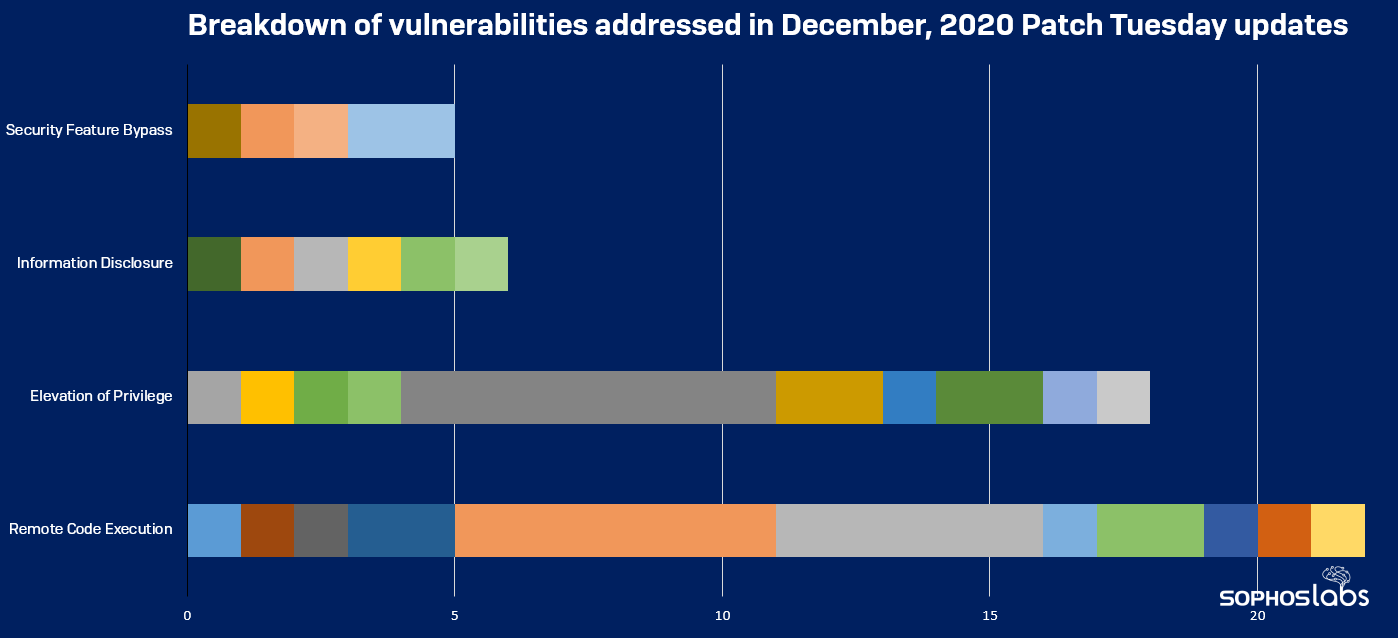
The final patch Tuesday release from Microsoft for 2020 squashes only the second-fewest number of bugs of the year, but the ones the company chose to repair include some of the most serious vulnerabilities the company has fixed in the past 12 months. Attackers who target the remote code execution vulnerabilities found in some of Microsoft’s premiere enterprise products, including Sharepoint and a (now outdated) version of Exchange, may be more likely to succeed because the weaknesses in both products are the result of logic bugs, which require less effort to discover and exploit than things like, for instance, memory corruption vulnerabilities.
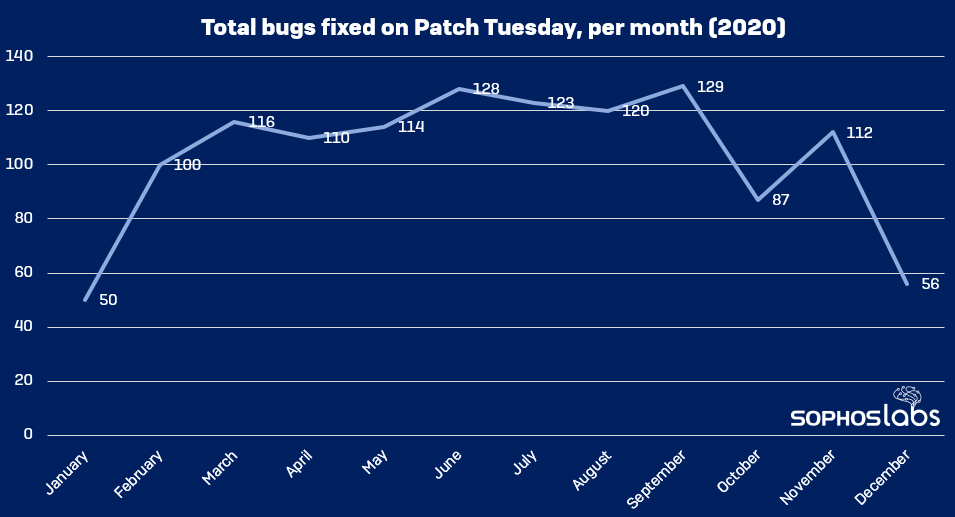
December’s collection of 56 fixes is second-smallest to the release at the beginning of the year, in January, when the company patched 50 bugs.
But don’t let the small number of fixes lull you into a sense of complacency. Nearly 40% of this month’s bugs can lead to attackers being able to launch malicious code on targeted systems. Thirty Microsoft products or Windows subsystems got updates today, with the Windows Backup Engine getting the most fixes (repairing seven privilege escalation bugs) for a single process. Microsoft’s Excel spreadsheet software, for example, receives fixes for six remote code execution bugs.
The SophosLabs Offensive Security Team has already demonstrated a proof-of-concept exploit against one of three Exchange remote code execution vulnerabilities (CVE-2020-17144) fixed this month. If successfully exploited, this bug permits the attacker to gain access to the full content of email stored on the targeted Exchange server.
As with all Patch Tuesdays, Microsoft publishes a detailed writeup about major fixes on their Security Updates page. The availability of patches does not mean that your computer will install it quickly, enough. To find and download this month’s Cumulative Update patch yourself, search for the term “2020-12” at the Microsoft Update Catalog website and select the monthly security rollup that matches your computer’s CPU architecture and build of Windows. You can also read the full technical details about each patch on December’s Security Updates Guide.
What follows are notes about some of the more critically important fixes released this month.
Windows NTFS Remote Code Execution Vulnerability
CVE-2020-17096
NTFS is the standard file system used in all modern Windows products, but it might surprise you that it has been in use since it was introduced in 1993 as part of Windows 3.1. This month’s fix addresses a bug present in the NTFS filesystem driver code. An attacker with access to perform low-level filesystem operations may trigger a stack memory corruption on an affected system.
There are two main ways an attacker may obtain or use such access:
- When an attacker exploits the bug remotely, by way of interacting with file shares on a remote Windows machine using the SMB2 protocol, they may be able to engage in remote code execution.
- If the attacker can execute a malicious exploit program targeting a vulnerable computer running Windows, using this exploit they may be able to perform a local privilege escalation, as well.
The former is, obviously, the most serious scenario. However as a general rule accessing a file share requires the attacker to have valid user credentials to the remote system. For a determined attacker who knows what they’re doing, this may not pose much of an impediment, but it’s likely beyond the capacity of an amateurish, opportunistic attacker.
In any case, successful exploitation of the stack memory corruption condition may lead to arbitrary code execution. Since the vulnerable code is running in the context of a Windows Kernel driver, this means a powerful compromise with the capability to easily circumvent many kinds of software, including (but not limited to) endpoint protection.
Microsoft SharePoint Remote Code Execution Vulnerability
CVE-2020-17121
Sharepoint suffers from a directory traversal vulnerability that may be triggered when it processes an attacker’s malicious input. An attacker may use this vulnerability to cause an unsafe deserialization of malicious input, ultimately leading to remote code execution.
In order to execute the attack, the attacker requires valid user credentials to the target SharePoint site, in order to log into it and create a new Team Site on it. Gaining useful credentials is an impediment to casual attackers and prevents them from leveraging the bug without taking additional steps.
Since the bug in question is a ‘logic’ type bug (as opposed to a memory corruption bug) it can be reliably exploited without having to account for unpredictable conditions, earning it an “Exploitation More Likely” rating from Microsoft.
Successful exploitation of this vulnerability can lead to the compromise of the system hosting the SharePoint server, which in turn can reveal sensitive files or data to the attacker.
Microsoft Exchange Remote Code Execution Vulnerability
CVE-2020-17144
While this is a quite serious vulnerability, the potential risk it poses is mitigated for two reasons: It only affects the Exchange 2010 mail server, for which Microsoft recently ended all support, and it requires the attacker to have valid account credentials for at least one email user on the affected server. The user doesn’t need to have administrative access.
An email user may upload a malicious configuration file to the Exchange server, on which the server proceeds to perform an unsafe deserialization. An attacker may exploit this condition to execute arbitrary code on the affected server, in the context of the privileged Exchange service process MSExchangeMailboxAssistants.exe, resulting in compromise of the server. Supplying this malicious configuration file requires the attacker to have valid email account credentials on the affected mail server.
Once the server is compromised, it exposes the contents of the mailboxes used by all accounts on the Exchange server to the attacker.
In some cases the same system running the Exchange server also hosts other sensitive or critical components or services,. For instance, an Exchange server doing double-duty as as a Domain Controller could lead to even worse consequences. As with the previously referenced Sharepoint bug, CVE-2020-17144 is also a logic bug and therefore easier for an attacker to discover and take advantage of the vulnerability.
Sophos protection
Here is a list of protection released by SophosLabs in response to this advisory to complement any existing protection and generic exploit mitigation capabilities in our products.
|
CVE
|
SAV
|
IPS
|
|---|---|---|
| CVE-2020-17096 | N/A | SID:2304630 |