Thanks to Anna Szalay (SophosLabs), Xinran Wu (SophosLabs) and Paul Ducklin (Naked Security)
for contributing to this article.
We’ve been saying it for some time: Mac malware is rare compared to the stuff that targets Windows. But Apple computers are far from immune.
This year’s SophosLabs malware forecast included Mac malware geared towards harvesting data, providing covert remote access to thieves and holding files for ransom.
Other examples of Mac ransomware include OSX/Filecode-K and OSX/Filecode-L.
Now comes word of a new piece of Mac ransomware, which SophosLabs has identified as OSX/Ransom-A. Widely reported as an example of ransomware-as-a-service (RaaS) for Macs, it has become popularly known as MacRansom.
How it works
This ransomware is not in the wild. Those who want a sample must contact its creators through a secure ProtonMail email address. SophosLabs did obtain a sample and made the following observations:
When you first run the OSX/Ransom-A malware app, you won’t see any tell-tale popups asking for a password. The malware installs itself quietly to work under your own account, rather than as a system-wide program.
OSX/Ransom-A simply copies itself into a subdirectory called ~/Library/.FS_Storage, effectively allowing it to hide in plain sight. (The directory name ~/ is Unix shorthand for “your own home folder”, e.g. /Users/yourname/.)
The Library directory is used officially by macOS to store all sorts of configuration files in dozens of different subdirectories, making it an excellent place for malware to lie around looking innocent.
On macOS, which is Unix-based, files and directories that start with a dot don’t show up by default in directory listings or in the Mac Finder, so you might never notice the presence of the rogue .FS_Storage hidey-hole used by the malware.
Even if you do notice the malware directory, the name .FS_Storage gives it an official look – it was chosen because it looks similar to .DS_Store, an official macOS filename that you may well have noticed before.
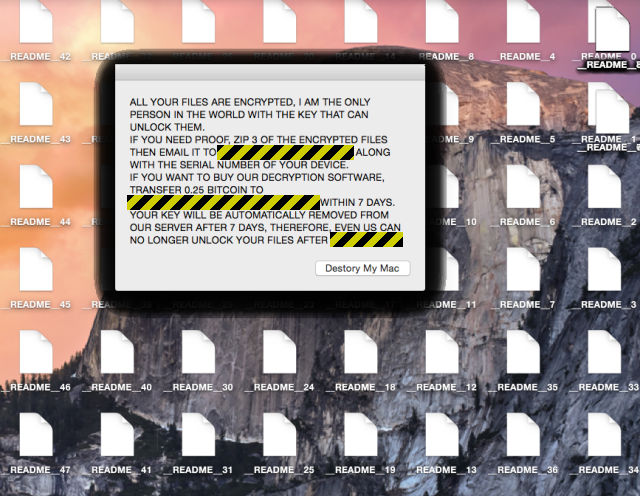
Once activated, OSX/Ransom-A follows the now-familiar pattern of encrypting your files and then offering to sell you back the decryption key you need to recover them:
Note that this malware goes after files by starting in the special directory /Volumes, which is where all your currently-attached hard disks show up, including Time Machine backup volumes, USB keys and other removable drives.
In other words, if you regularly leave your backup disks plugged in so that they are online all the time, you expose them to malware such as ransomware – which is why we routinely recommend keeping at least one recent backup copy not only offline, but also off-site, just in case.
Now what?
MacRansom is more evidence that hackers are working on ways to target Mac users with a variety of malware going forward.
Approach this as an awareness exercise.
As part of that, we offer the following resources:
- Read our advice on avoiding ransomware. Your best defense against any sort of malware is not to get infected in the first place.
- Listen to our podcast on dealing with ransomware. We explain what you need to know in plain English.
- Make regular backups and keep at least one copy offline. Ransomware is only one of many sudden ways to lose your precious data.
- Try our free Sophos Home product to protect your Mac. Anti-virus and web filtering is for everyone, not just for Windows.

Anonymous
You begin the most important paragraph with “When you first run …” ignoring vital pieces of information. How, exactly, is the software loaded onto the disk? In a browser from a nefarious website? From a USB drive? And does the malware need to be installed before it is “first run”? Does it just automagically run? Neglecting this kind of information makes this an incomplete story at best and a scare tactic at worst.
Bill Brenner
I respectfully have to disagree with your point on it being a scare tactic. We state throughout the article that this is not a widespread attack and that this latest piece of ransomware is simply an example of why Macs should not be considered bulletproof. At no point do we tell people they should be scared.
Bill Brenner
A point of clarification is in order:
Somewhere in the editing process, we accidentally deleted a line that explained that this ransomware is not in the wild, that those looking for a sample must contact the creator directly. We’ve put that line back in and apologize for the confusion. In the larger picture, this story was meant to raise awareness to the fact that malware creators are in fact focusing on Macs, even though real attacks remain rare when compared to its Windows counterparts.
Bryan
“This ransomware is not in the wild.”
yet.
:-)
Bill Brenner
Hence, the need to warn that it exists and offer up some best practices. :-)
Bryan
Naturally.
I appreciate the good info I get here at NS. Thanks Bill for continuing that tradition.
Paul Ducklin
Most (but far from all) ransomware arrives by email, either as an attachment or as a web link to a hacked or otherwise booby-trapped website. And, generally speaking, Mac apps don’t need installing…they arrive as an Application bundle, which is just a directory tree with a special structure that constitutes an the app. Double-clicking on the application directory “opens” the app (i.e. executes it as an OS process) in much the same way that double-clicking on a presentation file “opens” it (e.g. loads it into the Keynote presentation program).
Previous Mac malware we’ve written about has arrived in front of potential victims in many different ways, including sneaking in via an unpatched exploit, turning up as an attachment or a clickable link in a believable-sounding email, and even hidden inside an apparently-official Mac download on a legitimate app’s official website – the providers of the legitimate app got hacked, so their official software distribution site ended up being a conduit for cybercriminality for a few days.
A well-informed user of Mac or Windows should find it fairly easy to steer clear of malware and other suspicious emails and files…most of the time. But it only takes one tiny lapse in judgement to give malware a foothold – without any obvious warnings like password pop-ups or other alerts.
Sorry, I can’t see how it’s a “scare tactic” to explain how rogue Mac apps, such as this ransomware, can carry out their dirty work without any obvious tell-tales. You’d be surprised how many Mac users think that Mac malware can’t do anything bad without asking for permission first… those users therefore assume that they are invulnerable.
Anonymous
… who actually cares how mac ransomwares work on mac OS? most users definitely want just one thing. HOW the mac ransomware can be downloaded (via a browser? or some sneaky apps?) and installed on the mac OS. Mr. Brenner, your article does not contain the information here.
Bill Brenner
Hi, there. Please see my second response to the reader who commented before you. I think it will clear up the questions. If not, please do let me know and we’ll go from there.
Paul Ducklin
Actually, *lots* of our readers are interested in how Mac ransomware works.
They aren’t interested only in how malware might get in to start with (they already know that the crooks have many tricks up their sleeves, including phishing emails, exploit kits and booby-trapped websites). They also want to know what sort of things Mac malware can do if it does get in, and what symptoms to look out for if the worst should happen.
As the Boy Scouts of America like to say, “Be prepared!”
And as for “how software gets installed on macOS”, please see my comment above: generally speaking, Mac apps are just executable directory trees that don’t need an installation stage.
Michael Curtis
A very good article, but I think you should be a bit clearer with your path names. I know you say inside your home folder, but it would be better to write ~/Library/.FS_Storage. /Library/.FS_Storage is different and if it tried to write there I would hope it would prompt for a password.
It is interesting it is quite happy to try and run as the user rather than infect the machine.
Mark Stockley
Fixed, thanks!
Paul Ducklin
To be fair to us, we very carefully didn’t write “/Library/.FS_Storage”. (I know, because I was the person who chose the final form of the original text. The slash at the start of the absolute pathname appeared in the OP’s comment, but not in the article :-)
I deliberately avoided using the “~/” directory name because many Mac users aren’t familiar with it. It’s Unix shorthand for “your personal home directory”, so I purposely wrote it up as “the directory Library/.FS_Storage in your home folder”.
Anyway, I’ve tweaked the text again to keep Mark’s change but to add a short explanation that the “twiddle” character (“~”) has a special meaning in Unix.
glennfleishman
“Once activated”: launching it a single time doesn’t provide any prompts about unsigned apps? So a user launches it, it copies its nefarious files, and then it is activated? Any additional user-initiated steps? Does it also install a launch agent/daemon?
Paul Ducklin
Yes, it creates LaunchAgent entries so it works even after you remove or delete the original app… for non-Macsters, items in ~/Library/LaunchAgents are a bit like registry entries in HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run on Windows.
Michael Theobald
Oh come on! You tell me that ls() will not find a file with a leading dot (.). Just try ls -a /Library and such a file should be listed, if present. -Michael