Microsoft on Tuesday released patches for 59 vulnerabilities, including 5 critical-severity issues in Azure, .Net / Visual Studio, and Windows. The largest number of addressed vulnerabilities affect Windows, with 21 CVEs – but unusually, this represents less than half of the overall patch count. It’s followed by Visual Studio, with 3 of its own and 5 more shared with .NET. 3D Builder and Office follow with 7 apiece. .NET has 6 including the 5 it shares with Visual Studio. Exchange has 5, including 4 that were actually released in August (more on that in a second); Azure has 4; Dynamics has 3. Defender, Microsoft Identity Linux Broker, and SharePoint round out the collection with one each. There are no Microsoft advisories in this month’s release.
The release also includes information on one patch for Adobe Acrobat Reader and four high-severity flaws in Edge/Chromium, both released last week. The company is also offering information on two additional patches from outside companies (Autodesk, Electron) that affect, respectively, 3D Viewer and Visual Studio.
At patch time, two issues are known to be exploited in the wild. CVE-2023-36761 is an Important-class information-disclosure vulnerability in Word accessible through Preview Pane; CVE-2023-36802 is an Important-class elevation of privilege flaw in Windows (specifically, in the Microsoft Streaming Service Proxy component). An additional 12 vulnerabilities in Windows and Exchange are by the company’s estimation more likely to be exploited in the next 30 days.
Exchange is in a particularly sensitive state this month, as four of the issues in the September release were actually released in August but, for whatever reason, were not mentioned at that time. Since the patches were in fact available for hostile scrutiny for a month already, Microsoft considers these more likely to be exploited sooner than later. Three of these can lead to remote code execution, while one results in information disclosure; all are Important-class. Exchange admins should take care to prioritize these patches.
On the topic of earlier versions, readers are reminded that this is penultimate month for Windows Server 2012 / 2012 R2 patches; the venerable OS version reaches end-of-support in October, and Microsoft has released some guidance on what customers can next. That said, the Halloween season is near and the zombies are walking, with no fewer than nine CVEs this month applicable to Server 2008. There is also one moderate-severity Office patch covering the 2013 RT SP1 and SP1 versions of that product, both of which reached end-of-support in April.
We are including at the end of this post three appendices listing all Microsoft’s patches, sorted by severity, by predicted exploitability, and by product family. As per Microsoft’s guidance we’ll treat the patches and advisories for Adobe Acrobat Reader, AutoDesk, Chromium / Edge, and Electron as information-only and not include them in the following charts and totals, though we’ve added a chart at the end of the post providing basic information on those.
By The Numbers
- Total Microsoft CVEs: 59
- Total Microsoft advisories: 0
- Total external advisories covered in update: 7
- Publicly disclosed: 2
- Exploited: 2
- Severity
- Critical: 5
- Important: 53
- Moderate: 1
- Impact
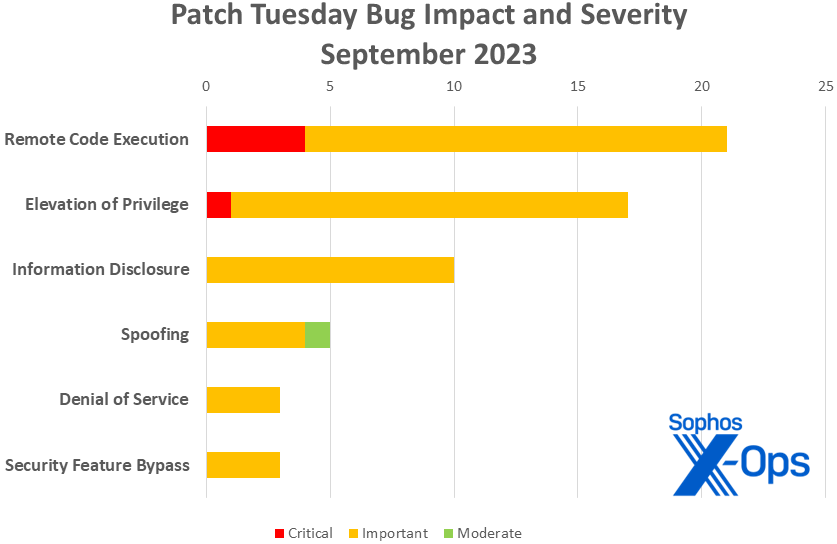
- Remote Code Execution: 21
- Elevation of Privilege: 17
- Information Disclosure: 10
- Spoofing: 5
- Denial of Service: 3
- Security Feature Bypass: 3
Figure 1: Remote code execution vulnerabilities once again lead the list for September
Products
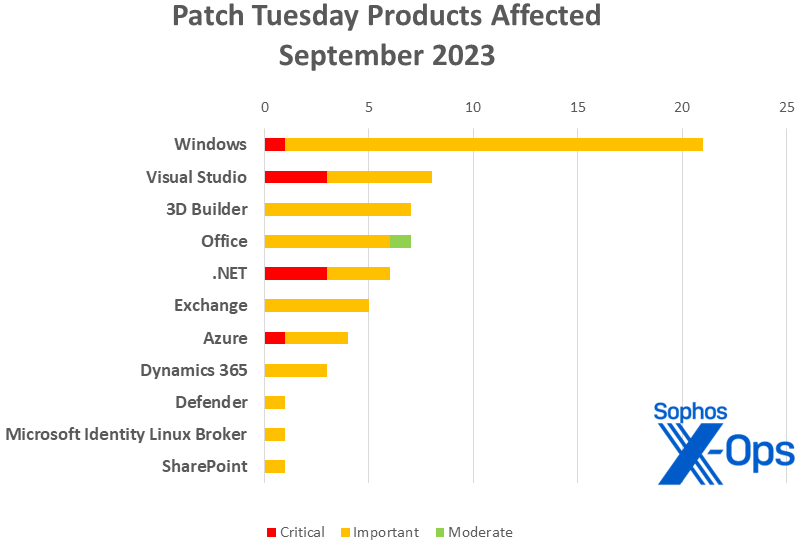
- Windows: 21
- Visual Studio: 8 (includes five with .NET; does not include advisory-only via Electron)
- 3D Builder: 7
- Office: 7
- .NET: 6 (includes 5 with Visual Studio)
- Exchange: 5 (includes four released in August 2023)
- Azure: 4
- Dynamics: 3
- 3D Viewer: 1 (advisory-only, via Autodesk)
- Defender: 1
- Microsoft Identity Linux Broker: 1
Figure 2: The September patches by product family; note that 3D Viewer fix from Autodesk is not included in this image, though it is included in the Products list above. For items that apply to more than one product family (e.g., patches shared by Visual Studio and .NET), the chart represents those patches in each family to which they apply, making the workload look slightly heavier than it will be in practice
Notable September updates
In addition to the multi-CVE Exchange situation discussed above, a few interesting items present themselves.
CVE-2023-38146 – Windows Themes Remote Code Execution Vulnerability
Themes may not be the first Windows features that comes to mind when you think of core system functionality, but plenty of end users still love personalizing their systems in that fashion. This remote-code execution flaw, which Microsoft considers Important-severity but assigns a CVSS base score of 8.8 (High, just shy of Critical), could be triggered by a specially crafted .theme file. Interestingly, a malicious theme file using this CVE would be more likely to succeed if the user were to load it via an external resource (e.g., an SMB), rather than downloading it and running it locally. Practically speaking, this means that home users are less susceptible to a successful attack, but it’s not impossible. This issue affects only Windows 11.
CVE-2023-36805 — Windows MSHTML Platform Security Feature Bypass Vulnerability
An odd Important-class item with a twist for those still running Windows Server 2012 R2: Those customers using that platform but ingesting only the Security Only updates for it will find the fix for this CVE in the IE Cumulative updates (5030209).
CVE-2023-36762 – Microsoft Word Remote Code Execution Vulnerability
CVE-2023-36766 — Microsoft Excel Information Disclosure Vulnerability
CVE-2023-36767 — Microsoft Office Security Feature Bypass Vulnerability
All three are Important-class issues; these three, however, apply to both Windows and Mac versions of the products. CVE-2023-36767 specifically affects Outlook, and Microsoft notes that while the email Preview Pane is not an attack vector, the attachment Preview Pane is.
Seven CVEs, 3D Viewer Remote Code Execution Vulnerability
All seven patches pertaining to 3D Builder are available through the Microsoft Store, as is the AutoDesk patch (CVE-2022-41303) related to 3D Viewer.
CVE-2023-38147 — Windows Miracast Wireless Display Remote Code Execution Vulnerability
An interesting Important-class vulnerability with an unusual attack vector: the attacker has to be physically close enough to the target system to send and receive radio transmissions. Once there, they could project to a vulnerable system on the same wireless network without authentication, if the system was configured to allow “Projecting to this PC” and marked as “Available Everywhere.”
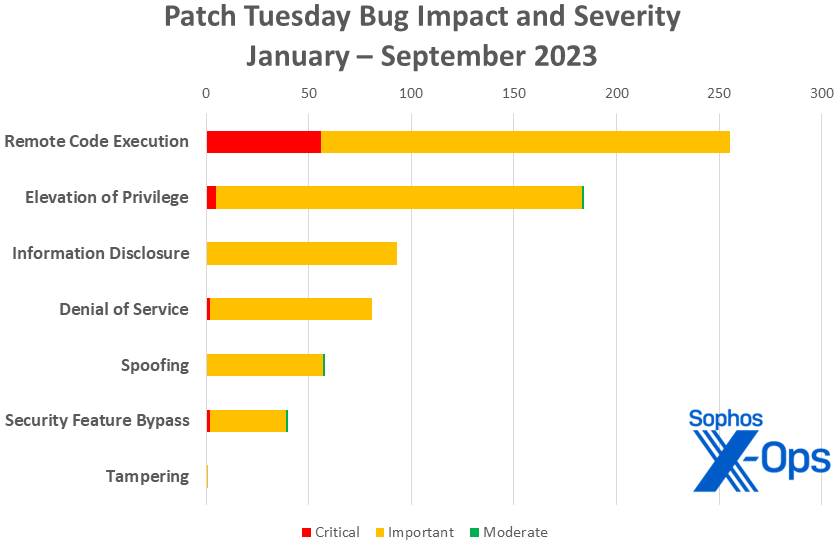
Figure 3: Two-thirds of the way through the year, remote code execution issues continue to lead the pack
Sophos protections
| CVE | Sophos Intercept X/Endpoint IPS | Sophos XGS Firewall |
| CVE-2023-26369 * | Exp/20113402-A | |
| CVE-2023-36802 | Exp/2336802-A | |
| CVE-2023-38142 | Exp/2338142-A | |
| CVE-2023-38148 | sid:2308811 | sid:2308811 |
| CVE-2023-38152 | sid:2308802 | sid:2308802 |
* This CVE is for the patch issued by Adobe today for Acrobat Reader; it is covered in Appendix D, below. The unusual-looking ID number is from a Sophos detection dating from 2011.
As you can every month, if you don’t want to wait for your system to pull down Microsoft’s updates itself, you can download them manually from the Windows Update Catalog website. Run the winver.exe tool to determine which build of Windows 10 or 11 you’re running, then download the Cumulative Update package for your specific system’s architecture and build number.
Appendix A: Vulnerability Impact and Severity
This is a list of September’s patches sorted by impact, then sub-sorted by severity. Each list is further arranged by CVE.
Remote Code Execution (21 CVEs)
| Critical severity | |
| CVE-2023-36792 | Visual Studio Remote Code Execution Vulnerability |
| CVE-2023-36793 | Visual Studio Remote Code Execution Vulnerability |
| CVE-2023-36796 | Visual Studio Remote Code Execution Vulnerability |
| CVE-2023-38148 | Internet Connection Sharing (ICS) Remote Code Execution Vulnerability |
| Important severity | |
| CVE-2023-33136 | Azure DevOps Server Remote Code Execution Vulnerability |
| CVE-2023-36739 | 3D Viewer Remote Code Execution Vulnerability |
| CVE-2023-36740 | 3D Viewer Remote Code Execution Vulnerability |
| CVE-2023-36742 | Visual Studio Code Remote Code Execution Vulnerability |
| CVE-2023-36744 | Microsoft Exchange Server Remote Code Execution Vulnerability |
| CVE-2023-36745 | Microsoft Exchange Server Remote Code Execution Vulnerability |
| CVE-2023-36756 | Microsoft Exchange Server Remote Code Execution Vulnerability |
| CVE-2023-36760 | 3D Viewer Remote Code Execution Vulnerability |
| CVE-2023-36762 | Microsoft Word Remote Code Execution Vulnerability |
| CVE-2023-36770 | 3D Builder Remote Code Execution Vulnerability |
| CVE-2023-36771 | 3D Builder Remote Code Execution Vulnerability |
| CVE-2023-36772 | 3D Builder Remote Code Execution Vulnerability |
| CVE-2023-36773 | 3D Builder Remote Code Execution Vulnerability |
| CVE-2023-36788 | .NET Framework Remote Code Execution Vulnerability |
| CVE-2023-36794 | Visual Studio Remote Code Execution Vulnerability |
| CVE-2023-38146 | Windows Themes Remote Code Execution Vulnerability |
| CVE-2023-38147 | Windows Miracast Wireless Display Remote Code Execution Vulnerability |
Elevation of Privilege (17 CVEs)
| Critical severity | |
| CVE-2023-29332 | Microsoft Azure Kubernetes Service Elevation of Privilege Vulnerability |
| Important severity | |
| CVE-2023-35355 | Windows Cloud Files Mini Filter Driver Elevation of Privilege Vulnerability |
| CVE-2023-36758 | Visual Studio Elevation of Privilege Vulnerability |
| CVE-2023-36759 | Visual Studio Elevation of Privilege Vulnerability |
| CVE-2023-36764 | Microsoft SharePoint Server Elevation of Privilege Vulnerability |
| CVE-2023-36765 | Microsoft Office Elevation of Privilege Vulnerability |
| CVE-2023-36802 | Microsoft Streaming Service Proxy Elevation of Privilege Vulnerability |
| CVE-2023-36804 | Windows GDI Elevation of Privilege Vulnerability |
| CVE-2023-38139 | Windows Kernel Elevation of Privilege Vulnerability |
| CVE-2023-38141 | Windows Kernel Elevation of Privilege Vulnerability |
| CVE-2023-38142 | Windows Kernel Elevation of Privilege Vulnerability |
| CVE-2023-38143 | Windows Common Log File System Driver Elevation of Privilege Vulnerability |
| CVE-2023-38144 | Windows Common Log File System Driver Elevation of Privilege Vulnerability |
| CVE-2023-38150 | Windows Kernel Elevation of Privilege Vulnerability |
| CVE-2023-38155 | Azure DevOps Server and Team Foundation Server Elevation of Privilege Vulnerability |
| CVE-2023-38156 | Azure HDInsight Apache Ambari Elevation of Privilege Vulnerability |
| CVE-2023-38161 | Windows GDI Elevation of Privilege Vulnerability |
Information Disclosure (10 CVEs)
| Important severity | |
| CVE-2023-36736 | Microsoft Identity Linux Broker Information Disclosure Vulnerability |
| CVE-2023-36761 | Microsoft Word Information Disclosure Vulnerability |
| CVE-2023-36763 | Microsoft Outlook Information Disclosure Vulnerability |
| CVE-2023-36766 | Microsoft Excel Information Disclosure Vulnerability |
| CVE-2023-36777 | Microsoft Exchange Server Information Disclosure Vulnerability |
| CVE-2023-36801 | DHCP Server Service Information Disclosure Vulnerability |
| CVE-2023-36803 | Windows Kernel Information Disclosure Vulnerability |
| CVE-2023-38140 | Windows Kernel Information Disclosure Vulnerability |
| CVE-2023-38152 | DHCP Server Service Information Disclosure Vulnerability |
| CVE-2023-38160 | Windows TCP/IP Information Disclosure Vulnerability |
Spoofing (5 CVEs)
| Important severity | |
| CVE-2023-36757 | Microsoft Exchange Server Spoofing Vulnerability |
| CVE-2023-36800 | Dynamics Finance and Operations Cross-site Scripting Vulnerability |
| CVE-2023-36886 | Microsoft Dynamics 365 (on-premises) Cross-site Scripting Vulnerability |
| CVE-2023-38164 | Microsoft Dynamics 365 (on-premises) Cross-site Scripting Vulnerability |
| Moderate severity | |
| CVE-2023-41764 | Microsoft Office Spoofing Vulnerability |
Denial of Service (3 CVEs)
| Important severity | |
| CVE-2023-36799 | .NET Core and Visual Studio Denial of Service Vulnerability |
| CVE-2023-38149 | Windows TCP/IP Denial of Service Vulnerability |
| CVE-2023-38162 | DHCP Server Service Denial of Service Vulnerability |
Security Feature Bypass (3 CVEs)
| Important severity | |
| CVE-2023-36767 | Microsoft Office Security Feature Bypass Vulnerability |
| CVE-2023-36805 | Windows MSHTML Platform Security Feature Bypass Vulnerability |
| CVE-2023-38163 | Windows Defender Attack Surface Reduction Security Feature Bypass |
Appendix B: Exploitability
This is a list of the September CVEs judged by Microsoft to be more likely to be exploited in the wild within the first 30 days post-release, as well as those already known to be under exploit. Each list is further arranged by CVE.
| Exploitation detected | |
| CVE-2023-36761 | Microsoft Word Information Disclosure Vulnerability |
| CVE-2023-36802 | Microsoft Streaming Service Proxy Elevation of Privilege Vulnerability |
| Exploitation more likely | |
| CVE-2023-36744 | Microsoft Exchange Server Remote Code Execution Vulnerability |
| CVE-2023-36745 | Microsoft Exchange Server Remote Code Execution Vulnerability |
| CVE-2023-36756 | Microsoft Exchange Server Remote Code Execution Vulnerability |
| CVE-2023-36777 | Microsoft Exchange Server Information Disclosure Vulnerability |
| CVE-2023-36804 | Windows GDI Elevation of Privilege Vulnerability |
| CVE-2023-38142 | Windows Kernel Elevation of Privilege Vulnerability |
| CVE-2023-38143 | Windows Common Log File System Driver Elevation of Privilege Vulnerability |
| CVE-2023-38144 | Windows Common Log File System Driver Elevation of Privilege Vulnerability |
| CVE-2023-38148 | Internet Connection Sharing (ICS) Remote Code Execution Vulnerability |
| CVE-2023-38152 | DHCP Server Service Information Disclosure Vulnerability |
| CVE-2023-38160 | Windows TCP/IP Information Disclosure Vulnerability |
| CVE-2023-38161 | Windows GDI Elevation of Privilege Vulnerability |
Appendix C: Products Affected
This is a list of September’s patches sorted by product family, then sub-sorted by severity. Each list is further arranged by CVE.
Windows (21 CVEs)
| Critical severity | |
| CVE-2023-38148 | Internet Connection Sharing (ICS) Remote Code Execution Vulnerability |
| Important severity | |
| CVE-2023-35355 | Windows Cloud Files Mini Filter Driver Elevation of Privilege Vulnerability |
| CVE-2023-36801 | DHCP Server Service Information Disclosure Vulnerability |
| CVE-2023-36802 | Microsoft Streaming Service Proxy Elevation of Privilege Vulnerability |
| CVE-2023-36803 | Windows Kernel Information Disclosure Vulnerability |
| CVE-2023-36804 | Windows GDI Elevation of Privilege Vulnerability |
| CVE-2023-36805 | Windows MSHTML Platform Security Feature Bypass Vulnerability |
| CVE-2023-38139 | Windows Kernel Elevation of Privilege Vulnerability |
| CVE-2023-38140 | Windows Kernel Information Disclosure Vulnerability |
| CVE-2023-38141 | Windows Kernel Elevation of Privilege Vulnerability |
| CVE-2023-38142 | Windows Kernel Elevation of Privilege Vulnerability |
| CVE-2023-38143 | Windows Common Log File System Driver Elevation of Privilege Vulnerability |
| CVE-2023-38144 | Windows Common Log File System Driver Elevation of Privilege Vulnerability |
| CVE-2023-38146 | Windows Themes Remote Code Execution Vulnerability |
| CVE-2023-38147 | Windows Miracast Wireless Display Remote Code Execution Vulnerability |
| CVE-2023-38149 | Windows TCP/IP Denial of Service Vulnerability |
| CVE-2023-38150 | Windows Kernel Elevation of Privilege Vulnerability |
| CVE-2023-38152 | DHCP Server Service Information Disclosure Vulnerability |
| CVE-2023-38160 | Windows TCP/IP Information Disclosure Vulnerability |
| CVE-2023-38161 | Windows GDI Elevation of Privilege Vulnerability |
| CVE-2023-38162 | DHCP Server Service Denial of Service Vulnerability |
Visual Studio (8 CVEs, includes 5 with .NET)
| Critical severity | |
| CVE-2023-36792 | Visual Studio Remote Code Execution Vulnerability |
| CVE-2023-36793 | Visual Studio Remote Code Execution Vulnerability |
| CVE-2023-36796 | Visual Studio Remote Code Execution Vulnerability |
| Important severity | |
| CVE-2023-36742 | Visual Studio Code Remote Code Execution Vulnerability |
| CVE-2023-36758 | Visual Studio Elevation of Privilege Vulnerability |
| CVE-2023-36759 | Visual Studio Elevation of Privilege Vulnerability |
| CVE-2023-36794 | Visual Studio Remote Code Execution Vulnerability |
| CVE-2023-36799 | .NET Core and Visual Studio Denial of Service Vulnerability |
3D Builder (7 CVEs)
| Important severity | |
| CVE-2023-36739 | 3D Viewer Remote Code Execution Vulnerability |
| CVE-2023-36740 | 3D Viewer Remote Code Execution Vulnerability |
| CVE-2023-36760 | 3D Viewer Remote Code Execution Vulnerability |
| CVE-2023-36770 | 3D Builder Remote Code Execution Vulnerability |
| CVE-2023-36771 | 3D Builder Remote Code Execution Vulnerability |
| CVE-2023-36772 | 3D Builder Remote Code Execution Vulnerability |
| CVE-2023-36773 | 3D Builder Remote Code Execution Vulnerability |
Office (7 CVEs)
| Important severity | |
| CVE-2023-36761 | Microsoft Word Information Disclosure Vulnerability |
| CVE-2023-36762 | Microsoft Word Remote Code Execution Vulnerability |
| CVE-2023-36763 | Microsoft Outlook Information Disclosure Vulnerability |
| CVE-2023-36765 | Microsoft Office Elevation of Privilege Vulnerability |
| CVE-2023-36766 | Microsoft Excel Information Disclosure Vulnerability |
| CVE-2023-36767 | Microsoft Office Security Feature Bypass Vulnerability |
| Moderate severity | |
| CVE-2023-41764 | Microsoft Office Spoofing Vulnerability |
.NET (6 CVEs, includes 5 with Visual Studio)
| Critical severity | |
| CVE-2023-36792 | Visual Studio Remote Code Execution Vulnerability |
| CVE-2023-36793 | Visual Studio Remote Code Execution Vulnerability |
| CVE-2023-36796 | Visual Studio Remote Code Execution Vulnerability |
| Important severity | |
| CVE-2023-36788 | .NET Framework Remote Code Execution Vulnerability |
| CVE-2023-36794 | Visual Studio Remote Code Execution Vulnerability |
| CVE-2023-36799 | .NET Core and Visual Studio Denial of Service Vulnerability |
Exchange (5 CVEs)
| Important severity | |
| CVE-2023-36744 | Microsoft Exchange Server Remote Code Execution Vulnerability |
| CVE-2023-36745 | Microsoft Exchange Server Remote Code Execution Vulnerability |
| CVE-2023-36756 | Microsoft Exchange Server Remote Code Execution Vulnerability |
| CVE-2023-36757 | Microsoft Exchange Server Spoofing Vulnerability |
| CVE-2023-36777 | Microsoft Exchange Server Information Disclosure Vulnerability |
Azure (4 CVEs)
| Critical severity | |
| CVE-2023-29332 | Microsoft Azure Kubernetes Service Elevation of Privilege Vulnerability |
| Important severity | |
| CVE-2023-33136 | Azure DevOps Server Remote Code Execution Vulnerability |
| CVE-2023-38155 | Azure DevOps Server and Team Foundation Server Elevation of Privilege Vulnerability |
| CVE-2023-38156 | Azure HDInsight Apache Ambari Elevation of Privilege Vulnerability |
Dynamics 365 (3 CVE)
| Important severity | |
| CVE-2023-36800 | Dynamics Finance and Operations Cross-site Scripting Vulnerability |
| CVE-2023-36886 | Microsoft Dynamics 365 (on-premises) Cross-site Scripting Vulnerability |
| CVE-2023-38164 | Microsoft Dynamics 365 (on-premises) Cross-site Scripting Vulnerability |
Defender (1 CVE)
| Important severity | |
| CVE-2023-38163 | Windows Defender Attack Surface Reduction Security Feature Bypass |
Microsoft Identity Linux Broker (1 CVE)
| Important severity | |
| CVE-2023-36736 | Microsoft Identity Linux Broker Information Disclosure Vulnerability |
SharePoint (1 CVE)
| Important severity | |
| CVE-2023-36764 | Microsoft SharePoint Server Elevation of Privilege Vulnerability |
Appendix D: Other Products
This is a list of advisories and third-party patches covered in the September Microsoft release, sorted by product group.
Adobe Acrobat Reader (one issue)
| CVE-2023-26369 | Out-of-bounds Write (CWE-787) |
Autodesk (one issue)
| CVE-2022-41303 | AutoDesk: CVE-2022-41303 use-after-free vulnerability in Autodesk® FBX® SDK 2020 or prior |
Chromium / Edge (4 issues)
| CVE-2023-4761 | Out of bounds memory access in FedCM |
| CVE-2023-4762 | Type Confusion in V8 |
| CVE-2023-4763 | Use after free in Networks |
| CVE-2023-4764 | Incorrect security UI in BFCache |
Electron (one issue)
| CVE-2023-39956 | Electron: CVE-2023-39956 -Visual Studio Code Remote Code Execution Vulnerability |

Leave a Reply