
A simple solution to a complex problem
Protecting remote and hybrid workers has been complex and expensive… until now.
Sophos Protected Browser, part of the Sophos Workspace Protection bundle, integrates all the security functions you need into a hardened Chromium browser. Get granular controls, tight security, and a transparent user experience for your hybrid or remote workers, third parties, M&A teams, or any external collaborators.

Zero Trust Network Access
Seamless in-browser integration with a rich RDP and SSH client and device posture assessment.

SaaS application control
Get control and insights into SaaS application usage and leverage data boundary controls.

Secure web gateway and DNS
Full web policy enforcement via the integrated SWG and Sophos DNS Protection (over HTTPS) using the latest AI threat intelligence from Sophos.

Hardened browser
A hardened but familiar Chromium browser provides added security against browser exploits and attacks.

Data boundary controls
With granular but easy control over copy/paste, screen captures, uploads and downloads, and data redaction capabilities.

Sophos Central management
Full Sophos Central management and reporting for all your Sophos products, including the Sophos Protected Browser.
Protect your applications
You need to provide secure access to your important business applications to those that need it, while also securing them from potential hacks and attacks. Sophos Protected Browser integrates Sophos ZTNA and SaaS app controls for a seamless and secure experience.
- ZTNA makes your apps invisible to the internet while providing secure access to all your workers on and off the network.
- ZTNA is integrated into Sophos Protected Browser for a seamless experience including direct support for SSH and RDP.
- SaaS app controls also enable you to determine who has access to important applications you rent.
- Device posture assessment and Synchronized Security support can be used in policies to temporarily block access to important applications for compromised devices.
Safely adopt Generative AI
Generative AI presents enormous opportunities to streamline workflows, but also enormous risks for exposing sensitive data. The web, DNS, and data boundary controls in Sophos Protected Browser make it easy to safely embrace the Generative AI solution you want while avoiding shadow AI usage.
- Control what Generative AI apps and services your users can access and block unsanctioned services.
- Gain visibility and insights into generative AI usage.
- Protect sensitive data from generative AI exposure by controlling copy/paste, upload, and download activities.
Protect your data
Sensitive data sharing mistakes are a common issue that can be easily prevented, even if you’re dealing with a rogue user. Sophos Protected Browser includes sophisticated data boundary controls that are easy to set up to prevent costly mistakes.
- Limit the ability to copy and paste data from select applications.
- Block taking screenshots of applications and their data.
- Prevent printing of certain application data.
- Control what can be uploaded and downloaded from the browser.
Protect your workspaces from breaches
Your remote workers, devices, and guests may be vulnerable to web browser or email attacks that attempt to exploit vulnerabilities in the browser itself, web content, or user behavior to get a foothold on your network. Sophos Protected Browser integrates a full Secure Web Gateway (SWG) and works together with Sophos DNS Protection to provide comprehensive workspace protection from attacks and breaches.
- Block malicious, risky, and unwanted websites with the integrated SWG and DNS Protection.
- Know that the browser used to access your corporate apps is hardened against attacks and exploits.
- Device assessment and Synchronized Security ensure that compromised devices are isolated until they are cleaned up.

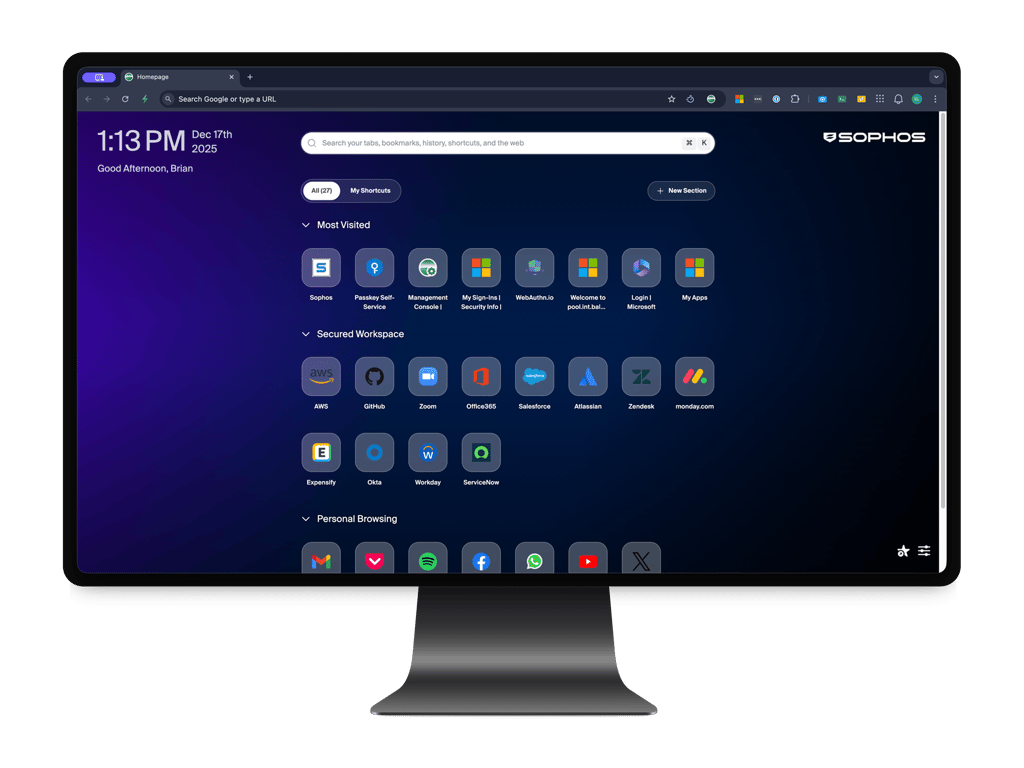
Sophos and Island.io partner to bring you Sophos Protected Browser
In partnership with Island.io and building on their strong foundation as a leader in the enterprise browser market, the Sophos Protected Browser integrates key Sophos technologies and threat intelligence, along with Sophos Central management, to provide the ideal workspace protection platform for our customers and partners.
Sophos Protected Browser — Part of Workspace Protection
Sophos Workspace Protection makes protecting your apps, data, and remote and hybrid workers easy and affordable. It includes everything you need to provide transparent secure access for those who need it — everywhere they go — while protecting it from those who don’t.

Protected Browser
One app to protect all your other apps

ZTNA
Secure access and protection for your apps
DNS Protection
An added layer of web protection across all apps.

Email Monitoring
Enhanced visibility and security for your existing email protection.
Cybersecurity for all your needs
Sophos Managed Detection and Response
- A global team of cybersecurity experts monitors your environment 24/7.
- Industry-leading threat researchers constantly discover new threat groups and attack techniques.
- Proactive threat hunting to find stealthy threats that elude detection by security tools.
- Full-scale incident response to fully eliminate adversaries. No caps or extra fees.
- Choose from a range of service tiers and threat response modes to meet your needs.
Sophos Endpoint
- Prevention first approach to block more threats upfront to minimize risk and reduce investigation and response workloads.
- Adaptive defenses that stop active adversaries with dynamic protection that automatically adapts as an attack evolves.
- Detection and response to neutralize sophisticated multi-stage attacks that can’t be stopped by technology alone.
- Streamlined management interface to focus on the threat, not administration.
Sophos Next-Gen Firewall
- Expose hidden risks with superior visibility into risky activity, suspicious traffic, and advanced threats.
- Stop unknown threats with protection technologies like deep learning and intrusion prevention that help keep your organization secure.
- Automatic threat response instantly identifies and isolates compromised systems to stop threats from spreading.
.svg?width=185&quality=80&format=auto&cache=true&immutable=true&cache-control=max-age%3D31536000)


.svg?width=13&quality=80&format=auto&cache=true&immutable=true&cache-control=max-age%3D31536000)




