There are lots of Linux servers out there – sufficiently many that it’s impossible to give the precise number, and difficult even to come up with a good approximation.
But we’re unlikely to offend anyone if we say that at least 20%, probably 40%, and possibly more than 50% of the internet’s servers run some flavour of Linux.
As a result, cybercrooks have learned how to hack into Linux servers on an industrial scale in order to steal both storage space and network bandwidth.
With these hacked servers, they push malware, spam, scams and phishing campaigns onto users worldwide.
Of course, the vast majority of the victims who get attacked or infected via compromised servers are running Windows, simply because the vast majority of end users are running Windows.
If you run a Linux desktop, life can be a lot quieter.
Part of that is being in a small minority, with Linux probably running on only about 2% of desktop computers worldwide.
Being in a small minority means you haven’t yet attracted much attention from cybercriminals, who are making huge amounts of money from the Windows ecosystem already.
But is that enough to consider yourself safe?
No, it isn’t.
Linux malware does exist and has occasionally spread extensively in the wild; Linux users do get phished; Linux laptops do get lost, or stolen or hacked; hard disks do get removed from Linux computers and sold without being wiped – and any of these could put you, your privacy, or even your identity, at risk.
So here are five easy steps to enhance your Linux security.
1. Choose Full Disk Encryption (FDE)
No matter which operating system you are using, we recommend that you encrypt your entire hard disk.
If your laptop is lost or stolen, using a simple login password won’t protect your data: a thief can just boot into Linux from a USB key and read all your data off without a password.
By encrypting your hard drive, you ensure your data remains secure, because the thief won’t be able to read anything without the FDE password.
The advantage of FDE over encrypting just your home folder and the files in it is that you no longer have to worry about temporary files, swap files or other directories where important files might end up without you realising it.
On any fairly recent computer, you’re unlikely to notice, or even to be able to measure, a slowdown in day-to-day use due to encrypting everything.
On Ubuntu and Fedora, as in many other Linux distributions (distros for short), full disk encryption is available right at install time.
You can easily enable it during the installation by selecting Encrypt the new Ubuntu installation for security:
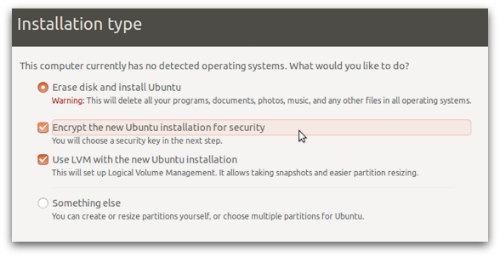
And, of course, remember to pick a proper password!
2. Keep your software up-to-date
Again, no matter which operating system you are using, you should always keep both your operating system and your applications, such as web browsers, PDF readers and video players, up to date.
Most Linux distros make this easy.
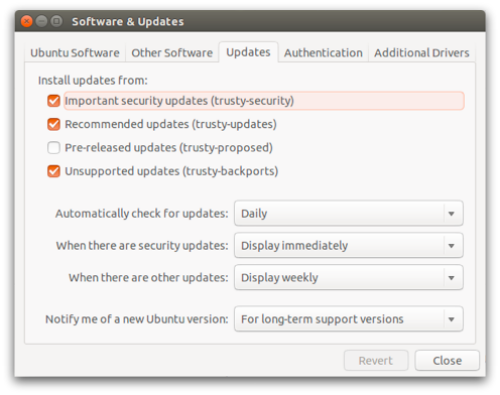
On Ubuntu, by default, security updates are installed automatically.
You can double-check this at System Settings | Software & Updates | Updates.
Make sure the Important security updates option is turned on:
3. Learn how to use Linux’s firewall
The Linux kernel includes a firewall component called iptables, which gives you a powerful way to manage network traffic and keep out many sorts of cyberattack.
On Ubuntu you will also have an application called Uncomplicated Firewall (UFW), a frontend program that simplifies setting up iptables.
By default UFW is disabled, but you can turn it on from a command prompt by doing:
$ sudo ufw enable Password: Firewall is active and enabled on system startup $
To learn more about iptables and what it can do, you might also want to try a graphical configuration tool such as GUFW or UFW Frontends.
On Fedora you will find FirewallD, an alternative firewall management toolkit that is enabled by default.
A graphical user interface for FirewallD, called firewall-config, is available; you can install it from a command prompt with:
$ yum install firewall-config
4. Tighten up security in your browser
The browser is the way in for many current cyberthreats, whether you use Mozilla Firefox, Google Chrome, Opera or another browser.
Many free extensions are available to improve the security of your browser, and your privacy as well. Among others, you may want to consider the following:
5. Use anti-virus software
We saved this one until last because it has long been a bone of contention with a vocal minority of Linux faithful.
Some people will tell you that it’s pointless installing an anti-virus software on a Linux-based operating system.
Half of the argument is that most of the malware you will detect on a Linux computer will be for Windows, and why should you be responsible for that?
The obvious answer is, “Why not? What if you pass an infected file onto someone else and thus make yourself part of the problem rather than the solution?”
The other half of the argument is that malware on Linux desktops is rare enough that you might as well pretend it doesn’t exist at all.
My personal opinion is that if you feel safe just because you think the risk of a breach is low, then attackers have already outsmarted you.
Image of computer courtesy of Shutterstock.
Tux (the Linux penguin) by Larry Ewing, Simon Budig and Anja Gerwinski, downloaded courtesy of Wikimedia Commons.

Eddie
AV-Comparatives just released a review of Security products for Linux (including Sophos).
Kasun
And dont disable SELinux on CentOS/Fedora family in OSes.
Paolo Rovelli
Agree! :)
SELinux and AppArmor are probably the most effective way to secure your machine, especially against new vulnerabilities.
Not disabling them is probably the most important thing you can do.
John
Ensuring third-party applications are up-to-date is very important. Some of the same flaws that exists in windows version of applications such as Adobe products, exists on Linux systems.
Pingoo
The Disconnect website – which I went to because I had not heard of it before says:
“Available on Mac (10.7+), Windows (7.0+), Android (4.0+), and iOS (7.0+)”
This is a post about Linux security?
Anna Brading
Hi Pingoo, We’ve changed the link to go the more specific page for the browser add-on which is available for any platform. Thanks for pointing that out.
Richard Klimming
I would recommend Privacy Badger over Ghostery. Badger is made by the EFF, and many people have done research concluding that Ghostery essentially contains malware. Ghostery also uses a unique font that can be used to fingerprint browsers and figure out who’s using the plugin; not very private compared to its alternative.
Giack
Although I personally do not like Ghostery either, let’s be clear: it is no malware and does not contain any. And no respectable computer security company has never claim otherwise.
All the criticism around Ghostery are related to Ghostrank, which is pretty much similar (although not strictly the same) of an ad program. Which is at least controversial since Ghostery is an ad blocker.
But, this does not make it a malware. Especially since you can disable it.
Alan Robertson
Hat’s off to you Paolo – I’ve literally just done an install of Linux Mint Rebecca and you’ve pretty much covered comprehensively the process. The only one I left out was NoScript – I run it myself but it is a little daunting for a first time user. I’ll install it later once she get’s used to Linux – “what do you mean there is no antivirus needed?”!! I do take your point about spreading to Windows users though. I’m off to investigate your Antivirus now. Thanks.
Anonymous
awesome tips really helpful to get good maturity on linux OS
Mark
If you are interested in the third party sites you interact with on the web, you should consider also installing Mozilla Lightbeam on your web browser. It does not enhance your protection, but it improves your privacy awareness.
Slashee the Cow
Just thought I’d add that if you are worried about the performance hit from encrypting your filesystem in Linux (and if you have a reasonably modern computer, you shouldn’t be), then create a separate partition for /home and just encrypt that, so all your data is encrypted but programs don’t need to be decrypted to run. Might be slightly less secure, since logs and such might contain personal data and won’t be encrypted, but it’s a lot better than nothing.
Paul Ducklin
We covered this issue in the article. We recommend just encrypting everything,
Matt
D’oh! Reading fail.
The Hermit
For browser privacy I strongly disagree with the recommendations above… Alone they are great but together they interfere with each other and leave gaps in your security. This is noticeable in cookies. I encourage noscript with ad block edge, which is adblock plus before they started selling immunity to advertisers. Privacy badger is decent but not necessary with a strict no script policy. Using Firefox you should go to preferences>privacy>”use custom settings for history” uncheck accept cookies from site and start your own whitelist of what you want to accept and from who. This is a headache at first as you have to fix most website functionality but after established will make for a more secure `privacy` browsing experience.
if you already have cookies ie the persistent google tracking cookie remove $HOME/.mozilla/’WHATEVERYOURUIDIS’/cookies.sqlite with firefox closed
doing this will force firefox to recreate the empty cookies.sqlite location with an empty file the next time firefox launces.
short version:
1. strict noscript
2. ad block edge
3. whitelist cookies ONLY
slarocque
SAV for Linux Basic supports RHEL and CentOS (both designed for servers) but not Fedora? Fedora is part of the same family and is used by desktop linux users extensively.
Since the title of this article is “5 tips to improve your Linux desktop security”, it would be very good to hear if it works for fedora as well (and if not, then when?)
Thanks.
Paul Ducklin
SAV for Linux (Basic or not) carries round a raft of precompiled kernel drivers that it will use if you have a stock kernel and module set from one of a list of (predominantly business-focused) distros.
But it also includes the source code of the kernel driver and will compile it, or attempt to, on any Linux system that doesn’t have a known kernel. So even if you have Red Hat but have rebuilt your own kernel, SAV will probably rebuild its drivers anyway.
Try it on Fedora, assuming you have the compiler tools and the kernel headers installed. I bet you it works just fine. If it doesn’t, I’ll eat my hat…
PS. As implied in the banner ad at the bottom of the article, and confirmed when you click through to the download page: “Sophos Antivirus for Linux provides pre-compiled support for a wide range of Linux distributions and kernels, including 64-bit versions. Have a customized Linux installation? Not a problem. Sophos Antivirus for Linux supports customized Linux distributions and kernels.”