Customer profile: A non-profit organization based in the USA, with approximately 1,000 devices.
The Sophos Managed Threat Response (MTR) team provides customers with swift, human-led responses to the nastiest threats and most sophisticated adversaries.
The hunt begins

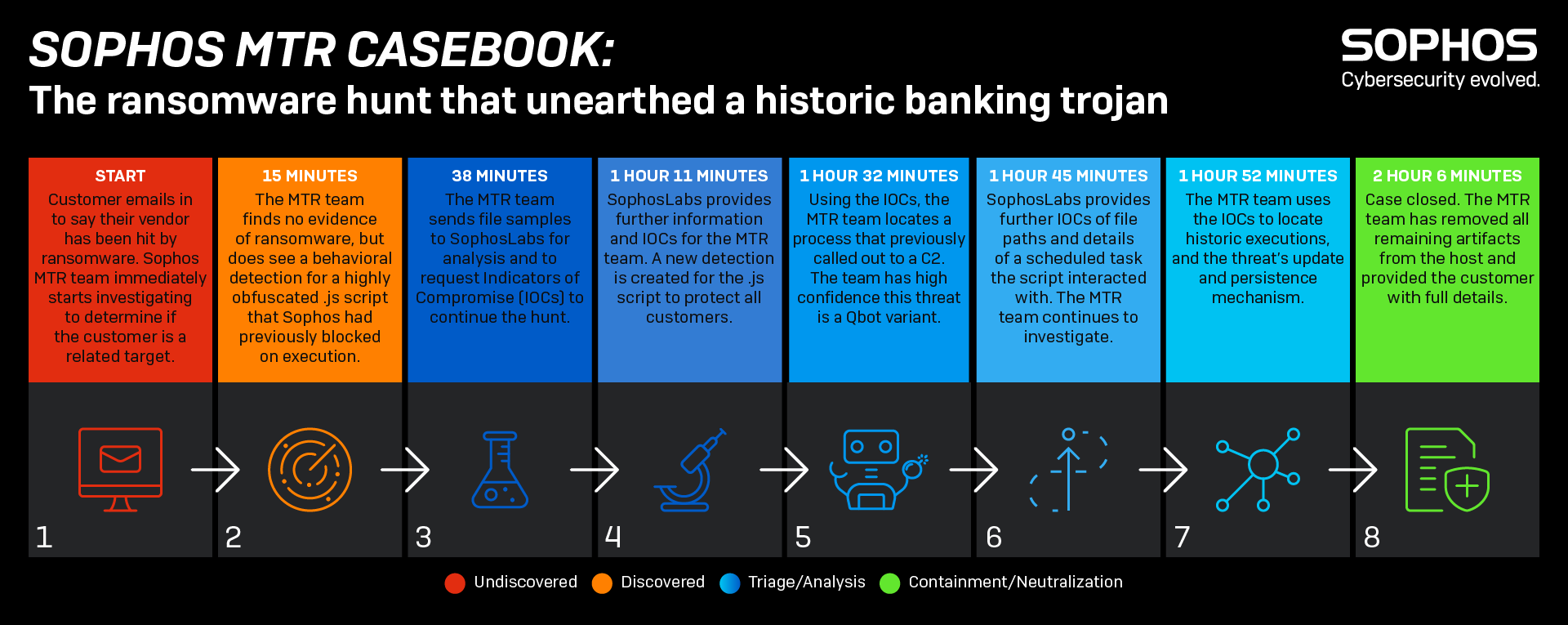
This case started with an email from a brand-new MTR customer. The customer had just heard that a third-party vendor they work with had been hit by ransomware and was worried they might also be affected.
The MTR team immediately picked up their request, opened a new case, and initiated a threat hunt. Within 15 minutes they were highly confident that there was no ransomware in the customer’s environment.
But the team did find something suspicious. Very recently, a script had been detected and blocked by the customer’s Sophos endpoint protection software.
What was odd was that it was in JavaScript which is typically used by websites to make them interactive. However, this detection wasn’t coming from a web browser – it was coming from the command line.
And it was obfuscated: someone didn’t want it to be read by human eyes.
Diving deeper
We sent the script to SophosLabs, our threat research and intelligence team, to get a deeper analysis of this script and what it was trying to do. Within minutes, SophosLabs began sharing actionable intelligence:
- The script was a downloader. It would have tried to download a malicious payload hosted at a URL. A search across network traffic data reveals the URL was never connected.
- The downloader script would have attempted to make a scheduled task.
While we couldn’t find any evidence of this task being created, we did find another suspicious-looking scheduled task that would run a different script.
This new script would attempt to find two files with the file extension .zzz and join them together into a .exe. It would then run this .exe, delete the scheduled task, delete the .zzz files, and finally delete the script.
This scheduled task was waiting to do its job but the files it was waiting for never appeared.
Situation resolved
The picture was clear. The suspect scripts and tasks belong to a variant of a banking trojan and information stealer known as Qbot. And had been running undetected on a device in the customer’s network for a very long time.
The criminals behind Qbot were trying to orchestrate the download of an update as two .zzz files in order to evade perimeter defenses, and then join them together once on the inside.
Unlucky for Qbot, we caught this process in the act.
As the customer had authorized Sophos to respond on their behalf, we cleaned up the Qbot infection, and informed the customer of what we had discovered.
The whole investigation, from the initial customer email to final clean up, took just 2 hours 6 minutes.
The customer was able to relax knowing that they hadn’t been affected by ransomware and that a historic banking malware had been fully removed.
And as this story shows, while ransomware is often the threat that is front of mind, it’s important to also be alert to the attacks that prefer to hide in the shadows.
Learn more
For more information on the Sophos MTR service visit our website or speak with a Sophos representative.
If you prefer to conduct your own threat hunts Sophos EDR gives you the tools you need for advanced threat hunting and IT security operations hygiene. Start a 30-day no obligation trial today.
