May 2019’s Patch Tuesday is notable for many reasons: not only it is Microsoft’s biggest release (in terms of the number of fixes) so far for the year, but it also also includes two critical updates: a patch for RDP that Microsoft deemed so critical they decided to push an out-of-support patch for Windows 2003 and XP, and another for DHCP server. Both could be exploited without any user interaction, and provide privileged access to the compromised server.
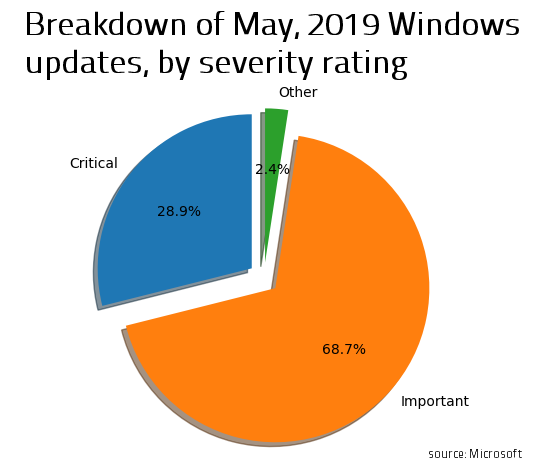
One of the highlights of this month PT is that Microsoft decided to release a total of 79 security updates for May 2019 for various products, which makes it the biggest release to date with 22 vulnerabilities flagged as Critical, and 56 as Important.
If that wasn’t enough, this month’s set of Windows updates coincides with a slew of fixes for Adobe products, including patches that address 84 distinct, important vulnerabilities in Adobe Reader, and one for Adobe Flash Player. Because most of those vulnerabilities involved memory corruption, Adobe characterized their exploitation as “less likely.” However, we still recommend that you download and deploy the patches from Adobe as soon as possible, because they’re still incredibly dangerous if someone figures out how to exploit them (and there are people who will try).
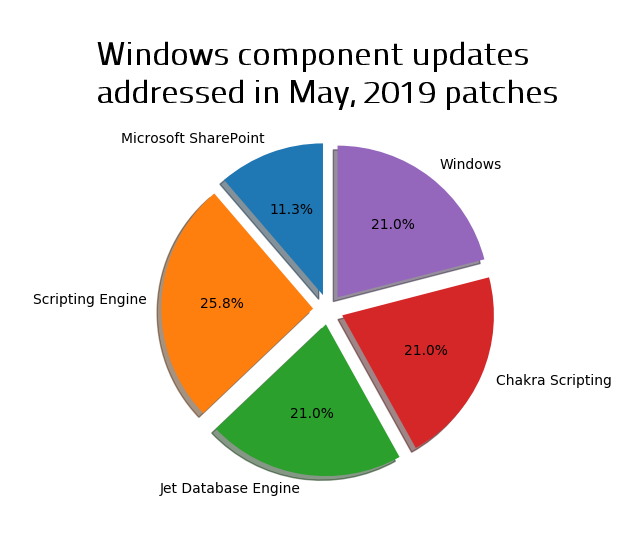
The most-affected Microsoft products by the latest updates are Chakra Scripting Engine (the core of the Edge browser, which fixed 14 potential Remote Code Execution vulnerabilities). Microsoft also fixed 13 bugs in the Jet Database Engine, and 12 that affected Office/SharePoint, addressing a wide range of vulnerabilities, from cross-site scripting (XSS) to EoP. Microsoft also patched several components of the Windows kernel (including GDI+, Win32k and NDIS drivers, Windows Error Reporting, Remote Desktop services (which we take to mean, not the RDP protocol, itself, or the client application) and DHCP services, and the Hyper-V hypervisor.
The month’s most important updates
Remote Desktop Service: The most important update from Microsoft will fix a Remote Code Execution vulnerability in Remote Desktop Services (CVE-2019-0708). The company disclosed little information regarding the vulnerability itself, but the very fact that Microsoft decided to provide patches for Windows XP and 2003, both of which have reached their end-of-life (in April, 2014 and July, 2015, respectively) imply that the underlying bug affecting this subsystem is likely to be exploitable, and possibly wormable, as no user interaction is required.
The vulnerability, tagged as Critical by Microsoft, can be triggered by an unauthenticated attacker by sending specifically crafted packets. A successful exploitation of this vulnerability would allow said attacker to entirely and remotely compromise the target server with maximum privileges. It should be stressed that owners of Windows 8/2012 and higher are not impacted by this vulnerability. If you own a Windows XP/2003 or Windows 7/2008, it is critical to patch as soon as possible, or upgrade to a more recent Windows version.
DHCP Server: Another critical vulnerability this month is designated CVE-2019-0725: Windows DHCP Server Remote Code Execution vulnerability. Although the Windows DHCP service has been the target for several vulnerabilities in the past few months, the vulnerability CVE-2019-0725 affects the Windows DHCP Server service, and doesn’t require authentication to be triggered. Therefore by successfully crafting specific DHCP datagrams, an attacker could exploit the vulnerability and run arbitrary privileged code on the DHCP server, which could in turn into a full AD domain compromise.
Chakra Scripting Engine Memory Corruption Vulnerabilities: ChakraCore (the Edge browser JavaScript engine) and Internet Explorer were found vulnerable to multiple use-after-free and type confusion vulnerabilities. By simply visiting a web page embedding an exploitation payload, a user can unwillingly allow an attacker to execute code with their level of privileges. The company’s patch addresses vulnerabilities with the following designations: CVE-2019-0912, CVE-2019-0913, CVE-2019-0914, CVE-2019-0915, CVE-2019-0916, CVE-2019-0917, CVE-2019-0922, CVE-2019-0923, CVE-2019-0924, CVE-2019-0925, CVE-2019-0927, CVE-2019-0933, CVE-2019-0937
Windows Kernel: This PT edition fixes several Windows kernel vulnerabilities, including a Win32k Elevation of Privilege vulnerability (CVE-2019-0892) and a Remote Code Execution vulnerability in GDI+ (CVE-2019-0903). Both components suffer from memory corruption bugs which are considered likely exploitable locally for elevating privileges. The GDI+ bug could also be triggered remotely by sharing a document via SMB, or over the web or via email. Other kernel patches (CVE-2019-0758, CVE-2019-0882, CVE-2019-0961, CVE-2019-0886) fix some information disclosure susceptible of helping defeating KASLR.
How is Sophos responding to these threats?
Here is a list of protection released by SophosLabs in response to this advisory to complement any existing protection and generic exploit mitigation capabilities in our products.
Important note: The proof-of-concept code provided with Microsoft advisories does not include active exploits, and as such is not applicable to Intercept X testing, which are marked as “N/V” (not validated). The IX ability to block the exploit depends on actual exploit weaponization approach which we won’t see until it’s spotted in the wild. The SAV and IPS detections developed for the PoCs do not guarantee interception of in-the-wild attacks
| CVE | SAV | IPS | Intercept-X |
| CVE-2019-0863 | Exp/20190863-A | N/V | N/V |
| CVE-2019-0938 | Exp/20190938-A | 9000919 | N/V |
| CVE-2019-0940 | Exp/20190940-A | 9000920 | N/V |
Additional IPS Signatures
Microsoft
| CVE | Sid |
| CVE-2019-0708 | 50137 (SFOS) 9000924 (CROS) |
| CVE-2019-0758 | 9000911 |
| CVE-2019-0882 | 9000912 |
| CVE-2019-0885 | 1060214041 |
| CVE-2019-0903 | 9000914 |
| CVE-2019-0884 | 9000913 |
| CVE-2019-0911 | 9000915 |
| CVE-2019-0918 | 9000916 |
| CVE-2019-0926 | 9000917 |
| CVE-2019-0930 | 9000918 |
Adobe
| CVE | Sid |
| CVE-2019-7142 | 48011 |
| CVE-2019-7759 | 49260 |
| CVE-2019-7764 | 49313 |
| CVE-2019-7766 | 49317 |
| CVE-2019-7771 | 44061 |
| CVE-2019-7779 | 49247 |
| CVE-2019-7784 | 42285 |
| CVE-2019-7794 | 1170412101 |
| CVE-2019-7796 | 3310706 |
| CVE-2019-7806 | 2200337 |
| CVE-2019-7820 | 40573 |
| CVE-2019-7826 | 40573 |
| CVE-2019-7837 | 37627 |
How long does it take to have Sophos detection in place?
We aim to add detection to critical issues based on the type and nature of the vulnerabilities as soon as possible. In many cases, existing detections will catch exploit attempts without the need for updates.
What if the vulnerability/0-day you’re looking for is not listed here?
If we haven’t released an update for a specific exploit, the most likely reason is that we did not receive the data that shows how the exploit works in the real world. As many of this month’s exploits were crafted in a lab and have not been seen in the wild, nobody has enough information (yet) about how criminals would, hypothetically, exploit any given vulnerability. If or when we receive information about real attacks, we will create new detections, as needed.
This story was modified on 22 May 2019 to add new Sid codes for IPS signatures developed to detect the so-called “BlueKeep” vulnerability affecting Remote Desktop Services (CVE-2019-0708)
Leave a Reply