Frequently asked questions about Sophos ZTNA
What is Zero Trust and ZTNA all about?
Zero Trust is exactly what it says on the tin: “Trust Nothing, Verify Everything.” This is a different approach from the old mindset of once something is on the network, it is “trusted.”
Zero Trust requires devices and users to prove they are trustworthy before providing access. This means verifying their identity and validating device health before providing access to corporate applications and data. It’s actually a very good way to manage network access – and seamless and simple too.
Please review this article for a great overview of Zero Trust Network Access.
What are the benefits of ZTNA compared to remote-access VPN?
ZTNA offers a number of added benefits that make it a very attractive solution to replace VPN for connecting remote workers and users to important applications and data:
- Better security: ZTNA only connects users to a specific application, not the whole network like VPN. This removes implicit trust and provides micro-segmentation of applications and data, ensuring threats can’t move laterally across the network. It also removes a growing attack vector where ransomware attackers are exploiting VPN clients to get a foothold on networks. ZTNA also incorporates device health into access policies: something VPN can’t do.
- Easier to enroll staff and stand up new applications: ZTNA is much easier to roll out and enroll new employees, especially if they are working remotely. VPN is more challenging and difficult to set up and deploy. Growing or dynamic organizations will greatly appreciate the added efficiency of ZTNA.
- Transparent to users: ZTNA offers “just works” transparency to users with frictionless connection management. VPN can be difficult and prone to initiating support calls.
But ZTNA isn’t just limited to secure access for remote workers; it works equally well both on and off the network, which is another advantage over VPN.
Download this white paper on the Six Advantages of ZTNA for deeper insights.
What does Sophos ZTNA include?
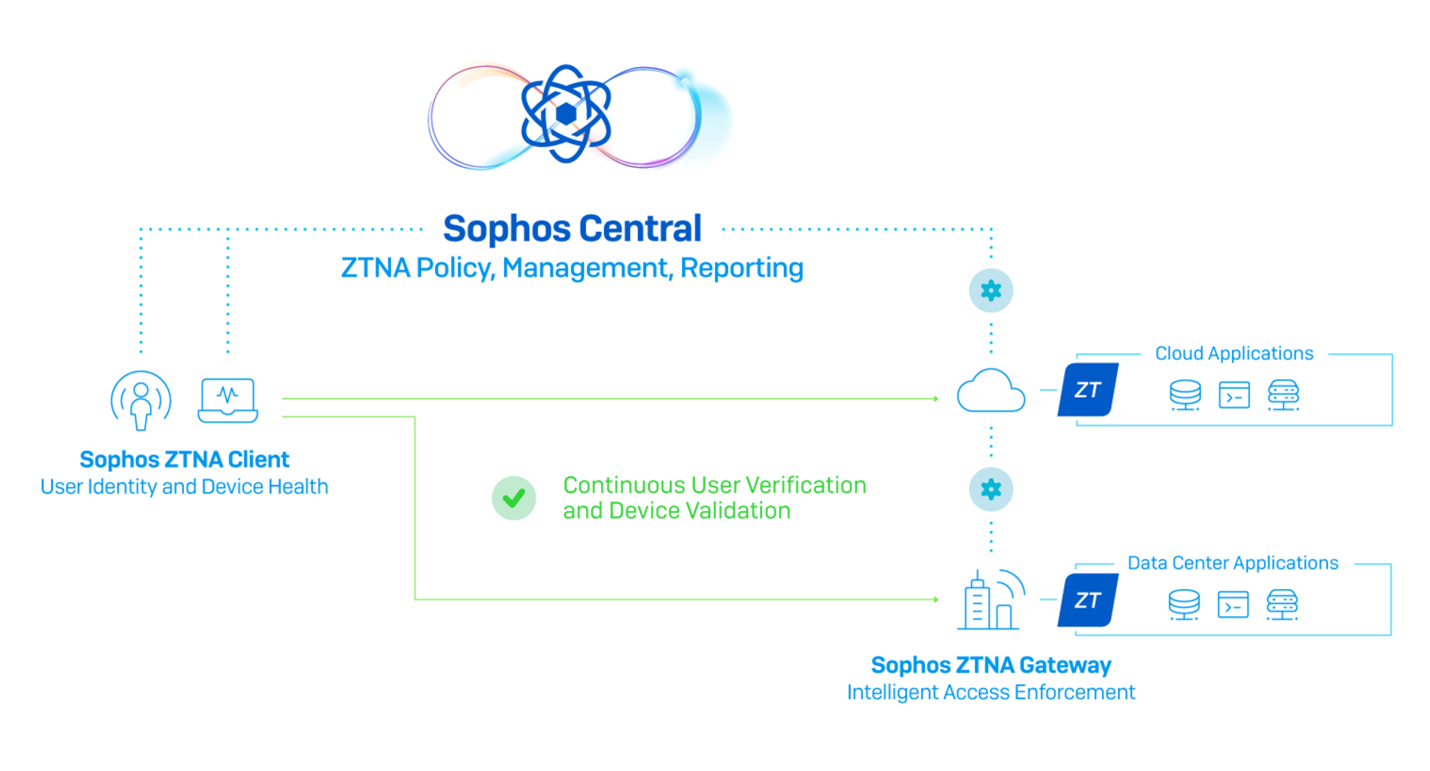
Sophos ZTNA is a new cloud-delivered, cloud-managed product to easily and transparently secure important networked applications with granular controls.
Sophos ZNTA consists of three components:
- Sophos Central – provides the ultimate cloud management and reporting solution for all Sophos products, including Sophos ZTNA. Sophos ZTNA is fully cloud-enabled, with Sophos Central providing easy deployment, granular policy management, and insightful reporting from the cloud.
- Sophos ZTNA Gateway – will come as a virtual appliance for VMware (on-prem) and AWS (public cloud) to secure networked applications. Additional platform support will follow.
- Sophos ZTNA Client – a single agent solution integrated with Intercept X provides easy deployment and Synchronized Security support for device health. While it offers tremendous benefits for customers using Intercept X, it works well with any endpoint product. It will initially support Windows, followed by macOS, Linux, and mobile device platforms as well.
Get the Sophos ZTNA datasheet for full details.
When will Sophos ZTNA be available?
The EAP Phase 2 for the release candidate version of ZTNA is underway, with general availability planned for January, 2022.
Which types of applications are ideal for ZTNA?
Sophos ZTNA can provide secure connectivity for any networked application hosted on your on-premise network, in your public cloud, or any other hosting site. Everything from RDP access to network file shares to applications like Jira, wikis, source code repositories, support and ticketing apps – anything you host.
ZTNA does not control access to public SaaS applications like Salesforce.com or Office365, which are public internet facing applications servicing many customers by design. Secure access to these applications is provided by the SaaS vendor and the application, and is often further enhanced through multi-factor authentication.
Which client, gateway, and identity platforms will be supported?
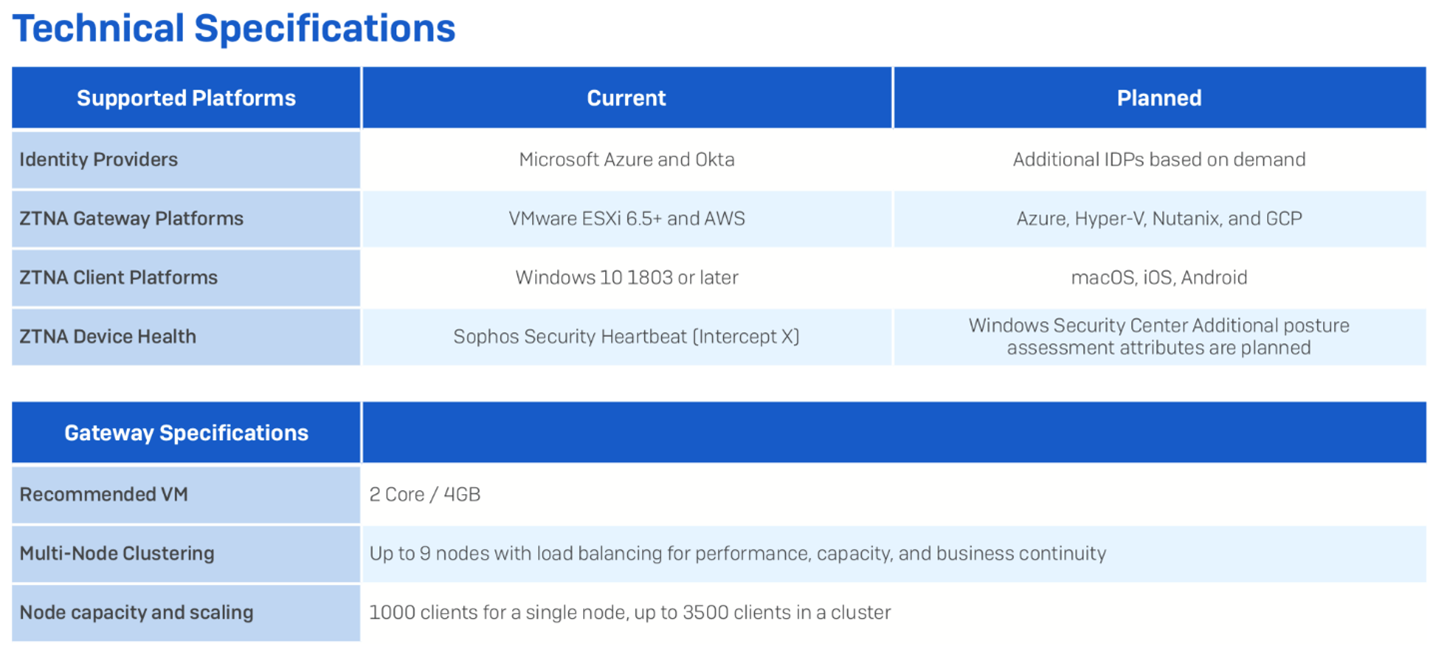
Get the Sophos ZTNA datasheet for full details.
Also check out the Sophos ZTNA Deployment Checklist for a list of pre-requisites for deploying ZTNA.
Is on-premises Active Directory supported?
You will need to connect and sync your on-premise AD to Azure or Okta to support Sophos ZTNA. If you’re not already, consider using Azure AD Connect.
Is ZTNA a stand-alone product or does it require another Sophos product?
Sophos ZTNA is a stand-alone product and does not require any other Sophos products. It is managed by Sophos Central, which is free, and obviously offers a ton of benefits when customers have other Sophos products. It can easily deploy as a single-agent with Intercept X, but Intercept X is not a requirement. Sophos ZTNA can work alongside any vendor’s desktop AV or firewall.
How will Sophos ZTNA client deployment work?
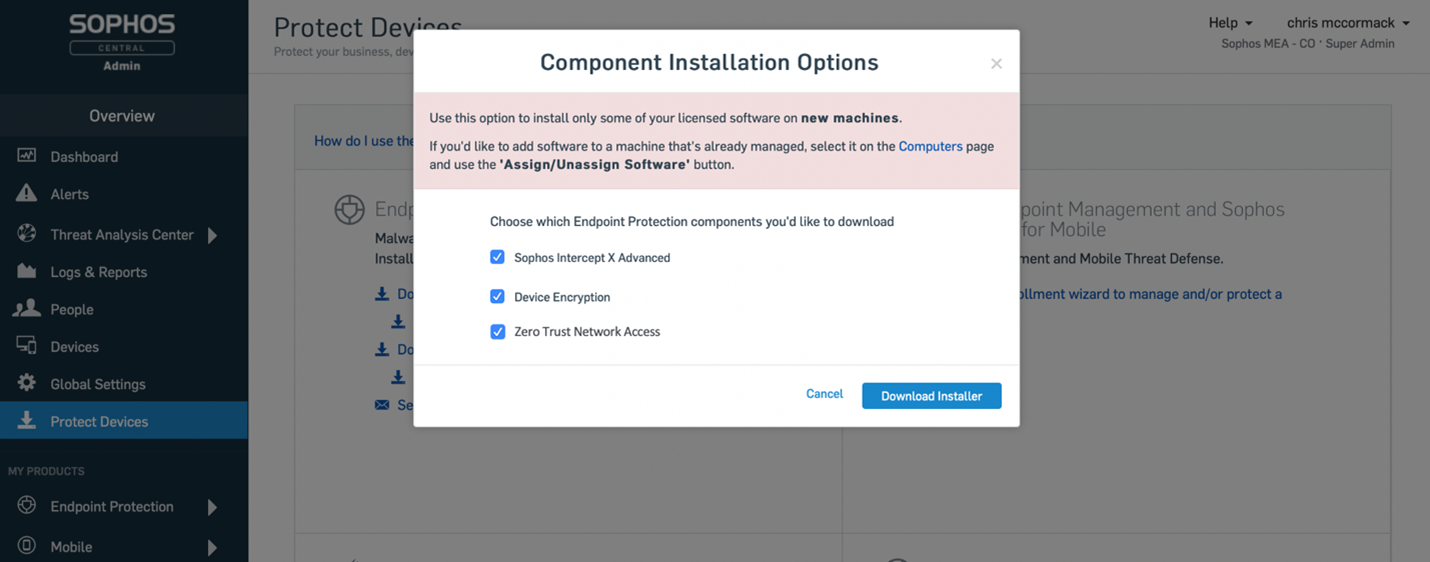
Sophos ZTNA is an easy-to-deploy option as a single client with Intercept X and Device Encryption when protecting devices from Sophos Central. As shown below…
Deploying the ZTNA client with another endpoint agent is also straightforward.
Does ZTNA integrate with Sophos Firewall and Intercept X?
Sophos ZTNA should be included with every Sophos Intercept X and Firewall sale where a customer has remote workers. Sophos ZTNA takes full advantage of Security Heartbeat to assess device health, which can be used in ZTNA policies.
As mentioned above, deployment of the ZTNA client can easily happen as part of an Intercept X rollout: it’s as simple as checking a box. Of course, Sophos ZTNA can also work perfectly with other vendor desktop AV or firewall products, but it will work better together with other Sophos products such as Sophos Firewall and Intercept X.
How does licensing and pricing work?
Sophos ZTNA is licensed on a per-user basis like our endpoint products. And it is not per-device: just per-user. So if a user has three devices, they only require one license.
Customers can deploy as many ZTNA gateways as they need to protect all their apps. There is no charge for the gateway or for Central management.
What makes Sophos ZTNA better than other ZTNA solutions?
Sophos ZTNA is the only ZTNA solution that is tightly integrated with a next-gen endpoint product: Intercept X. This has tremendous benefits that no other vendor can offer:
- Better end-to-end protection: With ZTNA and the world’s best next-gen endpoint protection working together, they can provide the best protection for user identity, device health, applications, segmentation, and prevent attacks from getting onto networks via remote systems.
- One client, one console, one vendor: This is something many organizations will appreciate – being able to reduce client, console, and vendor count to consolidate and make things easier.
How does ZTNA compare to…
Duo (or MFA)?
Duo is an identity technology provider focused on multi-factor authentication (MFA) to help users verify their identity. Identity and MFA – and thus Duo – are parts of a ZTNA solution. ZTNA also verifies device health. Sophos ZTNA will initially support Azure MFA and any identity provider that integrates with Azure. including Duo and other MFA solutions as well.
NAC?
NAC and ZTNA technologies may sound similar as they are both about providing access, but that’s where the similarities end. Network Access Control (NAC) is concerned about controlling physical access to a local on-premise network. ZTNA is concerned with controlling access to data and specific network applications regardless of which network they are on.
VPN?
While remote-access VPN has served us well, ZTNA has a number of benefits when compared to VPN as outlined above. Of course there will be some situations where VPN continues to be a good solution… where a relatively small number of people (e.g. the IT department) need broad access to network applications and services to manage them.
And of course, VPN will still be instrumental for site-to-site connectivity. But for most organizations’ users, ZTNA can replace remote-access VPN to provide a better, more granular security solution while being more transparent and easier for users.
Firewalls?
ZTNA is complimentary to a firewall just like VPN is complimentary to a firewall. Of course, the firewall still plays a critically important role in protecting corporate network and data center assets from attacks, threats, and unauthorized access. ZTNA bolsters a firewall by adding granular controls and security for networked applications in the cloud or on-premise.
WAF?
WAF and ZTNA are designed to protect different types of applications from different types of users. WAF is designed to protect and secure public-facing applications by providing firewall, threat detection, and other hardening like SQL injection attack defenses. ZTNA is designed to control access by staff to internal applications. It is not designed to provide public access; in fact, it is designed to ensure public users cannot access ZTNA protected apps.
Sophos Synchronized Security?
ZTNA and Sophos Synchronized Security are both conceptually similar in that they both can use device health to determine network access privileges. In fact, Sophos ZTNA uses Security Heartbeat as a key component in assessing device health. If a user has a device with a red Heartbeat, their application access can be limited through policy, just as their network access can be limited on the firewall. However, ZTNA goes further than Synchronized Security by also integrating user identity verification. ZTNA is also more about controlling privilege and access to applications while Synchronized Security is more about automated response to threats and preventing threats from moving or stealing data.
SASE?
SASE (pronounced “sassy”) or Secure Access Service Edge, is about the cloud delivery of networking and security and includes many components such as firewalls, SD-WAN, secure web gateways, CASB, and ZTNA designed to secure any user, on any network, anywhere through the cloud. So as you can see, ZTNA is a key component of SASE and will be an essential part of our overall SASE strategy.
To learn more about Sophos ZTNA and sign up for the early-access program, visit our ZTNA website.

Leave a Reply