By Andrew Brandt
A new ransomware that calls itself MegaCortex got a jolt of life on Wednesday as we detected a spike in the number of attacks against Sophos customers around the world, including in Italy, the United States, Canada, the Netherlands, Ireland, and France. The attackers delivering this new malware campaign employed sophisticated techniques in the attempt to infect victims.
The convoluted infection methodology MegaCortex employs leverages both automated and manual components, and appears to involve a high amount of automation to infect a greater number of victims. In attacks we’ve investigated, the attackers used a common red-team attack tool script to invoke a meterpreter reverse shell in the victim’s environment. From the reverse shell, the infection chain uses PowerShell scripts, batch files from remote servers, and commands that only trigger the malware to drop encrypted secondary executable payloads (that had been embedded in the initial dropped malware) on specified machines.
The attack was triggered, in at least one victim’s environment, from a domain controller inside an enterprise network whose administrative credentials the attacker seems to have obtained, in what appears to be a hands-on break in.
The malware’s name is a misspelled homage to the faceless, bureaucratic corporation where the character Neo worked in the first Matrix movie. The ransom note reads like it was written in the voice and cadence of Lawrence Fishburne’s character, Morpheus.
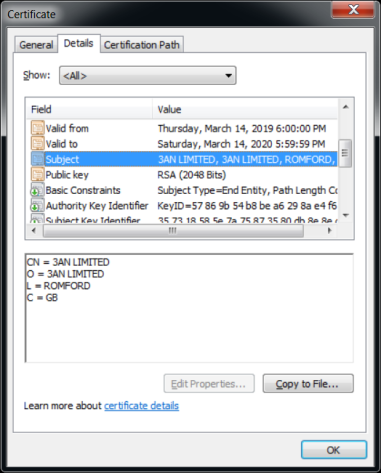
The ransom note’s cinematic fanboyism is not its sole reference to the past. The digitally-signed executable payload used to perform the encryption has been signed by a certificate with an identical Common Name (CN) as signed executables we’ve found that date back to November, 2018 though we’re still looking to see if they’re anything like the more recent samples. Searching on this CN, we’ve found several more samples in our repository that appear to be related to this same attacker.
The malware also employs the use of a long batch file to terminate running programs and kill a large number of services, many of which appear to be related to security or protection, which is becoming a common theme among current-generation ransomware families.
Looking back into malware repositories, we found a sample uploaded to VirusTotal from the Czech Republic on January 22. This appears to be the earliest known sample submitted to a public malware sharing service, but we’ve found files in our own repository with identical Common Name values. We first saw reports of the malware triggering alerts from customers dating back to February, but no major infections, and reports came only in dribs and drabs until the big spike on May 1st.
There have been (so far) 76 confirmed attacks stopped by Intercept X since February, with 47 of those (or about two thirds of the known incidents) happening in the past 48 hours. Each attack targeted an enterprise network and may have involved hundreds of machines.
While the ransom note doesn’t mention a price the criminals are demanding, they do offer the victims “a consultation on how to improve your companies (sic) cyber security” and “a guarantee that your company will never be inconvenienced by us” — you know, in the future, after this really big inconveniencing they’re engaged in is all through.
With the numbers of attempted infections rising, we assembled a team of malware analysts and support staff to tackle the initial analysis of the attack and its aftermath.
How MegaCortex strikes
Right now, we can’t say for certain whether the MegaCortex attacks are being aided and abetted by the Emotet malware, but so far in our investigation (which is still ongoing as this post goes live), there seems to be a correlation between the MegaCortex attacks and the presence on the same network of both Emotet and Qbot (aka Qakbot) malware.
Both of these malware families have the ability to serve as a delivery vehicle for other malware payloads, with Emotet closely associated with the Trickbot credential stealing malware, which also can download and install additional malware payloads to infected computers. We’ve seen no direct evidence that either Emotet or Qbot are the source.
Instead, victims report the attack was initiated from a compromised domain controller.
The attacker, using stolen admin creds, executed a PowerShell script that was heavily obfuscated.

Stripping back three layers of obfuscation reveals a series of commands that decodes a blob of base64-encoded data. The blob appears to be a Cobalt Strike script that opens a Meterpreter reverse shell into the victim’s network.

The attacker issues commands via the compromised domain controller (DC), which the attacker is remotely accessing using the reverse shell.
The DC uses WMI to push the malware — a copy of PsExec renamed rstwg.exe, the main malware executable, and a batch file — to the rest of the computers on the network that it can reach, and then runs the batch file remotely via PsExec.
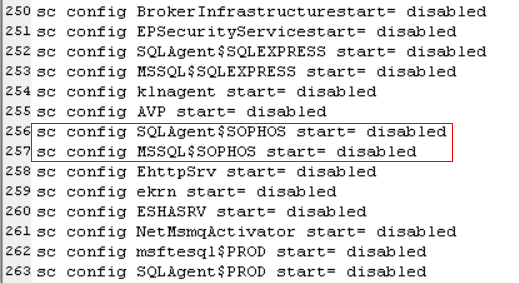
The batch file appears to be just a long list of commands to kill 44 processes, issue stop commands to 189 different services, and switch the Startup Type for 194 different services to Disabled, which prevents them from starting up again.
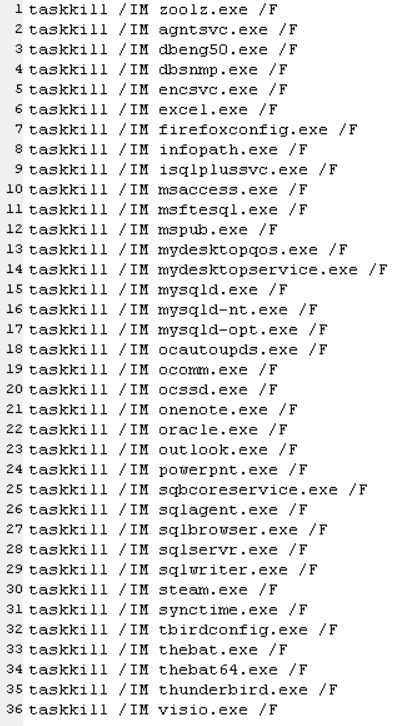
The attackers target a lot of security software, including some Sophos services, to stop them and try to set them to Disabled, but a properly configured installation won’t allow this.
The final step of the batch file is to launch the previously-downloaded executable, winnit.exe. The batch file executes winnit with a command flag that is a chunk of base64-encoded data.
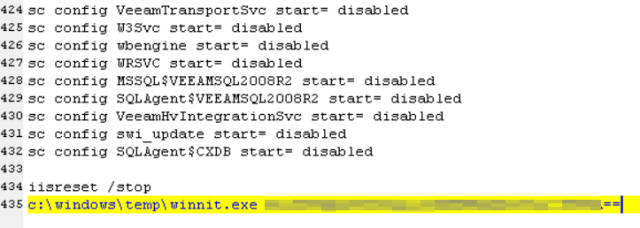
This command invokes winnit.exe to drop and execute a DLL payload with an eight-random-alphabetic character filename that performs the hostile encryption. There are also indications the attackers use other batch files, named with the numbers 1.bat through 6.bat, that are being used to issue commands to distribute the winnit.exe and the “trigger” batch file around the victim’s network.
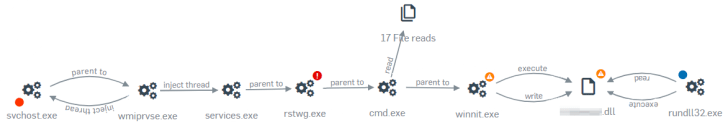
The attacker’s killchain as visualized in Sophos Intercept X
The ransom demand
In typical fashion, the ransom notification appears on the root of the victim’s hard drive as a plain text file. We’ve displayed it in an inverted color scheme to go with the mood the attacker sets by making Matrix movie references.
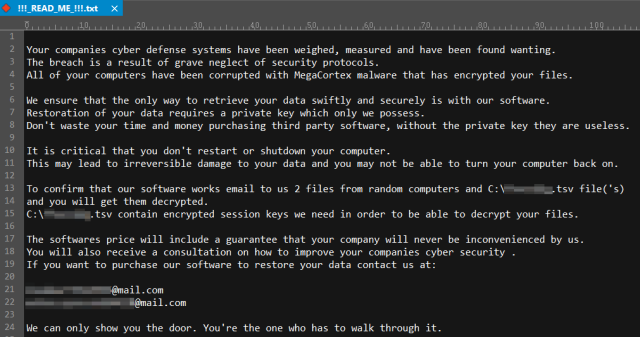
The ransomware generates a file with a .tsv file extension and the same eight-random-letter filename as the malicious DLL, and drops it to the hard drive. The ransom demand asks that a victim submit this file with their request to pay the ransom, sent to either of two free mail.com email addresses.
We’ll have more on this ransomware and its attack characteristics as our researchers continue to work on the case.
Recommended protection for MegaCortex
We’re still trying to develop a clearer picture of the infection process, but for now, it appears that there’s a strong correlation between the presence of MegaCortex, and a pre-existing, ongoing infection on the victims’ networks with both Emotet and Qbot. If you are seeing alerts about Emotet or Qbot infections, those should take a high priority. Both of those bots can be used to distribute other malware, and it’s possible that’s how the MegaCortex infections got their start.
We have not seen any indication so far that Remote Desktop Protocol (RDP) has been abused to break into the customer networks, but we know that holes in enterprise firewalls that allow people to connect to RDP remain relatively common. We strongly discourage this practice and suggest that any IT admin who wishes to do this put the RDP machine behind a VPN.
As the attack seems to indicate that an administrative password was abused by the criminals, we also recommend the widespread adoption of two-factor authentication for everything that currently requires just a password, and can use 2FA.
Keeping regular backups of your most important and current data on an offline storage device is the best way to avoid having to pay a ransom altogether.
And please remember, while it can be ill-advised to take security recommendations from a criminal in the act of holding your data hostage, the criminals who have broken into a network and attempted to encrypt hundreds of endpoints promise that they’ll never, ever do it again, pinky swear, if you just pay the ransom. I’m not so sure I believe them, but if you’re a victim, you may not have any other choice.
Sophos Antivirus detects these samples as Bat/Agent-BBIY, Troj/Agent-BBIZ, Troj/Agent-BAWS, and Troj/Ransom-FJQ. Sophos’ Intercept X protects customers from the attack.
Research for this report was contributed by SophosLabs and Sophos Support team members Anand Ajjan, Sergio Bestulic, Faizul Fahim, Sean Kowalenko, Savio Lau, Andrew Ludgate, Peter Mackenzie, Chee Hui. Tan, and Michael Wood.
IoCs
IP address/domains
Meterpreter’s reverse shell C2 address
89.105.198.28
File hashes
Batch script:
37b4496e650b3994312c838435013560b3ca8571
PE EXE:
478dc5a5f934c62a9246f7d1fc275868f568bc07
Secondary DLL memory injector:
2f40abbb4f78e77745f0e657a19903fc953cc664
Leave a Reply