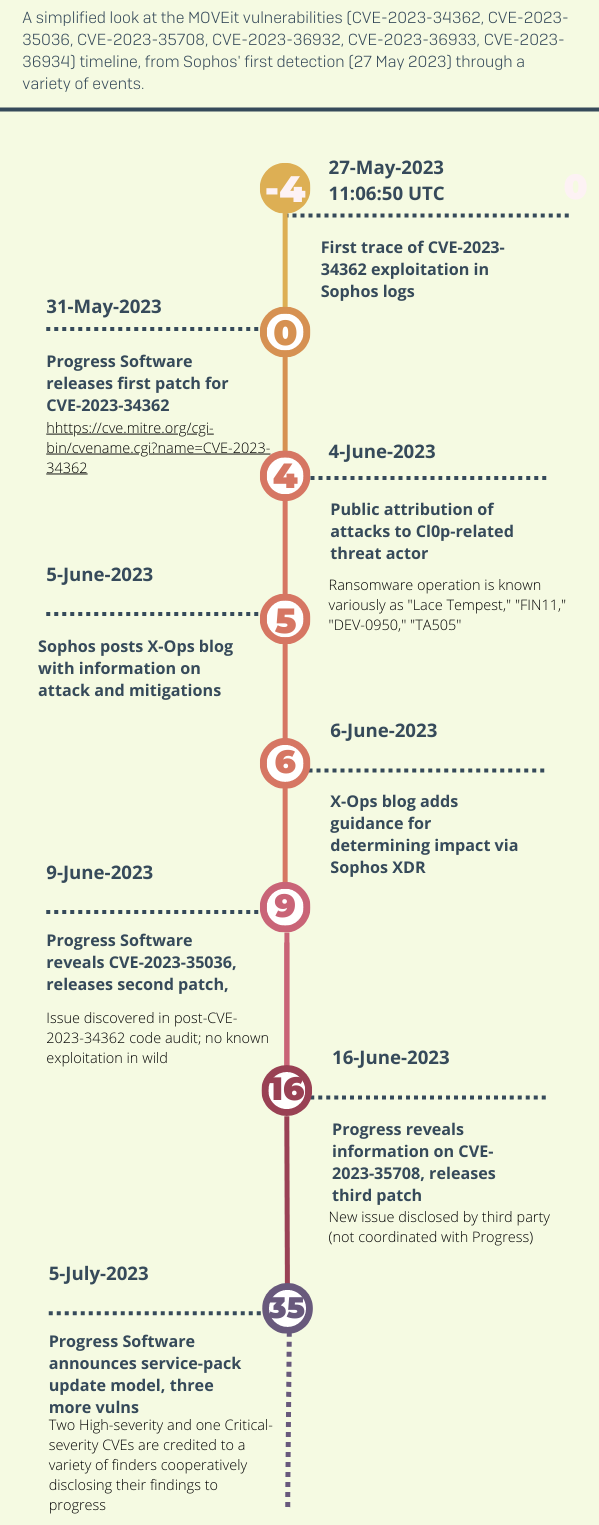
Sophos X-Ops is tracking the developing situation around SQL injection vulnerabilities affecting MOVEit Transfer and MOVEit Cloud. The vulnerabilities related to this are CVE-2023-34362, CVE-2023-35036, CVE-2023-35708, CVE-2023-36932, CVE-2023-36933, and CVE-2023-36934.
This post provides a situation overview and guidance from SophosLabs and Sophos MDR. We will update this page as events and understanding, including our threat and detection guidance, develop.
[Version 7 [Update 6] published 19:20 UTC, 11 July 2023 to add information on Sophos protections for and observed activity around CVE-2023-36934.
Version 6 [Update 5] published 21:55 UTC, 7 July 2023 to add information on three new vulnerabilities (CVE-2023-36932, CVE-2023-36933, CVE-2023-36934) and Progress’ new service-pack update model.
Version 5 [Update 4] published 20:25 UTC, 16 June 2023 to add CVE number (CVE-2023-35708) for third vulnerability and to state that MOVEit has a patch available.
Version 4 [Update 3] published 8:00 UTC, 16 June 2023 to include information from MOVEit on a third vulnerability, newly disclosed.
Version 3 [Update 2] published 20:30 UTC, 9 June 2023 to include information from MOVEit about newest patch and guidance, including notice of a second vulnerability (CVE-2023-35036).
Version 2 [Update 1] published 23:30 UTC, 6 June 2023 adding “Determining Impact with Sophos XDR” section providing datalake query and updating information on number and diversity of attacks as well as IIS log traces.
Initially posted at 22:43 UTC on 5 June 2023]
Situation Overview
UPDATED GUIDANCE AND INFORMATION:
On July 11, 2023, Sophos released new IPS signatures to protect against CVE-2023-36934 (sid:2308556 and sid:2308557). This, along with our IPS signature for CVE-2023-34362 (sid: 2308469) provide protection for Sophos customers against these vulnerabilities.
Early telemetry from our IPS signatures for CVE-2023-36934 show there are attacks against this vulnerability which was disclosed by Progress on July 5, 2023. MoveIT customers should follow Progress’ latest guidance and apply the service pack released on July 5, 2023. It’s important to note that Progress customers who have deployed previously released patches need to also deploy the latest July 5, 2023 service pack to be fully protected against all known and exploited vulnerabilities.
On July 5, 2023, Progress announced that they have formalized a service-pack-style update system for all MOVEit products. The first service pack, which was published at the time of the update, included fixes for three vulnerabilities discovered in older versions of MOVEit Transfer.
 As of June 15, 2023, Progress released a third patch and advisory material after a new vulnerability was disclosed. More information on CVE-2023-35708 is available at the link.
As of June 15, 2023, Progress released a third patch and advisory material after a new vulnerability was disclosed. More information on CVE-2023-35708 is available at the link.
As of June 9, 2023, Progress released a NEW patch. All MOVEit customers should apply this new patch as directed.
On May 31, 2023, Progress Software released a patch for CVE-2023-34362, a SQL injection vulnerability that could enable attackers to gain complete control over a MOVEit installation. (MOVEit is compliance-aware secure file transfer and automation software.) With this level of access, attackers could alter or steal data, install malicious software such as web shells, and/or alter the configuration of the server (including creating new accounts or altering existing ones), among other actions.
As discussed in the Progress advisory for on-premises customers, all MOVEit on-premises customers should apply the mitigations discussed in the advisory as soon as possible and deploy the patch as soon as possible after that. MOVEit cloud customers should read and follow the guidance in the Progress advisory for cloud customers.
Public reports indicate that attacks against this vulnerability were true “zero-day attacks” and may have begun as early as May 27, 2023 — before a patch was available or the vulnerability publicly disclosed or discussed.
These reports also indicate that known attacks against this vulnerability have focused on creating web shells on vulnerable systems and using that access to steal data from compromised systems.
On June 4, 2023, Microsoft Threat Intelligence attributed these attacks to “Lace Tempest,” which is “known for ransomware operations & running the Cl0p extortion site.” Lace Tempest is also tracked in the industry as FIN11, DEV-0950, and TA505.
Currently SophosLabs and MDR are seeing a very low number of attacks; however, the victims are diverse in both geography and sector. This correlates with the findings of other security vendors. In addition, the earliest Sophos observed exploitation occurred on May 27, 2023, four days prior to the public notification by Progress Software.
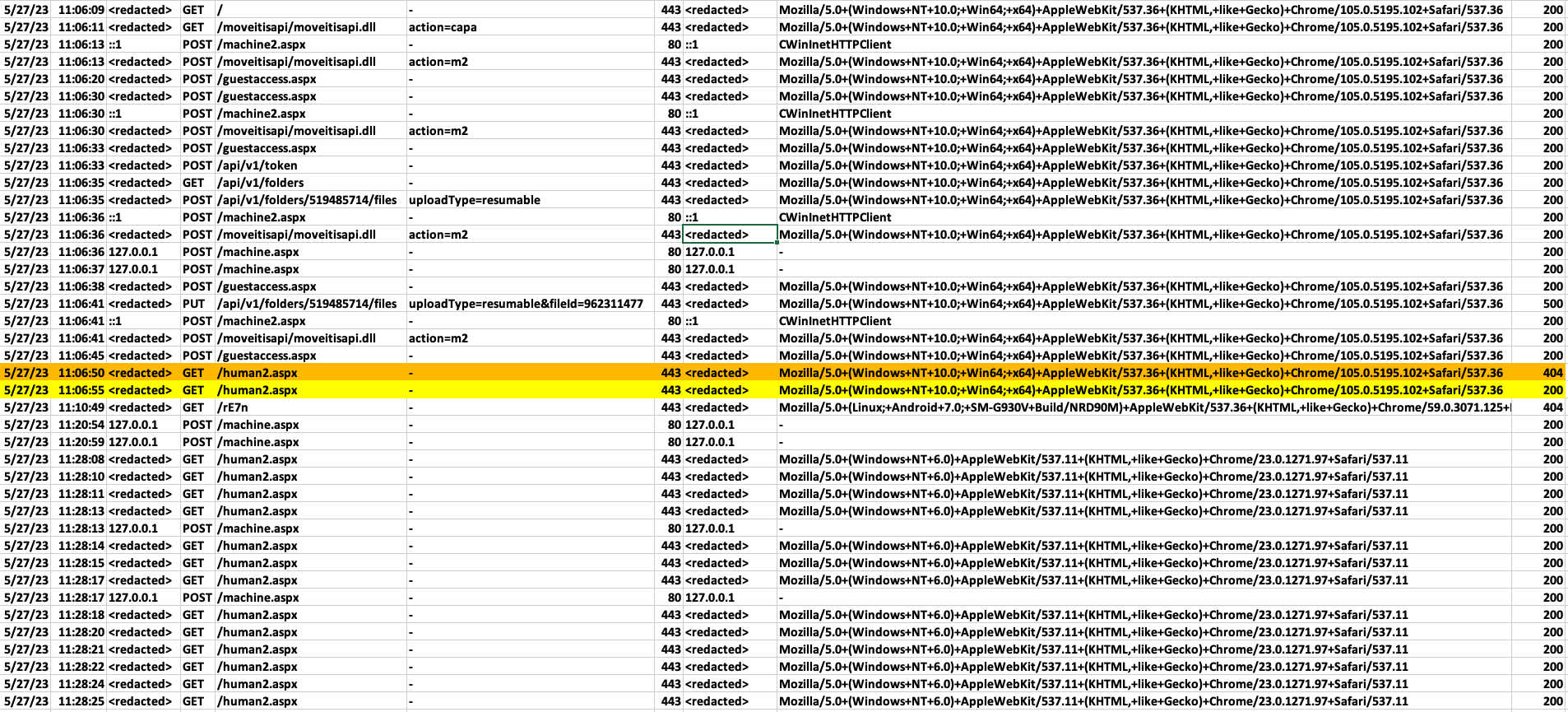
Sophos can also confirm that a key indicator of successful post-exploitation is the presence of a web shell: c:\MOVEit Transfer\wwwroot\human2.aspx. Below, in Figure 1, is an example of an attack and the follow-on web shell traffic as recorded in the IIS logs.
Figure 1: Attack in progress
Sophos products currently detect and protect against this web shell as Troj/WebShel-GO.
An additional indicator of exploitation is “App_Web_<Random8chars>.dll” generated by csc.exe compiler, which is spawned by the w3wp.exe parent process. This dll file contains the SQL injection commands, as well as the hard-coded web shell, and is likewise detected by Sophos products as Troj/WebShel-GO. All MOVEit customers should follow the steps outlined in the “Guidance” section below.
Of particular note: Since attacks began before a patch was available, all MOVEit customers should check for signs of compromise beyond those publicly discussed, as attacks could have happened before patching using methods not yet publicly identified. Also, it’s important to note that patching will NOT remove any web shells or other artifacts of compromise. This makes it critical that MOVEit customers include a check for compromise after deploying patches IN ADDITION TO deploying patches. Patching alone is NOT sufficient.
Guidance
- MOVEit on-premises customers: Apply the mitigations discussed in the advisory as soon as possible and deploy the patch as soon as possible after that, as directed in the guidance for Progress advisory for on-premises customers.
- MOVEit cloud customers: Read and follow the guidance in the Progress advisory for cloud customers.
- All MOVEit customers: Check for signs of malicious activity and take appropriate remediation action if such activity is detected.
Determining Impact with Sophos XDR
The below datalake query may be executed to review any csc.exe compiler activity related to MOVEit, which can indicate exploit attempts. Please note there will be benign activity also returned with this query, as this behavior also occurs during the software update process.
SELECT
customer_id,
meta_hostname,
date_format(from_unixtime(time), '%Y-%m-%d %H:%i:%S') as date_time,
time,
parent_sophos_pid,
sophos_pid,
parent_name,
parent_cmdline,
username,
path,
name,
cmdline,
parent_path,
sha1,
sha256,
company_name,
file_description,
file_size,
file_version,
is_process_file_signed,
original_filename,
product_name
FROM
xdr_data
WHERE
query_name = 'running_processes_windows_sophos'
AND LOWER(parent_name) = 'w3wp.exe'
AND LOWER(name) = 'csc.exe'
AND LOWER(parent_cmdline) LIKE '%moveitdmz%'
If the above query yields suspicious activity about which you would like additional details, the below query can be executed to provide deeper insight on the process. You will need to generate a variable ‘$$sophos_pid$$’ and enter the Sophos Process ID from the prior query. Similar to the first query, this may return benign results as well that require human analysis.
SELECT
STRFTIME('%Y-%m-%d %H:%M:%S',
DATETIME(sophos_process_activity.time, 'unixepoch'))
AS utc_time,
users.username,
process_journal.parent_sophos_pid,
sophos_process_activity.sophos_pid,
process_journal.path,
process_journal.process_name,
process_journal.cmd_line,
sophos_process_activity.subject,
sophos_process_activity.action,
sophos_process_activity.object,
sophos_process_activity.path,
sophos_process_activity.target_path
FROM
sophos_process_activity
LEFT JOIN sophos_process_journal AS process_journal
ON process_journal.sophos_pid = sophos_process_activity.sophos_pid
LEFT JOIN users
ON users.uuid LIKE process_journal.sid
WHERE
sophos_process_activity.sophos_pid = '$$sophos_pid$$'
AND sophos_process_activity.action = 'Created'
AND sophos_process_activity.object LIKE '%.dll'
Lastly, if you do have IIS log files available, the following query can be used to search for web shell activity. You will need to generate a variable, ‘$$log_path$$’ and enter the file path to the IIS log that you would like to review.
WITH sorter AS (
WITH content AS
--Split the raw log into sortable columns
(
SELECT
-- Grab data from the IIS logs, removing comment lines and limiting returned line count to ensure functionality
grep.line
FROM file
CROSS JOIN grep ON (grep.path = file.path)
WHERE
file.path LIKE '$$log_path$$'
AND (
grep.pattern = 'POST /api/v1/token'
OR grep.pattern = 'POST /guestaccess.aspx'
OR grep.pattern = 'GET /human2.aspx'
OR grep.pattern = 'GET /api/v1/folders'
)
)
SELECT
CAST(SPLIT(line,' ',0) AS TEXT) AS iis_date,
CAST(SPLIT(line,' ',1) AS TEXT) AS iis_time,
SPLIT(line,' ',2) AS source_ip,
SPLIT(line,' ',3) AS cs_method,
SPLIT(line,' ',4) AS cs_uri_stem,
SPLIT(line,' ',5) AS cs_uri_query,
SPLIT(line,' ',6) AS source_port,
SPLIT(line,' ',7) AS cs_username,
SPLIT(line,' ',8) AS remote_ip,
SPLIT(line,' ',9) AS user_agent,
SPLIT(line,' ',10) AS referer,
SPLIT(line,' ',11) AS status,
SPLIT(line,' ',12) AS substatus,
SPLIT(line,' ',13) AS win32status,
SPLIT(line,' ',14) AS timetaken
FROM content
WHERE iis_date NOT LIKE '#%'
)
SELECT
--CAST(MIN(datetime(iis_date || ' ' || iis_time)) AS varchar) AS first_seen,
--CAST(MAX(datetime(iis_date || ' ' || iis_time)) AS varchar) AS last_seen,
datetime(iis_date || ' ' || iis_time) AS timestamps,
source_ip,
cs_method,
cs_uri_stem,
cs_uri_query,
source_port,
cs_username,
remote_ip,
user_agent,
referer,
status,
CASE
WHEN status LIKE '100' THEN 'Continue'
WHEN status LIKE '101' THEN 'Switching protocols'
WHEN status LIKE '200' THEN 'OK. The client request has succeeded'
WHEN status LIKE '201' THEN 'Created'
WHEN status LIKE '202' THEN 'Accepted'
WHEN status LIKE '203' THEN 'Nonauthoritative information'
WHEN status LIKE '204' THEN 'No content'
WHEN status LIKE '205' THEN 'Reset content'
WHEN status LIKE '206' THEN 'Partial content'
WHEN status LIKE '301' THEN 'Moved permanently'
WHEN status LIKE '302' THEN 'Object moved'
WHEN status LIKE '304' THEN 'Not modified'
WHEN status LIKE '307' THEN 'Temporary redirect'
WHEN status LIKE '400' THEN 'Bad request'
WHEN status LIKE '401' THEN 'Access denied'
WHEN status LIKE '403' THEN 'Forbidden'
WHEN status LIKE '404' THEN 'Page Not found'
WHEN status LIKE '405' THEN 'Method Not Allowed'
WHEN status LIKE '406' THEN 'Client browser does not accept the MIME type of the requested page'
WHEN status LIKE '408' THEN 'Request timed out'
WHEN status LIKE '412' THEN 'Precondition faile'
WHEN status LIKE '500' THEN 'Internal server error'
WHEN status LIKE '501' THEN 'Header values specify a configuration that is not implemented'
WHEN status LIKE '502' THEN 'Web server received an invalid response while acting as a gateway or proxy'
WHEN status LIKE '503' THEN 'Service unavailable'
ELSE 'unknown'
END AS 'status_def',
CASE
WHEN status LIKE '400' AND substatus LIKE '1' THEN 'Invalid Destination Header'
WHEN status LIKE '400' AND substatus LIKE '2' THEN 'Invalid Depth Header'
WHEN status LIKE '400' AND substatus LIKE '3' THEN 'Invalid If Header'
WHEN status LIKE '400' AND substatus LIKE '4' THEN 'Invalid Overwrite Header'
WHEN status LIKE '400' AND substatus LIKE '5' THEN 'Invalid Translate Header'
WHEN status LIKE '400' AND substatus LIKE '6' THEN 'Invalid Request Body'
WHEN status LIKE '400' AND substatus LIKE '7' THEN 'Invalid Content Length'
WHEN status LIKE '400' AND substatus LIKE '8' THEN 'Invalid Timeout'
WHEN status LIKE '400' AND substatus LIKE '9' THEN 'Invalid Lock Token'
WHEN status LIKE '401' AND substatus LIKE '1' THEN 'Logon failed'
WHEN status LIKE '401' AND substatus LIKE '2' THEN 'Logon failed due to server configuration'
WHEN status LIKE '401' AND substatus LIKE '3' THEN 'Unauthorized due to ACL on resource'
WHEN status LIKE '401' AND substatus LIKE '4' THEN 'Authorization failed by filter'
WHEN status LIKE '401' AND substatus LIKE '5' THEN 'Authorization failed by ISAPI/CGI application'
WHEN status LIKE '401' AND substatus LIKE '501' THEN 'Access Denied: Too many requests from the same client IP; Dynamic IP Restriction Concurrent request rate limit reached'
WHEN status LIKE '401' AND substatus LIKE '502' THEN 'Forbidden: Too many requests from the same client IP; Dynamic IP Restriction Maximum request rate limit reached'
WHEN status LIKE '401' AND substatus LIKE '503' THEN 'Access Denied: the IP address is included in the Deny list of IP Restriction'
WHEN status LIKE '401' AND substatus LIKE '504' THEN 'Access Denied: the host name is included in the Deny list of IP Restriction'
WHEN status LIKE '403' AND substatus LIKE '1 ' THEN 'Execute access forbidden'
WHEN status LIKE '403' AND substatus LIKE '2 ' THEN 'Read access forbidden'
WHEN status LIKE '403' AND substatus LIKE '3 ' THEN 'Write access forbidden'
WHEN status LIKE '403' AND substatus LIKE '4 ' THEN 'SSL required'
WHEN status LIKE '403' AND substatus LIKE '5 ' THEN 'SSL 128 required'
WHEN status LIKE '403' AND substatus LIKE '6 ' THEN 'IP address rejected'
WHEN status LIKE '403' AND substatus LIKE '7 ' THEN 'Client certificate required'
WHEN status LIKE '403' AND substatus LIKE '8 ' THEN 'Site access denied'
WHEN status LIKE '403' AND substatus LIKE '9 ' THEN 'Forbidden: Too many clients are trying to connect to the web server'
WHEN status LIKE '403' AND substatus LIKE '10' THEN 'Forbidden: web server is configured to deny Execute access'
WHEN status LIKE '403' AND substatus LIKE '11' THEN 'Forbidden: Password has been changed'
WHEN status LIKE '403' AND substatus LIKE '12' THEN 'Mapper denied access'
WHEN status LIKE '403' AND substatus LIKE '13' THEN 'Client certificate revoked'
WHEN status LIKE '403' AND substatus LIKE '14' THEN 'Directory listing denied'
WHEN status LIKE '403' AND substatus LIKE '15' THEN 'Forbidden: Client access licenses have exceeded limits on the web server'
WHEN status LIKE '403' AND substatus LIKE '16' THEN 'Client certificate is untrusted or invalid'
WHEN status LIKE '403' AND substatus LIKE '17' THEN 'Client certificate has expired or is not yet valid'
WHEN status LIKE '403' AND substatus LIKE '18' THEN 'Cannot execute requested URL in the current application pool'
WHEN status LIKE '403' AND substatus LIKE '19' THEN 'Cannot execute CGI applications for the client in this application pool'
WHEN status LIKE '403' AND substatus LIKE '20' THEN 'Forbidden: Passport logon failed'
WHEN status LIKE '403' AND substatus LIKE '21' THEN 'Forbidden: Source access denied'
WHEN status LIKE '403' AND substatus LIKE '22' THEN 'Forbidden: Infinite depth is denied'
WHEN status LIKE '403' AND substatus LIKE '501' THEN 'Forbidden: Too many requests from the same client IP; Dynamic IP Restriction Concurrent request rate limit reached'
WHEN status LIKE '403' AND substatus LIKE '502' THEN 'Forbidden: Too many requests from the same client IP; Dynamic IP Restriction Maximum request rate limit reached'
WHEN status LIKE '403' AND substatus LIKE '503' THEN 'Forbidden: the IP address is included in the Deny list of IP Restriction'
WHEN status LIKE '403' AND substatus LIKE '504' THEN 'Forbidden: the host name is included in the Deny list of IP Restriction'
WHEN status LIKE '404' AND substatus LIKE '0' THEN 'Page Not found'
WHEN status LIKE '404' AND substatus LIKE '1' THEN 'Site Not Found'
WHEN status LIKE '404' AND substatus LIKE '2' THEN 'ISAPI or CGI restriction'
WHEN status LIKE '404' AND substatus LIKE '3' THEN 'Multipurpose Internet Mail Extensions (MIME) type restriction'
WHEN status LIKE '404' AND substatus LIKE '4' THEN 'No handler configured'
WHEN status LIKE '404' AND substatus LIKE '5' THEN 'Denied by request filtering configuration'
WHEN status LIKE '404' AND substatus LIKE '6' THEN 'Verb denied'
WHEN status LIKE '404' AND substatus LIKE '7' THEN 'File extension denied'
WHEN status LIKE '404' AND substatus LIKE '8' THEN 'Hidden namespace'
WHEN status LIKE '404' AND substatus LIKE '9' THEN 'File attribute hidden'
WHEN status LIKE '404' AND substatus LIKE '10' THEN 'Request header too long'
WHEN status LIKE '404' AND substatus LIKE '11' THEN 'Request contains double escape sequence'
WHEN status LIKE '404' AND substatus LIKE '12' THEN 'Request contains high-bit characters'
WHEN status LIKE '404' AND substatus LIKE '13' THEN 'Content length too large'
WHEN status LIKE '404' AND substatus LIKE '14' THEN 'Request URL too long'
WHEN status LIKE '404' AND substatus LIKE '15' THEN 'Query string too long'
WHEN status LIKE '404' AND substatus LIKE '16' THEN 'DAV request sent to the static file handler'
WHEN status LIKE '404' AND substatus LIKE '17' THEN 'Dynamic content mapped to the static file handler via a wildcard MIME mapping'
WHEN status LIKE '404' AND substatus LIKE '18' THEN 'Querystring sequence denied'
WHEN status LIKE '404' AND substatus LIKE '19' THEN 'Denied by filtering rule'
WHEN status LIKE '404' AND substatus LIKE '20' THEN 'Too Many URL Segments'
WHEN status LIKE '404' AND substatus LIKE '501' THEN 'Not Found: Too many requests from the same client IP; Dynamic IP Restriction Concurrent request rate limit reached'
WHEN status LIKE '404' AND substatus LIKE '502' THEN 'Not Found: Too many requests from the same client IP; Dynamic IP Restriction Maximum request rate limit reached'
WHEN status LIKE '404' AND substatus LIKE '503' THEN 'Not Found: the IP address is included in the Deny list of IP Restriction'
WHEN status LIKE '404' AND substatus LIKE '504' THEN 'Not Found: the host name is included in the Deny list of IP Restriction'
ELSE substatus || ' - Not Defined'
END AS substatus,
win32status,
timetaken
FROM sorter
Detection Protection
SophosLabs has blocked the malicious domains and published the following detections:
IPS Signatures:
- CVE-2023-36934 (sid:2308556 and sid:2308557)
- CVE-2023-34362 (sid: 2308469)
Static detections:
- Troj/WebShel-GO
Resources
More information on this emerging situation can be found on Sophos Naked Security.
Acknowledgements
Thanks to Andrew Ludgate and Mark Parsons for contributions to this writeup.

Leave a Reply