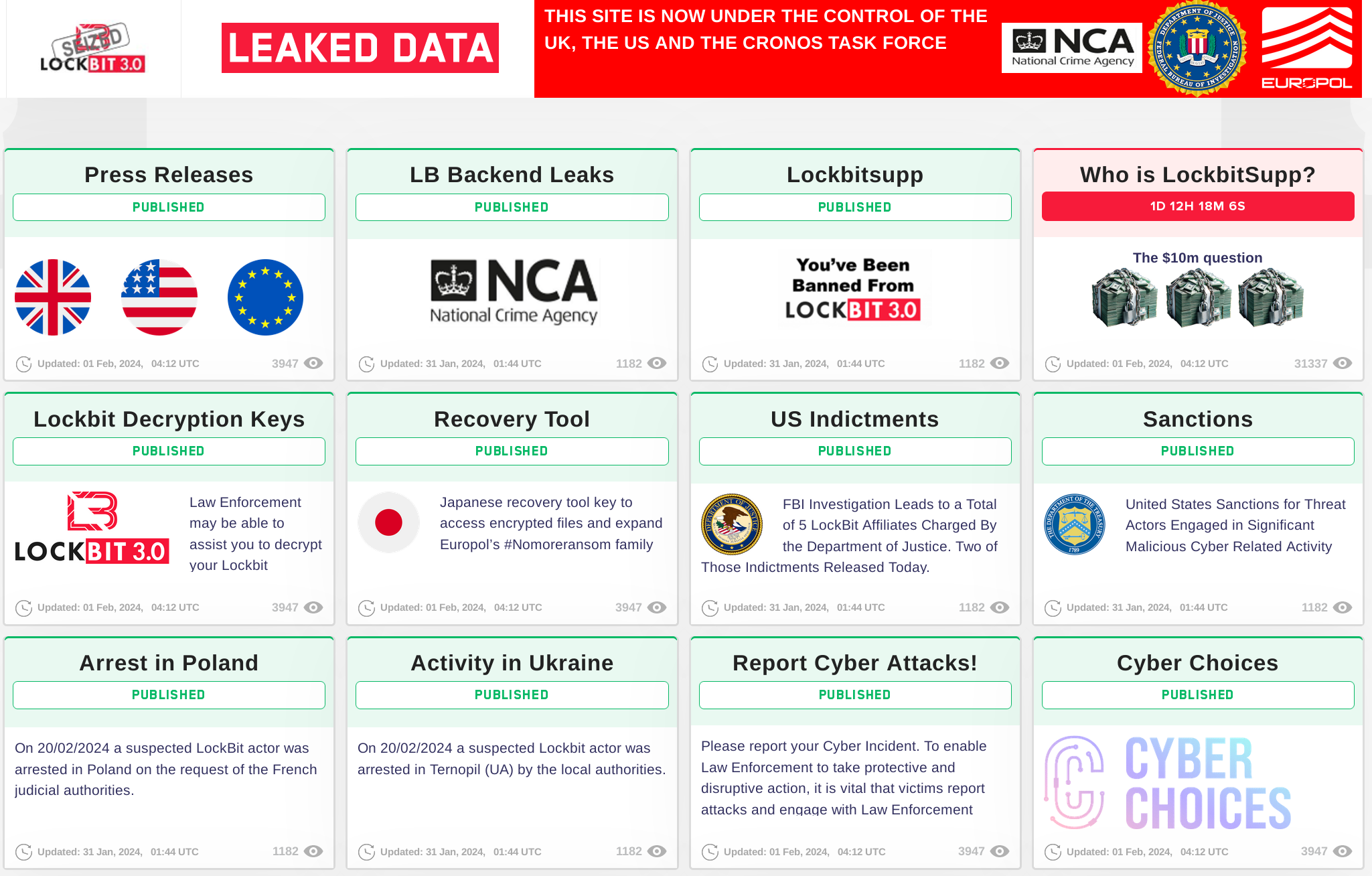
Late on February 19, 2024, the main website of LockBit, the most prolific ransomware group in recent memory, was seized by the United Kingdom’s National Crime Agency (NCA). In cooperation with their international law enforcement partners at the United States FBI, the French Gendarmerie National, Europol, and others, the NCA seized the physical servers that operated the primary site and have arrested two men, one in Poland and the other in Ukraine. Additionally, the US on the same day announced sanctions of two Russian nationals for their role in the criminal syndicate.
This type of coordinated, multinational law enforcement action gives us new insights into how these organized crime groups operate, and also exposes some of the limits we have available to us to rein in this type of activity.
Let’s start with the basics: What exactly makes up a “ransomware syndicate?” Most of the time they appear to take the form of an anarcho-syndicalist commune. Usually, that includes a core group of software developers to build the websites, malware, and payment sites; someone to launder money; and someone with a decent grasp of English to negotiate payment with the victims. The actual attacks themselves are conducted by so-called “affiliates.” These affiliates sign up to use the platform and brand name to extort victims and share the proceeds.
Identity is fluid in the criminal underworld
Our first problem lies in that structure: These “groups” are mostly loosely affiliated and operating under a brand name. Shutting down the brand does not necessarily impact the core group members themselves. By the US issuing sanctions against some of its members, the brand “LockBit” is as good as dead. No US-based entity will be willing to pay a ransom to LockBit, but if they reemerge tomorrow as CryptoMegaUnicornBit or similar, it will start the cycle all over again.
Depriving these individuals of income under a new name is very difficult. The sanctions issued today against Ivan Kondratyev and Artur Sungatov (the sanctioned Russian nationals) have ruined LockBit, but when they return as DatasLaYeR001 and Crypt0Keeper69 how will victims know that they are sanctioned entities? The sanctions are merely speed bumps, not real long-term solutions to the ransomware problem.
The five indictments by the US Department of Justice (DOJ) are likely just the beginning. In past cases of this sort, the only indictments made public are for individuals who are in countries where the US is unlikely to obtain law enforcement cooperation; absent that, the US will choose to the sanctioned entities list. Hopefully there are more sealed indictments lurking, unknown for now to their subjects; such indictments could, for instance, be used to ensnare other identified participants if they make the mistake of traveling internationally on a holiday. Participants in the LockBit crime family who were in law enforcement-friendly countries were arrested — in Poland (for money laundering) and in Ukraine (unspecified) — and will likely face charges in France.
Security is hard
How did law enforcement manage to take down these thugs? All indicators are that it may have started with an unpatched security vulnerability, CVE 2023-3824 — that is, if you believe the criminals themselves. Being a professional criminal hacker does not make you magically great at securing your own infrastructure, and observers had commented on LockBit’s struggle to manage their IT infrastructure in mid-2023 – ironically, just before CVE-2023-3824 was publicly reported.
Once the web server running the leak site was exploited, they were presumably able to physically seize the servers running the operation and begin to unravel more and more of the supporting infrastructure. Press have reported this was a multiyear operation. (As a reminder, LockBit is a relatively long-lived brand; the first sighting dates back to 2019, and as of 19 February 2024 their own file leak page says the site had been up for 4 years and 169 days.)
This is not a new idea or approach. We have seen law enforcement “hack” criminal infrastructure in earlier cases as well, sometimes using zero-day vulnerabilities in browsers and tools, other times catching the criminals making an error by forgetting to use a VPN or Tor Browser, leading to their identification and apprehension. These operation security (OpSec) errors are ultimately the undoing of even the most sophisticated criminals.
If we want to continue to increase the pressure on these groups, we must ramp up law enforcement’s ability to conduct these operations. They are essential not only to dismantling the infrastructure used in these attacks, but to undermining the confidence the co-conspirators place in the safety of their participation. We need more skilled, competitively compensated cyber-cops and a better-informed judiciary to approve these operations.
Sadly, despite the success the NCA and their partners have had, they have not totally disabled the Lockbit network. Several dark web sites used by the group are still available, including the most damaging one of all — the one hosting the purloined content from victims to expose them in retribution for their lack of payment. The harm was already done before the takedown, but their compromise was not complete.
Boasting, bluster, and attitude
People have been commenting on social media about the “epic trolling” of the NCA in their seizure and resurrection of the LockBit leak site. Was this an act of bravado alone or is there a deeper motive on behalf of police and policymakers? I don’t have the answer, yet I hope and suspect this is being done with intent.
Figure 1: The takedown page is informative, and it promises more excitement to come later in the week
Experience suggests that many, but not all, of the criminal puppeteers orchestrating these activities are in countries unable or unwilling to enforce the rule of law against groups targeting Western victims. Additionally, many of their affiliates know very well they are not as well-protected as the group leaders.
By making a scene and instilling fear, uncertainty, and doubt as to whether their tools, communications, and identities are being monitored or already compromised might dissuade the supporting actors from participating. There has been a well-justified paranoia among criminal gangs for a while that they have been compromised by researchers and law enforcement. They are right. We are among them, watching them. The trolling and exposure the NCA have orchestrated drives home the point: We are in you.
In criminals we trust?
Many victims have argued they paid the ransom to save their customers, employees, and shareholders from having their data exposed. The idea that paying extortionists to delete stolen data is a viable plan has been criticized by experts since the dawn of the crime itself. The NCA confirmed what we suspected; the criminals have kept copies of data stolen from victims and may have intended to further exploit or monetize said information. No honor among thieves.
What’s likely more important in this case isn’t our trust that the criminals are good for their word, rather how can we spread this distrust amongst their own operatives. Our own skepticism combined with the US sanctions should be enough to give almost any of us pause, but can we create an atmosphere where the criminals themselves are unsure whom to trust?
I think this could be our best deterrent. Not only should the NCA, FBI, Europol, and others strut and expose after a takedown, but researchers and others should continually expose chats, forums, and other access they have gained on public forums to show that what seems to be happening in the dark is likely on the radar of many.
Closing thoughts
We are not going to arrest or imprison our way out of this, certainly not when the world is moving toward an increasingly balkanized condition. I feel like we are rounding a corner with the maturity of our approach; we are working the levers to apply pressure where it counts and finally employing a multidisciplinary approach on all fronts utilizing the leverage at our disposal.
This event will not end ransomware and may not even end the active participation of many involved in the LockBit cartel. What it does is advance our approach to disrupting these groups, increasing their cost of doing business and increasing the distrust among the criminals themselves.
The criminals have been successful by creating scripts and patterns for how to systemically exploit victims and we may be approaching the turning point where the defenders have a script of their own. We must stand strong and support our law enforcement partners in this fight and work to hit them where it hurts most. They say teamwork makes the dream work and if they can’t form cohesive teams, they will either fade off into the sunset or turn on each other. Win – win.

MarcusA
Deter & persist in deterring. Good article.
The kind is dead. Long live the king.
Gotta love a good Monty Python reference too:
Oh, what a give away. Did you here that, did you here that, eh? That’s what I’m on about — did you see him repressing me, you saw it didn’t you?