By Pankaj Kohli
On the heels of the recent discovery of fake banking apps on Google Play, SophosLabs has discovered more Trojan apps on the official Android app marketplace.
These malware apps are more narrowly geographically focused, targeting victims in India. We recently found 12 malicious apps that collected users’ Internet banking credentials and credit card details, some of which have been available for download for, in some cases, more than two years, and had been installed by thousands of people. The campaign has evolved in that time; In the initial stages, it targeted only 3 large banks in India. Later iterations adopted long lists of national and regional banks and financial institutions from across India.
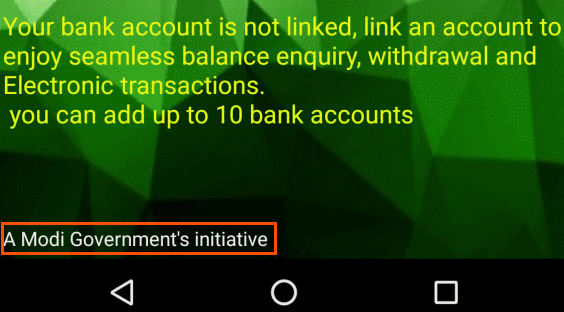
Some of these disguised themselves as Internet banking apps or electronic wallets, appearing to mimic the names or graphic design specifications of existing apps. Several others claimed to provide a unique (and somewhat bizarre) service that promises to withdraw money from your accounts and then deliver the cash right to the user’s doorstep. It probably did deliver cash to someone, but the recipient probably wasn’t the victim.
The malware author(s) responsible for these apps have published at least 12 different apps since May 2016. All the apps from this developer share a similar user interface, a similar code base, and all of them send the leaked information to the same command-and-control server, which suggests a single threat actor or a group behind the campaign.
Some of these apps were identical in every way to others but were published using different package names, which allows the creator(s) to upload them multiple times to Google Play.
Bank App Malware Modus Operandi
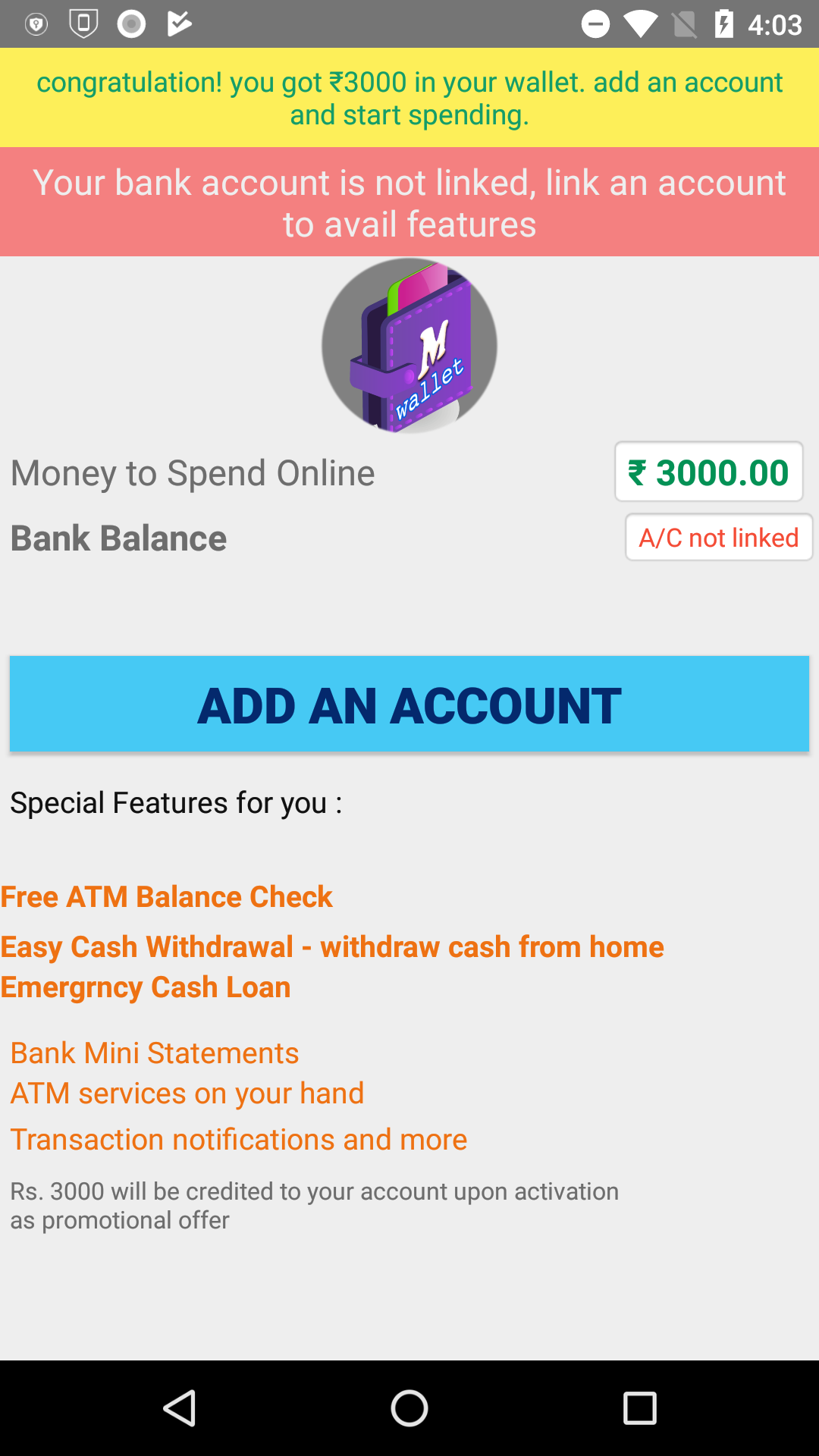
Many of these apps lured victims into downloading and using them by promising rewards such as cash back on purchases, free mobile data, or interest-free loans. Nobody got any rewards.
The most outlandish and hard-to-believe-anyone-would-fall-for-this scam operated by this crew claimed that their app offered, as a premium for its most valued customers, something called “e-ATM” service. I kid you not, this app promised to send a courier to an ATM and, using the credentials you provide, withdraw money (from your account) and deliver it to you.
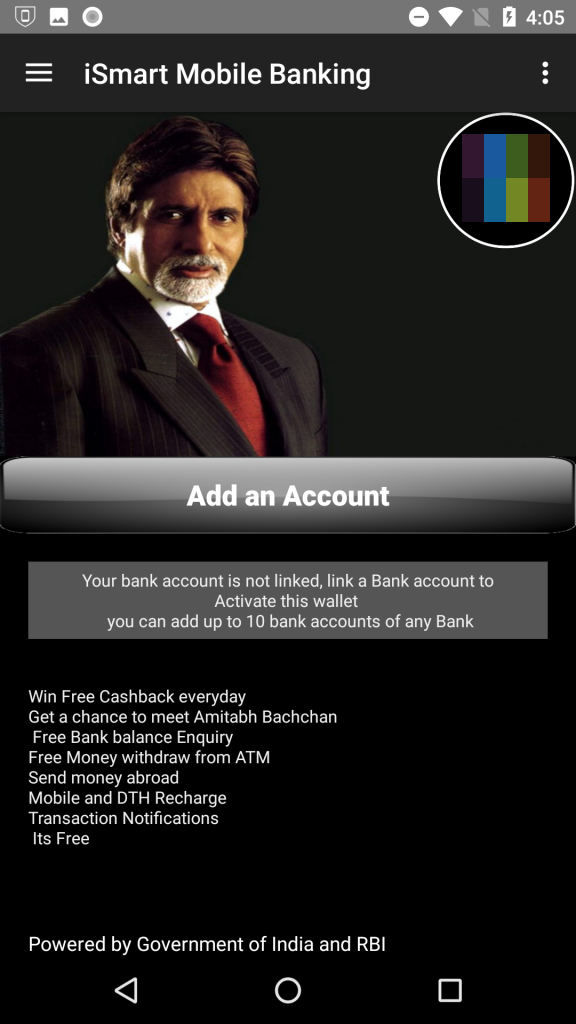
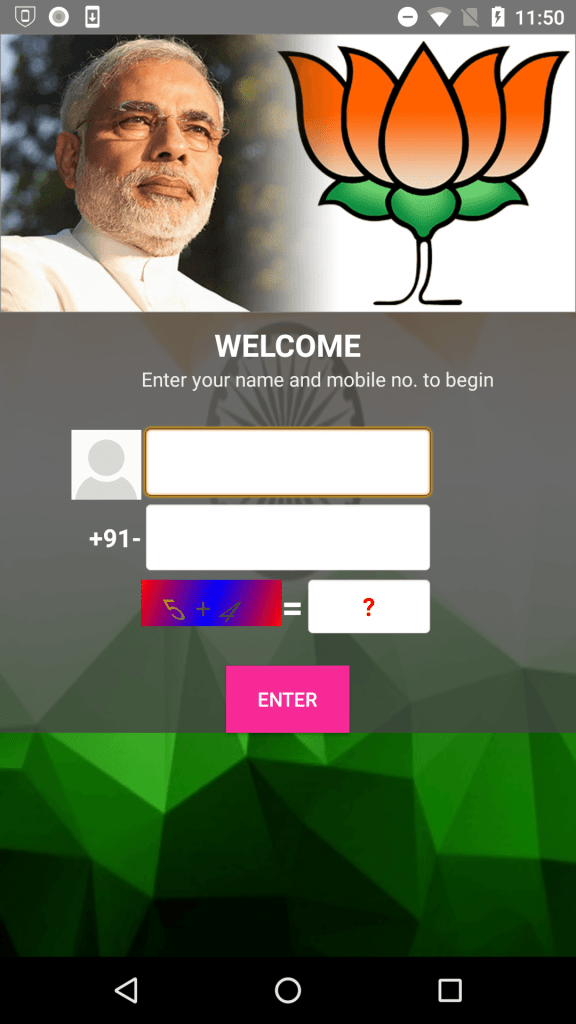
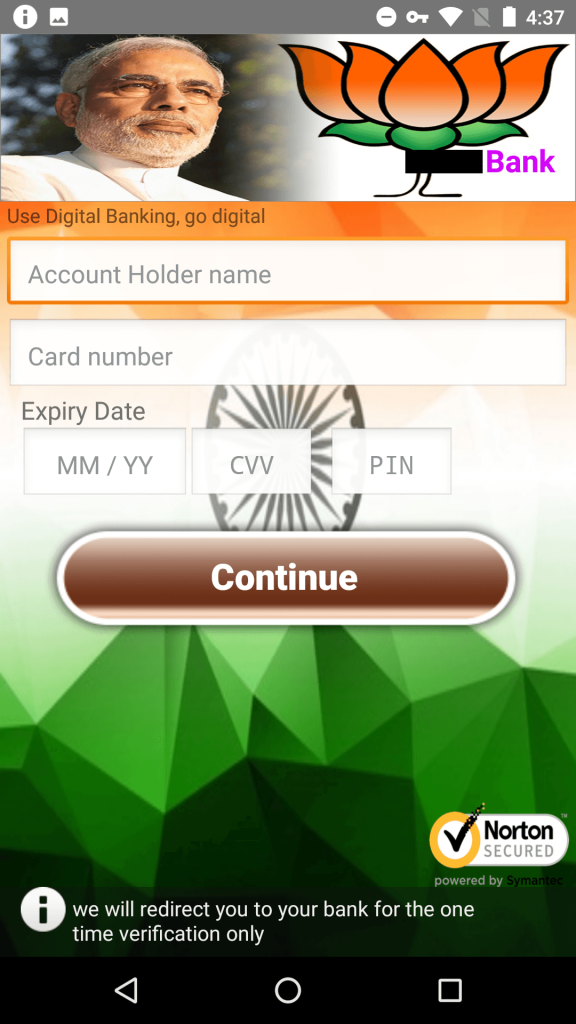
Some of these apps used a picture of the Indian actor Amitabh Bachchan, or referenced India’s financial-reformer Prime Minister Narendra Modi. Bachchan is a huge celebrity, and Modi has had a very complicated public impact on the financial system in India, affecting most of the population directly. Both are likely to draw attention as a sort of celebrity faux-endorsement; the app capitalizes on name recognition.
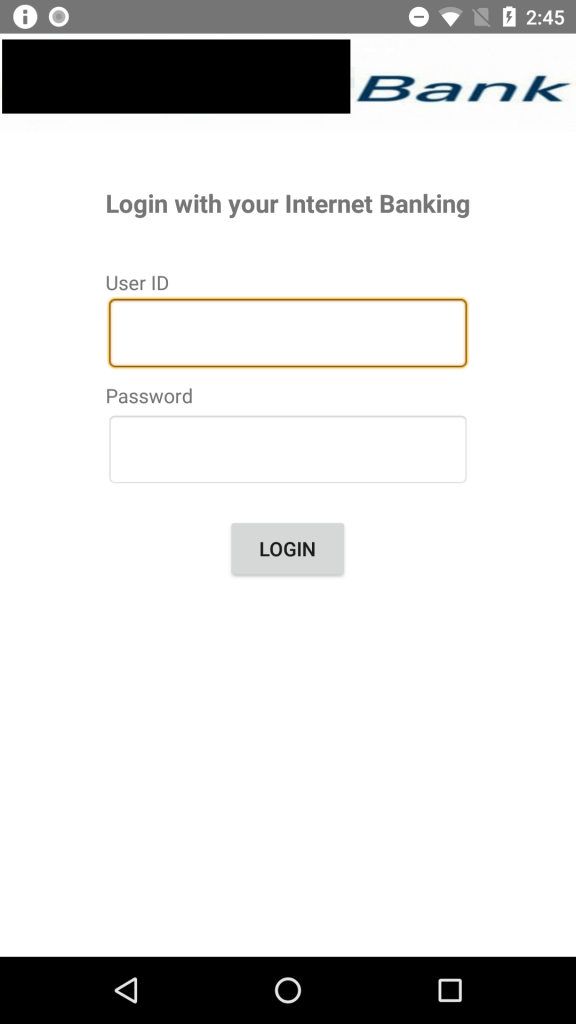
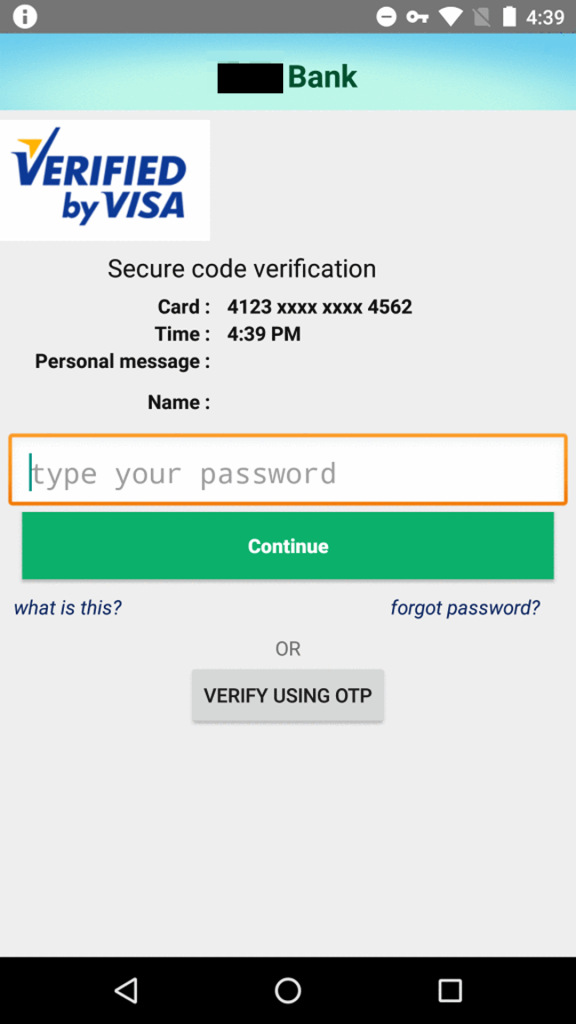
All of the apps ask the user to provide Internet banking credentials or credit card details, ostensibly to provide services such as viewing the user’s current balance, to make bank transfers, or to receive transaction notifications.
The latest app in this campaign is called All India Digital ATM by Modi, which promises cash back and other rewards when the user registers an account using a credit card or his Internet banking credentials. The app targets well known, large banks in India.
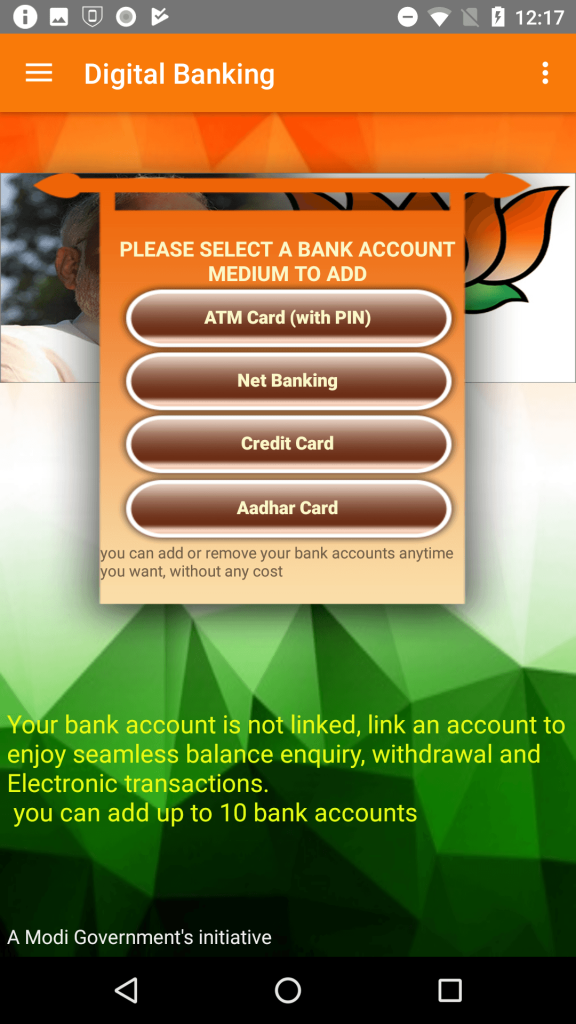
Apart from the specifically targeted banks, the app also has a generic interface that it can use to target about 25 other banks in India. When run, the app prompts the user to register using a name and phone number. The user is then asked to link a bank account using one of the four methods:
- ATM card and PIN
- Net Banking (username and password for online banking)
- Credit card
- Aadhar card (a resident identification card)
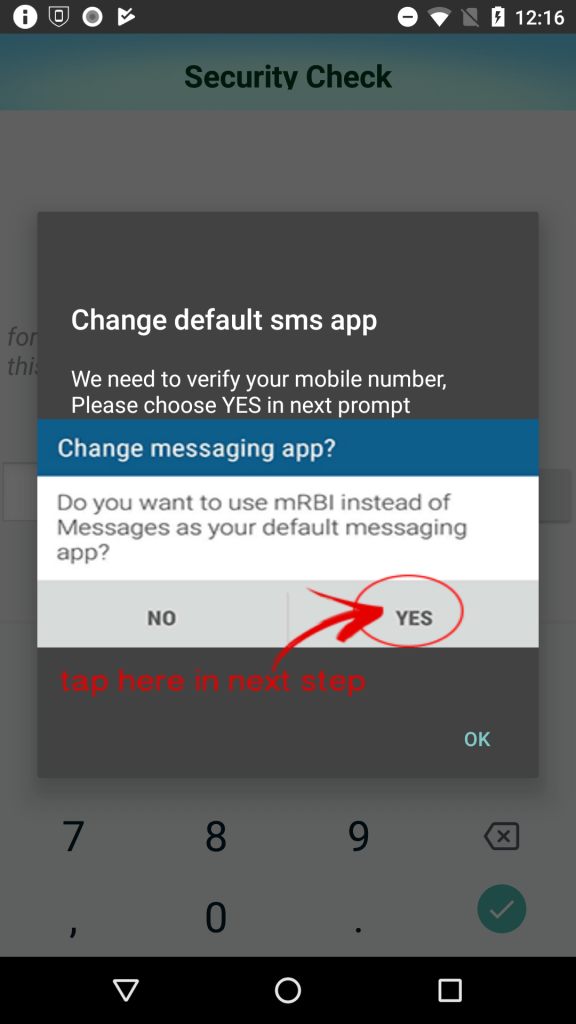
The app then presents the user with an activity that either prompts for credit card details or Internet banking credentials depending upon the option chosen by the user. The app also registers itself as the default app for receiving text messages, in order to intercept SMS-based one time passwords (OTPs), which are commonly used for two-factor authentication.
The app sends this collected information to its server without verifying any of the details for correctness.
None of the advertised functionalities, such as viewing account balance or bank transfers, are implemented by the app.
Communication
You’d think the criminals might wish to protect their ill-gotten rewards. You’d be wrong.
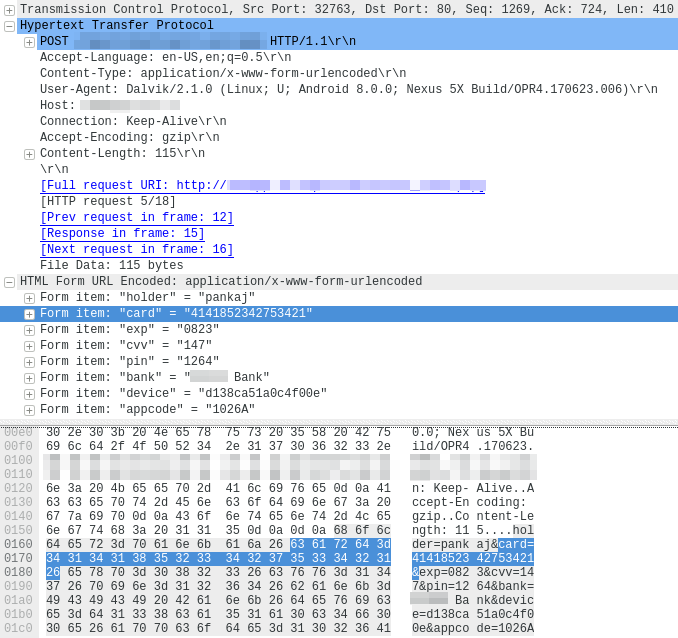
One way they might do that is by using SSL to transmit the stolen data back to HQ. Didn’t happen. The apps transmit their stolen banking credentials in the clear, over HTTP, which leaves them prone to eavesdropping while in transit.
Another way a more competent criminal might protect the data is to store it securely on the c2, in a non-obvious, inaccessible place. Whoever was behind this campaign didn’t do that, either. The server merely appends the stolen credentials to a plain text file which, in the case of the communication shown in this screenshot, was left available for anyone to download, without authentication, encryption, or protection of any kind.
Epilogue: App post facto
SophosLabs notified Google about the apps described here in July, 2018. Google removed the apps from Google Play. These malicious apps are detected by Sophos Mobile Security as Andr/FakeBank-L.
The recent discoveries of these Android banking malware presents a worrisome trend. The threat is underscored by the fact that such malware found and continues to find its way into Google Play, which remains one of the most common source of Android apps today, used by millions of users worldwide.
To avoid falling prey to such malicious apps, Android users should verify the developer publishing the app. Users should pay close attention to the user rating and read user reviews before installing such apps, even when downloading apps from trusted app marketplaces. The accelerating pace of the threat are helping drive adoption of mobile AV, like Sophos Mobile Security.
Indicators of compromise
SHA1
59464e675e164346538bb68e6d6825c9f5214478
bc76ba9bfb2dba96b8463bc73f6db3f990d28a1e
11778c30043ecf5717e8e60e4714debef92e9143
e81469f57d64b2560a0969ac9942c8e378452064
db47704b3368b01400b278889b90db159ceab11d
2f603cc3b3efbbae4ca6b6bb3b0b9fa5a8e2f66d
f5744c2a47060bf21e4e3223d3e1e6bb36c0f7f5
f4dcf6b60540f449de0c63731bec62daf7b9bf4e
a701cc3aabad28b3378d02e17d259ee06b8d52bd
2aea7ea08461026e5acb8665f3aac51f4fc3a0ac
d4f3c74f57076fe5ce2cd9e333045c8745ecfe32
1023b636e9935a5c6979925fb347aa708f5698a0
Update: Following some imprecise media reports of this research, we were contacted by fellow cybersecurity professionals about the statements in our article above. While we stand by the accuracy of our research and the integrity of our researchers, we found that the article omitted that some of the applications had been already removed at the time of the original research. We would like to add a clarifying footnote to this article:
- This research article omitted that the brand impersonating apps shared the developer certificate and the domain name usage which made them relevant to the research, and the apps had already been removed from the Google Play Store before this article was published.
- The app that was active when the research was conducted was immediately reported to Google, who removed it promptly from the Google Play Store.
- None of the 11 brand impersonating apps were active or posed a threat at the time this article was published.
- We have removed the names of the banks whose brands were leveraged by this fake app phishing campaign.
- SophosLabs would like to thank the individuals who contacted us about this research, and congratulate the efforts of the financial institutions in India who proactively take steps to protect their customers from this type of attack every day.



Anonymous
You are doing Sterling work – well done !