Sophos continues working to protect customers from the WannaCry ransomware attack. That effort has been successful, but we continue to receive many questions about how this attack happened, what we must do to defend our organizations, and, of course, what’s next?
This article is designed to answer those questions.
What happened?
A fast-spreading piece of ransomware called Wanna (also known as WannaCry, WCry, WanaCrypt, WanaCrypt0r and Wana DeCrypt0r) held computer systems hostage around the globe Friday. National Health Service hospitals (NHS) in the UK was hit hard, with its phone lines and IT systems being held hostage. From there, the attack spilled across the globe.
It encrypted victim’s files and changed the extensions to: .wnry, .wcry, .wncry and .wncrypt. It then presented a window to the user with a ransom demand:
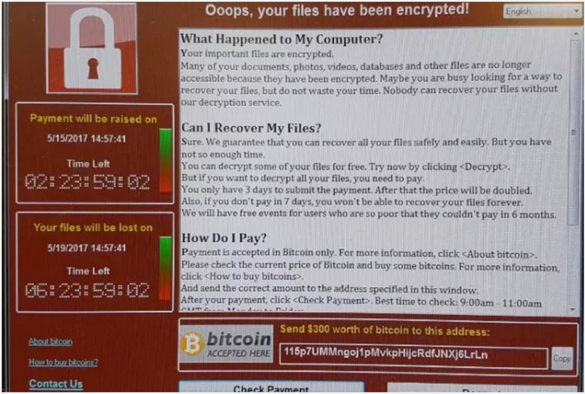
Analysis seems to confirm that the attack was launched using suspected NSA code leaked by a group of hackers known as the Shadow Brokers. It uses a variant of the ShadowBrokers’ APT EternalBlue Exploit (CC-1353). It also uses strong encryption on files such as documents, images, and videos.
This was different from past ransomware attacks. Why?
There were some unique aspects to the WannaCry attack. Typical ransomware infections happen after the victim clicks on a malicious email attachment or link. In this attack the malware was able to exploit a remote code execution (RCE) vulnerability that allowed it to infect unpatched machines without users having to do anything.
Because of that, this was able to spread in the same rapid fashion as the worm outbreaks common a decade ago, such as Slammer and Conficker.
Specifically, WannaCry exploited a Windows vulnerability Microsoft released a patch for in March. That flaw was in the Windows Server Message Block (SMB) service, which Windows computers use to share files and printers across local networks. Microsoft addressed the issue in its MS17-010 bulletin.
Organizations running older, no-longer-supporter versions of Windows were particularly hard hit. In fact, Microsoft took the highly unusual step of making a security update for platforms in custom support (such as Windows XP) available to everyone. The software giant said in a statement:
We know some of our customers are running versions of Windows that no longer receive mainstream support. That means those customers will not have received the Security Update released in March. Given the potential impact to customers and their businesses, we made the decision to make the Security Update for platforms in custom support only, Windows XP, Windows 8, and Windows Server 2003, broadly available for download here.
Is this over?
Unlikely. With the code behind Friday’s attack in the wild, we should expect copycats to cook up their own campaigns in the coming days to capitalize on the money-making opportunity in front of them. We also expect aftershocks Monday as employees at affected company’s who weren’t there Friday return to work and fire up their computers.
What is Sophos doing to protect customers?
Sophos continues to update protections against the threat. Sophos Customers using Intercept X and Sophos EXP products will also see this ransomware blocked by CryptoGuard. Please note that while Intercept X and EXP will block the underlying behavior and restore deleted or encrypted files in all cases we have seen, the offending ransomware splash screen and note may still appear.
Is there anything I need to do?
You’ll want to ensure all of your Windows environments have been updated as described in Microsoft Security Bulletin MS17-010 – Critical. Microsoft is providing Customer Guidance for WannaCrypt attacks. As noted above, Microsoft has made the decision to make the Security Update for platforms in custom support only — Windows XP, Windows 8, and Windows Server 2003 — broadly available for download:
| Windows Server 2003 SP2 x64 | Windows Server 2003 SP2 x86 | |
| Windows 8 x64 | Windows 8 x86 | |
| Windows XP SP2 x64 | Windows XP SP3 x86 | Windows XP Embedded SP3 x86 |
As we always say, patching is critical. For Sophos customers, keep checking the Wana Decrypt0r 2.0 Ransomware Knowledge Base where we’ll be issuing updates.

Anonymous
By “Sophos Endpoint Protection: Update immediately” – are you referring to the definitions or the client itself?
Mark Stockley
Hi, thanks for the feedback. We’re sorry that wasn’t clear so we’ve changed the language in the article. If your Sophos product is set to update itself automatically and working correctly then there is nothing you need to – you will have all current WannaCry detection capabilities and will quickly get any subsequent updates automatically.
Susan
For some reason, the Blog emails I have received the past 2 days are in a foreign language. Can you advise how to fix this?
Mark Stockley
Hi Susan, Sophos News has recently become multi-language and we are having some teething problems with the wordpress.com “New Post” emails. There isn’t a setting that you can change, it’s on us. We hope to have a fix rolled out later today.
Kent Clarkson
“Trust us, we’re from the government”
Good thing they have such powerful tools and high competence to secure them.
Anonymous
The government is the reason for wannacry. This virus shows the holes left by the government invading our lives They government always blame something and don’t stand up and fix the problems they cause. You think you can violate our lives and leave us to Rott. I hope they invade your lives and you end up with everything lost and burnt out and a bill to fix it.