This article is part of a series that aims to educate cyber security professionals on the lessons learned by breach victims. Each lesson will include simple recommendations, many of which do not require organizations to purchase any tools.
Multi-Factor Authentication (MFA) is a security measure that requires two or more proofs of identity to grant you access. In other words, you need more than just a password to be granted access. A one-time passcode, facial recognition, or a fingerprint might also be required as an additional security check.
Every admin knows the benefits of MFA for accessing business applications. They keep our Office365 and Salesforce data safe, even if an adversary obtains, guesses, buys or brute-forces a username and password.
However, when applications moved to the cloud, the login consoles of those applications were exposed to the Internet as well. System administration and security also moved to being managed ‘from the cloud’, and thus also needs MFA.
MITRE ATT&CK Technique T1078 (‘Valid Accounts’) describes how threat actors use valid accounts to gain initial access to the network, evade defenses, obtain persistence, and escalate their privileges.
These tactics in turn allow various defenses to be bypassed, including anti-virus, application control, firewalls, intrusion detection/prevention systems and system access controls. Unauthorized use of valid accounts is very hard to detect, as they look very much like business-as-usual.
Valid Accounts is one of the top 5 techniques Sophos observed for initial access (https://attack.mitre.org/tactics/TA0001/) as reported in the 2021 Active Adversary Playbook. Some administration tools (e.g. Solarwinds, Webroot, Kaseya, and Connectwise) have even been used to deliver malicious payloads.
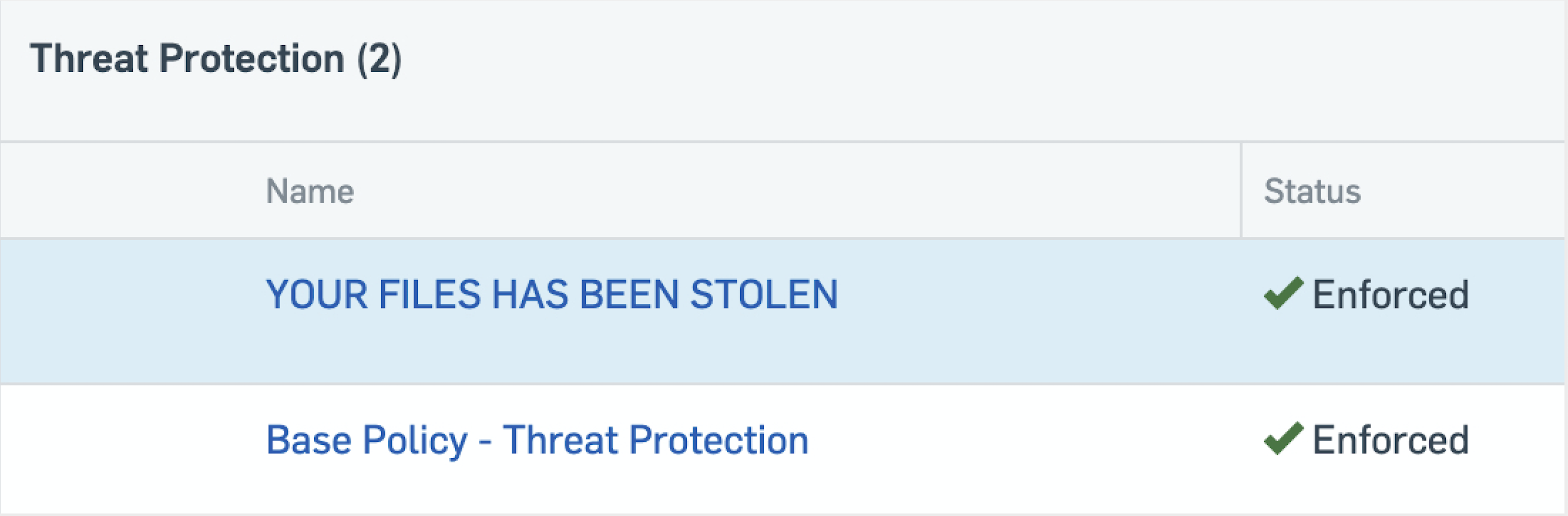
What happens when a threat actor gains access to a security console? In the example below, the threat actor simply wrote their own policy and turned every security setting off.
Even on-premises security administration systems should still use MFA if possible – life is easier for an adversary if they can just turn off your security solutions before deploying their malware. If you use a VPN to access the network, we highly recommend enabling MFA on that too.
Enabling MFA for your system administration and security tools achieves three goals:
- Reduces risk of access by unauthorized persons
- Generates alerts for attempted access, allowing an admin to block future attempts as needed
- Prevents account sharing, ensuring accurate audit trails that can tie behavior to a specific user
Enabling MFA often costs nothing more than your time. If you’ve been ignoring giant ‘Enable MFA’ banners on your consoles, it’s past time to take that action. If your security vendor doesn’t offer MFA options, it’s time to ask why not?

Leave a Reply