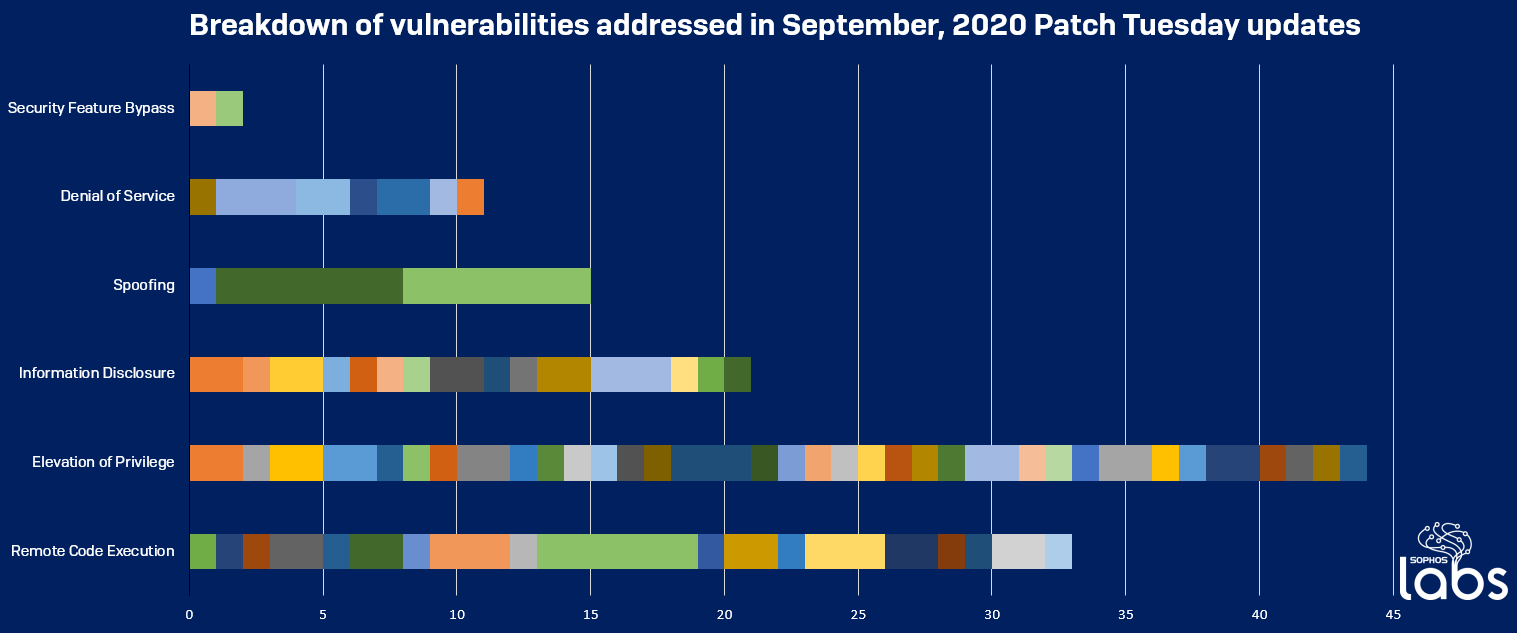
Microsoft released its monthly gaggle of updates today, which most people will receive as a small number of large update “rollup” packages when their computer decides to update itself automatically, as most do. The various patches across Microsoft’s product lines fix 129 bugs that can be broken down into six general categories based on how the bugs impact the end user of the computer if left unrepaired.
The company considers at least 24 of the bugs to fall in the “critical” category, which means they are either being actively exploited or are likely to be in the near future. However, since the critical and less-severe categories are all lumped into the same patch rollups, what’s important is that you apply the updates as soon as you are able.
Readers can find the full details about every patch this month in Microsoft’s Security Update Guide Release Notes, and Servicing Stack Updates. If you don’t want to wait, you can also download patches manually from the Microsoft Security Update Catalog, where they are organized by the operating system or product.
Since this month features a relatively large list of critical vulnerabilities in the updates, here are a list of the assigned CVE numbers and the names of the vulnerabilities flagged as critical.
- CVE-2020-0911: Windows Modules Installer Elevation of Privilege Vulnerability
- CVE-2020-0922: Microsoft COM for Windows Remote Code Execution Vulnerability
- CVE-2020-1013: Group Policy Elevation of Privilege Vulnerability
- CVE-2020-1033: Windows Kernel Information Disclosure Vulnerability
- CVE-2020-1039: Jet Database Engine Remote Code Execution Vulnerability
- CVE-2020-1044: SQL Server Reporting Services Security Feature Bypass Vulnerability
- CVE-2020-1057: Scripting Engine Memory Corruption Vulnerability
- CVE-2020-1129: Microsoft Windows Codecs Library Remote Code Execution Vulnerability
- CVE-2020-1172: Scripting Engine Memory Corruption Vulnerability
- CVE-2020-1200: Microsoft SharePoint Remote Code Execution Vulnerability
- CVE-2020-1210: Microsoft Excel Remote Code Execution Vulnerability
- CVE-2020-1252: Windows Remote Code Execution Vulnerability
- CVE-2020-1285: GDI+ Remote Code Execution Vulnerability
- CVE-2020-1319: Microsoft Windows Codecs Library Remote Code Execution Vulnerability
- CVE-2020-1452: Microsoft SharePoint Remote Code Execution Vulnerability
- CVE-2020-1453: Microsoft SharePoint Remote Code Execution Vulnerability
- CVE-2020-1460: Microsoft SharePoint Server Remote Code Execution Vulnerability
- CVE-2020-1508: Windows Media Audio Decoder Remote Code Execution Vulnerability
- CVE-2020-1576: Microsoft SharePoint Elevation of Privilege Vulnerability
- CVE-2020-1593: Windows Media Audio Decoder Remote Code Execution Vulnerability
- CVE-2020-1595: Microsoft SharePoint Remote Code Execution Vulnerability
- CVE-2020-16857: Microsoft Dynamics 365 for Finance and Operations (on-premises) Remote Code Execution Vulnerability
- CVE-2020-16862: Microsoft Dynamics 365 (on-premises) Remote Code Execution Vulnerability
- CVE-2020-16875: Microsoft Exchange Memory Corruption Vulnerability
Some of the surprises on the list include the GDI+ subsystem, which was also the subject of notable patches in both 2008 and 2009, and media codecs, which process images, audio, and video files; the business-focused Microsoft Dynamics 365, which hasn’t been prominently included in previous patch alerts, but has vulnerabilities in its “on-premises” version that aren’t present (or were fixed at Microsoft’s end) in the Office 365 Cloud version; and Windows Sharepoint, which is getting a lot of use as enterprises focus on helping their remote, distributed workforce to collaborate better during the continuing, extended quarantine from offices and schools.
The SophosLabs Offensive Security team, which anayzes software for vulnerabilities and takes responsibility for validating information provided by Microsoft to MAPP partner companies, sent along the following notes about the bugs they found most interesting from the current batch of fixes.
Windows Win32k Elevation of Privilege
CVE-2020-1152
This privilege escalation vulnerability is present in the DirectComposition subsystem of the Win32k.sys driver file. Introduced in Windows 8, DirectComposition is a C++ graphics component that enables high-performance bitmap composition with transforms, effects, and animations.
In order to manage these high-end graphics functions, Win32k introduces specific kernel objects and links those objects together by reference counting. This vulnerability comes from an integer overflow of the refcount of a marshaller object, which (when triggered) leads to use-after-free memory corruption. In order to trigger the vulnerability, a logged-in user would have to run a specially-crafted application or script — the kind of action that an attacker might take in the course of an active intrusion in order to give themselves privileges to execute other commands.
Windows Common Log File System Driver Elevation of Privilege Vulnerability
CVE-2020-1115
It’s a mouthful to say, but the gist of this bug means there’s a privilege escalation bug in the Common Log File System (CLFS) driver in Windows. The CLFS driver is used to generate and collect high performance transaction logs, and is enabled by default on any modern Windows computer because it is used both by the Kernel Transaction Manager (KTM) and by Microsoft’s NTFS file system. The driver was introduced in Windows Server 2003 R2, 15 years ago.
The vulnerability occurs when the driver is parsing a BFL log file. Windows computers wouldn’t normally build a log file containing the vulnerability, but it’s possible that an attacker could create a specially crafted BFL log that could trigger an exploit.
In a hypothetical attack that’s targeted at IT or security analysts (who might be sharing such files among themselves during an incident response), the weaponized log file would trigger the CLFS driver to issue a call to the RtlCopyMemory() function in the driver. Exploiting such memory corruption would result in an attacker being able to run arbitrary code in kernel-mode, compromising the host and, possibly, hindering an investigation.
Fortunately, we (probably) don’t have to remind this particular target audience about the importance of installing patches. But we’ll do it again anyway: Take your vitamins, wear a mask, and install your patches!
Sophos protection
Here is a list of protection released by SophosLabs in response to this advisory to complement any existing protection and generic exploit mitigation capabilities in our products.
| CVE | SAV | IPS |
|---|---|---|
| CVE-2020-0664 | n/a | SID:2303716 |
| CVE-2020-0856 | n/a | SID:2303717 |
Sophos aims to add detections for critical issues, based on the type and nature of the vulnerabilities, as soon as possible and where we have been given sufficient information to be able to do so. In many cases, existing detections in endpoint products such as Intercept X will catch and block exploit attempts without the need for updates.

Leave a Reply