Thanks to Simon Porter of SophosLabs for his help with this article.
Ransomware still hogs the “malware attack” headlines these days, for obvious reasons.
But there are still plenty of other malware families out there to worry you, including some that go after data you probably never thought crooks would care about.
For example, just under 18 months ago, our researchers looked into a malware strain they dubbed AdKoob (koob is book backwards), which featured code that tried to sneak into your Facebook acount to peek at how you were spending your online ad money.
As curious as this sounds, don’t forget that:
- Any data-grabbing malware means you have suffered a breach. If any of that data relates to your customers, you’re left with a lot of explaining to do, including, “What else did these guys do while they were inside?”
- Operational data about your business has value to the crooks. That data can be used or sold on for use in further attacks, giving the crooks an intimate and believable pretext to contact you or your customers in future.
- This might be the tip of the iceberg. If the same stolen password or credentials could also be used to buy ads, to read your Facebook contacts, or to mess up your on online presence, then looking at your ad data might merely be a test for whether to press on with the attack.
Well, AdKoob variants have made a return in recent weeks, so the crooks still seem to have a use for them.
We wrote up a detailed analysis of its behaviour back in 2018, and while a lot of the malware code looks the same, some of the details have changed, including what you’ll see if you receive one of these files.
![]()
Most of the samples pretend to be PDF-related, and launch an installer with a name like pdfreader2019 Setup that, unsurprisingly, installs an app called pdfreader2019.
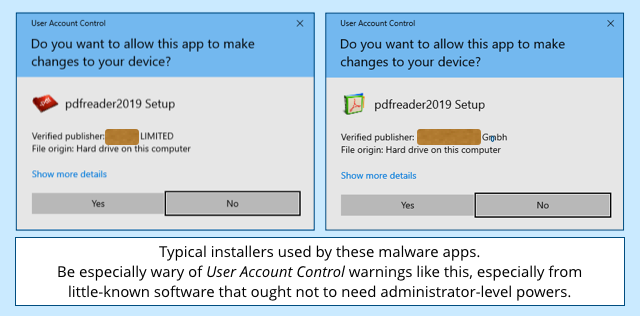
Note that this malware triggers a User Account Control (UAC) that asks you to “allow this app to access your device.”
That’s shorthand for “this software wants to access parts of your system that aren’t strictly necessary to install a vanilla app, so you need to give it permission to perform actions that would normally need an Adminstrator login.”
Malware that doesn’t trigger a UAC pop-up is dangerous enough on its own – typically, it can read and modify all your files right away – but malware that gets “access your device” powers can do much more, including installing background services that keep running even after you log out, and spying on other users as well as on you.
In other words, the absence of a UAC prompt doesn’t mean that you aren’t dealing with malware…
…but the presence of a UAC warning means that if what you are installing turns out to be malware, you just made a bad thing much worse.
Many of the recent samples are digitally signed to give them a veneer of authenticity. (We’ve blanked out the names of the companies that own the certificates used for signing – we don’t want to suggest that they were directly involved in creating these malware executables.)
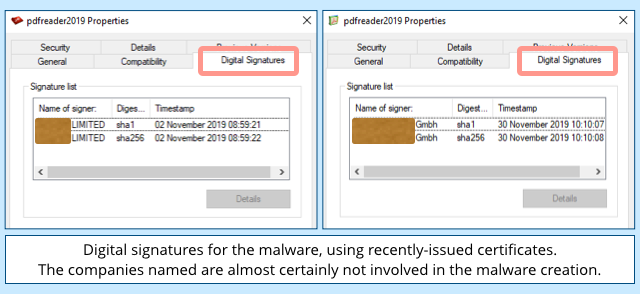
Sadly, digital certificates for signing Windows EXE files aren’t terribly difficult for crooks to acquire, so in this case, as the old joke goes, the certificates aren’t worth the paper they’re not printed on.
There are several approaches the crooks can take to get their hands on digital certificates in other people’s names, such as:
- Steal a certificate by hacking into a company server. Like Bitcoin wallets and customer databases, code signing certificates are just computer files that can be copied.
- Find a certificate that was accidentally included in a public software upload. Many software repositories, such as GitHub, now scan through uploads to look for files that should have been excluded, but it’s easy for a careless developer to upload more than was intended.
- Pretend to represent a company and buy a certificate in its name. Crooks can look through company registration websites to find small businesses whose names they can assume, and then talk a certificate issuer into believing they are the technical contact for the business.
As we mentioned above, one of the tricks up this malware’s sleeve is to dig into your browser’s database of cookies to look for authentication tokens – basically, short-term web passwords – that can be used to do Facebook lookups to reveal your ad spending.
Quite what the crooks do with this information, we can’t tell you – for all we know, the ad-spend lookup might merely be a way of verifying that the authentication token is valid, ready for worse to come later on.
However, and intriguingly, what we do know is that some of the samples of this malware were signed with a certificate that appeared to belong to a company associated with adware.
Indeed, that certificate had also been used to sign adware.
Adware isn’t strictly malware, but most people want to keep it off their computers anyway, because it goes out of its way to foist ads on them that they don’t want, and to track the sort of ads they’re seeing from other sources.
You can imagine how a company like that might be very interested indeed in sniffing out what ad money you are spending, and what you’re spending it on.
What to do?
- Watch out for emails or websites that urge you to install “a new document reader or video viewer” to display their content. If you genuinely need new software to view a file you’ve just received, do your own search and make your own choice of which app to install. Never install apps just because someone else told you to.
- Be suspicious if apps pop up User Acess Control warnings asking for powers you don’t think they need. Malware is dangerous enough without “access your device” powers, so don’t make things even easier for the crooks by inviting them in as Administrators.
- Log out of websites and online services when you aren’t using them. Malware can’t steal authentication tokens that aren’t there, so don’t make it easier for the crooks by leaving login tokens around when they aren’t needed.
- Guard your cryptographic signing certificates. If you’re a developer and you let your code signing certificates fall into the hands of crooks, you’ve become part of the problem, not the solution.
The good news is that this malware isn’t likely to get onto your computer without your help, so be conservative about the apps you install!

Anonymous
you have “rearsearchers”? or is that a joke?
Paul Ducklin
Fixed, thanks!
Steve
Oooh, and a wicked one at that! Good for a grin though.