Remember how an Argentinian Starbucks store recently turned out to be doing JavaScript cryptomining on the side?
That’s where someone else uses your computer, via your web browser, to perform a series of calculations that help to generate some sort of cryptocurrency, and keeps the proceeds for themselves.
In that case, it seems to have been a unilateral decision by the Wi-Fi provider to include coin mining JavaScript code in the Wi-Fi registration page.
We’re guessing that the provider figured it would be OK to “borrow” approximately 10 seconds of CPU time whenever someone connected to the Wi-Fi, presumably as a way of earning a few extra pennies in return for providing free internet access:
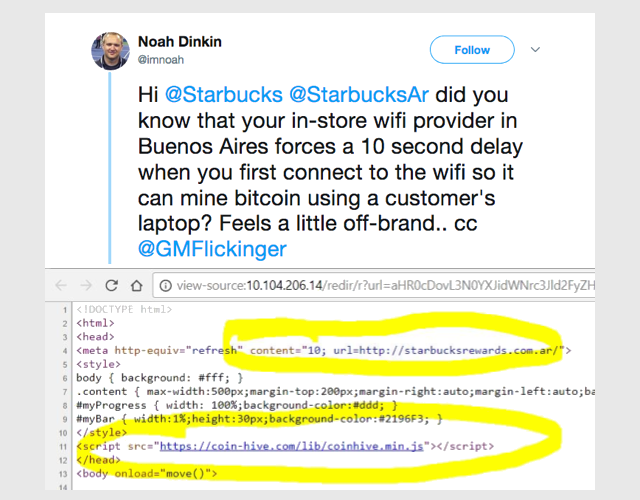
(Just for the record, the tweeter was wrong above, inasmuch as the code was mining Monero, not Bitcoin – but the sentiment was spot-on.)
Starbucks wasn’t impressed, and “took swift action to ensure [the] internet provider resolved the issue”.
We’re guessing here, but we’re prepared to assume that this “swift action” involved a very short phone call in a rather loud voice.
But it’s not only the Wi-Fi operator or the coffee shop owner that you need to worry about.
If you join a public Wi-Fi network, and you don’t use a VPN, or stick to HTTPS websites, or both, then…
…anyone else in the coffee shop (or bus, or train, or hotel lobby, or wherever it is) at the same time can sniff out what you’re doing, and perhaps also trick you into seeing and doing something you didn’t expect.
Thanks to a “for academic purposes only” project called CoffeeMiner, rogues in your local cafe can now trick you into cryptomining, along with any other web-based cyberdodginess they might have in mind:
The project is the brainchild of a software developer from Barcelona who goes by the name Arnau Code, and if you ignore its potential for misuse (please read the disclaimer!), we think it’s a well-prepared tutorial about Man-in-the-Middle MitM) attacks.
If you’ve ever wondered why HTTPS (the padlock in your browser) really matters, and why every site really ought to use it instead of serving up content using plain old HTTP, you should look at Arnau’s article. Don’t just take it from us that HTTPS is about more than secrecy. The CoffeeMiner project is a good reminder that HTTPS is about authenticity and tamper-resistance, too – getting the right stuff from the right place.
A MitM attack is where someone else on the network gets to see your network requests before they set off to their final destination, and can intercept the replies before they get back to you.
Instead of talking directly to the site you’re expecting, you are effectively talking through a middleman, who can alter what you ask in the first place, and change what you see in reply.
Altering the answers is what CoffeeMiner does: through a variety of tricks, it intercepts your web traffic before it reaches the Wi-Fi access point in the coffee shop; it covertly fetches the web page you requested on your behalf; and it sneaks a line of coin-mining JavaScript in the reply.
In other words, every website you visit could, in theory, end up temporarily mining cryptocurrency for someone else.
Simply explained, Coffee Miner:
- Tricks your network card into thinking that the CoffeeMiner is the access point. The open source product
dnsiffis used for this part. - Passes on all your network traffic directly except for web requests.
- Pushes your web traffic into a man-in-the-middle proxy. The open source toolkit
mitmproxyis used here. - Inserts one line of coin-mining HTML into your web replies.
The CoffeeMiner code doesn’t actually inject coin mining code directly; instead it injects a line like this:
![]()
The IP number and port (in this example, 192.0.2.42:8000) is a web server running on the CoffeeMiner computer itself – in fact, it’s part of the CoffeeMiner toolkit – that serves up the actual cryptomining code of your choice. (Arnaud Code chose a widepspread miner known as CoinHive.)
What to do?
This isn’t really a lesson about cryptomining, though that certainly adds to the intrigue.
The problem here is that on an untrusted network (and that means almost every network you’ll ever use these days, because it’s hard to vouch for every user and every device attached at any moment), a rogue user can very easily mess with any web traffic that isn’t encrypted using HTTPS.
Without HTTPS, there is no confidentiality, so anyone can see what you are doing and saying; there is no identification, so you have no idea who’s replying; and there is no integrity, because you can’t tell when someone has tampered with what you’ve just downloaded, for example by stuffing a coin mining script into every web page.
As we mentioned at the start:
- Stick to sites that use HTTPS. A web-based MitM attack will almost always trigger a warning that you are connecting via an imposter server.
- Urge sites that don’t yet use HTTPS to start doing so. It’s a little bit more work, but worth the effort.
- Use a VPN if your work provides one. This encrypts all your network traffic back to head office, not just your web browsing.
By the way, if you want to run a VPN at home, and you have a spare computer handy, why not try the Sophos XG Firewall Home Edition? You get a free licence for everything the product can do, including anti-virus, web filtering, email security, IPS, plus a fully-fledged VPN.

Richard Wall (@Skavenger0)
Interestingly I did a security demo the other day and it took me quite a while to find a public website that people would recognize that wasn’t running SSL. Things are looking better. Issue now is we keep advising people to check for SSL but the criminals are now also using https making sites look more legitimate.
Paul Ducklin
Indeed, and here’s an interesting story about “phishing via HTTPS” (probably should have linked to this somewhere in the article itself):
https://nakedsecurity.sophos.com/2017/12/08/phishing-embraces-https-hoping-youll-check-for-the-padlock/
I agree that HTTP-only sites are thinning out, but I do come across them regularly. I find that Firefox’s “anti-padlock”, that crossed-out-with-a-red-line icon that reminds you that a site is *not* encrypted – does very handily make them stand out, so I suspect I am noticing them more than I used to even though they are diminishing, which I reckon is a good thing!
sevencyclist
Wouldn’t a VPN only help if you have it running before you connect to Wi-Fi?
Just clarifying …
Paul Ducklin
The answer is, not if it’s set up properly. After all, to activate the VPN you need to establish a data connection first – you need an insecure link to carry your packets from end to end, so you can negotiate the cryptographic exchange needed to upgrade to a secure link that runs in a VPN “tunnel” over the insecure link.
A cryptograhpically secure VPN typically uses some kind of exchange of digital certificates up front, whereby each end can validate the identity of the other and then agree on a secret key for the “tunnel”. WPA/WPA2 used with a pre-shared key (PSK) [a] doesn’t use public key cryptography to establish a session key (so the session key can be sniffed) and [b] doesn’t encrypt any further than the access point.
Lee
Also, if you have a 4G connection and VPN is switched on and then you connect to a different data connection ie Wi-Fi then you may notice your VPN will reconnect. Mine does anyway.
sevencyclist
Ah ok, forgot about how our VPN is set up. In fact, we do have the cert already set up on our VPN client. Thanks.
ted
FYI, the profit from CPU mining is much less than displaying ads.
Paul Ducklin
Quite a lot of sites in my research were happily doing both :-) Thing is, if you have an adblocker then ads make nothing off you; but you probably do have JavaScript enabled for Wi-Fi connection portals…either because they render outside your regular browser (e.g. in WebView not in Safari) or because you have to let the scripts run to connect at all.