Among the 94 vulnerabilities fixed this month by Microsoft, 29 are rated as Critical. Most importantly, the Remote Desktop Protocol (RDP) and its associated service (RDS) collect a total of 6 CVEs, which seems to show a renewed interest in the RDP protocol by vulnerability researchers; two of those classified as wormable (CVE-2019-1181 and CVE-2019-1182) by Microsoft.
Additional details can be found in the Microsoft Security Update Guide.
In addition, the company released two advisories about Active Directory, ADV190014 (Critical) and ADV190023 (Important).
This month major updates cover vulnerabilities in the following components:
- Remote Desktop Protocol / Remote Desktop Services
- Hyper-V
- DHCP
- Internet Explorer, Edge & ChakraCore
- Microsoft Office
- Microsoft Windows kernel (RPC, GDI, WSL)
- Jet Database Engine
- Visual Studio
- Windows VBScript Engine
All of the critical vulnerabilities should be patched, as they may enable a successful attacker to take over the targeted system/service with a high level of privilege, which can later be used to compromise a network further.
The vulnerabilities CVE-2019-1181 and CVE-2019-1182 turn out to be particular nasty as only any Windows OS supporting RDP8 or RDP8.1 (Windows 7 through 10, including Server) are, by default, impacted. Network admins can enable Network Level Authentication (aka. NLA) to slow down an attacker, but NLA will not provide sufficient protection to entirely mitigate these vulnerabilities.
Affected systems that have Network Level Authentication (NLA) enabled prevent “wormable” malware or advanced malware threats that could exploit the vulnerability, as NLA requires authentication before the vulnerability can be triggered. However, affected systems are still vulnerable to Remote Code Execution (RCE) exploitation if the attacker has valid credentials that can be used to successfully authenticate.
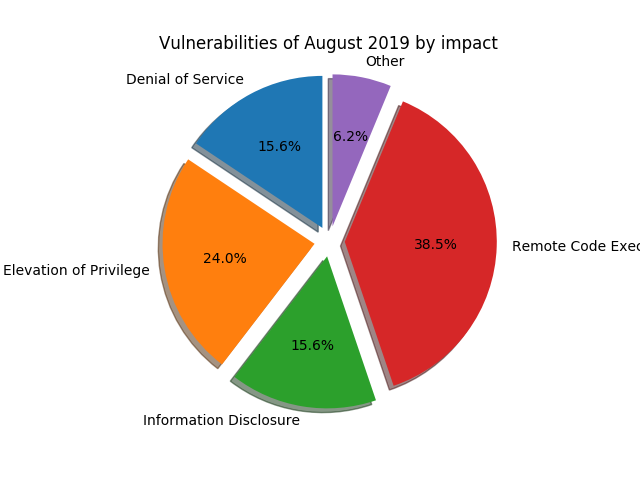
Important updates this month
Remote Desktop Services: Following up the trend started by the “BlueKeep” vulnerability reported last May, this month PT fixes CVE-2019-1181 and CVE-2019-1182: two remote code execution vulnerabilities within the Remote Desktop Services – formerly known as Terminal Services. As with BlueKeep, little information was publicly disclosed by Microsoft, which considered the vulnerabilities wormable; but unlike BlueKeep, the vulnerabilities affect all Windows from 7 to 10. Although NLA would provide a temporary workaround to exploiting them (by forcing attacker to successfully authenticate first), the only way to secure the RDP service is by patching it. An unauthenticated successful attacker who exploited this vulnerability can execute arbitrary code on the targeted system, with the highest level of usermode privilege.
Hyper-V: An input validation issue in the VMSwitch component of Hyper-V is what an attacker could exploit in a Hyper-V guest VM to achieve remote code execution onto the Hyper-V host (designated as CVE-2019-0720). Although its exploitability was marked as “less likely”, its impact highly encourages to apply MS patches as soon as possible, along with the other Hyper-V related CVEs issued this month: CVE-2019-0714, CVE-2019-0717, CVE-2019-0718, CVE-2019-0720, CVE-2019-0715,CVE-2019-0723 and CVE-2019-0965.
Web browsers and JS engine: A total of 10 vulnerabilities affecting ChakraCore (the Edge browser JavaScript engine), Edge, and Internet Explorer were patched this month. Memory Corruption Vulnerabilities: ChakraCore and Internet Explorer were found vulnerable to a range of vulnerabilities, from simple information to type confusion vulnerability. By simply visiting a web page embedding an exploitation payload, a user can unwillingly allow an attacker to execute code with their level of privileges. The company’s patch addresses vulnerabilities with the following designations: CVE-2019-1131,CVE-2019-1139,CVE-2019-1140,CVE-2019-1141,CVE-2019-1195,CVE-2019-1196,VE-2019-1197,CVE-2019-1193,CVE-2019-1192 and CVE-2019-1030.
DHCP: DHCP has been under scrutiny over the last several months. Therefore this month is not spared with some new vulnerabilities discovered in both the Windows DHCP client and server. Despite the complexity of reliable exploitation, exploiting those vulnerabilities would result in Denial of Service, or potentially code execution. The CVEs assigned are the following: CVE-2019-0736, CVE-2019-1206, CVE-2019-1212, and CVE-2019-1213.
Windows Kernel: As usual the Windows was patched in several locations: Elevation of Privilege (EoP) in various internal components such as RPC runtime or the GDI were fixed (CVE-2019-1173,CVE-2019-1174,CVE-2019-1175,CVE-2019-1177,CVE-2019-1178,CVE-2019-1179,CVE-2019-1180,CVE-2019-1184,CVE-2019-1186,CVE-2019-1159,CVE-2019-1164,CVE-2019-1227,CVE-2019-1228, CVE-2019-1143,CVE-2019-1154,CVE-2019-1158).
How is Sophos responding to these threats?
Here is a list of protection released by SophosLabs in response to this advisory to complement any existing protection and generic exploit mitigation capabilities in our products.
| CVE | SAV | IPS | Intercept-X |
| CVE-2019-1141 | Exp/20191141-A | 2200885 | N/V |
| CVE-2019-1196 | Exp/20191196-A | 2201342 | N/V |
N/V = Not Validated. The PoC code provided with MAPP advisories does not include active exploits and as such is not applicable to Intercept X testing. The IX ability to block the exploit depends on actual exploit weaponization approach which we won’t see until it’s spotted in the wild. The SAV and IPS detections developed for the PoCs do not guarantee interception of in-the-wild attacks
Additional IPS Signatures
Microsoft
|
CVE |
SID |
| CVE-2019-1139 | 2201340 |
| CVE-2019-1140 | 2201341 |
| CVE-2019-1141 | 2200885 |
| CVE-2019-1195 | 2200885 |
| CVE-2019-1197 | 2200885 |
| CVE-2019-1199 | 2201343 |
| CVE-2019-1201 | 35190 |
Adobe
| CVE | SID |
| CVE-2019-7832 | 3310867 |
| CVE-2019-7965 | 9000957 |
| CVE-2019-8005 | 49294 |
| CVE-2019-8009 | 4300087 |
| CVE-2019-8011 | 44059 |
| CVE-2019-8025 | 26021 |
| CVE-2019-8029 | 2201201 |
| CVE-2019-8035 | 2200337 |
| CVE-2019-8045 | 3310026 |
| CVE-2019-8047 | 39873 |
| CVE-2019-8098 | 2201224 |
| CVE-2019-8099 | 9000941 |
| CVE-2019-8100 | 9000929 |
| CVE-2019-8101 | 9000941 |
| CVE-2019-8103 | 9000941 |
| CVE-2019-8105 | 2201217 |
| CVE-2019-8106 | 9000941 |
How long does it take to have Sophos detection in place?
We aim to add detection to critical issues based on the type and nature of the vulnerabilities as soon as possible. In many cases, existing detections will catch exploit attempts without the need for updates.
What if the vulnerability/0-day you’re looking for is not listed here?
If we haven’t released an update for a specific exploit, the most likely reason is that we did not receive the data that shows how the exploit works in the real world. As many of this month’s exploits were crafted in a lab and have not been seen in the wild, nobody has enough information (yet) about how criminals would, hypothetically, exploit any given vulnerability. If or when we receive information about real attacks, we will create new detections, as needed.
