Update (2022-01-18): Microsoft has released an out-of-band (OOB) patch one week later that fixes some issues caused by the cumulative updates that were published on Patch Tuesday. The problems affect native VPN connectivity in the operating system, as well as issues where Server domain controllers restart unexpectedly, virtual machines fail to start, or ReFS-formatted removable media fails to mount. If you’ve experienced any of these issues, check the Update Catalog site (linked below) for details.
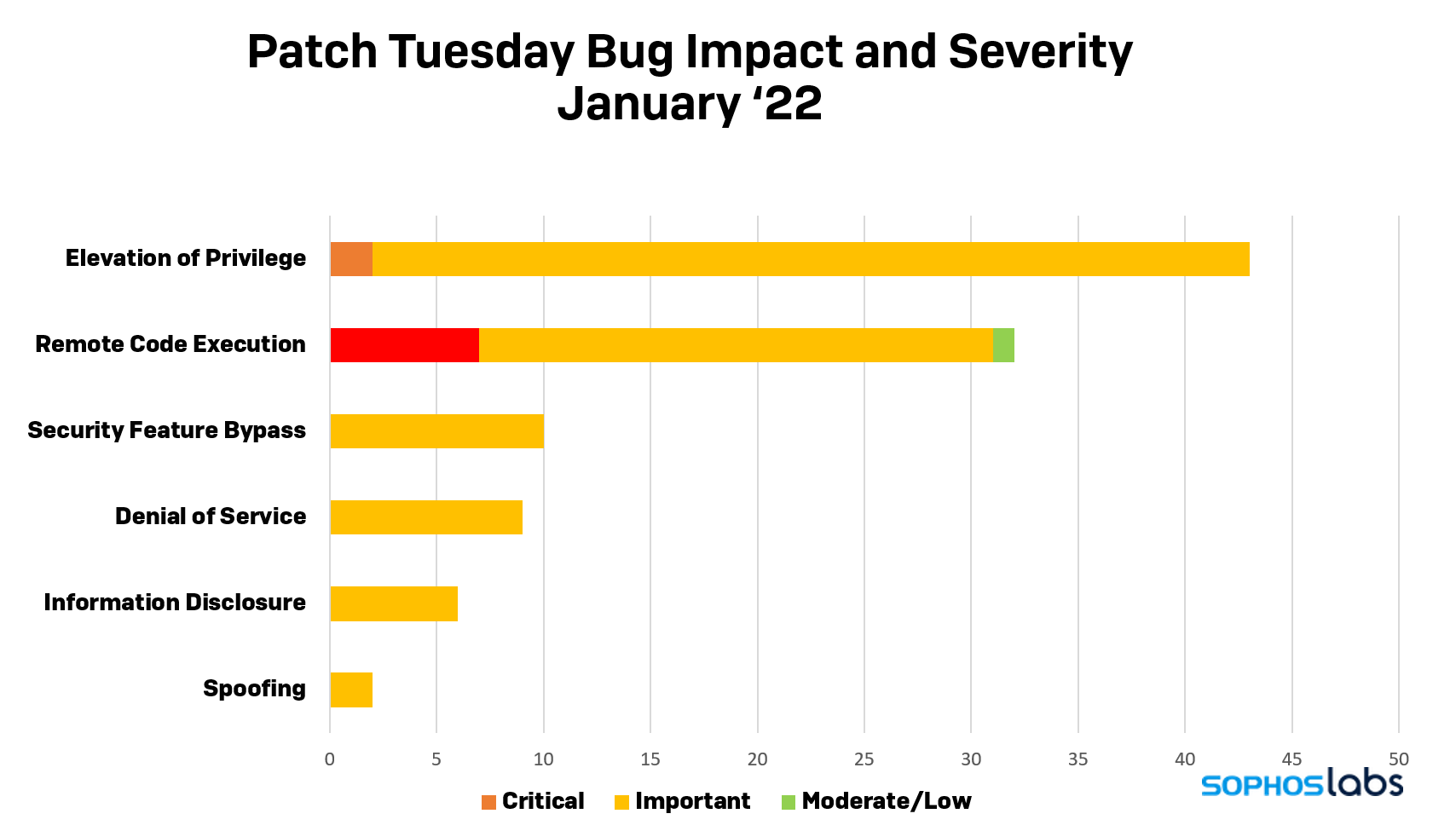
The volume of fixes issued in the first Patch Tuesday release of 2022 breaks into the triple-digits, with nine critical fixes for some of Microsoft’s most popular software packages. While the 43 Elevation of Privilege (EoP) bugs in this month’s release represented the category with the highest proportion of repairs, seven of the nine critical fixes this month fall under the category of Remote Code Execution (RCE), the most worrisome type of software flaw.
Among the products getting a bump from this cumulative release are various Office applications (Word, Excel, and Sharepoint); commonly-patched Windows components like the graphics subsystem, Remote Desktop client, Edge (Chromium) browser; Windows Defender; and the core Windows kernel. But a host of less commonly-updated software packages made the cut this month as well, such as the open-source cURL, Libarchive, and BIND packages for Windows, and the Windows Resiliant File System (ReFS).
As you can do every month, if you don’t want to wait for your system to pull down the updates itself, you can download them manually from the Windows Update Catalog website. Run the winver.exe tool to determine which build of Windows 10 or 11 you’re running, then download the Cumulative Update package for your particular system and build number.
Critical Fixes
Microsoft considers the updates to nine of these packages to be of critical importance to fix, but only one of those bugs — an RCE affecting the cURL utility — has been publicly disclosed (in the list of security-related fixes for version 7.81.0 or the release video), and fortunately, as of this writing, none have been exploited by attackers (yet).
The other fixes have been made to ActiveX Directory Domain Services and the Virtual Machine IdeOpticalDriver (EoP); and to DirectX (2), Excel, Exchange Server, Windows Media, the HTTP protocol stack, and as mentioned, cURL (RCE).
Notable fixes that fall in Microsoft’s “important” category affect the Windows IKE Extension cryptographic key-exchange component of Windows, a pair of Security Feature Bypass bugs affecting Windows Defender’s Application Control and Credential Guard features, and EoPs affecting the Windows Common Log File System Driver and Event Tracing.
Here are just a few of the updates that caught our eye this month, either because they have higher than average potential to be abused, or because they fix an out-of-the-ordinary software package.
Open Source cURL RCE (or is it?)
CVE-2021-22947
The cURL command-line tool is one of the most widely-used data collection utilities on any platform, let alone on Windows. The tool is available on a wide variety of platforms, from the defunct BeOS to Windows, commonly used to retrieve web-based information or interact with web-based APIs. It’s such a useful tool that Microsoft includes a version of it with at least some builds of Windows 10. It’s actually unclear why Microsoft decided to characterize a vulnerability that would permit an attacker to MITM cURL and inject modified information into a TLS connection as remote code execution. According to the cURL website, the tool has fixed 42 security-related problems since the version 7.55.0 copy I found on my fresh install of Windows 10 version 21H1, so this seems like a long-overdue update.
Security Feature Bypasses in Windows Defender
CVE-2022-21906, -21921
The bugs affecting Windows Defender focus on two important features of the product: Credential Guard and Application Control. Credential Guard prevents malware from stealing passwords from common saved-password storage locations, while Application Control restricts which programs can run in the Windows kernel. Credential Guard runs in most versions of Windows 10 and 11, but Application Control (WDAC) is only available in specific versions of Windows. Needless to say, a bypass of either of these security features in a tool designed to keep a computer safe from just this kind of bypass would be problematic.
Security Feature Bypass in Secure Boot
CVE-2022-21894
The Secure Boot process helps guarantee the integrity of code on the boot storage device, so any compromise of this process might permit an attacker to modify a boot drive in a way that could break the trust in its integrity. Practically speaking, an attacker could prevent the machine from booting or could add their own code to the boot process. In any case, it’s also something you wouldn’t want a malicious actor to mess around with. This patch will be available to all releases of Windows from Windows 8.1 to Windows 11.
RCEs in Windows Resiliant File System (ReFS)
CVE-2022-21892, -21928, -21958, -21959, -21960, -21961, -21962, -21963
The ReFS, first released in Windows Server 2012, is a major update to (but not a replacement of) the now-legacy NTFS file system. For one thing, ReFS partitions are not bootable, but they are capable of handling extremely large files and storage capacity. For instance, ReFS disks can handle individual files as large as 1 yobibyte, four orders of magnitude larger than 1TB. An unnamed researcher found no fewer than eight remote code execution vulnerabilities and provided proof-of-concept code to Microsoft. The attack requires physical presence (i.e., the insertion of a malicious USB drive — or the mounting of a malicious virtual hard drive (VHD) — into a targeted computer), which limits the attack surface. While this mainly applies to large storage arrays you’d typically see in datacenters, fixes will be released for all versions of Windows 10 and 11, and Server versions from 2016 onward..
RCE in the HTTP protocol stack
CVE-2022-21907
Microsoft’s HTTP protocol stack is a component used to host web pages on a Windows server. An unauthenticated attacker could send a specially crafted packet to a targeted server that’s using the HTTP Protocol Stack (http.sys) to process packets, and presumably trick it into running code on their behalf. Microsoft’s notes on this bug indicate they will prioritize pushing this update to servers (versions 2019, 20H2, and 2022 are affected) but the patch will be also be part of the main update package for Windows 10 and 11 desktop machines, as well. On just Windows Server 2019 and Windows 10 build 1809, the vulnerable code is not loaded by default, but only when a certain registry key has been set. With bugs such as ProxyLogon/ProxyShell still in wide abuse, this is one you won’t want to wait to update.
Sophos protection
SophosLabs is working on several new detections in response to this advisory. The detections below complement any existing protection and generic exploit mitigation capabilities in our products. Sophos may release additional protection signatures after this article is published.
|
CVE |
SAV |
| CVE-2022-21887 | Exp/2221887-A |
| CVE-2022-21919 | Exp/2221919-A |