There are lots of Linux servers out there – sufficiently many that it’s impossible to give the precise number, and difficult even to come up with a good approximation.
But we’re unlikely to offend anyone if we say that at least 20%, probably 40%, and possibly more than 50% of the internet’s servers run some flavour of Linux.
As a result, cybercrooks have learned how to hack into Linux servers on an industrial scale in order to steal both storage space and network bandwidth.
With these hacked servers, they push malware, spam, scams and phishing campaigns onto users worldwide.
Of course, the vast majority of the victims who get attacked or infected via compromised servers are running Windows, simply because the vast majority of end users are running Windows.
If you run a Linux desktop, life can be a lot quieter.
Part of that is being in a small minority, with Linux probably running on only about 2% of desktop computers worldwide.
Being in a small minority means you haven’t yet attracted much attention from cybercriminals, who are making huge amounts of money from the Windows ecosystem already.
But is that enough to consider yourself safe?
No, it isn’t.
Linux malware does exist and has occasionally spread extensively in the wild; Linux users do get phished; Linux laptops do get lost, or stolen or hacked; hard disks do get removed from Linux computers and sold without being wiped – and any of these could put you, your privacy, or even your identity, at risk.
So here are five easy steps to enhance your Linux security.
1. Choose Full Disk Encryption (FDE)
No matter which operating system you are using, we recommend that you encrypt your entire hard disk.
If your laptop is lost or stolen, using a simple login password won’t protect your data: a thief can just boot into Linux from a USB key and read all your data off without a password.
By encrypting your hard drive, you ensure your data remains secure, because the thief won’t be able to read anything without the FDE password.
The advantage of FDE over encrypting just your home folder and the files in it is that you no longer have to worry about temporary files, swap files or other directories where important files might end up without you realising it.
On any fairly recent computer, you’re unlikely to notice, or even to be able to measure, a slowdown in day-to-day use due to encrypting everything.
On Ubuntu and Fedora, as in many other Linux distributions (distros for short), full disk encryption is available right at install time.
You can easily enable it during the installation by selecting Encrypt the new Ubuntu installation for security:
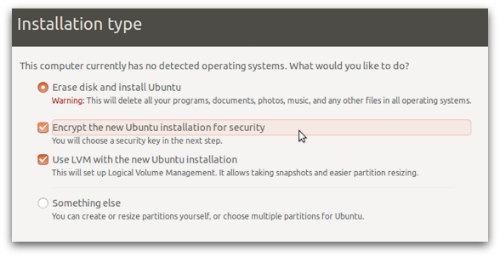
And, of course, remember to pick a proper password!
2. Keep your software up-to-date
Again, no matter which operating system you are using, you should always keep both your operating system and your applications, such as web browsers, PDF readers and video players, up to date.
Most Linux distros make this easy.
On Ubuntu, by default, security updates are installed automatically.
You can double-check this at System Settings | Software & Updates | Updates.
Make sure the Important security updates option is turned on:
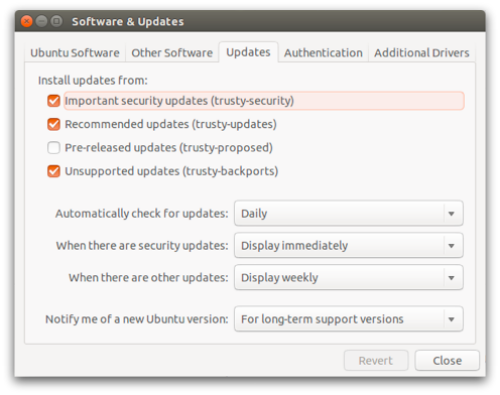
3. Learn how to use Linux’s firewall
The Linux kernel includes a firewall component called iptables, which gives you a powerful way to manage network traffic and keep out many sorts of cyberattack.
On Ubuntu you will also have an application called Uncomplicated Firewall (UFW), a frontend program that simplifies setting up iptables.
By default UFW is disabled, but you can turn it on from a command prompt by doing:
$ sudo ufw enable Password: Firewall is active and enabled on system startup $
To learn more about iptables and what it can do, you might also want to try a graphical configuration tool such as GUFW or UFW Frontends.
On Fedora you will find FirewallD, an alternative firewall management toolkit that is enabled by default.
A graphical user interface for FirewallD, called firewall-config, is available; you can install it from a command prompt with:
$ yum install firewall-config
4. Tighten up security in your browser
The browser is the way in for many current cyberthreats, whether you use Mozilla Firefox, Google Chrome, Opera or another browser.
Many free extensions are available to improve the security of your browser, and your privacy as well. Among others, you may want to consider the following:
5. Use anti-virus software
We saved this one until last because it has long been a bone of contention with a vocal minority of Linux faithful.
Some people will tell you that it’s pointless installing an anti-virus software on a Linux-based operating system.
Half of the argument is that most of the malware you will detect on a Linux computer will be for Windows, and why should you be responsible for that?
The obvious answer is, “Why not? What if you pass an infected file onto someone else and thus make yourself part of the problem rather than the solution?”
The other half of the argument is that malware on Linux desktops is rare enough that you might as well pretend it doesn’t exist at all.
My personal opinion is that if you feel safe just because you think the risk of a breach is low, then attackers have already outsmarted you.
Image of computer courtesy of Shutterstock.
Tux (the Linux penguin) by Larry Ewing, Simon Budig and Anja Gerwinski, downloaded courtesy of Wikimedia Commons.
