Cryptocurrency-based crime has metastasized into many forms. Because of the ease with which cryptocurrency ignores borders and enables multinational crime rings to quickly obtain and launder funds, and because of widespread confusion about how cryptocurrency functions, a wide range of confidence scams have focused on convincing victims to convert their personal savings to crypto—and then separate them from it.
Among these sorts of organized criminal activities, none seem as pervasive as “pig butchering” (from the Mandarin term, sha zhu pan, coined to describe the activity). Most of these scams use dating applications or other social media to lure victims into what they think is a budding romantic or platonic relationship, and then introduce a fraudulent scheme to make money together. In some recent cases we found the scammers using generative AI to write messages to their targets to make them more convincing.
We first began investigating pig butchering scams in 2020 in connection with fake cryptocurrency-trading mobile apps that device users had downloaded at the direction of someone the user had been contacted by more often than not through a dating app or website. We dubbed these “CryptoRom” apps, and have continued to research the scam rings, and how they evade platform security on mobile devices. One method that has become prevalent over the past year is to leverage the weaknesses of legitimate cryptocurrency applications through their ability to be linked to web applications.
Recently, I shared the details of a scam case in which an individual victim (whom we referred to as “Frank”) lost over $20,000 USD in a fake “mining pool.” Based on the details Frank provided, we were able to uncover a much larger set of scams using over a dozen different domains. The infrastructure of these domains was built on five different controlling “contract wallets” that directed cryptocurrency from victims’ wallets to other wallets for laundering. This set of scams appears to have interacted with over 90 victims. We have high confidence that the scam was run by three sets of affiliates connected to a multinational Chinese-language crime organization.
Looking back to the beginning of 2023, I found these contract wallets had moved $1.22 million worth of Tether (USDT) cryptocurrency from targeted wallets to destinations laundering the stolen crypto between January 1 and November 20. They appear to have been run by three separate threat activity groups using identical fraudulent decentralized finance (“DeFi”) app sites, suggesting that they are part of or affiliated with a single organized crime ring.
The ring is potentially much larger. I found traces of two other domains that matched our fingerprint for the site that had been deactivated before I could collect contract data. Examining the wallets that received the funds for laundering, I found additional contract wallets that were moving scammed funds from other victims—some pointing to additional laundering wallets. I continue to analyze the data to identify further scam operations.
In total, the wallets involved in the scheme moved nearly $2.9 million worth of cryptocurrency this year as of November 15, coming from the scams we tracked and other illegal activity.
Following the money
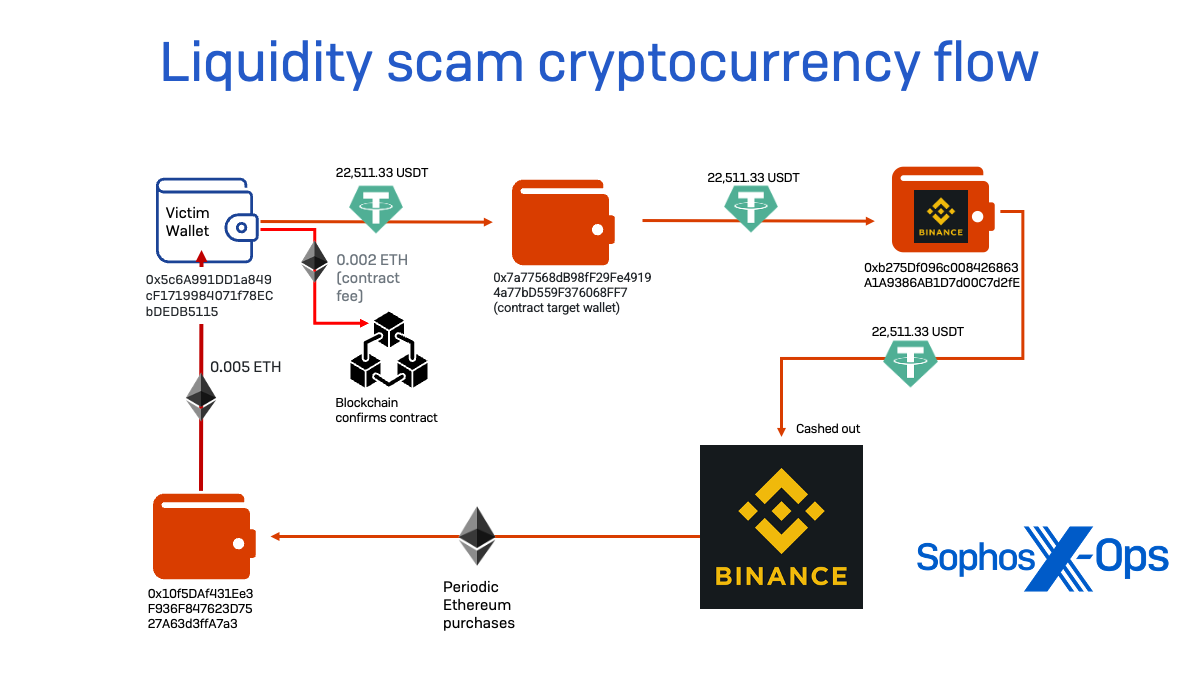
During our investigation of the scam targeting “Frank,” I tracked the flow of cryptocurrency from his wallet. The scammer’s trap was a fake decentralized finance app hosted on the domain allnodes[.]vip—a site registered through and hosted by Alibaba.
The app created a smart contract—paid for in Ethereum provided by the scammer in Frank’s case, and likely in all other scams run by this ring—that gave another wallet address a virtually unlimited “allowance,” allowing its owner to see the balance of the wallet being linked and to transfer Tether tokens deposited in the linked wallet. This remote address—the contract wallet—never moved cryptocurrency to itself but instead transferred balances to other wallets under control of the scammers using the smart contract authority by authorizing transactions on the blockchain.
Looking at transactions for the control node, I was able to determine that our victim was not the first targeted by this particular scam configuration. The control node was first active on April 5, making what may have been a test transfer of $55 worth of Tether to check the fake DeFi app’s configuration; the first victim appears to have had funds transferred the next day, being hit over the following two weeks for a total of $15,400 worth of cryptocurrency. In total before the node went quiet in early August, at least 7 targets would be fleeced by the scammers for amounts ranging from $2,000 to over $50,000—totaling $177,560.
Using characteristics of this scam, I went hunting for additional sites that were similar. And it quickly became clear that this was connected to a much larger operation.
Hunting for more domains and contract wallets
By examining domain registry data, I found another domain using the same branding (allnodes[.]xyz) also registered and hosted through Alibaba at a different IP address. The sites were identical in appearance and in underlying HTML and JavaScript code. The sites shared not just the same appearance, but the same script file names and used the same JavaScript-based in-site chat service (tawk[.]to). However, the app at the .xyz domain used a different contract wallet for its smart contract payload.
I expanded my search by examining the web requests from each of these sites and searching for sites with the same JavaScript and filenames. Based on those fingerprints, I found 11 additional domains hosting the same exact code, some sharing the same contract wallets in their configurations.
In total, I found four addresses acting as control nodes across 14 domains. I also found two domains that had ceased operation but matched all characteristics in historical telemetry and third-party data. Examining the sites, I discovered distinct groupings of domains using similar naming conventions, domain registrars and hosts, suggesting different sub-groups were operating identical scam kits simultaneously. This is similar to what we found when investigating pig butchering fake exchange sites, where dozens of sites were using the same code but with different associated wallet addresses.
| Group | Domain | Contract wallets | Hosting | Registrar | Total Crypto volume of transactions
(US $) |
|
|---|---|---|---|---|---|---|
| Allnodes | allnodes.vip | 0x6B79f38233726282c7F88FE670F871eAbd0c746c | Alibaba Singapore | Alibaba Cloud | 177,596.00 | |
| allnodes.xyx | 0xd2b14d2fff430a720cf44bbd064f548a585e73de | Alibaba Cloud | Alibaba Cloud | 174,934.00 | ||
| Trust | trust-oke[.}com | 0xcf6b558c218a9148cd77c04be4e3d1c1fc9d61a2 | Amazon | Amazon | 676,869.00 | |
| trust-btrust-oke[.}com | ||||||
| trust-usdt[.]com | ||||||
| trust-v2[.]com | ||||||
| trust-bnb[.]link | ||||||
| v2-eth[.]com | ||||||
| net-8897[.]com | ||||||
| Ada | ada-defi[.]pics | 0xeb7b75dd5b4b6ef7bbc6ec079cd329a782fc1efe | Cloudflare protected | Dynadot | 62,660.00 | |
| ada-defi[.]beauty | ||||||
| ada-defi[.]xyz | ||||||
| ada-coin[.]info | ||||||
| eth-defi[.]one | ||||||
| Unknown | trust-eth[.]com | Google, then Cloudflare | Gname.com | |||
| eth-mining[.]xyz | Google, then Cloudflare | Dynadot |
As shown in the table above, two groups of domains had shared contract wallet addresses. And through examining transaction data, I found that both “allnodes” domains, despite having separate contract wallets, routed cryptocurrency to the same destinations.
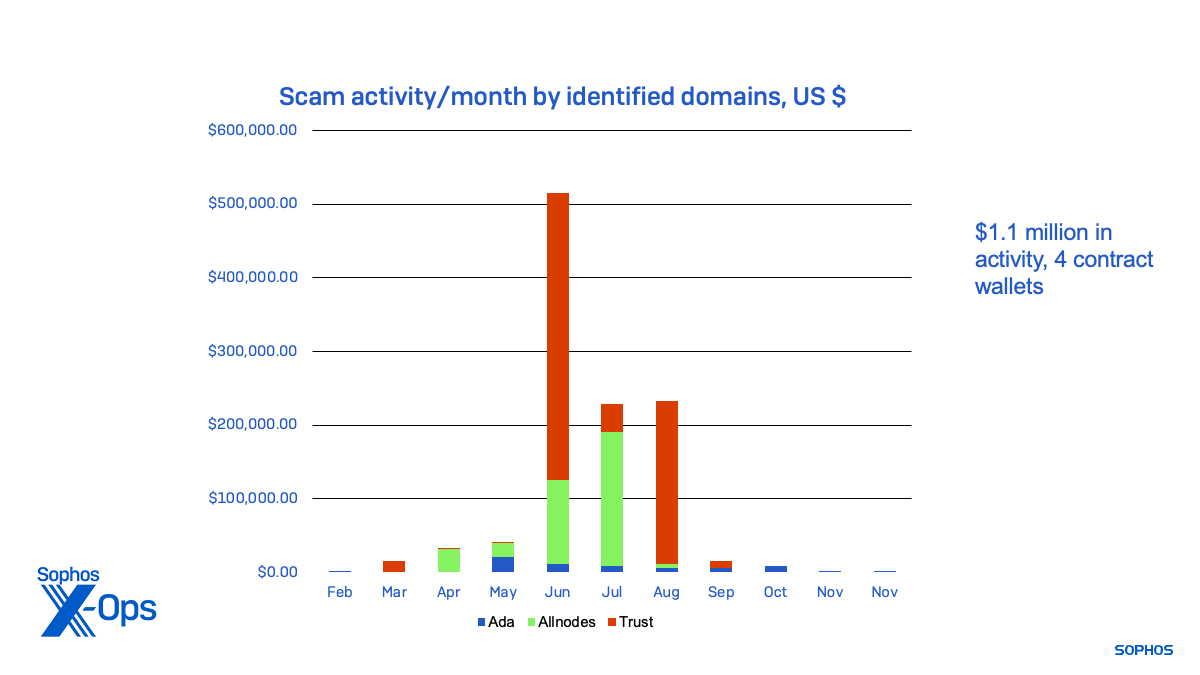
Activity for the scam sites and their contract wallets, some of which appeared to be testing the scripts associated with contract wallets, dated back to February. Most of the actual scam activity associated with the sites occurred in the summer months, as shown below by the volume of cryptocurrency moved through each of the primary contract wallets:
Further examining the transaction data for the wallets receiving fraudulent withdrawals, I discovered additional contract wallets sending crypto following the same pattern. They were using the same destination wallets as two of the above groups:
- 0x73b970978cbf19a5e1c727de20ad73db316f3817 and 0xf12a365e53313e59E915f0e8D432a326556dD22C, connected to “Trust” destination wallet;
- 0x3698cc343414c69233fe580cef379f02a91bc421 , connected to an “Ada” group destination wallet.
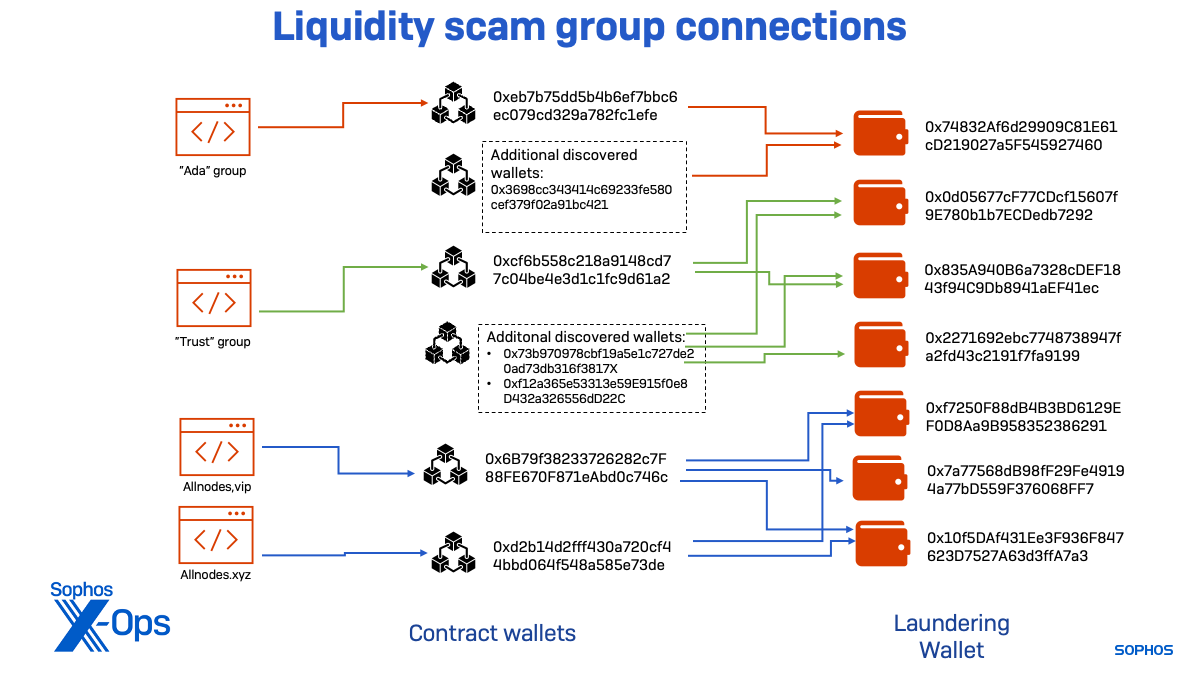
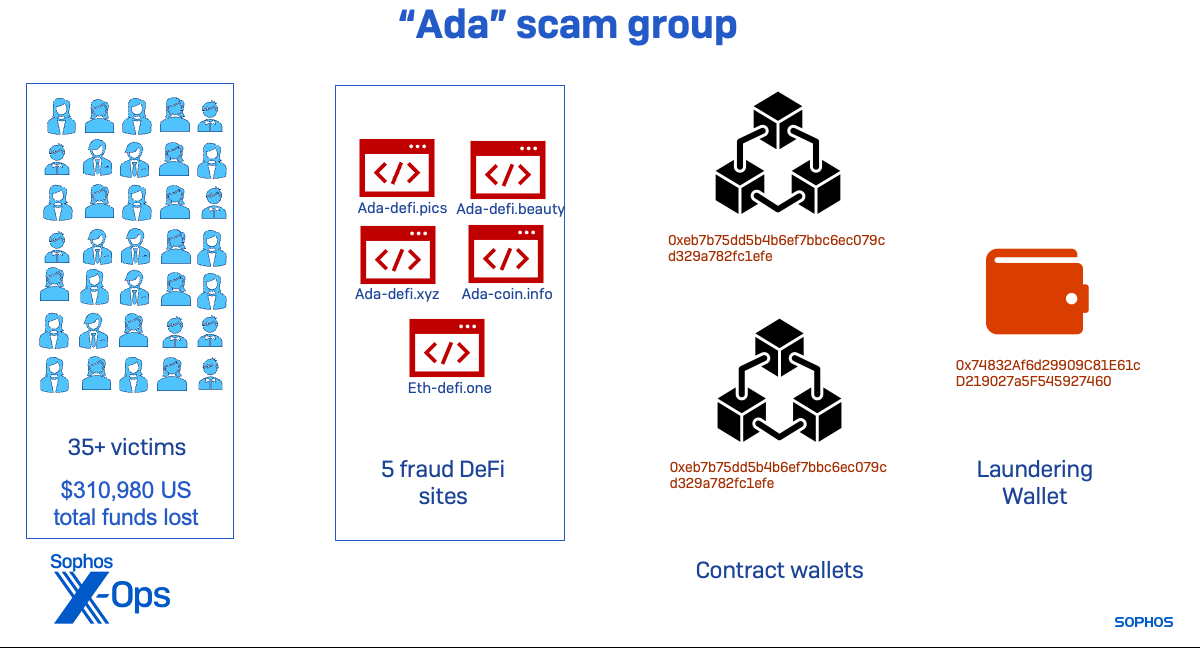
The “Ada” subgroup used a single wallet to launder funds from both its associated contract wallets. This group of sites was active beginning in March, but the wallets showed signs of scam activity as early as February, suggesting another domain was part of the group.
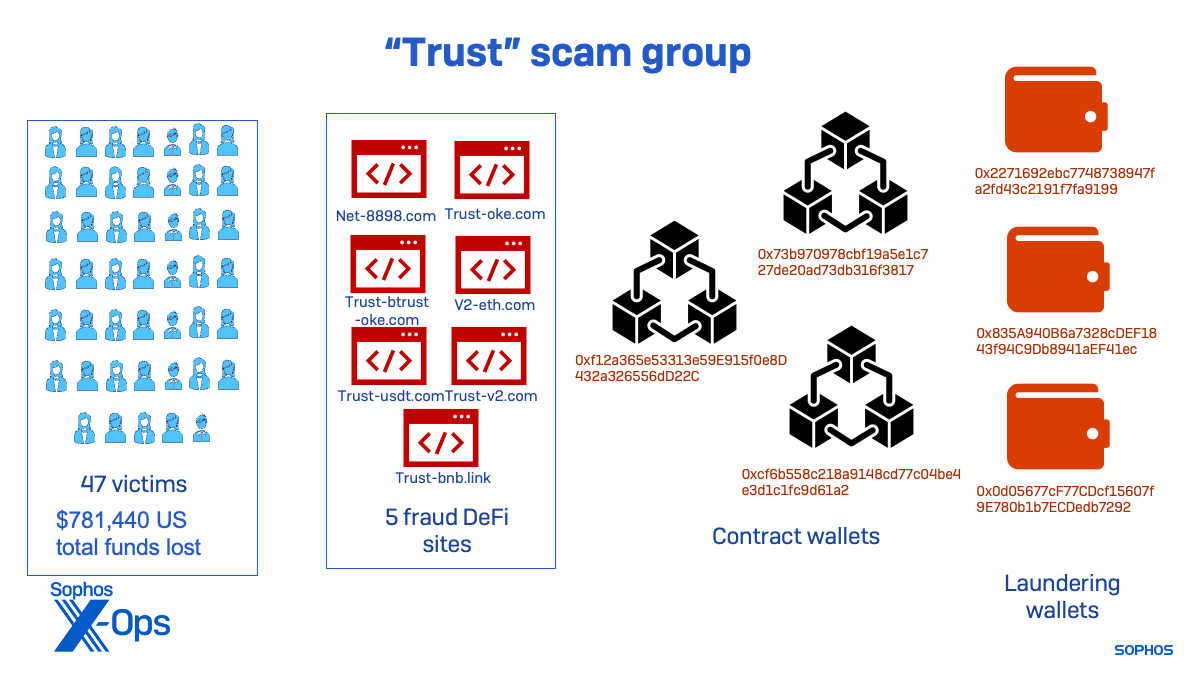
The “Trust” threat activity cluster appears to have been active the longest. One of its contract wallets was highly active in January, indicating that another scam site was active in 2022. That wallet’s activity fell off completely in March, with other wallets connected to newer sites becoming more active. As of November, the “Trust” cluster was still active, but far less than during the peak of the scam sites I identified.
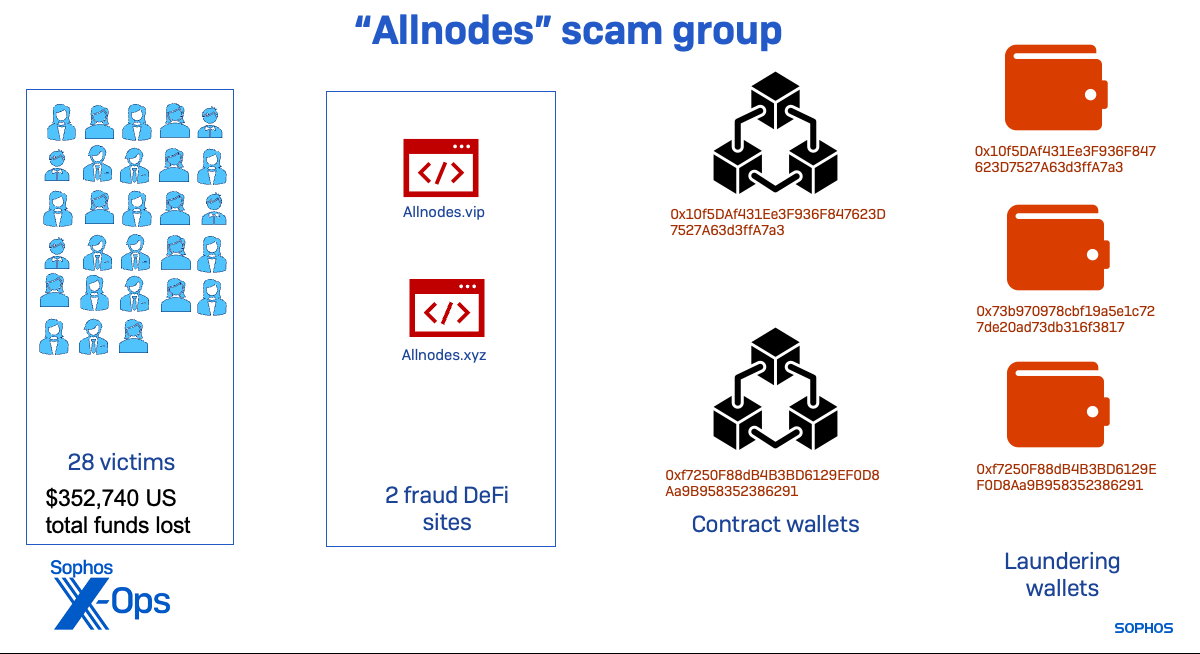
The “Allnodes” cluster was the one associated with the “Frank” case. It started later than the others and shut down activity tied to the infrastructure we identified shortly after we were contacted by the victim and began alerting wallet developers and exchanges of its presence. No further cash out activity was seen on the wallets associated with this threat group after August.
Despite being relatively short-lived, the Allnodes group managed to bring in over $352,000 before its lifecycle was ended—most of which was cashed out through Hong Kong bank accounts.
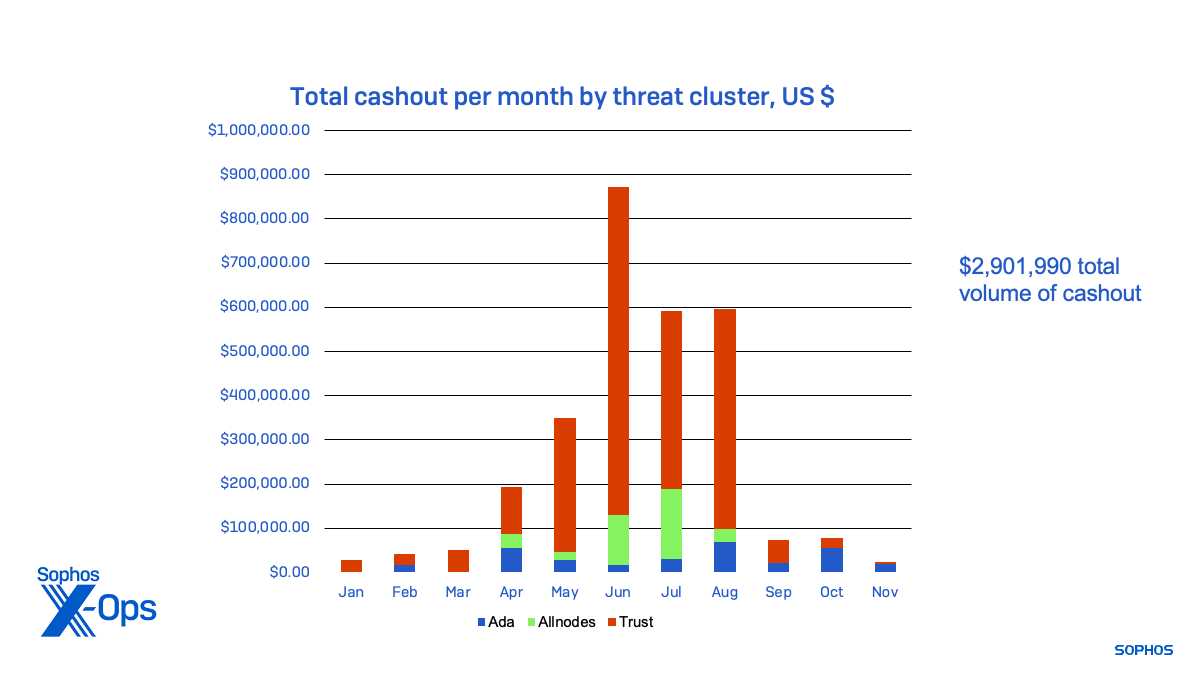 Figure 8: The funds cashed out by each of the threat activity clusters, from January 2023 to November 2023
Figure 8: The funds cashed out by each of the threat activity clusters, from January 2023 to November 2023
In total, the groups using the liquidity mining scam kit brought in over $2.9 million over the course of the year. It’s likely that they continue to run other, similar scams with new infrastructure. And there are many other scam operations using similar tactics, tools and practices—as I found investigating tips I received from other scam victims during the course of this research.
More kits, more scams
Following the same methods—hunting for domains that used DeFi and cryptocurrency names or borrowed branding from legitimate cryptocurrency-related brands—we found multiple additional scams. One, I identified, fronted by the domain eth-defi[.]xyz, yielded another contract wallet address: 0x2e7e4df940a2c999bf5b5cdcd15a738b8bb462d5.
Between August 18 and November 28, that contract wallet had pulled $115,820 worth of Tether cryptocurrency from victims. The majority of those funds were cashed out through Binance.
![Figure 9: The fake liquidity mining site eth-defi[.]xyz](https://news.sophos.com/wp-content/uploads/2023/12/eth-defi-xyz.png)
As I investigated these rings, I saw a shift in tools and tactics by other scam operations—which in part appears to be driven by the response of exchanges and wallet developers to share threat data, enabling them to block scams at the app level. Scam tool developers are taking measures to block harvesting of contract node data, controlling which wallets could be used for the scam, and taking greater care to evade geolocation and analysis. These more cautious scam deployments spanned hundreds of domains.
One example of this variation in scam site tooling—related to a scam hosted at phpsqo[.]top—came from a victim. The target, a student in Poland, was approached through WhatsApp by someone claiming to be a Chinese woman living in Germany. The interaction led to the target connecting her mobile wallet to a contract wallet through that domain: 0x63809823AD21B6314624621172bAf4532c5B8b72
The target put $1,177.79 worth of USDT in the wallet and saw daily deposits until the entire balance was pulled about a week later.
This contract wallet was extremely active, with over 950 transactions between March 26 and November 15, so manual analysis of the total number of victims and cryptocurrency transferred is still in progress. But drawing from a random sampling of the transactions, I estimate the contract wallet transferred at least $200,000 worth of cryptocurrency over that period.
Getting that data would have been difficult without the victim providing her wallet address, as the site uses JavaScript to detect the web agent connecting and disallows desktop browsers in addition to checking for cryptocurrency wallet connections.:
![Figure 10: a screenshot of phpsqo[.]top showing how it appears in a desktop browser](https://news.sophos.com/wp-content/uploads/2023/12/phpsqo-top.png)
I also identified through DNS hunting another set of about 100 sites using yet another mining scam kit. This one allows someone to connect to the site with a browser-based wallet but checks the wallet balance before allowing a connection to the contract wallet. Still others use an API from WalletConnect to obscure the contract wallet address and keep out visitors without a specific set of mobile wallets compatible with that service.
![Figure 11: USDmining[.]shop, another liquidity mining scam site, requires a balance in a connected wallet before the contract can be accessed](https://news.sophos.com/wp-content/uploads/2023/12/USDmining-shop.png)
Caveat Investor
When compared to last year’s investigations, it is clear that liquidity mining scam operations have matured in their techniques, tools, and practices, and that scam decentralized finance app “kits” have made these operations simpler to scale up—while being more accessible to less technically-capable cybercriminals. The shifting tactics in newer kits suggest significant technical efforts are being made by tool developers in the employ of the Chinese organized crime operations that back these scam rings.
Because these scams use legitimate applications that have been enabled to connect to decentralized finance applications, the best defense against these ever-maturing scams remains public awareness of the scams and healthy skepticism toward online interactions. Because victims of pig butchering-style scams such as these are often isolated and targeted through emotional appeals, wide public outreach is the only way to prevent or reduce loss.
We continue to do what we can by reporting sites, blocking them through negative reputation scores, and collaborating with hosting providers, law enforcement and cryptocurrency exchanges to get sites and exchange accounts tied to them shut down.
If you believe you are a victim of one of these scams, you should:
- Immediately withdraw all funds from the wallet that you connected to the scam site.
- Document everything you can, including messages between you and the possible scammer, your cryptocurrency wallet address, and the domain you were instructed to connect to.
- Contact law enforcement. Even if your case is not large enough on its own to warrant a federal case, contact the appropriate law enforcement agency for your locality and country (). Your data may be helpful in creating a larger case against rings.
- Contact the Cybercrime Support Network. They can provide resources to assist you in reporting crime and dealing with the aftermath.
A list of the most recently active domains discovered to be associated with these scams and other indicators of the scam operations researched here can be found on our GitHub. Additional domains will be added as we process them.

Leave a Reply