Four days after WannaCry hijacked 200,000 computers in 150 countries, SophosLabs has determined that this probably didn’t start the way a typical ransomware attack does, as a phishing email carrying a malicious attachment or link the user is tricked into opening. It also appears the first infections were in south-east Asia.
Researchers assumed early on that the outbreak began with an email link or attachment, but SophosLabs VP Simon Reed said this looks like a worm from start to finish:
There were no outlook.exe files anywhere, nothing but a compromised Windows SMB driver as the starting point. So far, we haven’t found anything but evidence of a network worm.
In other words, this outbreak was a throwback to those of the early 2000s. Only this time, instead of mere noise and network downtime, a much more damaging payload of ransomware ground many organizations to a halt.
What follows are additional details from the SophosLabs investigation.
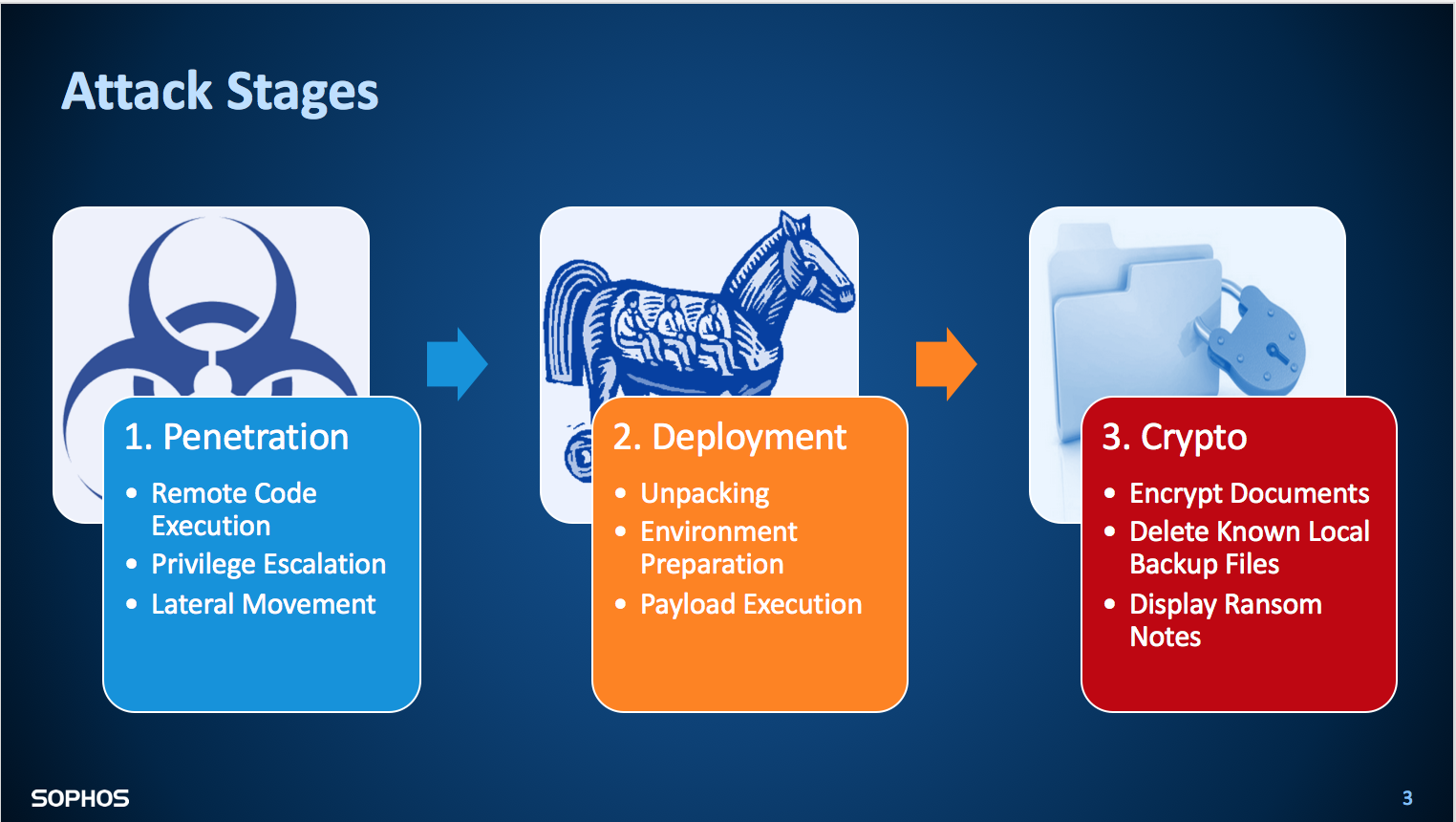
A three-pronged assault
The investigation revealed a three-stage attack, starting with remote code execution and the malware gaining advanced user privileges. From there, the payload was unpacked and executed. Once computers were hijacked, it encrypted documents and displayed ransom notes.
Analysis seems to confirm that Friday’s attack was launched using suspected NSA code leaked by a group of hackers known as the Shadow Brokers. It used a variant of the Shadow Brokers’ APT EternalBlue Exploit (CC-1353) and used strong encryption on files such as documents, images, and videos. It also went after servers, trying to encrypt SQL server databases and Microsoft Exchange data files.
There were three key factors that caused this attack to spread so quickly:
- The inclusion of code that caused the threat to spread across networks as a worm quickly without needing further user action after the initial infection had taken place.
- It exploited a vulnerability that many organizations had not patched against. Patching operating systems is the first line of a security strategy, yet many still struggle to achieve regular updates across their environments.
- Organizations are still running Windows XP. Microsoft had discontinued support for Windows XP and not issued a patch for this system, but subsequently issued a patch for Windows XP in light of this attack. Microsoft does support legacy versions of Windows, but at extra cost.
As we’ve noted previously, the attack exploited a Windows vulnerability Microsoft had released a patch for in March. That flaw was in the Windows Server Message Block (SMB) service, which Windows computers use to share files and printers across local networks. Microsoft addressed the issue in its MS17-010 bulletin.
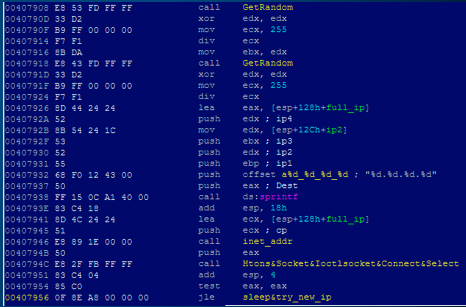
The worm generated random IP addresses, as the following code snippet shows. Once the IP addresses were defined, the worm sent malicious SMB packets to the remote host, spreading itself.
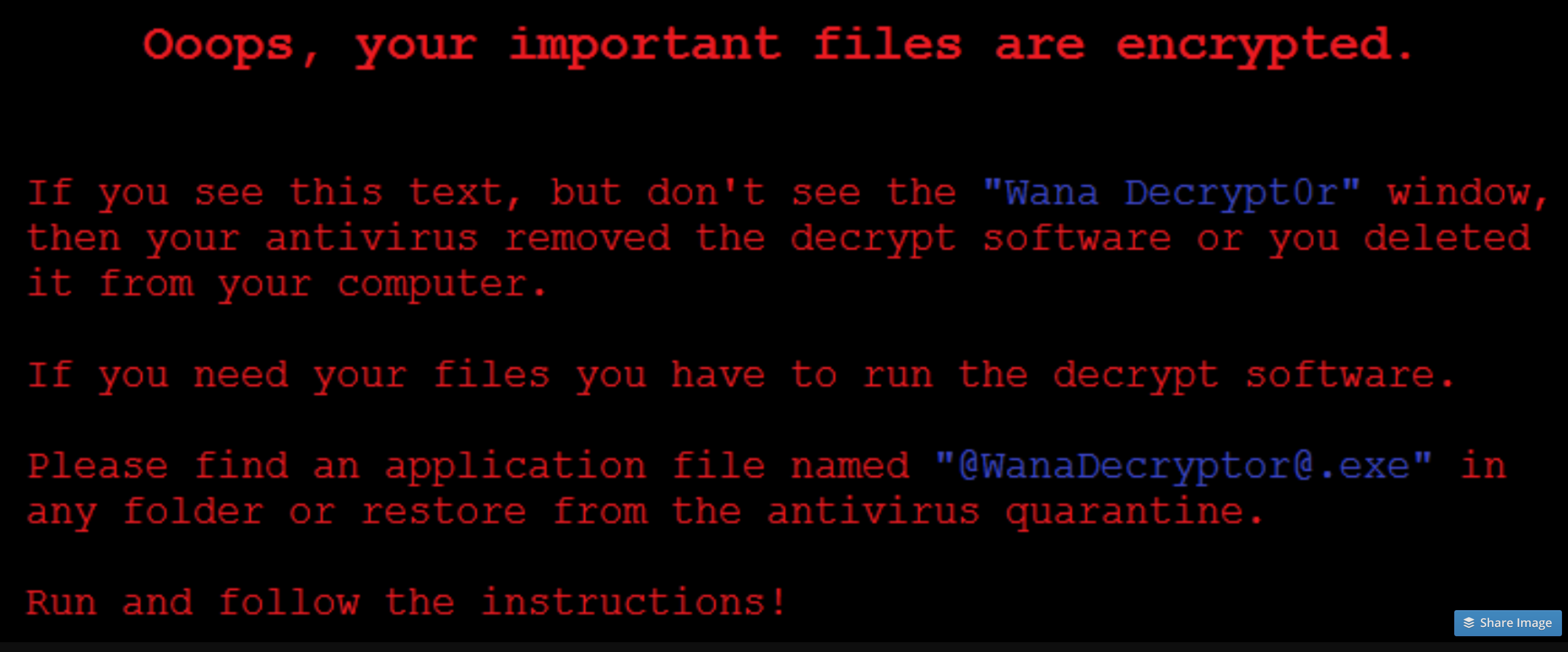
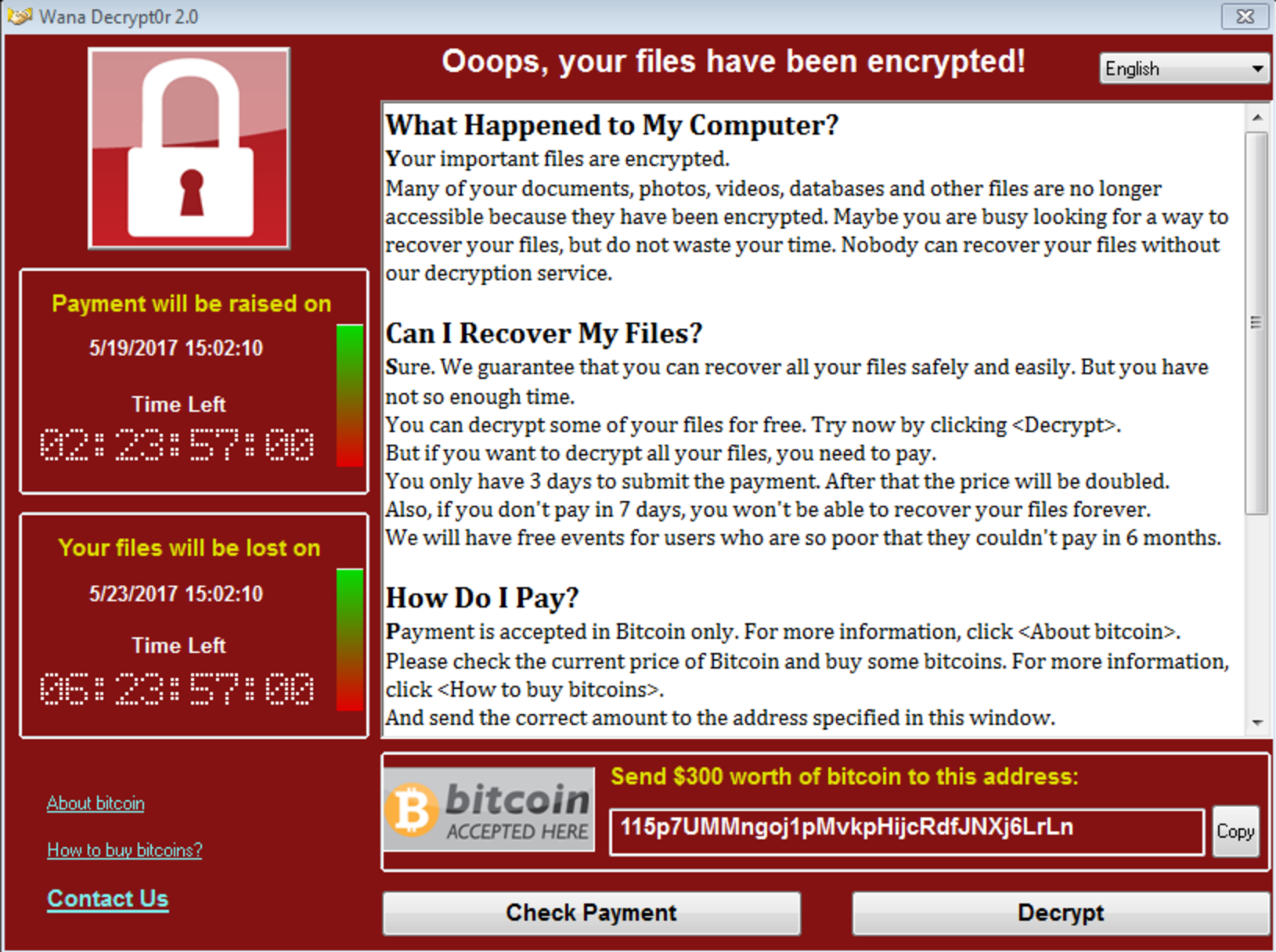
From there, files on the hijacked computers were encrypted and ransom notes like this appeared on victims’ screens:
Where infections began
SophosLabs’ investigation indicates the first infections Friday appeared in India, Hong Kong and the Philippines. The findings of south-east Asian origin are in sync with that of other research organizations, such as Nominum. Yuriy Yuzifovich, head of data science and security research, and Yohai Einav, principal security researcher, wrote on their website:
Our first evidence for WannaCry was found at 7:44am UTC, when a client from an ISP in south-east Asia hit WannaCry’s kill-switch domain (iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea[.]com). In the following hours we identified thousands of additional WannaCry-infected clients, from a wide variety of countries and ISPs, trying to communicate with the domain.
Ransom tally
Over the weekend, accounts set up to collect ransom payments had received smaller amounts than expected for an attack of this size. But by Monday morning, the balances were on the rise, suggesting that more people were responding to the ransom message Monday. On Saturday, three ransomware-associated wallets had received 92 bitcoin payments totaling $26,407.85 USD. By Sunday, the number between the three wallets was up to $30,706.61 USD. By Monday morning, 181 payments had been made totaling 29.46564365 BTC ($50,504.23 USD).
The three bitcoin wallets had received 253 payments totaling 41.78807332 BTC ($71,647.06 USD) by Tuesday evening.
Worm defenses
With the return of old-school worm outbreaks like this one, it’s worth reviewing steps users can take to avoid infection. Unfortunately, some of those steps have proven unpopular, as Naked Security’s John Dunn wrote yesterday. Admins can block services or ports at firewall level but not often indefinitely. Suspending email is another tactic that works until everyone complains.
The best advice remains the same as it did when the outbreak began:
To guard against malware exploiting Microsoft vulnerabilities:
- Stay on top of all patch releases and apply them quickly.
- If at all possible, replace older Windows systems with the latest versions.
And since the worm payload was ransomware, a reminder on defenses for that are in order:
- Back up regularly and keep a recent backup copy off-site.There are dozens of ways other than ransomware that files can suddenly vanish, such as fire, flood, theft, a dropped laptop or even an accidental delete. Encrypt your backup and you won’t have to worry about the backup device falling into the wrong hands.
- Be cautious about unsolicited attachments.The crooks are relying on the dilemma that you shouldn’t open a document until you are sure it’s one you want, but you can’t tell if it’s one you want until you open it. If in doubt, leave it out.
- Use Sophos Intercept X and, for home (non-business) users, register for Sophos Home Premium Beta, which stops ransomware in its tracks by blocking the unauthorized encryption of files.

trefunny
so the consensus so far is that these systems were directly exploited, not from an internal user downloading it to start with?
that is surprising even though it shouldn’t be if you have spent 5 minutes on shodan…
Louis
“… Admins can block services or ports at firewall level but not often indefinitely…”
For this particular case, it is nevertheless frightening and irresponsible to leave SMB ports open on the Internet …
brianr2015
I am amazed that there are still system out there with SMB ports open to the world, is there a reason for it which I not aware of?
Mark Stockley
Unauthenticated? Can’t think of one. Accidentally enabling File and Printer sharing over the internet is an old Windows problem though.
When you look at the outbreak; at the continued use of a 16 year old operating system that’s long out of support; at the widespread non-patching of a two month old and highly publicised critical flaw… I’ll put it down to carelessness or ignorance until I see a better explanation.
The Flying Dutchman
These days most internet-connected computers should be behind a modem/router which normally speaking should block SMB by default, you’d have to explicitly enable it.
Mark Stockley
That’s what should be happening. A quick look on Shodan shows hundreds of thousands of SMB servers visible on the internet running on Microsoft operating systems that are out of mainstream support.
brianr2015
What’s “even” worse is that some of those must have been UK NHS systems!
NikTheGeek Ⓐ (@NikTheGeek)
Using Shodan, it’s quite surprising how many UK organisations have 445 open to Windows-based devices
1G0R
Also see Microsoft now talking more about MS17-008 – vSMB RCE…could this have been the start or perhaps the next steps?