[Update, 2023-05-10: Additional information added about CVE-2023-24932]
Microsoft on Tuesday released patches for 38 vulnerabilities in 6 product families, including 6 Critical-severity issues in Windows and one in SharePoint. As usual, the largest number of addressed vulnerabilities affect Windows, with 27 CVEs. Office follows with 4 CVEs, then SharePoint (3), AV1 Video Extension (2), and Teams and Visual Studio (one each).
At patch time, just two of the issues this month (CVE-2023-29325 and CVE-2023-24932, both Windows) have been publicly disclosed. Microsoft’s updated guidance for CVE-2023-24932 (aka Secure Boot Security Feature Bypass) says this bug has been exploited in the wild by malware called the BlackLotus UEFI bootkit. The company also published additional Secure Boot exploit mitigations that some system administrators may want to take to protect specific systems from BlackLotus; The mitigations, once enabled, are not reversible: In Microsoft’s words, “Even reformatting of the disk will not remove the revocations if they have already been applied.” These mitigations also have a dramatic effect on recovery images, or bootable external media. “After these revocations are applied, the devices will intentionally become unable to start by using recovery or installation media, unless this media has been updated with the security updates released on or after May 9, 2023. This includes both bootable media, such as discs, external drives, network boot recovery, and restore images,” the company writes.
As for the rest, only one other has been detected under exploit in the wild: CVE-2023-29336, an Important-severity elevation-of-privilege issue in Windows. However, Microsoft cautions that eight of the issues addressed are more likely to be exploited in either the latest or earlier versions of the affected product soon (that is, within the next 30 days). Interestingly, Microsoft this month offered no guidance overview on exploitation likelihood in earlier versions versus latest versions for any of the 38 patches, though a few apply only to one or the other.
By popular demand, we are including at the end of this post three appendices listing all the month’s patches, sorted by severity, by predicted exploitability, and by product family.
By the numbers
- Total Microsoft CVEs: 38
- Total advisories shipping in update: 0
- Publicly disclosed: 2
- Exploited: 1
- Severity
- Critical: 7
- Important: 31
- Impact
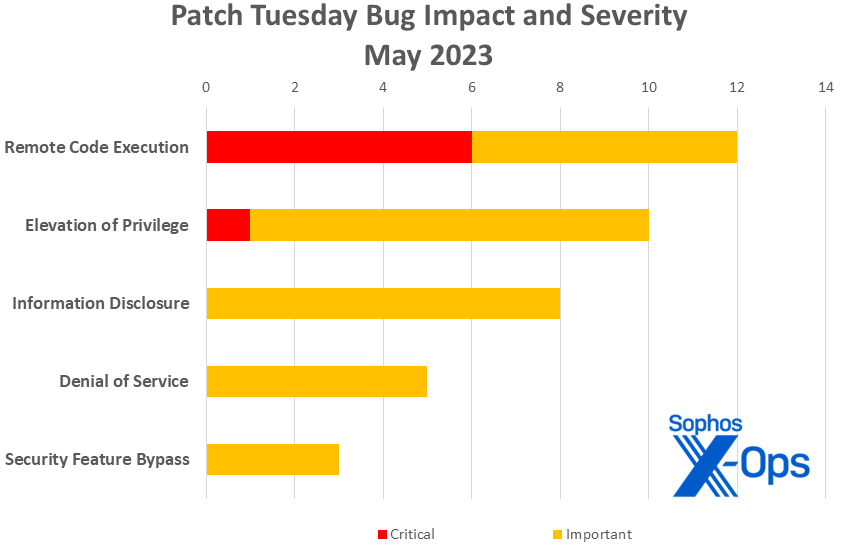
- Remote code execution: 12
- Elevation of privilege: 10
- Information disclosure: 8
- Denial of service: 5
- Security feature bypass: 3
Figure 1: Remote code execution issues once again make up the largest portion of May 2023’s patches from Microsoft, but security feature bypass makes a stronger-than-usual swing with three patches
The six product families in the May release:
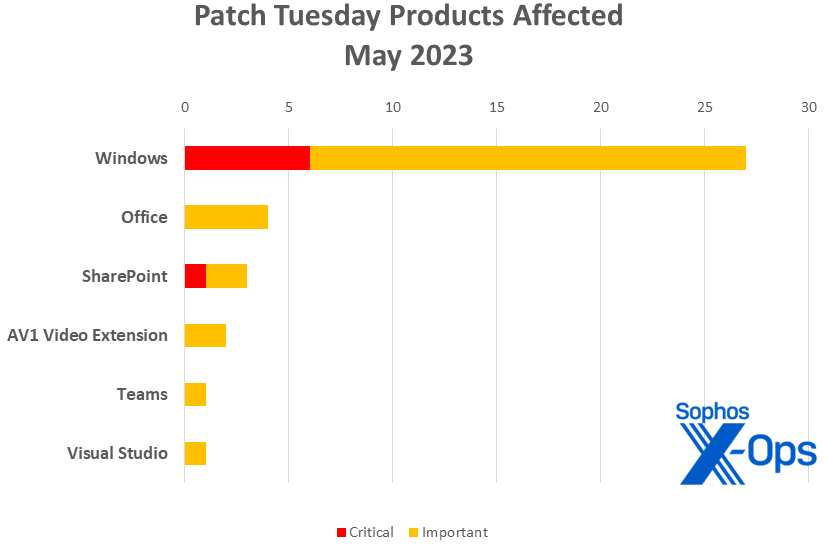
- Windows: 27
- Office: 4
- SharePoint: 3
- AV1 Video Extension: 2
- Teams: 1
- Visual Studio: 1
Microsoft also acknowledged three Chromium-related CVEs and five GitHub-related CVEs in this month patch-release announcements. The three Chromium-related issues (CVE-2023-29334, CVE-2023-29350, CVE-2023-29354) were patched prior to today’s release, while the five GitHub-related issues (CVE-2023-25652, CVE-2023-25815, CVE-2023-29007, CVE-2023-29011, CVE-2023-29012), all of which affect Visual Studio, were patched today.
Figure 2: Windows patches make up two-thirds of the May 2023 load, and six of seven of the Critical-class issues
Notable May updates
CVE-2023-24941 – Windows Network File System Remote Code Execution Vulnerability
CVE-2023-29325 – Windows OLE Remote Code Execution Vulnerability
Both of these Critical-class RCE patches are thought to be more likely to end up under active exploitation within the next 30 days; worse, both come with fairly detailed installation requirements. System administrators are cautioned to read the instructions very carefully and, in the case of the NFS patch, to be sure that a patch addressing CVE-2022-26937 (released May 2022) is already installed.
CVE-2023-24932 – Secure Boot Security Feature Bypass Vulnerability
As with the previous two patches, this one comes with extra steps: The patch updates Windows Boot Manager, but it’s not enabled by default, so additional steps by the system administrator will be necessary. This patch is related to ongoing attempts to address a vulnerability used by the BlackLotus bootkit. Microsoft described their progress on that process in a standalone post.
CVE-2023-24881 — Microsoft Teams Information Disclosure Vulnerability
Continuing the theme of the Notable Updates this month, this Important-class information disclosure issue takes a bit more attention than usual. First, sysadmins must upgrade to the latest Teams JavaScript SDK library; second, sysadmins must not refer to any domain outside their own control, and must avoid any wildcard domains. System administrators are strongly advised to review Microsoft’s guidance on this patch before proceeding.
CVE-2023-29340 — AV1 Video Extension Remote Code Execution Vulnerability
Finally, this Important-class RCE, one of two addressing AV1 this month, only affects users who installed their extension through the Microsoft Store – and then only if they don’t have auto-updates enabled.
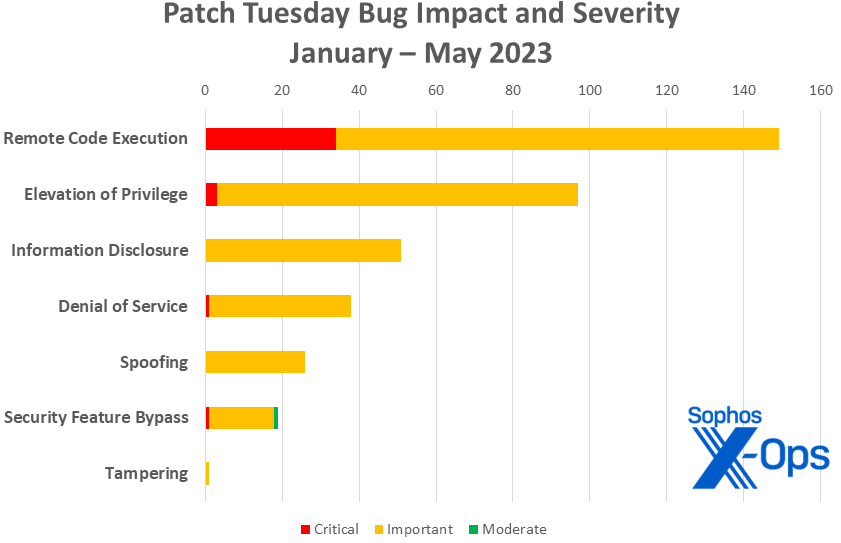
Figure 3: As the year goes on, remote code execution flaws account for the largest number of patches overall and the largest number of critical-severity patches so far
Sophos protections
This table will be updated as individual signatures are finalized.
| CVE | Sophos Intercept X/Endpoint IPS | Sophos XGS Firewall |
| CVE-2023-24902 | Exp/2324902-A | |
| CVE-2023-24941 | 2308380 | 2308380 |
| CVE-2023-24950 | 2308385 | 2308385 |
| CVE-2023-29325 | 2308384 | 2308384 |
As you can every month, if you don’t want to wait for your system to pull down Microsoft’s updates itself, you can download them manually from the Windows Update Catalog website. Run the winver.exe tool to determine which build of Windows 10 or 11 you’re running, then download the Cumulative Update package for your specific system’s architecture and build number.
Appendix A: Vulnerability Impact and Severity
This is a list of May’s patches sorted by impact, then sub-sorted by severity. Each list is further arranged by CVE.
Remote Code Execution (12 CVEs)
| Critical severity | |
| CVE-2023-24903 | Windows Secure Socket Tunneling Protocol (SSTP) Remote Code Execution Vulnerability |
| CVE-2023-24941 | Windows Network File System Remote Code Execution Vulnerability |
| CVE-2023-24943 | Windows Pragmatic General Multicast (PGM) Remote Code Execution Vulnerability |
| CVE-2023-24955 | Microsoft SharePoint Server Remote Code Execution Vulnerability |
| CVE-2023-28283 | Windows Lightweight Directory Access Protocol (LDAP) Remote Code Execution Vulnerability |
| CVE-2023-29325 | Windows OLE Remote Code Execution Vulnerability |
| Important severity | |
| CVE-2023-24905 | Remote Desktop Client Remote Code Execution Vulnerability |
| CVE-2023-24947 | Windows Bluetooth Driver Remote Code Execution Vulnerability |
| CVE-2023-24953 | Microsoft Excel Remote Code Execution Vulnerability |
| CVE-2023-29340 | AV1 Video Extension Remote Code Execution Vulnerability |
| CVE-2023-29341 | AV1 Video Extension Remote Code Execution Vulnerability |
| CVE-2023-29344 | Microsoft Office Remote Code Execution Vulnerability |
Elevation of Privilege (10 CVEs)
| Critical severity | |
| CVE-2023-29324 | Windows MSHTML Platform Elevation of Privilege Vulnerability |
| Important severity | |
| CVE-2023-24899 | Windows Graphics Component Elevation of Privilege Vulnerability |
| CVE-2023-24902 | Win32k Elevation of Privilege Vulnerability |
| CVE-2023-24904 | Windows Installer Elevation of Privilege Vulnerability |
| CVE-2023-24946 | Windows Backup Service Elevation of Privilege Vulnerability |
| CVE-2023-24948 | Windows Bluetooth Driver Elevation of Privilege Vulnerability |
| CVE-2023-24949 | Windows Kernel Elevation of Privilege Vulnerability |
| CVE-2023-24950 | Microsoft SharePoint Server Elevation of Privilege Vulnerability |
| CVE-2023-29336 | Win32k Elevation of Privilege Vulnerability |
| CVE-2023-29343 | SysInternals Sysmon for Windows Elevation of Privilege Vulnerability |
Information Disclosure (8 CVEs)
| Important severity | |
| CVE-2023-24881 | Microsoft Teams Information Disclosure Vulnerability |
| CVE-2023-24900 | Windows NTLM Security Support Provider Information Disclosure Vulnerability |
| CVE-2023-24901 | Windows NFS Portmapper Information Disclosure Vulnerability |
| CVE-2023-24944 | Windows Bluetooth Driver Information Disclosure Vulnerability |
| CVE-2023-24945 | Windows iSCSI Target Service Information Disclosure Vulnerability |
| CVE-2023-24954 | Microsoft SharePoint Server Information Disclosure Vulnerability |
| CVE-2023-28290 | Remote Desktop Protocol Client Information Disclosure Vulnerability |
| CVE-2023-29338 | Visual Studio Code Information Disclosure Vulnerability |
Denial of Service (5 CVEs)
| Important severity | |
| CVE-2023-24898 | Windows SMB Denial of Service Vulnerability |
| CVE-2023-24939 | Server for NFS Denial of Service Vulnerability |
| CVE-2023-24940 | Windows Pragmatic General Multicast (PGM) Denial of Service Vulnerability |
| CVE-2023-24942 | Remote Procedure Call Runtime Denial of Service Vulnerability |
| CVE-2023-29333 | Microsoft Access Denial of Service Vulnerability |
Security Feature Bypass (3 CVEs)
| Important severity | |
| CVE-2023-24932 | Secure Boot Security Feature Bypass Vulnerability |
| CVE-2023-28251 | Windows Driver Revocation List Security Feature Bypass Vulnerability |
| CVE-2023-29335 | Microsoft Word Security Feature Bypass Vulnerability |
Appendix B: Exploitability
This is a list of the May CVEs judged by Microsoft to be more likely to be exploited in the wild within the first 30 days post-release, as well as those already known to be under exploit. Each list is further arranged by CVE.
| Exploit detected | |
| CVE-2023-29336 | Win32k Elevation of Privilege Vulnerability |
| Exploitation more likely | |
| CVE-2023-24902 | Win32k Elevation of Privilege Vulnerability |
| CVE-2023-24941 | Windows Network File System Remote Code Execution Vulnerability |
| CVE-2023-24949 | Windows Kernel Elevation of Privilege Vulnerability |
| CVE-2023-24950 | Microsoft SharePoint Server Elevation of Privilege Vulnerability |
| CVE-2023-24954 | Microsoft SharePoint Server Information Disclosure Vulnerability |
| CVE-2023-24955 | Microsoft SharePoint Server Remote Code Execution Vulnerability |
| CVE-2023-29324 | Windows MSHTML Platform Elevation of Privilege Vulnerability |
Appendix C: Products Affected
This is a list of May’s patches sorted by product family, then sub-sorted by severity. Each list is further arranged by CVE.
Windows (27 CVEs)
| Critical severity | |
| CVE-2023-24903 | Windows Secure Socket Tunneling Protocol (SSTP) Remote Code Execution Vulnerability |
| CVE-2023-24941 | Windows Network File System Remote Code Execution Vulnerability |
| CVE-2023-24943 | Windows Pragmatic General Multicast (PGM) Remote Code Execution Vulnerability |
| CVE-2023-28283 | Windows Lightweight Directory Access Protocol (LDAP) Remote Code Execution Vulnerability |
| CVE-2023-29324 | Windows MSHTML Platform Elevation of Privilege Vulnerability |
| CVE-2023-29325 | Windows OLE Remote Code Execution Vulnerability |
| Important severity | |
| CVE-2023-24898 | Windows SMB Denial of Service Vulnerability |
| CVE-2023-24899 | Windows Graphics Component Elevation of Privilege Vulnerability |
| CVE-2023-24900 | Windows NTLM Security Support Provider Information Disclosure Vulnerability |
| CVE-2023-24901 | Windows NFS Portmapper Information Disclosure Vulnerability |
| CVE-2023-24902 | Win32k Elevation of Privilege Vulnerability |
| CVE-2023-24904 | Windows Installer Elevation of Privilege Vulnerability |
| CVE-2023-24905 | Remote Desktop Client Remote Code Execution Vulnerability |
| CVE-2023-24932 | Secure Boot Security Feature Bypass Vulnerability |
| CVE-2023-24939 | Server for NFS Denial of Service Vulnerability |
| CVE-2023-24940 | Windows Pragmatic General Multicast (PGM) Denial of Service Vulnerability |
| CVE-2023-24942 | Remote Procedure Call Runtime Denial of Service Vulnerability |
| CVE-2023-24944 | Windows Bluetooth Driver Information Disclosure Vulnerability |
| CVE-2023-24945 | Windows iSCSI Target Service Information Disclosure Vulnerability |
| CVE-2023-24946 | Windows Backup Service Elevation of Privilege Vulnerability |
| CVE-2023-24947 | Windows Bluetooth Driver Remote Code Execution Vulnerability |
| CVE-2023-24948 | Windows Bluetooth Driver Elevation of Privilege Vulnerability |
| CVE-2023-24949 | Windows Kernel Elevation of Privilege Vulnerability |
| CVE-2023-28251 | Windows Driver Revocation List Security Feature Bypass Vulnerability |
| CVE-2023-28290 | Remote Desktop Protocol Client Information Disclosure Vulnerability |
| CVE-2023-29336 | Win32k Elevation of Privilege Vulnerability |
| CVE-2023-29343 | SysInternals Sysmon for Windows Elevation of Privilege Vulnerability |
Office (4 CVEs)
| Important severity | |
| CVE-2023-24953 | Microsoft Excel Remote Code Execution Vulnerability |
| CVE-2023-29333 | Microsoft Access Denial of Service Vulnerability |
| CVE-2023-29335 | Microsoft Word Security Feature Bypass Vulnerability |
| CVE-2023-29344 | Microsoft Office Remote Code Execution Vulnerability |
SharePoint (3 CVEs)
| Critical severity | |
| CVE-2023-24955 | Microsoft SharePoint Server Remote Code Execution Vulnerability |
| Important severity | |
| CVE-2023-24950 | Microsoft SharePoint Server Elevation of Privilege Vulnerability |
| CVE-2023-24954 | Microsoft SharePoint Server Information Disclosure Vulnerability |
AV1 (2 CVEs)
| Important severity | |
| CVE-2023-29340 | AV1 Video Extension Remote Code Execution Vulnerability |
| CVE-2023-29341 | AV1 Video Extension Remote Code Execution Vulnerability |
Teams (one CVE)
| Important severity | |
| CVE-2023-24881 | Microsoft Teams Information Disclosure Vulnerability |
Visual Studio (one CVE)
| Important severity | |
| CVE-2023-29338 | Visual Studio Code Information Disclosure Vulnerability |

Leave a Reply