April’s Patch Tuesday release from Microsoft includes fixes for 74 security vulnerabilities found in Windows and other Microsoft products. 16 of the bugs were labeled as critical fixes by Microsoft.
Simultaneously, Adobe published updates for its Flash plugin and for the Acrobat and Adobe Reader software, in addition to patches for the Shockwave player, InDesign, DreamWeaver, and several other enterprise applications. The fixes to Flash and Acrobat both resolve a number of serious bugs, some of which can result in the execution of arbitrary code on the victim’s computer if the victim views a maliciously crafted Flash app or opens a weaponized PDF document using one of the vulnerable versions of these tools. It’s possible that the Adobe bugs may be exploited on operating systems other than just Windows, such as MacOS, Chrome OS, or Linux. These Adobe applications are not updated through Microsoft’s Update mechanism and require users to visit Adobe’s website to download the updates.
A total of 13 of these new Microsoft bugs are elevation of privilege (EoP) flaws, a vulnerability class that allows an attacker with initial access to a system to gain more control over it. Two EoP flaws, patched during earlier Patch Tuesday releases (CVE-2019-0803 and CVE-2019-0859), have apparently been spotted being exploited in the wild according to Microsoft, which is why it is so important to install these updates as soon as possible.
Another 13 remote code execution vulnerabilities affect the two Microsoft web browsers, Edge and Internet Explorer.
It’s worth reminding readers that the availability of patches does not mean that your computer has installed them, yet. To find and download this month’s Cumulative Update patch yourself, search for the term “2019-04” at the Microsoft Update Catalog website.
Here are some details about the most notable vulnerabilities fixed in this month’s release:
Windows Virtual Store
CVE-2019-0730, CVE-2019-0731, CVE-2019-0796, CVE-2019-0805, CVE-2019-0836, CVE-2019-0732
As a result of a concentrated effort to uncover bugs in the Windows Virtual Store Driver (also known as LUA File Virtualization – luafv.sys), Microsoft fixed 6 bugs in this component.
The bugs exist in the programmatic interface between user programs and the high-privilege Windows Virtual Store driver, in code paths that are unreachable by network services, web browsers, or document readers. These bugs fall under the Elevation of Privilege classification.
Edge Web Browser
CVE-2019-0806, CVE-2019-0810, CVE-2019-0812, CVE-2019-0829, CVE-2019-0860, CVE-2019-0861
Now to the regularly scheduled batch of newly fixed security vulnerabilities in the JIT component of Edge’s JavaScript engine Chakra.
After many dozens of critical security bugs have been found in this same component, it seems that Microsoft’s decision to replace Edge’s internals with Chromium’s is a wise one, at least for the purposes of security.
A remote attacker, running a malicious website, could exploit any of these to gain control of a Windows machine unlucky enough to browse to it via Edge.
VBScript
CVE-2019-0739, CVE-2019-0752, CVE-2019-0753, CVE-2019-0793, CVE-2019-0794, CVE-2019-0862
Another vulnerability-prone engine receives 6 bug fixes.
These bugs are as risky to affected systems as any other browser vulnerability, but the good news is that on up-to-date Windows systems, VBScript is only supported by the deprecated Internet Explorer browser, and even then it’s blocked for Internet sites by default.
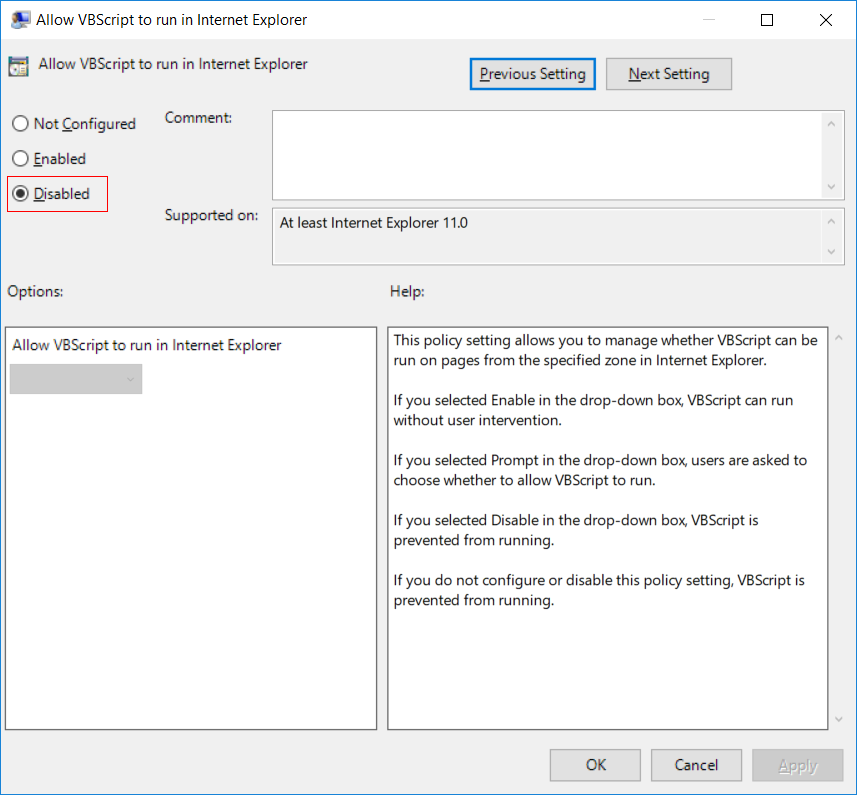
Users that did not go out of their way to enable VBScript support on their browser should not be concerned about getting compromised by these bugs. Users who did, well, you (or a network administrator) should really turn that off by toggling the Group Policy setting titled Allow VBScript to run in Internet Explorer to Disabled. You can find this policy item in the Group Policy tool (gpedit.msc) under Computer Configuration >> Administrative Templates >> Windows Components >> Internet Explorer >> Internet Control Panel >> Security Page >> Internet Zone
IOleCvt Interface
CVE-2019-0845
This extremely hard-to-exploit buffer overflow bug in the OlePrn.OleCvt ActiveX control probably should not bother anyone, and does not normally warrant a mention here – except for the fact it was found and reported to Microsoft by the SophosLabs Offensive Security Research team! Expect more in the future.
Sophos coverage
Sophos has released following detection to address the vulnerabilities mentioned above. Please note that additional vulnerabilities and corresponding detection may be released in the future.
|
CVE |
SAV |
IPS |
Intercept-X |
|
CVE-2019-0753 |
Exp/20190753-A |
2201101 |
N/V |
| CVE-2019-0793 | Exp/20190793-A |
2201102 |
N/V |
| CVE-2019-0803 | Exp/20190803-A |
N/A |
N/V |
| CVE-2019-0806 | Exp/20190806-A |
3310803 |
N/V |
| CVE-2019-0812 | Exp/20190812-A | 3310801 |
N/V |
| CVE-2019-0859 | Exp/20190859-A | N/A |
N/V |

Leave a Reply