Is it honestly so bad to expose a server with RDP to the internet? In order to find out, we did just that.
For science, we stood up a server, exposed RDP to the internet, and walked away for 15 days. When we came back, we found out that login attempts started in less than one minute from the moment we exposed the port. Even if you’re thinking about “temporarily” exposing a server to the internet with RDP for someone to remotely access it, those unwanted brute force attempts roll in quickly.
Digging deeper, we compiled statistics on the usernames most commonly used to attempt access. Unsurprisingly, “administrator” and variants of that word/title took the top three spots. On our exposed system, “administrator” alone accounted for 866,862 failed login attempts over those 15 days.
| Username | Count |
| administrator | 866862 |
| administrador | 152289 |
| administrateur | 111460 |
| backup | 94541 |
| admin | 88367 |
| user | 24030 |
| scanner | 18781 |
| escaner | 12455 |
| usuario | 12238 |
| Guest | 8784 |
Figure 1: The ten usernames most often attempted in brute-force attacks on our guinea-pig RDP server over 15 days; “escaner” and “usuario” are respectively “scanner” and “user” in Spanish
To be sure, the high number of attempts on that specific account name was not surprising; in most of the cases the Sophos IR team has handled in which exposed RDP was the initial access vector, the attacker managed to obtain access by brute-forcing the administrator account. Worse, we regularly see that the organizations that expose RDP to the internet quite often have poor password policies, which makes it easy for ransomware groups to brute force their way into those accounts.
Beyond these attempts, in total we saw that 137,500 unique usernames were attempted over the course of 15 days, with scanning activity originating from 999 unique IP addresses. In total, we saw just over 2 million failed login attempts in the 15 days. So, to answer the original question: YES. There is a vast amount of scanning activity that seeks open RDP. It’s still a common access vector. And it’s definitely dangerous to expose RDP to the internet.
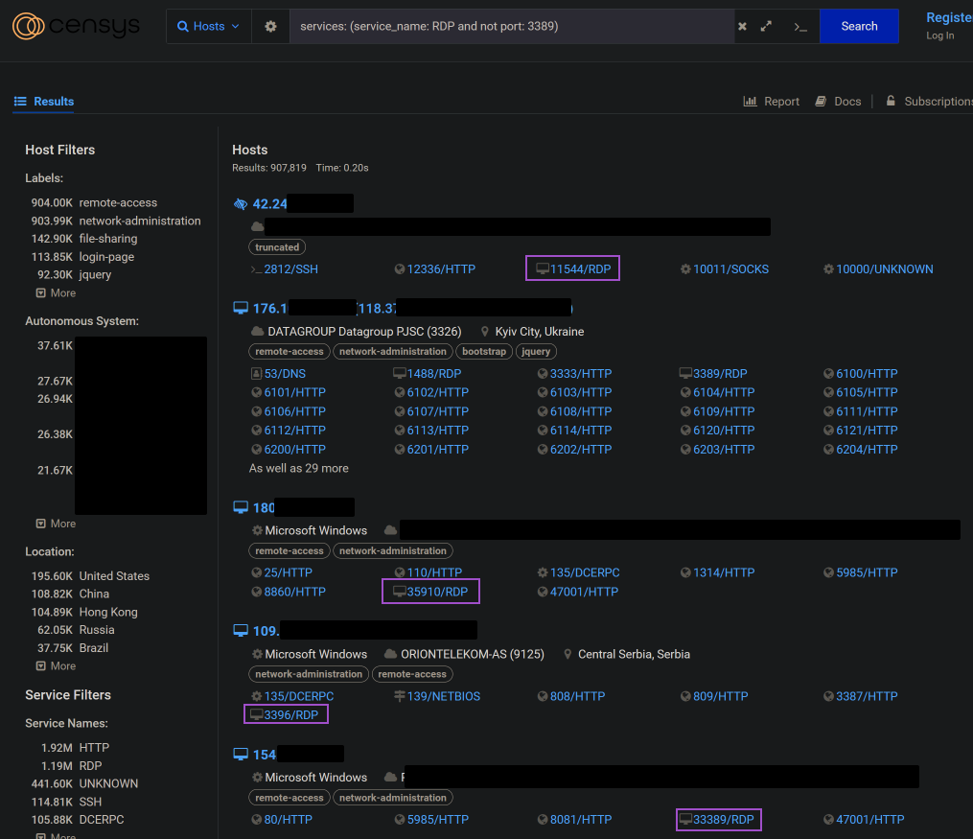
By default, RDP is exposed on port 3389. What happens when it’s exposed on a non-default port? Unfortunately, it does not matter; scanners and ransomware groups still easily identify that an RDP port is open and listening, no matter how obscure the port number is. To illustrate that, we did a simple search on censys.io, seeking RDP listening on ports other than 3389.
Figure 2: As seen on Censys, “hiding” exposed RDP on a nonstandard port is not remotely effective
As the image shows, security through obscurity doesn’t work any better than security through ephemerality – having the port open “temporarily” — did in the first example. Brute force attempts began less than one minute from when the RDP port opened.
So what’s an administrator to do? For access, there are much more secure methods to allow remote access to an environment – for instance, a VPN with MFA. (Recommendations for individual enterprises are beyond the scope of this article, but know that solutions exist.) As for investigators, in the next part of this series we’ll look at multiple queries that can enhance understanding of attack specifics.
Remote Desktop Protocol: The Series
Part 1: Remote Desktop Protocol: Introduction (post, video)
Part 2: Remote Desktop Protocol: Exposed RDP (is dangerous) ([you are here], video)
Part 3: RDP: Queries for Investigation (post, video)
Part 4: RDP Time Zone Bias (post, video)
Part 5: Executing the External RDP Query (post, video)
Part 6: Executing the 4624_4625 Login Query (post, video)
GitHub query repository: SophosRapidResponse/OSQuery
Transcript repository: sophoslabs/video-transcripts
YouTube playlist: Remote Desktop Protocol: The Series

Leave a Reply