Microsoft on Tuesday released patches for 83 vulnerabilities in six Microsoft product families. This includes 15 Critical-class issues affecting Azure, Office, SharePoint, and Windows. Once again the majority of CVEs affect Windows; the operating system takes the lion’s share of the CVEs with 68, followed by five for Office and four for SharePoint. Azure admins get some respite this month with just three patches for that platform (including one for Service Fabric), and Visual Studio and .NET together account for another three.
One vulnerability (CVE-2022-41043), an information disclosure bug in Office, has been publicly disclosed. Another (CVE-2022-41033), an elevation-of-privilege flaw in the COM+ Event System Service, has been exploited. The remaining issues remain undisclosed and unexploited, according to Microsoft. Notable by their absence are the two high-profile Exchange Server vulnerabilities (CVE-2022-41040, CVE-2022-41082), both of which were in the news last week. Since the public disclosure of the two issues, Microsoft has issued several rounds of mitigations and guidance for what appears to be a close variant of the legendary ProxyShell attack.
Elsewhere in the release, an unusual Critical-class spoofing vuln (CVE-2022-34689) appears to have been disclosed to Microsoft by two somewhat unusual sources: the UK National Cyber Security Centre (NCSC) and the US National Security Agency (NSA). Exploitation of this bug is described as more likely, and it’s some fairly exciting stuff: According to Microsoft, an attacker could manipulate an existing public x.509 certificate to spoof their identify and perform actions such as authentication or code signing as the targeted certificate.
By the Numbers
- Total Microsoft CVEs: 83
- Total advisories shipping in update: 0
- Publicly disclosed: 1
- Exploitation detected: 1
- Exploitation more likely in latest version: 13
- Exploitation more likely in older versions: 14
- Severity
- Critical: 15
- Important: 68
- Moderate: 0
- Low: 0
- Impact
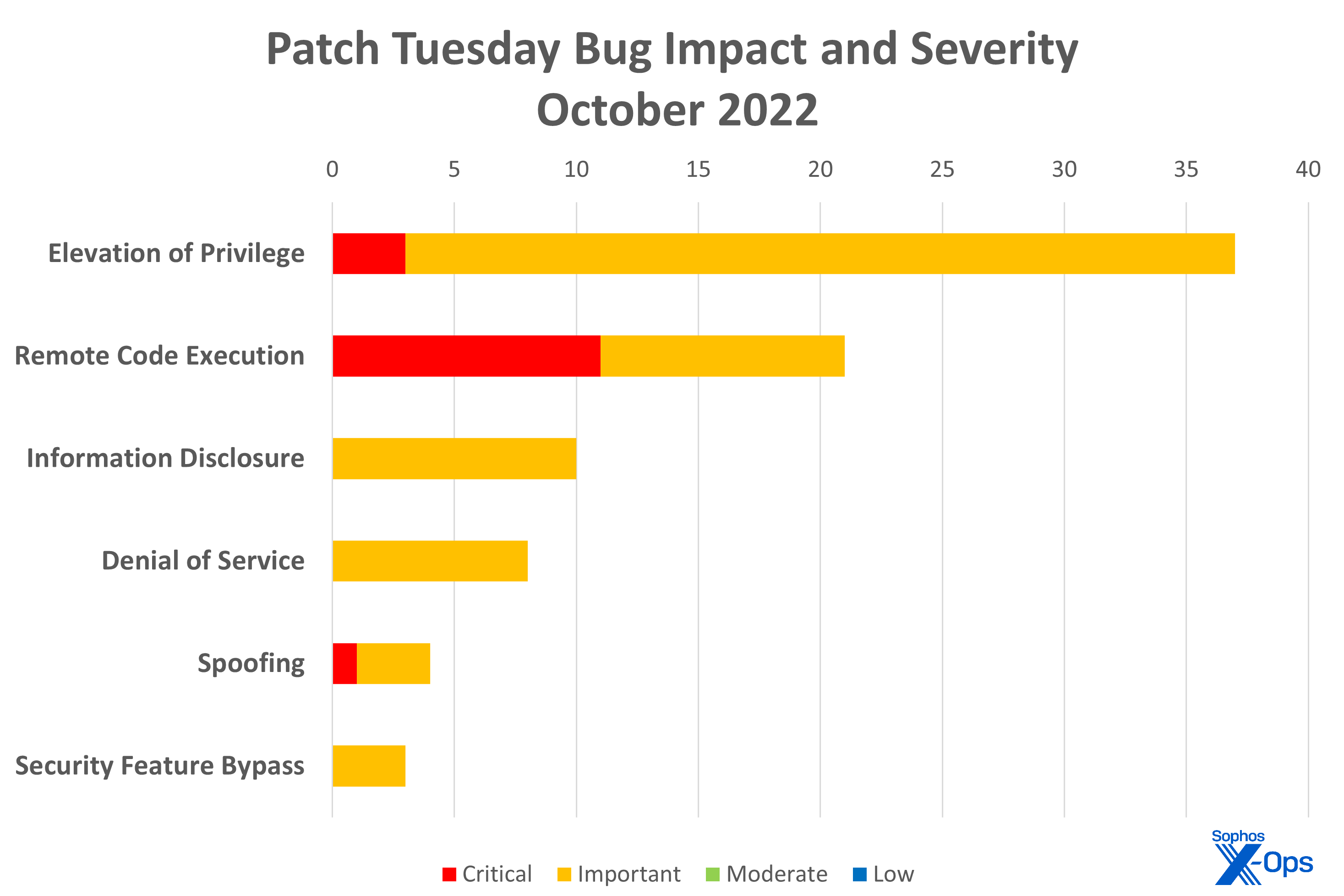
- Elevation of Privilege: 37
- Remote Code Execution: 21
- Information Disclosure: 10
- Denial of Service: 8
- Spoofing: 4
- Security Feature Bypass: 3
Figure 1: Far more elevation-of-privilege issues addressed this month, but fully half the remote-code execution issues are Critical-class
- Products:
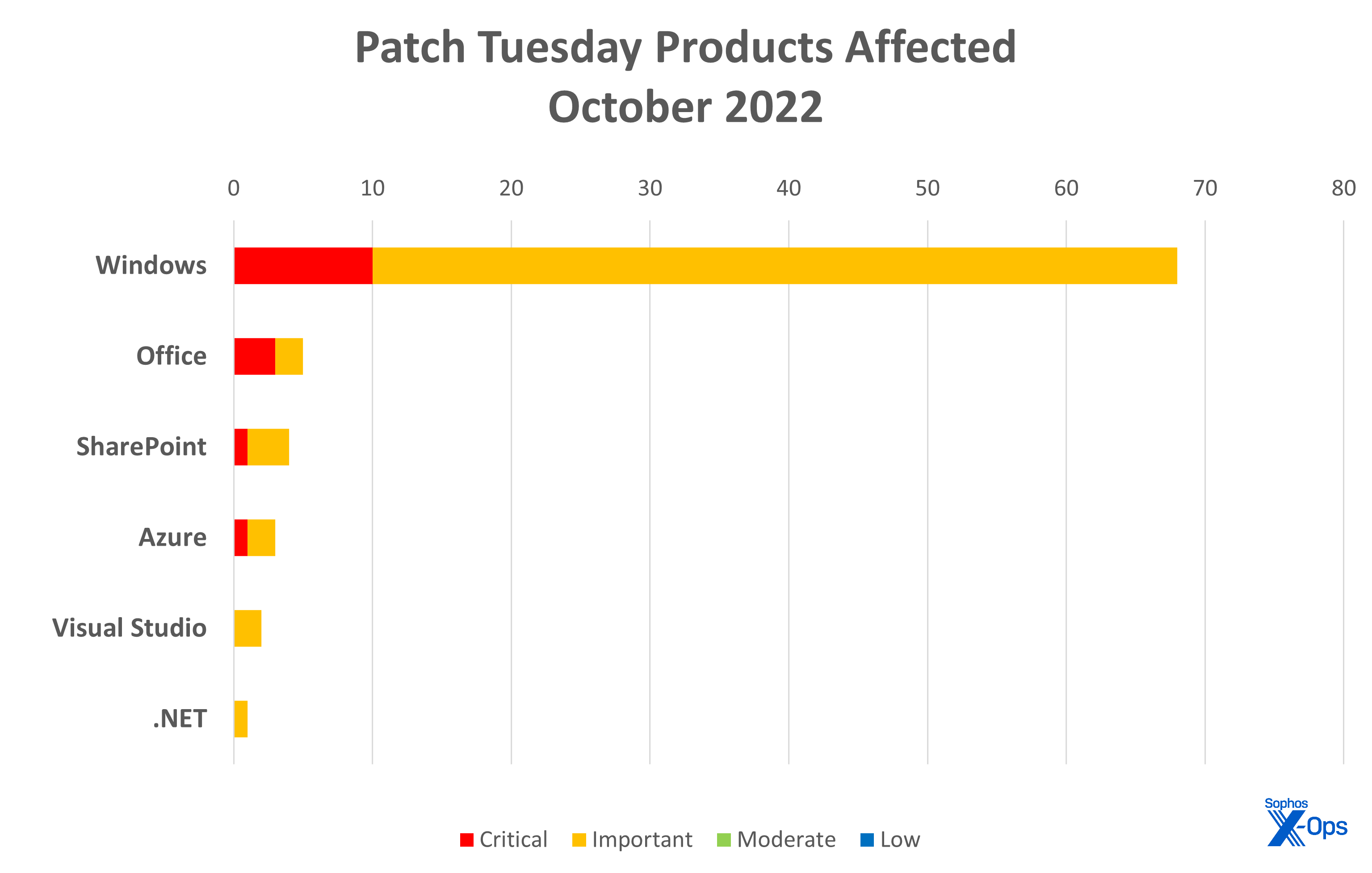
- Microsoft Windows: 68
- Microsoft Office: 5
- SharePoint: 4
- Azure (including Service Fabric): 3
- Visual Studio: 2
- .NET: 1
Figure 2: Windows, Windows, Windows
Notable Vulnerabilities
Not Present: Exchange
System administrators should continue to monitor Microsoft communications for changes and updates regarding the two active Exchange Server vulnerabilities. Sophos will continue to add protections as those become available.
CVE-2022-22035, CVE-2022-24504, CVE-2022-30198, CVE-2022-33634, CVE-2022-38000, CVE-2022-38047, CVE-2022-41081: Windows Point-to-Point Tunneling Protocol Remote Code Execution Vulnerabilities
A collection of no fewer than seven Critical remote code execution bugs in the Windows Point-to-Point Protocol (PPTP). Microsoft assesses these are all less likely to be exploited, and there doesn’t look to be any in-the-wild exploitation at the time of going to press. According to the CVSS metric, the attack complexity is high; an attacker would have to craft a malicious PPTP packet, send it to a PPTP server, and win a race condition in order to obtain remote code execution.
CVE-2022-38048, CVE-2022-38049, CVE-2022-41031: Office/Word Remote Code Execution Vulnerabilities
Several Critical Office vulnerabilities this month, which could lead to remote code execution if successfully exploited. It’s worth noting that with all three of these bugs, the attack vector itself is local, and user interaction is required. An attacker would need to craft a file designed to exploit the vulnerability and send the file to a victim – so there’d probably be an element of social engineering involved as well. While the bugs are rated Critical, there are some upsides: Microsoft assesses exploitation as less likely in both older and newer product versions, and the Preview Pane isn’t an attack vector.
CVE-2022-37987 and CVE-2022-37989: Windows Client Server Run-time Subsystem (CSRSS) Elevation of Privilege Vulnerabilities
A brace of Important privilege escalation vulnerabilities in the Windows Client Server Run-time Subsystem (CSRSS), both of which are rated as more likely to be exploited in both older and newer versions and could result in an attacker gaining SYSTEM privileges. As with most of the bugs so far this month, there’s no evidence they’ve been exploited in the wild or publicly disclosed.
CVE-2022-38022: Windows Kernel Elevation of Privilege Vulnerability
An odd little item with a very low (3.1) CVSS, this vuln is interesting not because what it does is so hilariously specific – as per Microsoft, the ability to delete an empty folder on a file system – but because it’s a reminder that in a world of chained attacks, a tiny flaw such as this should be patched because it can be part of a bigger attack sequence.
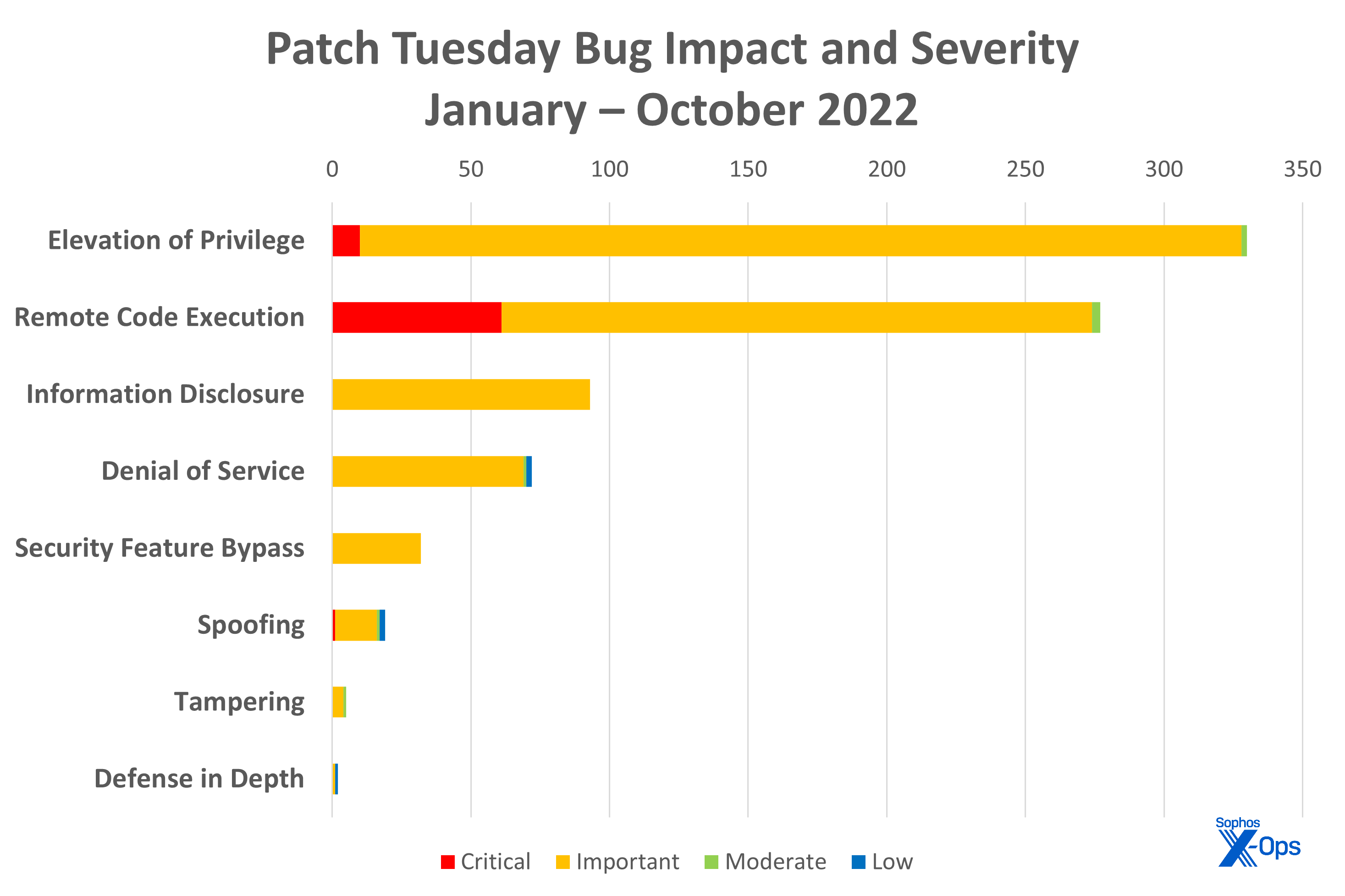
Figure 3: Elevation of privilege continues to dominate the patches released in 2022
Sophos protections
| CVE | Sophos Intercept X / Endpoint IPS | Sophos XGS Firewall |
| CVE-2022-37970 | Exp/2237970-A | |
| CVE-2022-37974 | 2307765, 2307767 | 2307765, 2307767 |
| CVE-2022-37989 | Exp/2237989-A | |
| CVE-2022-38050 | Exp/2238050-A | |
| CVE-2022-38053 | 2307772 | 2307772 |
(Ever wondered about behavior names, by the way? Sophos’ naming conventions line up with the MITRE ATT&CK framework. Details are available elsewhere on our site.)
As you can every month, if you don’t want to wait for your system to pull down the updates itself, you can download them manually from the Windows Update Catalog website. Run the winver.exe tool to determine which build of Windows 10 or 11 you’re running, then download the Cumulative Update package for your particular system’s architecture and build number.

Leave a Reply