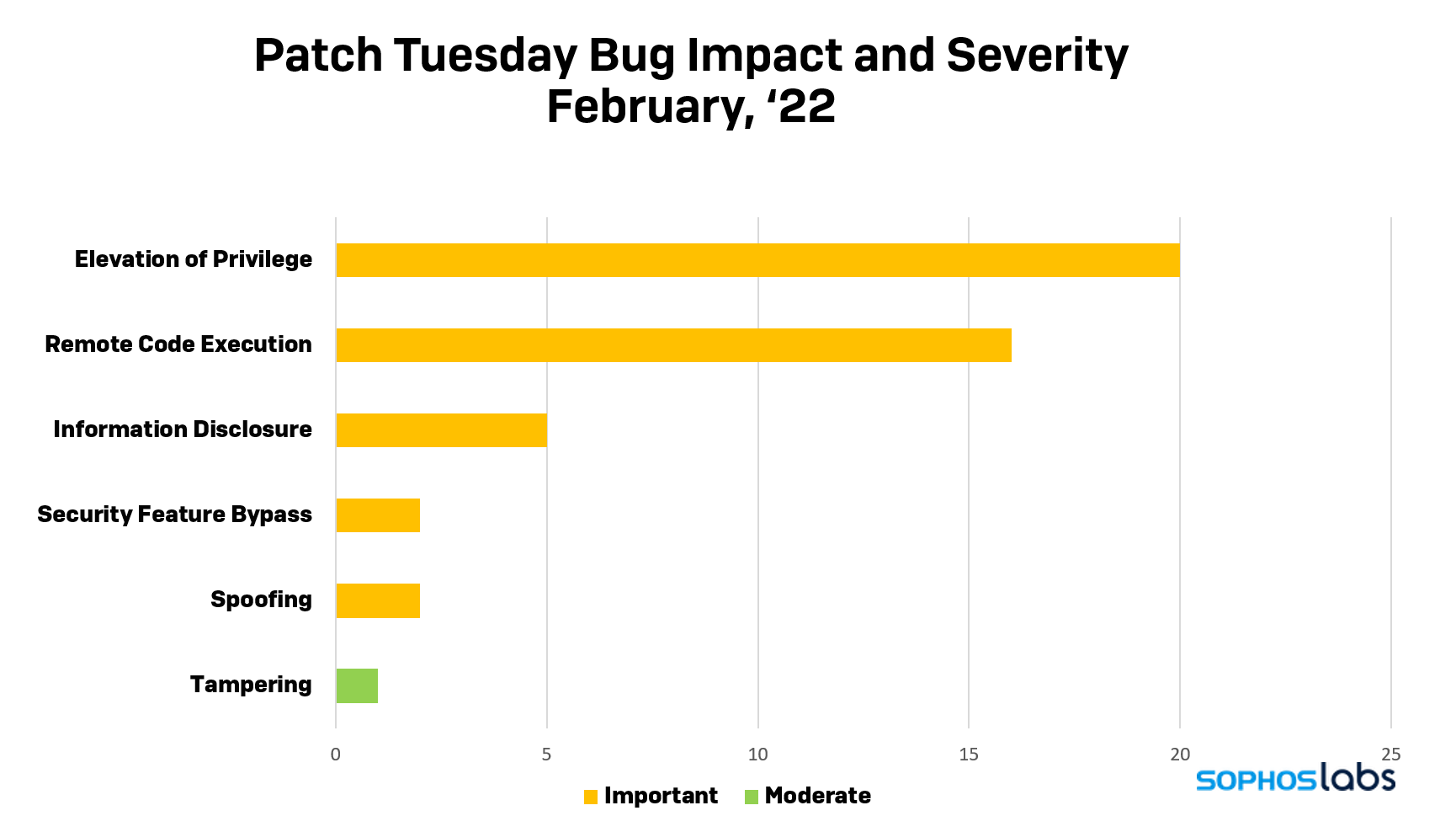
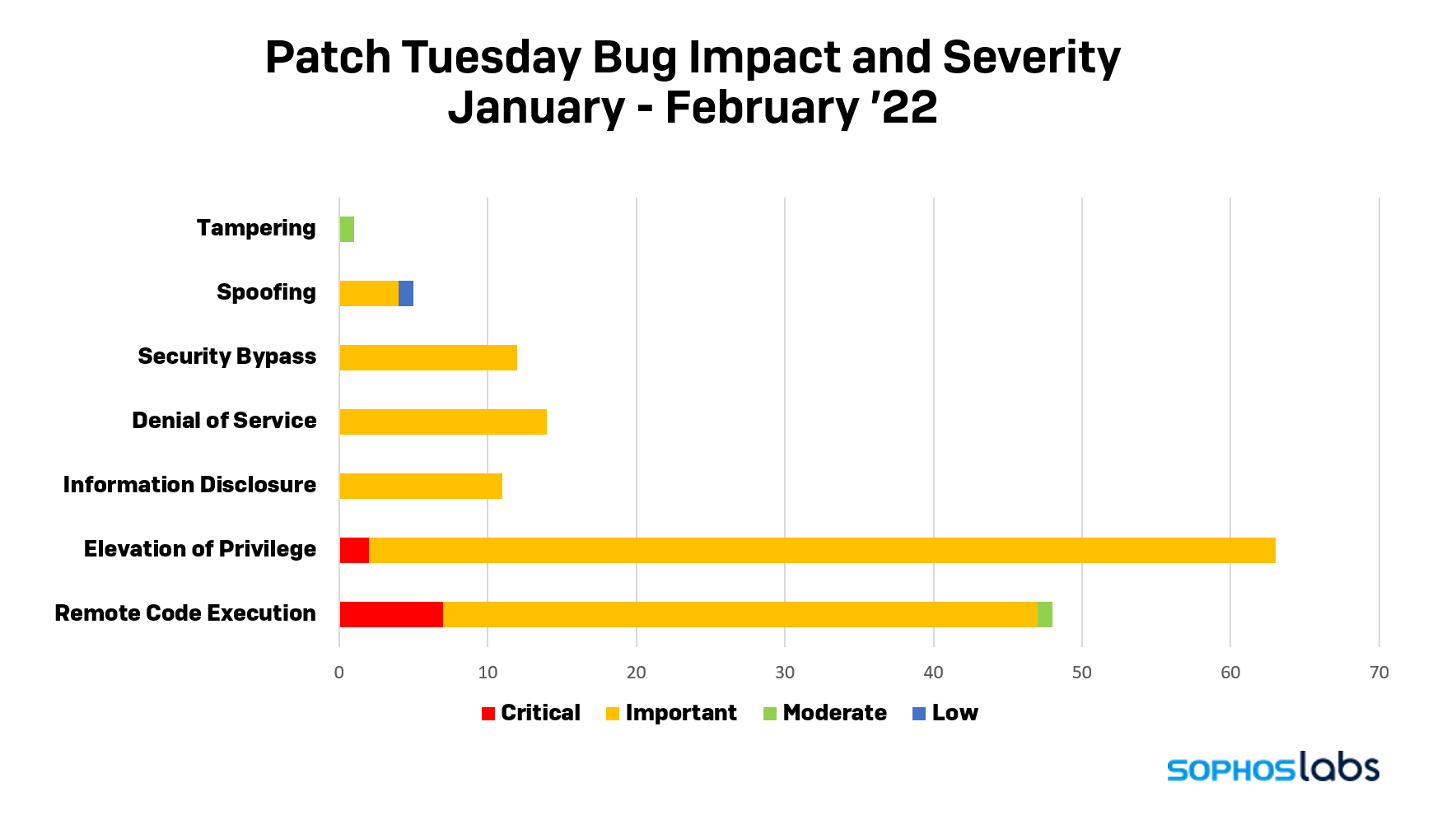
February 2022 provides a month of some respite after two relatively heavy and challenging months. After fixing 64 vulnerabilities in December 2021 and fixing over 100 in January 2022, February presents 52 vulnerabilities.
February is also a quieter month, since at the time of release Microsoft rated none of the vulnerabilities critical. Only one is listed as being publicly known (still not critical), and none have been publicly exploited, according to the company.
However, it’s not a month off: This month’s patches fix Microsoft Windows, Office, Microsoft Dynamics, the Edge browser, Microsoft Visual Studio, and some lesser known products. Three of the vulnerabilities affecting Visual Studio and Windows are notable.
Also, Microsoft has just announced a major change in how some Microsoft Office applications will handle macros in documents that come from the internet: VBA macros obtained from the internet will now be blocked by default. This change will be rolled out starting in April, 2022 with Version 2203.
Notable Vulnerabilities
Windows DNS Server Remote Code Execution Vulnerability
CVE-2022-21984
While this vulnerability is rated as “Important”, organizations that use Active Directory may want to prioritize this as a “Critical” update. This affects all instances of Windows DNS server, including those running Active Directory. Microsoft notes that there are at best, only partial mitigations to this vulnerability. Applying the update is the only thorough remedy.
Based on the information provided about this CVE by Microsoft, it appears to be a SYSTEM-level code execution vulnerability in Microsoft’s DNS server, meaning that it’s network-based. This would seem to indicate that a successful compromise of an Active Directory server using this could potentially give attackers control over Active Directory, putting the full network at risk.
It is listed as “Exploitation Less Likely” for both the latest and older software releases. It’s also not publicly disclosed. And the credits indicate that this is an internal find by the Microsoft Offensive Research & Security Engineering (MORSE). All of these mitigate the risks of active attacks against this vulnerability, at least in the near-term.
CVE-2022-21991 Visual Studio Code Remote Development Extension Remote Code Execution Vulnerability
Developers and those who manage developer environments should note there are two Visual Studio vulnerabilities this month, and CVE-2022-21991 is particularly notable.
This affects the Visual Studio Code Remote Development Extension. Microsoft’s page notes “The Remote Development extension pack allows you to open any folder in a container, on a remote machine, or in the Windows Subsystem for Linux (WSL) and take advantage of VS Code’s full feature set.”
Microsoft notes regarding this vulnerability that “[a]n attacker would need to send a specially crafted request to a host running the Visual Studio Code Remote Development Extension. This issue only affects systems configured to host a remote development environment.”
While this means only those development environments that have installed this are at risk, it also means that development environments that have installed this tool to enable remote development are at risk for a network-based code execution attack. A successful attack could potentially put anything in that development environment at risk, including but not limited to source code, tools, documents or any other resources housed in that remote-enabled development environment.
The ramifications of this are that development environments that use the Visual Studio Code Remote Development Extension could be at risk from attacks targeting the integrity of the source code they develop, as we’ve seen in some supply-chain attacks over the years.
It’s also worth noting CVE-2022-21986 Kestrel Web Server Denial of Service Vulnerability which also affects Visual Studio. In this case, it impacts the Kestrel web server that is part of Visual Studio 2017 for Mac.
Microsoft Dynamics GP and Microsoft Dynamics 365 (on-premises)
There are six vulnerabilities that affect customers using older and on-premises versions of Microsoft Dynamics: Microsoft Dynamics GP, a predecessor of the current Microsoft Dynamics 365 and the on-premises version of Microsoft Dynamics 365. Both products are subject to remote code execution vulnerabilities. Because Microsoft Dynamics customers can include small-to-medium businesses (SMBs) who may not have a regular patching program in place, these are important updates to call out.
Windows Kernel Elevation of Privilege Vulnerability
CVE-2022-21989
This is the one vulnerability that is publicly known. It’s also rated as “Exploitation” likely for both the latest and older versions of Windows. This is an elevation of privilege (EoP) vulnerability affecting AppContainer. A successful attack could elevate privileges from a container and execute code or access resources at a higher integrity level than that AppContainer’s execution environment.
Microsoft Windows
All total, 26 of this month’s vulnerabilities apply to various versions of Microsoft Windows. All are rated as “Important”. None are publicly disclosed and none are publicly exploited at the time of release.
As noted earlier, one of these (CVE-2022-21984) affects Windows DNS and another (CVE-2022-21989) is a publicly known EoP kernel vulnerability rated as “likely” to be exploited. Additional key points regarding the other Windows vulnerabilities include:
- One vulnerability, CVE-2022-21996 – Win32k Elevation of Privilege Vulnerability, applies to Windows 11 only.
- There are four vulnerabilities (CVE-2022-22717, CVE-2022-22718, CVE-2022-21997 CVE-2022-21999) affecting the Print Spooler, a component that has been under attack and scrutiny since the PrintNightmare situation began in late June 2021. It’s worth noting these are all EoP vulnerabilities, and none have been publicly disclosed nor have they been publicly exploited, as far as Microsoft knows.
- There are four vulnerabilities (CVE-2022-21981, CVE-2022-22710, CVE-2022-21998, CVE-2022-22000) affecting the Windows Common Log File System Driver. Two are EoPs, one is a Denial of Service (DoS), and one Information Disclosure
- Four vulnerabilities (CVE-2022-22709, CVE-2022-21844, CVE-2022-21926, CVE-2022-21927) affect Microsoft Windows Codecs Library.
- Two vulnerabilities (CVE-2022-22712, CVE-2022-21995) affect Hyper-V, including one RCE vulnerability.
- Two vulnerabilities (CVE-2022-21985, CVE-2022-22001) affecting Remote Access Connection Manager: an Information Disclosure and an EoP vulnerability.
- One RCE vulnerability (CVE-2022-21992) affecting Windows Mobile Device Management
- One EoP vulnerability (CVE-2022-21994) affecting Windows DWM Core Library (Desktop Window Manager).
- One information disclosure vulnerability (CVE-2022-21993) affecting the NFS ONCRPC XDR kernel mode driver.
- One EoP vulnerability (CVE-2022-22715) affecting Named Pipes.
- One RCE vulnerability (CVE-2022-21971) affecting the Windows runtime.
- One RCE vulnerability (CVE-2022-21974) affecting the Windows Roaming Security RMS (RMSRoamingSecurity.dll).
- One DoS vulnerability (CVE-2022-22002) affecting the Windows User Account Profile Picture.
The full list of vulnerabilities that are applicable to Microsoft Windows is listed below.
| 1. | CVE-2022-21844 | HEVC Video Extensions Remote Code Execution Vulnerability | Remote Code Execution |
| 2. | CVE-2022-21926 | HEVC Video Extensions Remote Code Execution Vulnerability | Remote Code Execution |
| 3. | CVE-2022-21927 | HEVC Video Extensions Remote Code Execution Vulnerability | Remote Code Execution |
| 4. | CVE-2022-22715 | Named Pipe File System Elevation of Privilege Vulnerability | Elevation of Privilege |
| 5. | CVE-2022-21974 | Roaming Security Rights Management Services Remote Code Execution Vulnerability | Remote Code Execution |
| 6. | CVE-2022-22709 | VP9 Video Extensions Remote Code Execution Vulnerability | Remote Code Execution |
| 7. | CVE-2022-21996 | Win32k Elevation of Privilege Vulnerability | Elevation of Privilege |
| 8. | CVE-2022-22710 | Windows Common Log File System Driver Denial of Service Vulnerability | Denial of Service |
| 9. | CVE-2022-21981 | Windows Common Log File System Driver Elevation of Privilege Vulnerability | Elevation of Privilege |
| 10. | CVE-2022-22000 | Windows Common Log File System Driver Elevation of Privilege Vulnerability | Elevation of Privilege |
| 11. | CVE-2022-21998 | Windows Common Log File System Driver Information Disclosure Vulnerability | Information Disclosure |
| 12. | CVE-2022-21984 | Windows DNS Server Remote Code Execution Vulnerability | Remote Code Execution |
| 13. | CVE-2022-21994 | Windows DWM Core Library Elevation of Privilege Vulnerability | Elevation of Privilege |
| 14. | CVE-2022-22712 | Windows Hyper-V Denial of Service Vulnerability | Denial of Service |
| 15. | CVE-2022-21995 | Windows Hyper-V Remote Code Execution Vulnerability | Remote Code Execution |
| 16. | CVE-2022-21989 | Windows Kernel Elevation of Privilege Vulnerability | Elevation of Privilege |
| 17. | CVE-2022-21992 | Windows Mobile Device Management Remote Code Execution Vulnerability | Remote Code Execution |
| 18. | CVE-2022-21997 | Windows Print Spooler Elevation of Privilege Vulnerability | Elevation of Privilege |
| 19. | CVE-2022-21999 | Windows Print Spooler Elevation of Privilege Vulnerability | Elevation of Privilege |
| 20. | CVE-2022-22717 | Windows Print Spooler Elevation of Privilege Vulnerability | Elevation of Privilege |
| 21. | CVE-2022-22718 | Windows Print Spooler Elevation of Privilege Vulnerability | Elevation of Privilege |
| 22. | CVE-2022-22001 | Windows Remote Access Connection Manager Elevation of Privilege Vulnerability | Elevation of Privilege |
| 23. | CVE-2022-21985 | Windows Remote Access Connection Manager Information Disclosure Vulnerability | Information Disclosure |
| 24. | CVE-2022-21971 | Windows Runtime Remote Code Execution Vulnerability | Remote Code Execution |
| 25. | CVE-2022-21993 | Windows Services for NFS ONCRPC XDR Driver Information Disclosure Vulnerability | Information Disclosure |
| 26. | CVE-2022-22002 | Windows User Account Profile Picture Denial of Service Vulnerability | Denial of Service |
Microsoft Office
Eleven vulnerabilities affect Microsoft Office. All are rated as “Important.” None are publicly disclosed and none are publicly exploited at the time of release.
- Three RCE vulnerabilities (CVE-2022-22003, CVE-2022-23252, CVE-2022-22004) affect Microsoft Office.
- Thee vulnerabilities (CVE-2022-21987, CVE-2022-21968, CVE-2022-22005) affect Microsoft SharePoint and include one RCE, one EoP and one spoofing vulnerability.
- One DoS vulnerability (CVE-2022-21965) affects Microsoft Teams.
- One information disclosure vulnerability (CVE-2022-22716) affects Microsoft Excel.
- One RCE vulnerability (CVE-2022-21988) affects Microsoft Visio.
- One security feature bypass (CVE-2022-23255) affects Microsoft OneDrive for Android.
- One security feature bypass (CVE-2022-23280) affects Microsoft Outlook for Mac. This vulnerability has a no-user-interaction preview pane attack vector however the main impact appears to be exposing the IP address of the target: code execution is possible.
The full list of vulnerabilities that are applicable to Microsoft Office is listed below.
| 1. | CVE-2022-21965 | Microsoft Teams Denial of Service Vulnerability | Denial of Service |
| 2. | CVE-2022-21968 | Microsoft SharePoint Server Security Feature BypassVulnerability | Elevation of Privilege |
| 3. | CVE-2022-21987 | Microsoft SharePoint Server Spoofing Vulnerability | Spoofing |
| 4. | CVE-2022-21988 | Microsoft Office Visio Remote Code Execution Vulnerability | Remote Code Execution |
| 5. | CVE-2022-22003 | Microsoft Office Graphics Remote Code Execution Vulnerability | Remote Code Execution |
| 6. | CVE-2022-22004 | Microsoft Office ClickToRun Remote Code Execution Vulnerability | Remote Code Execution |
| 7. | CVE-2022-22005 | Microsoft SharePoint Server Remote Code Execution Vulnerability | Remote Code Execution |
| 8. | CVE-2022-22716 | Microsoft Excel Information Disclosure Vulnerability | Information Disclosure |
| 9. | CVE-2022-23252 | Microsoft Office Information Disclosure Vulnerability | Information Disclosure |
| 10. | CVE-2022-23255 | Microsoft OneDrive for Android Security Feature Bypass Vulnerability | Security Feature Bypass |
| 11. | CVE-2022-23280 | Microsoft Outlook for Mac Security Feature Bypass Vulnerability | Security Feature Bypass |
Microsoft Dynamics
Five of the six vulnerabilities this month affect Microsoft Dynamics GP, a predecessor of the current Microsoft Dynamics 365. One affects Microsoft Dynamics 365 but the on-premises version only.
One of the Microsoft Dynamics GP vulnerabilities is an RCE (CVE-2022-23274), three are EoPs (CVE-2022-23271, CVE-2022-23272, CVE-2022-23273) and the last one is a spoofing vulnerability (CVE-2022-23269).
Microsoft Dynamics 365 is also affected by an RCE (CVE-2022-21957) but it’s important to note this only affects the on-premises version of the product.
The full list of vulnerabilities that are applicable to Microsoft Dynamics is listed below.
| 1. | CVE-2022-21957 | Microsoft Dynamics 365 (on-premises) Remote Code Execution Vulnerability | Remote Code Execution |
| 2. | CVE-2022-23269 | Microsoft Dynamics GP Spoofing Vulnerability | Spoofing |
| 3. | CVE-2022-23271 | Microsoft Dynamics GP Elevation Of Privilege Vulnerability | Elevation of Privilege |
| 4. | CVE-2022-23272 | Microsoft Dynamics GP Elevation Of Privilege Vulnerability | Elevation of Privilege |
| 5. | CVE-2022-23273 | Microsoft Dynamics GP Elevation Of Privilege Vulnerability | Elevation of Privilege |
| 6. | CVE-2022-23274 | Microsoft Dynamics GP Remote Code Execution Vulnerability | Remote Code Execution |
Microsoft Edge
There are four vulnerabilities affecting the Chromium-based Microsoft Edge. Two “Important” rated EoPs (CVE-2022-23262 and CVE-2022-23263), one “Moderate” rated Tampering vulnerability, and one “Low” rated Spoofing vulnerability.
In addition to these vulnerabilities affecting Edge, specifically, Microsoft also published guidance that they have incorporated fixes to a range of CVEs affecting the underlying Chromium engine. The company says “no action is required” to address the 19 bugs (CVE-2021-0452 through CVE-2021-0470) affected. Between these and the 51 bugs specific to Microsoft patches, these bring the total number of fixes in February to 70.
The full list of vulnerabilities that are applicable to Microsoft Edge is listed below.
| 1. | CVE-2022-23261 | Microsoft Edge (Chromium-based) Tampering Vulnerability | Tampering |
| 2. | CVE-2022-23262 | Microsoft Edge (Chromium-based) Elevation of Privilege Vulnerability | Elevation of Privilege |
| 3. | CVE-2022-23263 | Microsoft Edge (Chromium-based) Elevation of Privilege Vulnerability | Elevation of Privilege |
| 4. | CVE-2022-23264 | Microsoft Edge (Chromium-based) Spoofing Vulnerability | Spoofing |
Microsoft Visual Studio
Two vulnerabilities affect Microsoft Visual Studio: one RCE (CVE-2022-21991) and one DoS (CVE-2022-21986) discussed above.
The full list of vulnerabilities that are applicable to Visual Studio is listed below.
| 1. | CVE-2022-21991 | Visual Studio Code Remote Development Extension Remote Code Execution Vulnerability | Remote Code Execution |
| 2. | CVE-2022-21986 | Kestrel Web Server Denial of Service Vulnerability | Denial of Service |
Other Products
The other products are affected by EoPs and include the Azure Data Explorer (CVE-2022-23256), Microsoft Power BI (CVE-2022-23254) and SQL Server 2019 for Linux Containers (CVE-2022-23276).
The full list of vulnerabilities that are applicable to other products is listed below.
| 1. | CVE-2022-23256 | Azure Data Explorer Spoofing Vulnerability | Elevation of Privilege |
| 2. | CVE-2022-23254 | Microsoft Power BI Elevation of Privilege Vulnerability | Elevation of Privilege |
| 3. | CVE-2022-23276 | SQL Server for Linux Containers Elevation of Privilege Vulnerability | Elevation of Privilege |
Exploitability Indexes
Below are the Exploitability Indexes for this month’s release, at the time of release.
Exploitation More Likely for Latest Versions
| CVE-2022-21981 | Windows Common Log File System Driver Elevation of Privilege Vulnerability |
| CVE-2022-21994 | Windows DWM Core Library Elevation of Privilege Vulnerability |
| CVE-2022-21996 | Win32k Elevation of Privilege Vulnerability |
| CVE-2022-21999 | Windows Print Spooler Elevation of Privilege Vulnerability |
| CVE-2022-22000 | Windows Common Log File System Driver Elevation of Privilege Vulnerability |
| CVE-2022-22005 | Microsoft SharePoint Server Remote Code Execution Vulnerability |
| CVE-2022-22715 | Named Pipe File System Elevation of Privilege Vulnerability |
| CVE-2022-22718 | Windows Print Spooler Elevation of Privilege Vulnerability |
| CVE-2022-21989 | Windows Kernel Elevation of Privilege Vulnerability |
Exploitation More Likely for Older Versions
| CVE-2022-21981 | Windows Common Log File System Driver Elevation of Privilege Vulnerability |
| CVE-2022-21994 | Windows DWM Core Library Elevation of Privilege Vulnerability |
| CVE-2022-21999 | Windows Print Spooler Elevation of Privilege Vulnerability |
| CVE-2022-22000 | Windows Common Log File System Driver Elevation of Privilege Vulnerability |
| CVE-2022-22005 | Microsoft SharePoint Server Remote Code Execution Vulnerability |
| CVE-2022-22715 | Named Pipe File System Elevation of Privilege Vulnerability |
| CVE-2022-22718 | Windows Print Spooler Elevation of Privilege Vulnerability |
| CVE-2022-21989 | Windows Kernel Elevation of Privilege Vulnerability |
Sophos protection
| CVE | SAV |
| CVE-2022-21989 | Exp/2221989-A |
| CVE-2022-21996 | Exp/2221996-A |
| CVE-2022-22715 | Exp/2222715-A |
As you can do every month, if you don’t want to wait for your system to pull down the updates itself, you can download them manually from the Windows Update Catalog website. Run the winver.exe tool to determine which build of Windows 10 or 11 you’re running, then download the Cumulative Update package for your particular system architecture and build number.