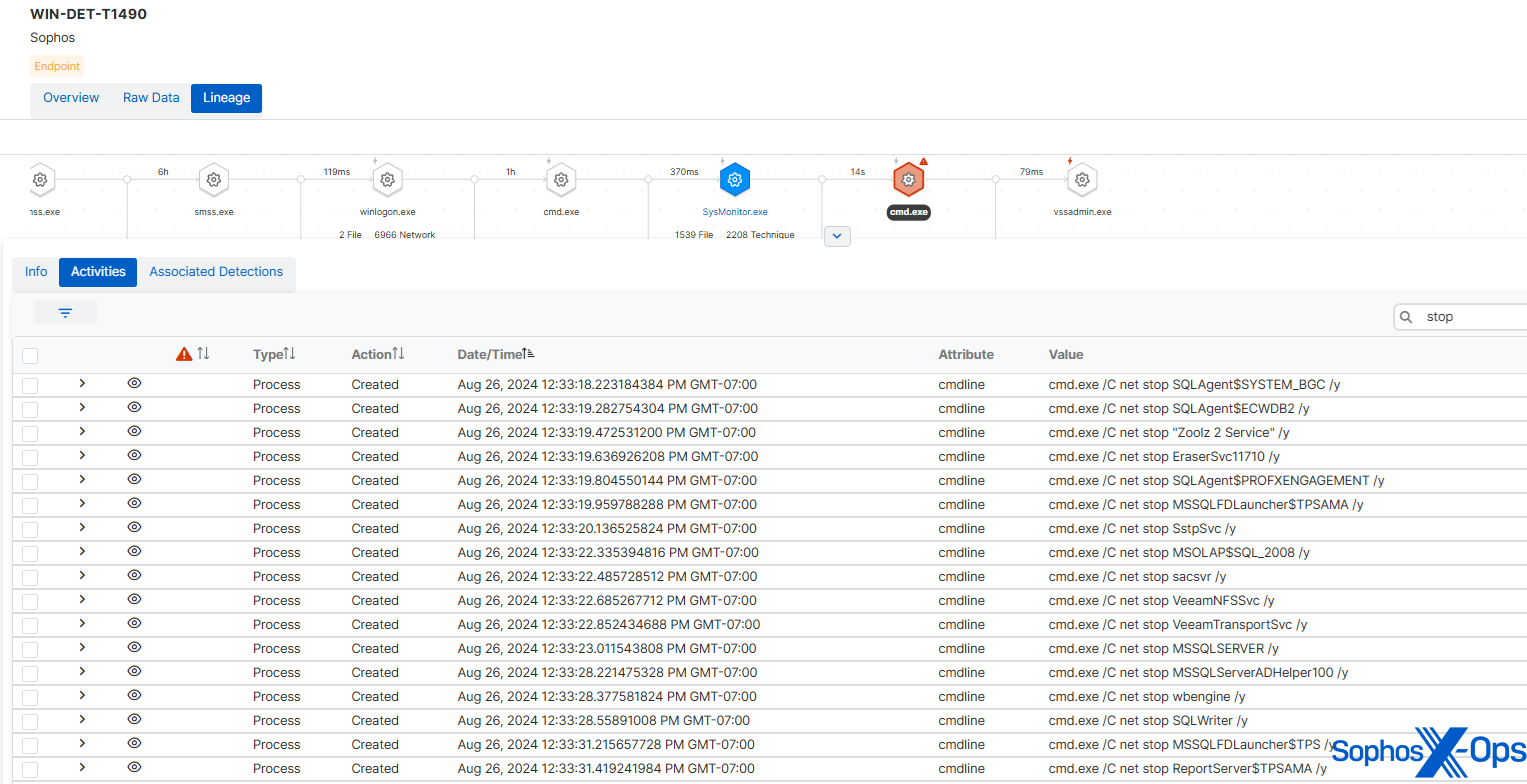
さらに、多くのランサムウェアの亜種と同様に、Cl0p ランサムウェアは、セキュリティサービスや暗号化される重要なデータを含む可能性のあるサービスなど、さまざまなサービスのリストを巡回し、net stop コマンドを用いて終了させようとします。
MITRE のサンプルは、本物の Cl0p ランサムウェアが使用したものと同じリストを同じ順番で使用しました。ただし、おそらくテストの中断を防ぐために、セキュリティサービスリストから除外されています。
図 9: MITRE の Cl0p サンプルで使用された net stop コマンドを示すソフォスの検出結果
MITRE のマルウェアはファイルの暗号化に AES を使用し、暗号化されたファイル内のデータに特別なマーカー (「<Cl1pCl0p!?」) を付与しました。このアプローチは、「Clop^」というマーカーを使用していた実際のマルウェアに似せたものです。しかし、2019 年のサンプルが暗号化アルゴリズムのサポートに advapi32.dll CryptAcquireContextW API を使用していたのに対し、MITRE のバージョンはオープンソースの CryptoPP ライブラリを採用していました。現在数多くのランサムウェアファミリによって使用されているより新しいアプローチです。
LockBit
LockBit は Cl0p と同様、2024 年 2 月に法執行機関によって活動を大幅に制限されたとはいえ、活発なランサムウェアグループです。さらに、2022 年に流出した LockBit のビルダーを用いて、攻撃者はランサムウェアを展開し続けています。MITRE の LockBit シナリオには、一部の LockBit アフィリエイトが使用することが知られている TTP が含まれています (Cl0p シナリオと同様、一般的なランサムウェアバイナリの動作は攻撃全体で一貫していますが、バイナリは一元的に開発および配布されるため、アフィリエイトは幅広いアプローチから選択でき、プレイブックやその後の TTP と IOC が異なる可能性があることは注目に値します)。これらの TTP には、初期アクセスの手法、ThunderShell と PsExec の使用、さまざまな防御回避戦略が含まれています。
初期アクセス
MITRE の「攻撃者」は、以前侵害された認証情報を使用して外部向けの TightVNC サービス (正規のリモート管理ツール) を使用、認証することで攻撃を開始しました。Cl0p のシナリオで前述したように、サービスとしてのランサムウェア (RaaS) のアフィリエイトは、初期アクセスブローカーがサイバー犯罪フォーラムで販売する以前に侵害されたサービスと認証情報を使用し、この方法で初期アクセスを取得するのが一般的です。
攻撃者はアクセス権を得ると、さまざまな探索コマンドを実行しました。これらのコマンドは、ソフォスが RaaS 攻撃の初期段階でしばしば観察するコマンドと一致しており、以下のようなものでした。
nltest /dclist:<domain>
cmdkey /list
net group “Domain Admins” /domain
net group “Enterprise Admins” /domain
net localgroup Administrators /domain
powershell /c "get-wmiobject Win32_Service |where-object { $_.PathName -notmatch \"C:\Windows\" -and $_.State -eq \"Running\"} | select-object name, displayname, state, pathname
これらのコマンドは、2022 年の LockBit 攻撃で観測されたものとほぼ同じです。
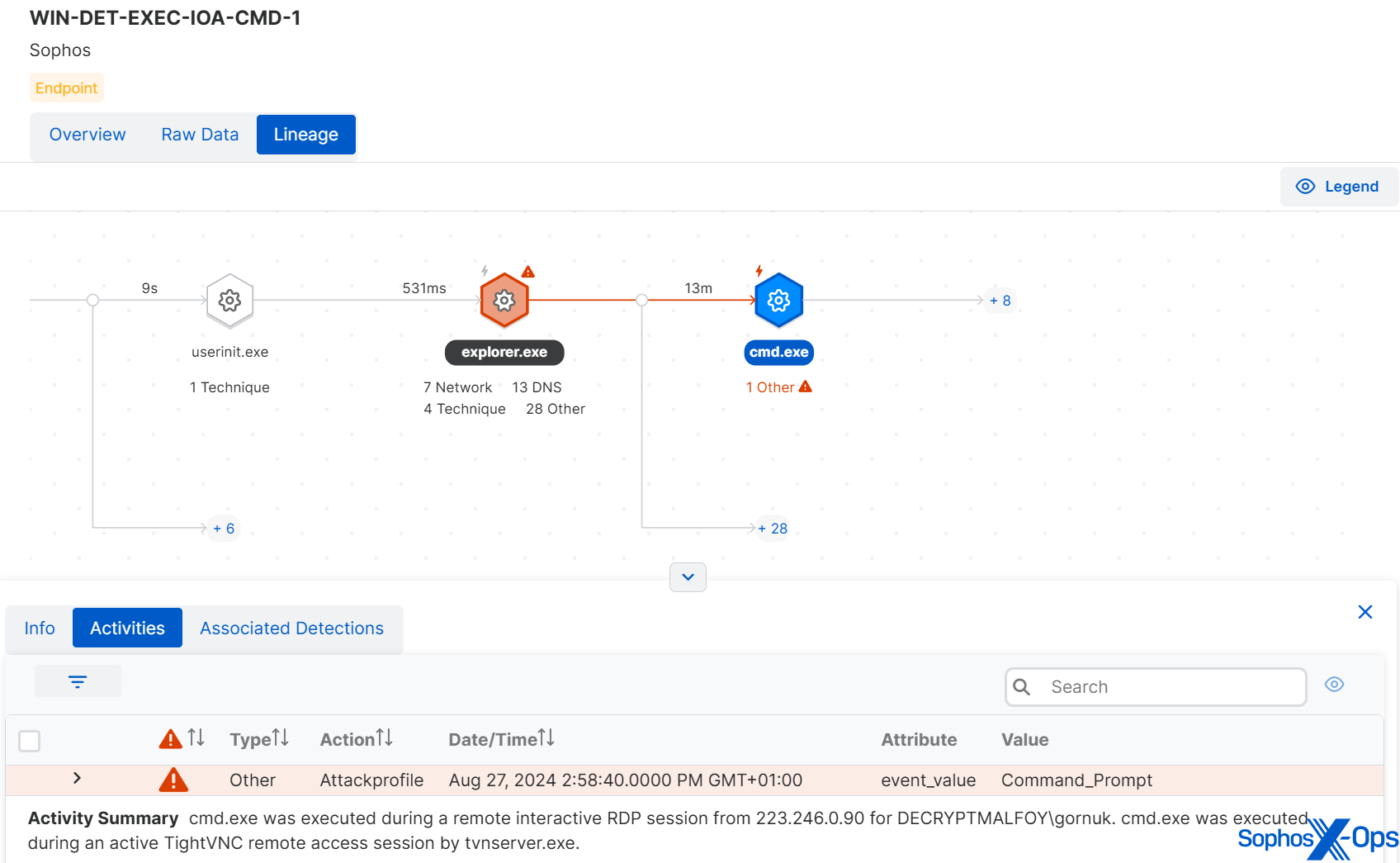
リモートインタラクティブセッション中の cmd.exe の実行は、TightVNC 接続や不審な IP アドレスからのリモートインタラクティブログオンと同様、攻撃の重要な指標でした。
図 10: 初期アクセス段階での不審な活動の調査
常駐
環境内での足場を維持するため、攻撃者は次に ThunderShell として知られる PowerShell リモートアクセスシェルを展開しました。CISA が指摘するように、このシェルは LockBit のアフィリエイトが使用することで知られるツールで、初期アクセスに用いた方法が失われた場合でも、常駐し続けることができます。この段階で、ソフォスはくり返し発生するネットワーク接続を監視して「ビーコン」活動を特定し、疑わしいと思われるプロセスや接続にフラグを立てました。
MITRE の「攻撃者」は、winlogon自動ログオンレジストリキーを用いて、さらなる常駐化を確立しました。この活動は、実際のシナリオで想定される活動とは若干異なります。ソフォスの経験上、攻撃者は平文の認証情報を特定する目的で鍵を一覧化します。
影響
MITREは、RaaS のアフィリエイトが二重の恐喝 (他の多くのランサムウェアグループが使用する手法) を実行するために使用する特注の LockBit 流出ツール StealBit をエミュレートしました。このツールを使用することにより、機密データを暗号化する前にリモートサーバーに流出させられます。
MITRE バージョンの StealBit (connhost.exe と名付けられています) は本物と同様、PEB の「BeingDebugged」フラグを使用してアタッチされたデバッガをチェックし、LoadLibraryExA と GetProcAddress を使用して動的 API 解決を実行しました。解決された DLL は XOR で難読化されたファイル名で保存されました。このアプローチは、本物の StealBit マルウェアと非常によく似ています。
侵入後、MITRE の「攻撃者」はデータを暗号化し、環境全体で自己複製するために、エミュレートバージョンの LockBit 実行ファイルを展開しました。
実際のバージョンと同様に、MITRE の LockBit サンプルは (静的解析から API 名を隠蔽するために) メモリ内 API ハッシュアルゴリズムを使用した動的 API 解決や、NtSetInformationThread によるアンチデバッグなど、いくつかの回避テクニックを使用していました。ソフォスは 2022 年の LockBit 3.0 の分析でこれらの方法の両方を文書化しましたが、MITRE の実装が DJB2 ハッシュを使用していたことは注目に値します。このハッシュの使用はオリジナルの LockBit のアプローチ (ROR ベースのハッシュメソッドとシードキーを使用したカスタム実装) とは異なりますが、最終的な結果は同じです。同時に、ソフォスや他のベンダーが以前に検出した可能性のある既知の IOC の侵入も防げます。
図 11: MITRE バージョンの LockBit は、DJB2 ハッシュアルゴリズムの実装を使用していました。このハッシュは複雑な実装です。MITRE は本物の LockBit バイナリの機能を再現するために多大な労力を費やしているようです。
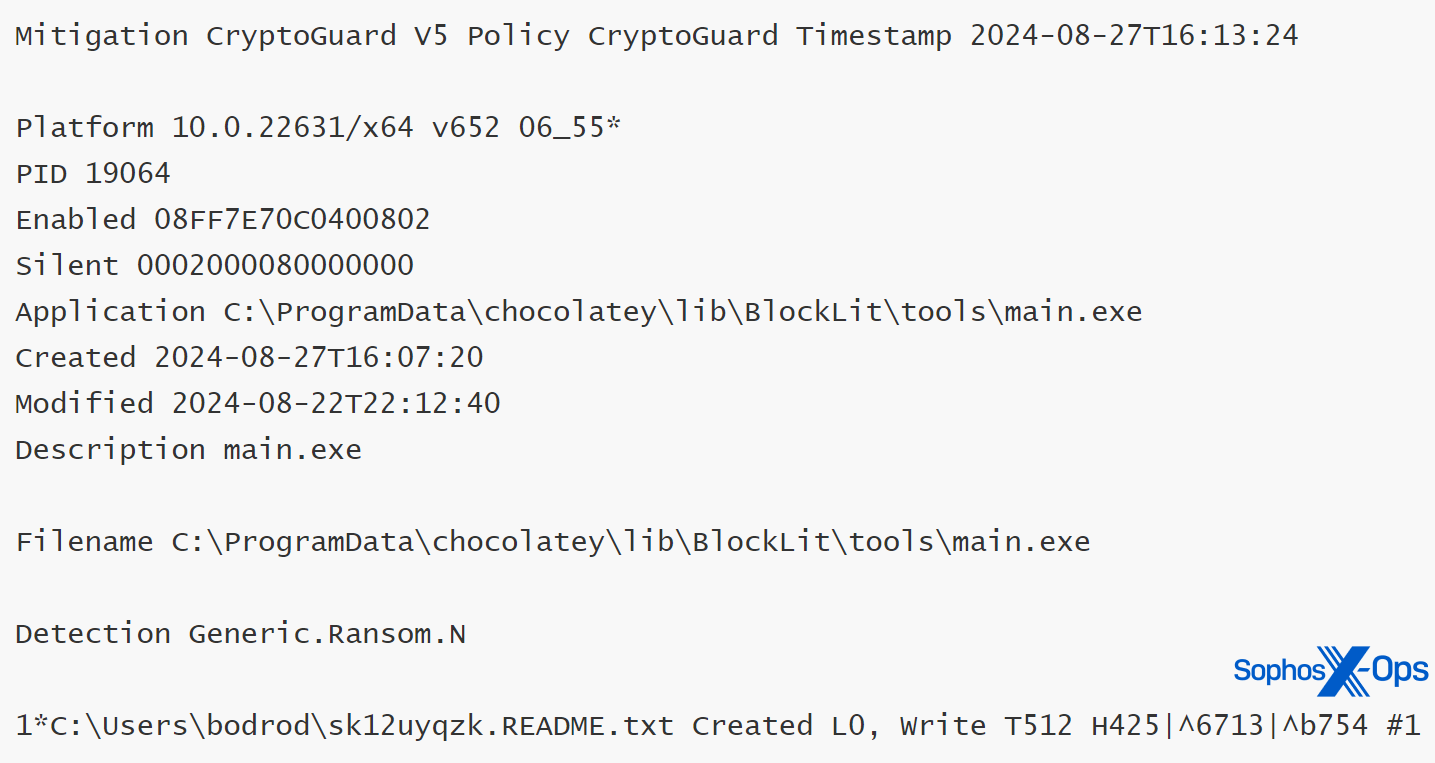
ソフォスは CryptoGuard を使用してこのアクティビティを検出しましたが、このテストは監視専用モードで実行されたため、CryptoGuard は暗号化をロールバックしませんでした。保護に焦点を当てた別のテストでは、リモート暗号化のエミュレーション中であっても、暗号化されたファイルは元の状態にロールバックされました。
図 12: ランサムウェアの活動の検出とランサムノートの作成を示す CryptoGuard のサムプリント情報
結論
2024 年、ソフォスが MITRE の ATT&CK Evaluations:
Enterprise に参加するのは 4 年目となりました。例年通り、エンドツーエンドの攻撃チェーンとリアルさに焦点を当てたこの評価は、ソフォスおよび他のベンダーの能力を評価する上で非常に有意義なものでした。また、MITRE が透明性を重視していることもソフォスは歓迎しています。
どのような種類のエミュレーションでもそうですが、こうした評価の価値の多くは、シナリオがいかに正確で現実的であるかに依拠します。ソフォスは、MITRE のテストが実際の攻撃からわずかに逸脱していることを指摘しましたが、その多くは避けられない制約によるものでした。今回のテストは全体的には、既知の攻撃キャンペーンや攻撃者と非常に類似していました。
複数のベンダーが参加する透明かつ現実的な評価は、ベンダー自身だけでなく、お客様、ひいては社会に広く利益をもたらします。ソフォスは、今後も積極的にこのような評価に参加し、ソフォスの考えや発見を逐次報告していきます。