Active adversaries are highly skilled cybercriminals. They use hands-on-keyboard and AI-assisted methods to circumvent preventative security controls and execute advanced multi-stage attacks.
Organizations need adaptive security controls designed to detect, investigate, and respond to the approaches commonly used by these sophisticated threat actors. Effective response to advanced threats requires a toolset that enables security operators to make data-driven decisions faster and execute tasks with speed and efficiency.
Sophos continuously leverages the threat intelligence and cybersecurity expertise from our Sophos X-Ops unit, as well as telemetry from Sophos’ and third-party security solutions, to provide the strongest protection, detection, and response to the most advanced attacks. We are always innovating, and the latest enhancements to the Sophos Extended Detection and Response (XDR) platform provide even greater power to defend against active adversaries.
Enhanced Sophos XDR detections
Check out some of our latest enhancements in this quick demo video:
Configurable suppression rules
Security operators have greater control over the detections generated by the Sophos XDR platform using an intuitive suppression wizard, enabling analysts to focus on the most important detections and cases by suppressing confirmed-benign events. Granular rules can be created based on specific attributes including severity, detection type, MITRE ATT&CK details, and more.
Comprehensive detection summaries
Security operators need to make decisions and execute tasks at speed, so it’s crucial that threat alerts are immediately comprehensible to analysts of all skill levels. Sophos XDR detections now include “natural language” descriptions to help accelerate investigation and response.
Streamlined SophosLabs Intelix integration
Detections generated by Sophos Endpoint are now automatically sent to SophosLabs Intelix for threat classification and analysis. Detection details are now enriched with high-fidelity threat intelligence with no need to manually submit to SophosLabs.
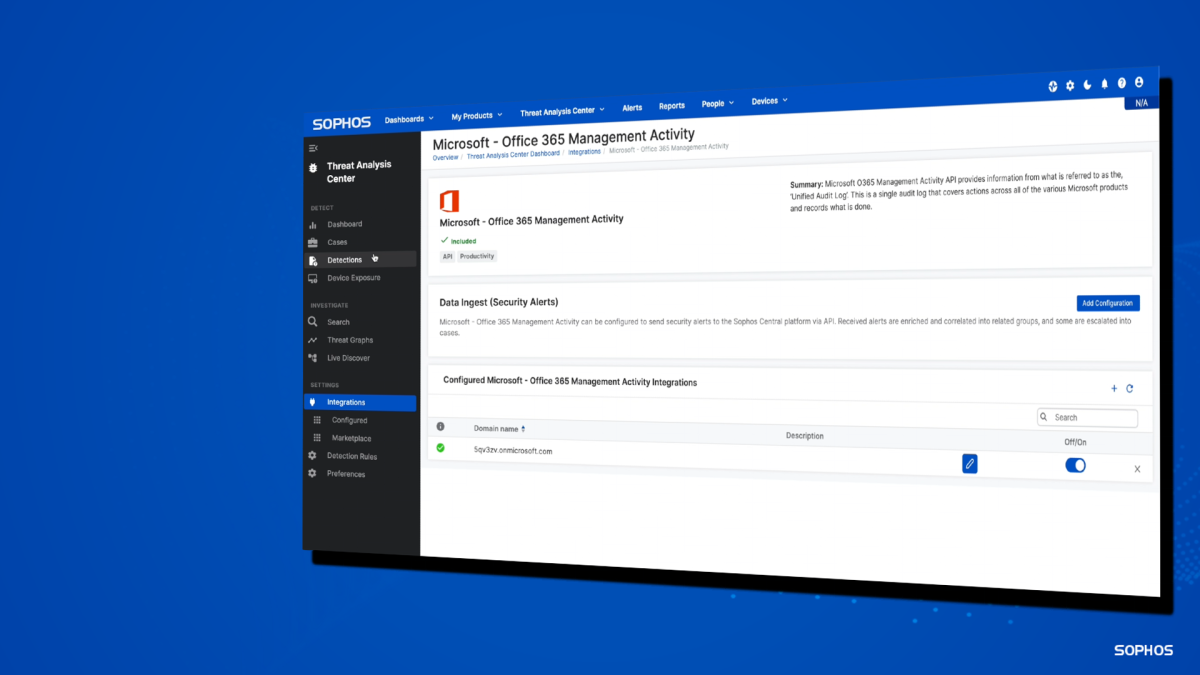
Enhanced Microsoft 365 detections
Sophos XDR collects and analyzes comprehensive audit log data from Microsoft 365 and uses proprietary rules to identify more threats than Microsoft security tools can on their own. The latest Microsoft “platform detections” in Sophos XDR focus on identifying compromised accounts and Business Email Compromise.
The “Microsoft Office 365 Management Activity API” integration is included with Sophos XDR at no additional cost.
Sophos XDR Public APIs
Extending our open ecosystem approach, we’ve introduced two new APIs to enable organizations to integrate Sophos XDR data seamlessly into existing security operations tools and workflows.
Organizations with established security operations programs can use these new APIs to surface threat detections and case investigation details from the Sophos XDR platform in their security information and event management (SIEM), professional services automation (PSA), and IT service management (ITSM) tools, providing the flexibility to leverage these existing investments.
- Accelerate investigation and response – enable automated workflows that leverage Sophos XDR detections and case details
- Centralize analysis of security telemetry – correlate Sophos XDR detections with alerts and telemetry from other data sources
- Enrich with third-party threat intelligence – augment Sophos XDR detections with additional threat intelligence for added context
Learn more in our documentation: Detections API | Cases API
Increase multi-dimensional visibility with technology integrations
Active adversaries execute attacks that cross multiple domains across the victim’s environment – the full scope of which cannot be detected by a single point product. Telemetry from multiple sources is needed to provide a more complete view of an active adversary’s activity at each stage of an attack.
The Sophos XDR platform collects, correlates, and analyzes data from a wide range of event sources, while automated actions and optimized workflows allow analysts to detect, investigate, and respond to active adversaries at speed across all key attack surfaces.
We are constantly expanding our expansive partner ecosystem with additional turnkey integrations with endpoint, firewall, network, email, cloud, identity, productivity, and backup solutions.
New integrations available for Sophos XDR and Sophos MDR customers include the following:
 |
 |
 |
 |
| Forcepoint Next-Gen Firewall |
F5 BIG IP Application Security Manager (ASM) |
Cisco Umbrella | Cisco Identity Services Engine (ISE) |
| Integration Pack: Firewall |
Integration Pack: Firewall |
Integration Pack: Network |
Integration Pack: Identity |
| Learn more | Learn more | Learn more | Coming soon |
Explore our current range of third-party integrations on the Sophos Marketplace.
Microsoft Graph security integration (Version 2)
By ingesting, correlating, and analyzing telemetry via the Microsoft Graph security and Microsoft Office 365 Management Activity APIs, the Sophos platform uses advanced proprietary threat detection rules to identify threats that could otherwise be missed. These turnkey Microsoft integrations are included with Sophos XDR and Sophos MDR subscriptions at no additional cost, and over 20,000 customers are already using them to extend visibility and protection across their IT environments.
In July, we are releasing a new version of our Microsoft Graph security integration. The new version, called “Microsoft Graph security API (Alerts v2)”, provides additional information from a broad range of Microsoft security solutions that analysts can use to accelerate detection, investigation, and response. And yes, the new version will still be included in the standard price of Sophos XDR and Sophos MDR!
Quickly identify vulnerable endpoints and servers
Identifying devices that are potentially exposed to threats is critical for managing cybersecurity risk. We’ve recently introduced a new Device Exposure dashboard in the Sophos Central console that provides Sophos XDR and Sophos MDR with a clear overview of endpoint and server devices missing critical operating system updates. The visualization highlights the time elapsed since the last OS updates were applied, with one-click access to customizable queries for further details.
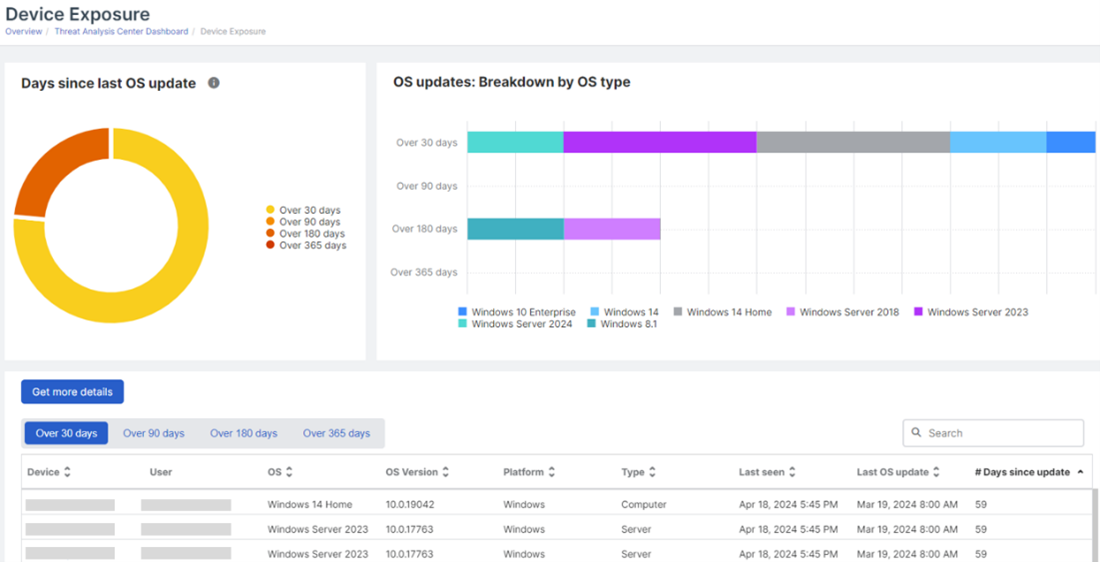
Learn more about the new Device Exposure dashboard
Vulnerability management delivered as a managed service
The modern attack surface continues to grow beyond the borders of traditional on-premises IT, and most organizations now have a significant number of internet-facing assets they don’t even realize they own, let alone understand whether they are vulnerable to attack. With our latest service offering – Sophos Managed Risk, powered by Tenable – our dedicated team of experts helps eliminate blind spots in your external attack surface and prioritizes remediation efforts based on the exposures that pose the highest risk to your organization.
Recognized by industry experts and customers
Sophos XDR and Sophos MDR continue to garner high praise from customers and industry experts for superior detection, investigation, and response capabilities.
Recent proof points include:
- A Leader in the 2024 IDC MarketScape for Worldwide Managed Detection and Response (MDR)
- A Leader in Frost & Sullivan’s 2024 Frost Radar™ for Global Managed Detection and Response
- The only vendor named a Gartner Customers’ Choice in Endpoint Protection Platforms, Managed Detection & Response Services, Network Firewalls, and Mobile Threat Defense
- The only vendor named a Leader in EPP, EDR, MDR, XDR, and Firewall in the G2 Winter 2024 Reports
- A Leader for the 14th consecutive time in the Gartner® Magic Quadrant™ for Endpoint Protection Platforms
Elevate your defenses against active adversaries
To learn more and explore how Sophos XDR can help your organization better defend against active adversaries, speak with a Sophos adviser or your Sophos partner today.
You can also take it for a test drive in your own environment with a no-obligation, 30-day free trial – available from our website or (for existing Sophos customers) directly within the Sophos Central console in just a couple of clicks.