The deluge of patches in April dried up substantially in May, as Microsoft on Tuesday released 59 patches touching 11 product families. Windows as usual takes the lion’s share of patches with 48, with the rest spread among .NET, 365 Apps for Enterprise, Azure, Bing Search for iOS, Dynamics 365, Intune, Office, Power BI, SharePoint, and Visual Studio. There is just one critical-severity issue, affecting SharePoint.
At patch time, two issues, both important-severity faults affecting Windows, are known to be under active exploit in the wild. Ten additional important-severity vulnerabilities in Windows and SharePoint are by the company’s estimation more likely to be exploited in the next 30 days. Eight of the issues are amenable to detection by Sophos protections, and we include information on those in a table below.
In addition to these patches, the release includes advisory information on six patches related to the Edge browser; two related to Visual Studio but managed by GitHub, not Microsoft; and four from Adobe. We don’t include advisories in the CVE counts and graphics below, but we provide information on all of them in an appendix at the end of the article. We are as usual including at the end of this post three other appendices listing all Microsoft’s patches, sorted by severity, by predicted exploitability, and by product family.
By the numbers
- Total Microsoft CVEs: 59
- Total Edge / Chrome advisory issues covered in update: 6
- Total non-Microsoft Visual Studio advisory issues covered in update: 2
- Total Adobe issues covered in update: 4
- Publicly disclosed: 2
- Exploited: 2
- Severity
- Critical: 1
- Important: 57
- Moderate: 1
- Impact:
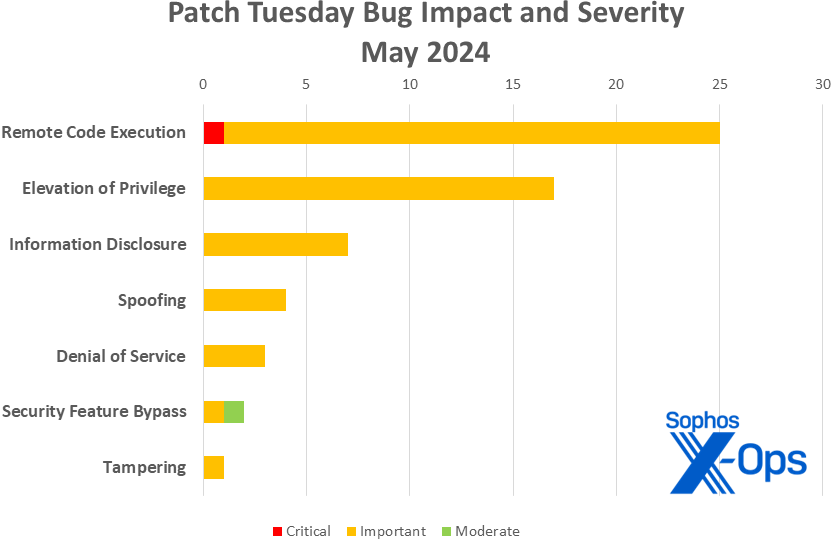
Figure 1: May continues the previous month’s emphasis on RCE issues, though all seven of Microsoft’s usual impact categories put in an appearance
Products
- Windows: 48
- Dynamics 365: 2
- SharePoint: 2
- Visual Studio: 2 (including one shared with .NET; in addition, two advisory issues apply to VS)
- .NET: 1 (shared with Visual Studio)
- 365 Apps for Enterprise: 1 (shared with Office)
- Azure: 1
- Bing Search for iOS: 1
- Intune: 1
- Office: 1 (shared with 365 Apps for Enterprise)
- Power BI: 1
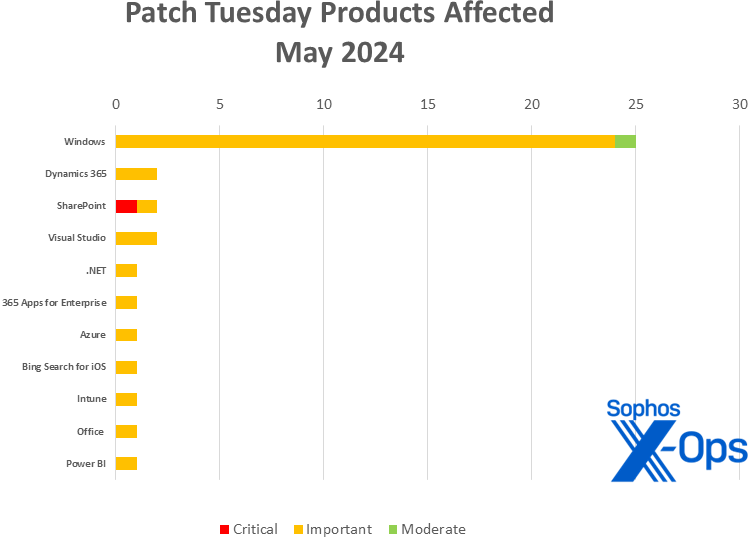
Figure 2: Windows takes the overwhelming number of May patches, but only SharePoint has a critical-severity issue to manage
Notable May updates and themes
In addition to the issues discussed above, a few specific items merit attention.
CVE-2024-4559 – Chromium: CVE-2024-4671 Use after free in Visuals
Are we really leading this section with an advisory this month? Yes. This Chrome bug was technically patched Friday (one day after an anonymous researcher reported it to Google), and it’s mentioned in Microsoft’s Patch Tuesday release simply to assure Edge users that the latest version addresses this high-severity issue. That said, Edge – and all browsers using Chromium OSS – need to patch immediately, as this one was found in the wild. Go.
CVE-2024-30040 – Windows MSHTML Platform Security Feature Bypass Vulnerability
CVE-2024-30051 — Windows DWM Core Library Elevation of Privilege Vulnerability
Two additional issues have been detected under exploit in the wild. The MSHTML issue has a base CVSS value of 8.8; the bug bypasses a feature in Microsoft 365 called OLE Auto-Activation Block, which allows admins to prevent abuse of OLE/COM. An attacker would abuse this bug by sending the targeted user a maliciously crafted file and then convincing them, to quote the bulletin, “to manipulate the specially crafted file, but not necessarily click or open the malicious file.” The DWM Core Library issue has a lower 7.8 base CVSS – and shares the stage with three other fixes addressing that component – but the list of credited finders is various and startling, including researchers from Kaspersky, Google Threat Analysis Group, Google Mandiant, and DBAPPSecurity WeBin Lab.
CVE-2024-30050 – Windows Mark of the Web Security Feature Bypass Vulnerability
April showers may be over, but the steady pitter-pat of Mark of the Web issues continues. This one’s Moderate in impact and limited in scope – a successful attack would lead to limited losses of integrity and availability of security features that rely on MotW, including Protected Mode in Office. Still, Microsoft assesses this one to be more likely to be exploited within the next 30 days, and the uses of a vulnerability like this in a chained attack should be kept in mind. Sophos has developed Intercept X/Endpoint IPS and XGS Firewall protections against this issue, as covered in the table below.
CVE-2024-30044 – Microsoft SharePoint Server Remote Code Execution Vulnerability
The month’s sole Critical-severity vulnerability affects SharePoint and is believed by Microsoft to be more likely to see exploitation in the next 30 days. Once again, Sophos has developed Intercept X/Endpoint IPS and XGS Firewall protections against this issue, as covered in the table below.
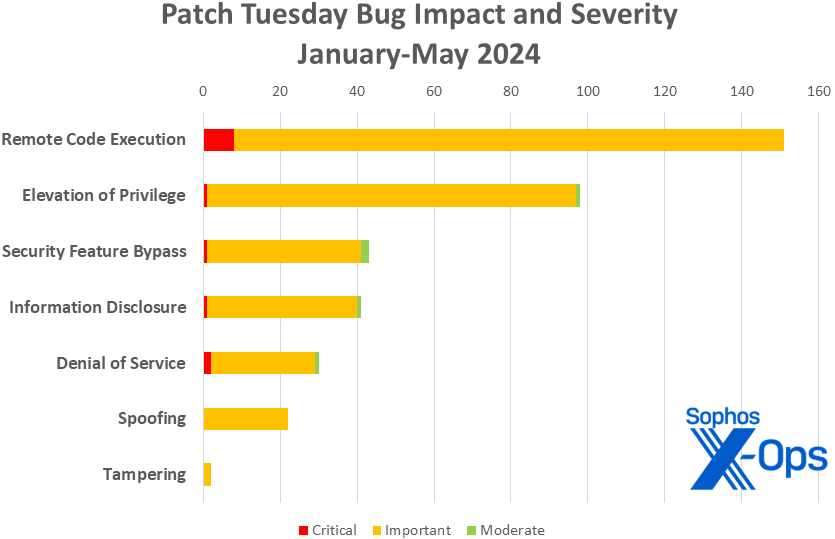
Figure 3: RCE issues continue to outpace all other types of vulnerability in 2024
Sophos protections
| CVE | Sophos Intercept X/Endpoint IPS | Sophos XGS Firewall |
| CVE-2024-29996 | Exp/2429996-A | Exp/2429996-A |
| CVE-2024-30025 | Exp/2430025-A | Exp/2430025-A |
| CVE-2024-30032 | Exp/2430032-A | Exp/2430032-A |
| CVE-2024-30034 | Exp/2430034-A | Exp/2430034-A |
| CVE-2024-30035 | Exp/2430035-A | Exp/2430035-A |
| CVE-2024-30037 | Exp/2430037-A | Exp/2430037-A |
| CVE-2024-30044 | Exp/2430044-A, sid:2309589 | sid:2309589 |
| CVE-2024-30050 | sid:2309595 | sid:2309595 |
As you can every month, if you don’t want to wait for your system to pull down Microsoft’s updates itself, you can download them manually from the Windows Update Catalog website. Run the winver.exe tool to determine which build of Windows 10 or 11 you’re running, then download the Cumulative Update package for your specific system’s architecture and build number.
Appendix A: Vulnerability Impact and Severity
This is a list of May patches sorted by impact, then sub-sorted by severity. Each list is further arranged by CVE.
Remote Code Execution (25 CVEs)
| Critical severity | |
| CVE-2024-30044 | Microsoft SharePoint Server Remote Code Execution Vulnerability |
| Important severity | |
| CVE-2024-29997 | Windows Mobile Broadband Driver Remote Code Execution Vulnerability |
| CVE-2024-29998 | Windows Mobile Broadband Driver Remote Code Execution Vulnerability |
| CVE-2024-29999 | Windows Mobile Broadband Driver Remote Code Execution Vulnerability |
| CVE-2024-30000 | Windows Mobile Broadband Driver Remote Code Execution Vulnerability |
| CVE-2024-30001 | Windows Mobile Broadband Driver Remote Code Execution Vulnerability |
| CVE-2024-30002 | Windows Mobile Broadband Driver Remote Code Execution Vulnerability |
| CVE-2024-30003 | Windows Mobile Broadband Driver Remote Code Execution Vulnerability |
| CVE-2024-30004 | Windows Mobile Broadband Driver Remote Code Execution Vulnerability |
| CVE-2024-30005 | Windows Mobile Broadband Driver Remote Code Execution Vulnerability |
| CVE-2024-30006 | Microsoft WDAC OLE DB provider for SQL Server Remote Code Execution Vulnerability |
| CVE-2024-30009 | Windows Routing and Remote Access Service (RRAS) Remote Code Execution Vulnerability |
| CVE-2024-30010 | Windows Hyper-V Remote Code Execution Vulnerability |
| CVE-2024-30012 | Windows Mobile Broadband Driver Remote Code Execution Vulnerability |
| CVE-2024-30014 | Windows Routing and Remote Access Service (RRAS) Remote Code Execution Vulnerability |
| CVE-2024-30015 | Windows Routing and Remote Access Service (RRAS) Remote Code Execution Vulnerability |
| CVE-2024-30017 | Windows Hyper-V Remote Code Execution Vulnerability |
| CVE-2024-30020 | Windows Cryptographic Services Remote Code Execution Vulnerability |
| CVE-2024-30021 | Windows Mobile Broadband Driver Remote Code Execution Vulnerability |
| CVE-2024-30022 | Windows Routing and Remote Access Service (RRAS) Remote Code Execution Vulnerability |
| CVE-2024-30023 | Windows Routing and Remote Access Service (RRAS) Remote Code Execution Vulnerability |
| CVE-2024-30024 | Windows Routing and Remote Access Service (RRAS) Remote Code Execution Vulnerability |
| CVE-2024-30029 | Windows Routing and Remote Access Service (RRAS) Remote Code Execution Vulnerability |
| CVE-2024-30042 | Microsoft Excel Remote Code Execution Vulnerability |
| CVE-2024-30045 | .NET and Visual Studio Remote Code Execution Vulnerability |
Elevation of Privilege (17 CVEs)
| Important severity | |
| CVE-2024-26238 | Microsoft PLUGScheduler Scheduled Task Elevation of Privilege Vulnerability |
| CVE-2024-29994 | Microsoft Windows SCSI Class System File Elevation of Privilege Vulnerability |
| CVE-2024-29996 | Windows Common Log File System Driver Elevation of Privilege Vulnerability |
| CVE-2024-30007 | Microsoft Brokering File System Elevation of Privilege Vulnerability |
| CVE-2024-30018 | Windows Kernel Elevation of Privilege Vulnerability |
| CVE-2024-30025 | Windows Common Log File System Driver Elevation of Privilege Vulnerability |
| CVE-2024-30027 | NTFS Elevation of Privilege Vulnerability |
| CVE-2024-30028 | Win32k Elevation of Privilege Vulnerability |
| CVE-2024-30030 | Win32k Elevation of Privilege Vulnerability |
| CVE-2024-30031 | Windows CNG Key Isolation Service Elevation of Privilege Vulnerability |
| CVE-2024-30032 | Windows DWM Core Library Elevation of Privilege Vulnerability |
| CVE-2024-30033 | Windows Search Service Elevation of Privilege Vulnerability |
| CVE-2024-30035 | Windows DWM Core Library Elevation of Privilege Vulnerability |
| CVE-2024-30037 | Windows Common Log File System Driver Elevation of Privilege Vulnerability |
| CVE-2024-30038 | Win32k Elevation of Privilege Vulnerability |
| CVE-2024-30049 | Windows Win32 Kernel Subsystem Elevation of Privilege Vulnerability |
| CVE-2024-30051 | Windows DWM Core Library Elevation of Privilege Vulnerability |
Information Disclosure (7 CVEs)
| Important severity | |
| CVE-2024-30008 | Windows DWM Core Library Information Disclosure Vulnerability |
| CVE-2024-30016 | Windows Cryptographic Services Information Disclosure Vulnerability |
| CVE-2024-30034 | Windows Cloud Files Mini Filter Driver Information Disclosure Vulnerability |
| CVE-2024-30036 | Windows Deployment Services Information Disclosure Vulnerability |
| CVE-2024-30039 | Windows Remote Access Connection Manager Information Disclosure Vulnerability |
| CVE-2024-30043 | Microsoft SharePoint Server Information Disclosure Vulnerability |
| CVE-2024-30054 | Microsoft Power BI Client Javascript SDK Information Disclosure Vulnerability |
Spoofing (4 CVEs)
| Important severity | |
| CVE-2024-30041 | Microsoft Bing Search Spoofing Vulnerability |
| CVE-2024-30047 | Dynamics 365 Customer Insights Spoofing Vulnerability |
| CVE-2024-30048 | Dynamics 365 Customer Insights Spoofing Vulnerability |
| CVE-2024-30053 | Azure Migrate Cross-Site Scripting Vulnerability |
Denial of Service (3 CVEs)
| Important severity | |
| CVE-2024-30011 | Windows Hyper-V Denial of Service Vulnerability |
| CVE-2024-30019 | DHCP Server Service Denial of Service Vulnerability |
| CVE-2024-30046 | Visual Studio Denial of Service Vulnerability |
Security Feature Bypass (2 CVEs)
| Important severity | |
| CVE-2024-30040 | Windows MSHTML Platform Security Feature Bypass Vulnerability |
| Moderate severity | |
| CVE-2024-30050 | Windows Mark of the Web Security Feature Bypass Vulnerability |
Tampering (1 CVE)
| Important severity | |
| CVE-2024-30059 | Microsoft Intune for Android Mobile Application Management Tampering Vulnerability |
Appendix B: Exploitability
This is a list of the May CVEs already under exploit in the wild, and those judged by Microsoft to be more likely to be exploited in the wild within the first 30 days post-release. The list is arranged by CVE.
| Exploitation detected | |
| CVE-2024-30040 | Windows MSHTML Platform Security Feature Bypass Vulnerability |
| CVE-2024-30051 | Windows DWM Core Library Elevation of Privilege Vulnerability |
| Exploitation more likely within the next 30 days | |
| CVE-2024-29996 | Windows Common Log File System Driver Elevation of Privilege Vulnerability |
| CVE-2024-30025 | Windows Common Log File System Driver Elevation of Privilege Vulnerability |
| CVE-2024-30032 | Windows DWM Core Library Elevation of Privilege Vulnerability |
| CVE-2024-30034 | Windows Cloud Files Mini Filter Driver Information Disclosure Vulnerability |
| CVE-2024-30035 | Windows DWM Core Library Elevation of Privilege Vulnerability |
| CVE-2024-30037 | Windows Common Log File System Driver Elevation of Privilege Vulnerability |
| CVE-2024-30038 | Win32k Elevation of Privilege Vulnerability |
| CVE-2024-30044 | Microsoft SharePoint Server Remote Code Execution Vulnerability |
| CVE-2024-30049 | Windows Win32 Kernel Subsystem Elevation of Privilege Vulnerability |
| CVE-2024-30050 | Windows Mark of the Web Security Feature Bypass Vulnerability |
Appendix C: Products Affected
This is a list of May’s patches sorted by product family, then sub-sorted by severity. Each list is further arranged by CVE. Patches that are shared among multiple product families are listed multiple times, once for each product family.
Windows (48 CVEs)
| Important severity | |
| CVE-2024-26238 | Microsoft PLUGScheduler Scheduled Task Elevation of Privilege Vulnerability |
| CVE-2024-29994 | Microsoft Windows SCSI Class System File Elevation of Privilege Vulnerability |
| CVE-2024-29996 | Windows Common Log File System Driver Elevation of Privilege Vulnerability |
| CVE-2024-29997 | Windows Mobile Broadband Driver Remote Code Execution Vulnerability |
| CVE-2024-29998 | Windows Mobile Broadband Driver Remote Code Execution Vulnerability |
| CVE-2024-29999 | Windows Mobile Broadband Driver Remote Code Execution Vulnerability |
| CVE-2024-30000 | Windows Mobile Broadband Driver Remote Code Execution Vulnerability |
| CVE-2024-30001 | Windows Mobile Broadband Driver Remote Code Execution Vulnerability |
| CVE-2024-30002 | Windows Mobile Broadband Driver Remote Code Execution Vulnerability |
| CVE-2024-30003 | Windows Mobile Broadband Driver Remote Code Execution Vulnerability |
| CVE-2024-30004 | Windows Mobile Broadband Driver Remote Code Execution Vulnerability |
| CVE-2024-30005 | Windows Mobile Broadband Driver Remote Code Execution Vulnerability |
| CVE-2024-30006 | Microsoft WDAC OLE DB provider for SQL Server Remote Code Execution Vulnerability |
| CVE-2024-30007 | Microsoft Brokering File System Elevation of Privilege Vulnerability |
| CVE-2024-30008 | Windows DWM Core Library Information Disclosure Vulnerability |
| CVE-2024-30009 | Windows Routing and Remote Access Service (RRAS) Remote Code Execution Vulnerability |
| CVE-2024-30010 | Windows Hyper-V Remote Code Execution Vulnerability |
| CVE-2024-30011 | Windows Hyper-V Denial of Service Vulnerability |
| CVE-2024-30012 | Windows Mobile Broadband Driver Remote Code Execution Vulnerability |
| CVE-2024-30014 | Windows Routing and Remote Access Service (RRAS) Remote Code Execution Vulnerability |
| CVE-2024-30015 | Windows Routing and Remote Access Service (RRAS) Remote Code Execution Vulnerability |
| CVE-2024-30016 | Windows Cryptographic Services Information Disclosure Vulnerability |
| CVE-2024-30017 | Windows Hyper-V Remote Code Execution Vulnerability |
| CVE-2024-30018 | Windows Kernel Elevation of Privilege Vulnerability |
| CVE-2024-30019 | DHCP Server Service Denial of Service Vulnerability |
| CVE-2024-30020 | Windows Cryptographic Services Remote Code Execution Vulnerability |
| CVE-2024-30021 | Windows Mobile Broadband Driver Remote Code Execution Vulnerability |
| CVE-2024-30022 | Windows Routing and Remote Access Service (RRAS) Remote Code Execution Vulnerability |
| CVE-2024-30023 | Windows Routing and Remote Access Service (RRAS) Remote Code Execution Vulnerability |
| CVE-2024-30024 | Windows Routing and Remote Access Service (RRAS) Remote Code Execution Vulnerability |
| CVE-2024-30025 | Windows Common Log File System Driver Elevation of Privilege Vulnerability |
| CVE-2024-30027 | NTFS Elevation of Privilege Vulnerability |
| CVE-2024-30028 | Win32k Elevation of Privilege Vulnerability |
| CVE-2024-30029 | Windows Routing and Remote Access Service (RRAS) Remote Code Execution Vulnerability |
| CVE-2024-30030 | Win32k Elevation of Privilege Vulnerability |
| CVE-2024-30031 | Windows CNG Key Isolation Service Elevation of Privilege Vulnerability |
| CVE-2024-30032 | Windows DWM Core Library Elevation of Privilege Vulnerability |
| CVE-2024-30033 | Windows Search Service Elevation of Privilege Vulnerability |
| CVE-2024-30034 | Windows Cloud Files Mini Filter Driver Information Disclosure Vulnerability |
| CVE-2024-30035 | Windows DWM Core Library Elevation of Privilege Vulnerability |
| CVE-2024-30036 | Windows Deployment Services Information Disclosure Vulnerability |
| CVE-2024-30037 | Windows Common Log File System Driver Elevation of Privilege Vulnerability |
| CVE-2024-30038 | Win32k Elevation of Privilege Vulnerability |
| CVE-2024-30039 | Windows Remote Access Connection Manager Information Disclosure Vulnerability |
| CVE-2024-30040 | Windows MSHTML Platform Security Feature Bypass Vulnerability |
| CVE-2024-30049 | Windows Win32 Kernel Subsystem Elevation of Privilege Vulnerability |
| CVE-2024-30051 | Windows DWM Core Library Elevation of Privilege Vulnerability |
| Moderate severity | |
| CVE-2024-30050 | Windows Mark of the Web Security Feature Bypass Vulnerability |
Dynamics 365 (2 CVEs)
| Important severity | |
| CVE-2024-30047 | Dynamics 365 Customer Insights Spoofing Vulnerability |
| CVE-2024-30048 | Dynamics 365 Customer Insights Spoofing Vulnerability |
SharePoint (2 CVEs)
| Critical severity | |
| CVE-2024-30044 | Microsoft SharePoint Server Remote Code Execution Vulnerability |
| Important severity | |
| CVE-2024-30043 | Microsoft SharePoint Server Information Disclosure Vulnerability |
Visual Studio (2* CVEs)
| Important severity | |
| CVE-2024-30045 | .NET and Visual Studio Remote Code Execution Vulnerability |
| CVE-2024-30046 | Visual Studio Denial of Service Vulnerability |
* In addition, this release includes information on two GitHub-issued advisories affecting Visual Studio; please see Appendix D for details.
.NET (1 CVE)
| Important severity | |
| CVE-2024-30045 | .NET and Visual Studio Remote Code Execution Vulnerability |
365 Apps for Enterprise (1 CVE)
| Important severity | |
| CVE-2024-30042 | Microsoft Excel Remote Code Execution Vulnerability |
Azure (1 CVE)
| Important severity | |
| CVE-2024-30053 | Azure Migrate Cross-Site Scripting Vulnerability |
Bing Search for iOS (1 CVE)
| Important severity | |
| CVE-2024-30041 | Microsoft Bing Search Spoofing Vulnerability |
Intune (1 CVE)
| Important severity | |
| CVE-2024-30059 | Microsoft Intune for Android Mobile Application Management Tampering Vulnerability |
Office (1 CVE)
| Important severity | |
| CVE-2024-30042 | Microsoft Excel Remote Code Execution Vulnerability |
Power BI (1 CVE)
| Important severity | |
| CVE-2024-30054 | Microsoft Power BI Client Javascript SDK Information Disclosure Vulnerability |
Appendix D: Advisories and Other Products
This is a list of advisories and information on other relevant CVEs in the May Microsoft release, sorted by product.
Relevant to Edge / Chromium (6 CVEs)
| CVE-2024-4331 | Chromium: CVE-2024-4331 Use after free in Picture In Picture |
| CVE-2024-4368 | Chromium: CVE-2024-4368 Use after free in Dawn |
| CVE-2024-4558 | Chromium: CVE-2024-4558 Use after free in ANGLE |
| CVE-2024-4559 | Chromium: CVE-2024-4559 Heap buffer overflow in WebAudio |
| CVE-2024-4671 | Chromium: CVE-2024-4671 Use after free in Visuals |
| CVE-2024-30055 | Microsoft Edge (Chromium-based) Spoofing Vulnerability |
Relevant to Visual Studio (non-Microsoft CVE issuer) (2 CVEs)
| CVE-2024-32002 | Recursive clones on case-insensitive filesystems that support symlinks are susceptible to Remote Code Execution |
| CVE-2024-32004 | GitHub: CVE-2023-32004 Remote Code Execution while cloning special-crafted local repositories |
Relevant to Adobe (non-Microsoft release) (4 CVEs)
| CVE-2024-30284 | Use After Free (CWE-416) |
| CVE-2024-30310 | Out-of-bounds Write (CWE-787) |
| CVE-2024-30311 | Out-of-bounds Read (CWE-125) |
| CVE-2024-30312 | Out-of-bounds Read (CWE-125) |

Leave a Reply