In November 2022, we wrote about a multi-country takedown against a Cybercrime-as-a-Service (CaaS) system known as iSpoof.
Although iSpoof advertised openly for business on a non-darkweb site, reachable with a regular browser via a non-onion domain name, and even though using its services might technically have been legal in your country (if you’re a lawyer, we’d love to hear your opinion on that issue once you’ve seen the historical website screenshots below)…
…a UK court had no doubt that the iSpoof system was implemented with life-ruining, money-draining malfeasance in mind.
The site’s kingpin, Tejay Fletcher, 35, of London, was given a prison sentence of well over a decade to reflect that fact.
Show any number you like
Until November 2022, when the domain was taken down after a seizure warrant was issued to US law enforcement, the site’s main page looked something like this:
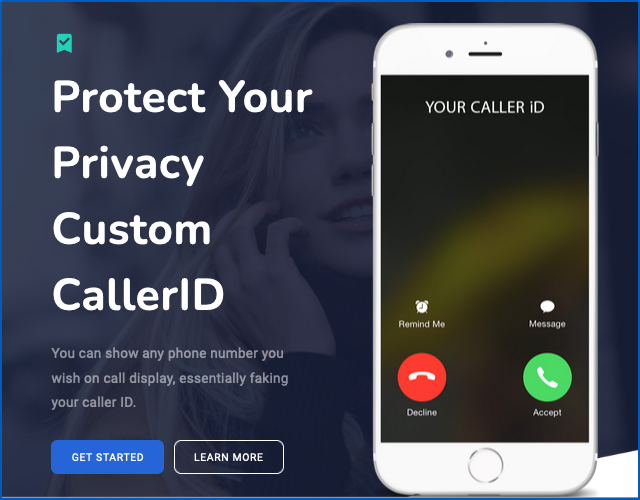
You can show any number you wish on call display, essentially faking your caller ID.
And an explanatory section further down the page made it pretty clear that the service wasn’t merely there to enhance your own privacy, but to help you mislead the people you were calling:
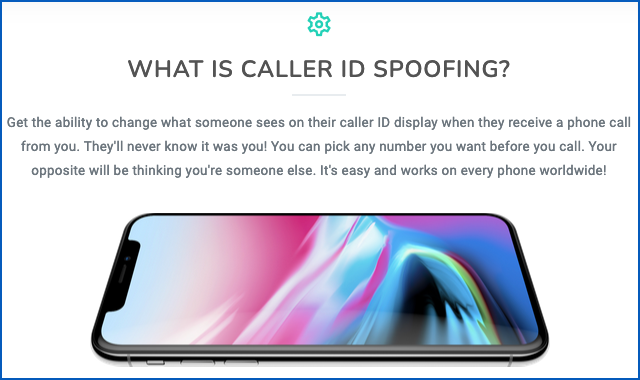
Get the ability to change what someone sees on their caller ID display when they receive a phone call from you. They’ll never know it was you! You can pick any number you want before you call. Your opposite will be thinking you’re someone else. It’s easy and works on every phone worldwide!
In case you were still in any doubt about how you could use iSpoof to help you rip off unsuspecting victims, here’s the site’s own marketing video, provided courtesy of the Metropolitan Police (better known as “the Met”) in London, UK:
As you will see below, and in our previous coverage of this story, iSpoof users weren’t actually anonymous at all.
More than 50,000 users of the service have been identified already, with close to 200 people already arrested and under investigation in the UK alone.
Pretend to be a bank…
Simply put, if you signed up for iSpoof’s service, no matter how technical or non-technical you were, you could immediately start placing calls that would show up on victims’ phones as if those calls were coming from a company that they already trusted.
As the Metropolitan Police put it:
Users of iSpoof, who had to pay to use its services, posed as representatives of banks including Barclays, Santander, HSBC, Lloyds and Halifax [well-known British banks], pretending to warn of suspicious activity on their accounts.
Scammers would encourage the unsuspecting members of the public to disclose security information such as one-time passcodes to obtain their money.
The total reported loss from those targeted via iSpoof is £48 million in the UK alone, with average loss believed to be £10,000. Because fraud is vastly under reported, the full amount is believed to be much higher.
In the 12 months until August 2022 around 10 million fraudulent calls were made globally via iSpoof, with around 3.5 million of those made in the UK.
Interestingly, the Met says that about 10% of those UK calls (about 350,000 in all), made to 200,000 different potential victims, lasted more than a minute, suggesting a surprisingly high success rate for scammers who used the iSpoof service to give their bogus calls a fraudulent air of legitimacy.
When calls arrive from a number you’re inclined to trust – for example, a number you use sufficiently often that you’ve added it into your own contact list so it comes up with an identifier of your choice, such as Credit Card Company, rather than something generic-looking such as +44.121.496.0149…
…you’re unsurprisingly more likely to trust the caller implicitly before you hear what they’ve got to say.
After all, the system that transmits away the caller’s number to the recipient before the call is even answered is known in the jargon as Caller ID, or Calling Line Identification (CLI) outside North America.
It’s not any sort of ID
Those magic words ID and identification shouldn’t really be there, because a technically savvy caller (or a completely non-technical caller who was using the iSpoof service) could insert any number they liked when initiating the call.
In other words, Caller ID not only tells you nothing about the person using the phone that’s calling you, but also tells you nothing trustworthy about the number of the phone that’s calling you.
Caller ID “identifies” the caller and the calling number no more reliably that the return address that’s printed on the back of a snail-mail envelope, or the Reply-To address that’s in the headers of any emails you receive.
All those “identifications” can be chosen by the originator of the communication, and can say pretty much anything that the sender or caller chooses.
They should really be called What the Caller Wants you to Think, Which Could Be a Pack of Lies, rather than being referred to as an ID or an identification.
And there was an awful lot of lying going on, thanks to iSpoof, with the Met claiming:
Before it was shut down in November 2022, iSpoof was constantly growing. 700 new users were registering with the site every week and it was earning on average £80,000 per week. At the point of closure it had 59,000 registered users.
The website offered a number of packages for users who would buy, in Bitcoin, the number of minutes they wanted to use the software for to make calls.
The site raked in loads of profit, according to the Met:
iSpoof made just over £3 million with Fletcher profiting around £1.7-£1.9 million from running and enabling fraudsters to ruin victim’s lives. He lived an extravagant lifestyle, owning a Range Rover worth £60,000 and a Lamborghini Urus worth £230,000. He regularly went on holiday, with trips to Jamaica, Malta and Turkey in 2022 alone.
Earlier in 2023, Fletcher pleaded guilty to the offences of making or supplying articles for use in fraud, encouraging or assisting the commission of an offence, possessing criminal property and transferring criminal property.
Last week he was given a prison sentence of 13 years and 4 months; 169 other people in the UK “have now been arrested on suspicion of using iSpoof [and] remain under police investigation.”
What to do?
- TIP 1. Treat Caller ID as nothing more than a hint.
The most important thing to remember (and to explain to any friends and family you think might be vulnerable to this sort of scam) is this: THE CALLER’S NUMBER THAT SHOWS UP ON YOUR PHONE BEFORE YOU ANSWER PROVES NOTHING.
- TIP 2. Always initiate official calls yourself, using a number you can trust.
If you genuinely need to contact an organisation such as your bank by phone, make sure that you initiate the call, and use a number than you worked out for yourself.
For example, look at a recent official bank statement, check the back of your bank card, or even visit a branch and ask a staff member face-to-face for the official number that you should call in future emergencies.
- TIP 3. Be there for vulnerable friends and family.
Make sure that friends and family whom you think could be vulnerable to being sweet-talked (or browbeaten, confused and intimidated) by scammers, no matter how they’re first contacted, know that they can and should turn to you for advice before agreeing to anything over the phone.
And if anyone asks them to do something that’s clearly an intrusion of their personal digital space, such as installing Teamviewer to let them onto the computer, reading out a secret access code off the screen, or telling them a personal identification number or password…
…make sure they know it’s OK simply to hang up without saying a single word further, and getting in touch with you to check the facts first.

Mahhn
Great news to hear!!
Busted and thousands of scum to be Doxed, and get the karma they worked for.
Now if the telecoms would stop Enabling these types of crimes by allowing spoofing…..
Paul Ducklin
Will be interesting to see how many of the other people who thought they ere anonymous but got busted anyway end up getting prosecuted and convicted. Apparently, the UK cops started with anyone who had spent more than £100’s worth of BTC (about $125) to buy services from the site.
This suggests, fortunately, that most of the “customers” didn’t get drawn in very deeply… but even one spoofed call (e.g. to stalk someone) can be considered bad enough.
Maybe some of them will just “get a talking to”, or a police caution, or something of that sort. Unfortunately, it’s hard to imagine the Crown Prosecution Service having the time and funds available to prosecute 1000s of what the state might see as “low-level” criminality.
I guess that’s why the cops are still appealing to anyone who has received spoofed calls to contact them. Apparently, several hundred victims came forward as a result of the arrests last year, perhaps because they didn’t know they could report it until the matter got some publicity.
hilgarj
I do not think the information in this article is entirely accurate. In the United States phone companies such as AT&T, T-Mobile, and Verizon have implemented the FCC’s anti-spoofing protocol, known as STIR/SHAKEN, to prevent scam and spam callers from spoofing their number and showing up on caller ID as a local caller. STIR/SHAKEN works by adding a digital certificate to the Session Initiation Protocol information used to initiate and route calls in VoIP systems. So when another Verizon user calls my Verizon phone I see a V next to their number and I know it is truly from that number.
Paul Ducklin
As far as I can see, some calls between some users on some services provided by some mobile phone companies in some countries may have a letter V added to the number to denote…
…verified? Verizon?
I think it’s still fair to say that for most calls between most users on most services in most countries (and still for some calls in countries where STIR/SHAKEN is available), Caller ID is not yet any sort of “trustworthiness proof”. I therefore stick by my advice to “treat it as a hint”, and to call important services such as your card provider or your bank back yourself.
Mahhn
I get spoofed calls every day, for over 2 years now (5-25 a day). I auto ignore all calls not in my phonebook, anyone else that is legit can leave a message.. I suspect most of the spoofed calls originate from India and Bangladesh (from before I was ignoring them). – I had to look up the stir/shaken- From https://www.fcc.gov/call-authentication “foreign calls into the United States—are similarly required to apply STIR/SHAKEN to foreign-originated calls by June 30, 2023.”
Fingers crossed this actually works.
Paul Ducklin
I can’t help but think that STIR/SHAKEN is a bit like getting a “cybersecurity badge” for your website: it tells you the other person is using STIR/SHAKEN, but it doesn’t vouch for the caller themselves or for the truthfulness of what they tell you.
Part of the problem is that the well-established US name, “Caller ID”, is seductively misleading. It’s a bit like using a name such as “Fact-checking Approval Service” to describe TLS, when all TLS means is “transport layer security”, which at least says what it does.
Julio Martínez
STIR SHAKEN would give assurance the caller ID is authentic or would give you a warning and leave it up to you. It’s a regulation in USA, but not in Europe or other parts of the world.
Dave Goodrich
I don’t get it. This group got busted for selling the service of faking your caller ID? Why? Dell Computing still calls my desk once a month and it NEVER says Dell. Mostly it says anonymous. Nearly every cold call I get has a faked caller ID. Just last week I got a call to consolidate my student debt, which I have none, and the caller ID said Shirley Indiana. Shirley has a population of maybe 75 people. When I asked if they really had an office there the caller claimed it was their home office.
I am not taking his side here, but why is this guy getting singled out? Everyone is faking caller ID. STIR/SHAKEN is a scam, it made no difference in the number of fake caller IDs I see on my phone.
DAve
Paul Ducklin
A few notes: firstly, this guy wasn’t helping people to suppress Caller ID/CLI (you can turn it off in your own phone) but enabling them to spoof other companies’ phone well-known numbers to make fraud easier; secondly, his marketing material and service “features” make it clear that no one was buying into this service just to pretend to be from Shirley, Indiana, but instead to pretend to be from your bank; and thirdly, he wasn’t charged or prosecuted in the US, but in England, so different laws and telco regulations apply. (STIR/SHAKEN is not mandated for anyone; nor, so far as I know, is it used anywhere here.)
I *think* our anti-spoofing rules were tightened up a bit recently, but that was in November 2022 and those rules would not have been in force when iSpoof was active and the kingpin charged. Still no mandatory cryptographic protocols, if memory serves.
Write to your Congressperson? (I am not being facetious here; I don’t know what else to suggest.)
Anonymous
I appreciate the clear thoughts Paul. But, faking your company and faking where your company is/what it does/how it came by your PIM/etc are the same thing in my mind. It is deceit.
As far as what to do about caller ID? Rather than writing to the government, I simply stopped answering calls from places I have never been or people I do not know.
DAve
Paul Ducklin
The problem here, of course, is that you can’t tell that you don’t know the caller until after you answer… and by the time you do that, you are more likely to believe them because the call feels legitimate.
By all means refuse to answer calls that are clearly *not* from anyone you know, but don’t forget that Caller ID doesn’t mean the caller is someone you *do* know, merely that they aren’t obviously someone you don’t.
And if that sounds weirdly vague… it IS vague, because Caller ID is vague and, in general (except perhaps for some calls from some users on some networks in the US) is no more trustworthy than the name that someone tells you when you call them and they answer.
(When someone says, “Hi, this is Aaron Abdabs from Aardvark Corp”, it might actually be Zoe Zzyzx from Zymurgy Inc for all you know… a “known unknown”, as you might call it.)