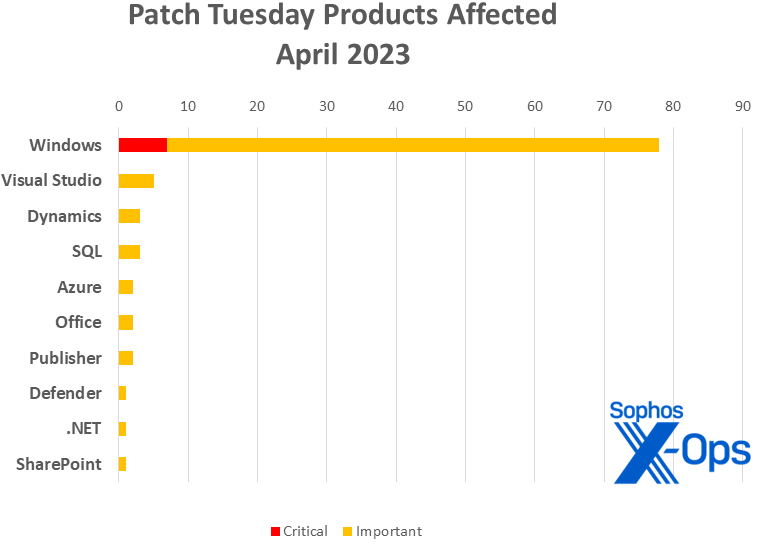
Microsoft on Tuesday released patches for 97 vulnerabilities in ten product families, including 7 Critical-severity issues in Windows. As is the custom, the largest number of addressed vulnerabilities affect Windows, with 77 CVEs. Visual Studio follows with 5 CVEs; followed by Dynamics and SQL (3 each); Azure, Office, and Publisher (2 each); and Defender, .NET (counted separately from the Visual Studio patches), and SharePoint (one each).
At patch time, none of the issues this month has been publicly disclosed, and only one appears to be under exploit in the wild: CVE-2023-28252, an Important-severity elevation-of-privilege issue in Windows’ Common Log File system driver. However, Microsoft cautions that ten of the Windows CVEs addressed are more likely to be exploited in the affected product soon (that is, within the next 30 days). Interestingly, eight of the ten flagged issues apply only to the latest version of Windows, not to earlier versions.
Two of those Windows issues also have a 9.8 CVSS base score (and an 8.5 temporal score), signaling to network administrators that they are worth prioritizing. CVE-2023-28231 (DHCP Server Service Remote Code Execution Vulnerability) and CVE-2023-21554 (Microsoft Message Queuing Remote Code Execution Vulnerability) are both Critical-severity RCEs submitted to Microsoft by external security researchers, and both are flagged by Microsoft as more likely to be exploited within the next 30 days. Another Critical-severity messaging issue, CVE-2023-28250 (Windows Pragmatic General Multicast [PGM] Remote Code Execution Vulnerability), also received a 9.8 CVSS score this month, though Microsoft considers exploitation of this issue less likely in the next 30 days.
It’s not a light patch load, but observers may find cheer in an interesting statistic: Our year-over-year numbers indicate that Microsoft is confronting far fewer elevation-of-privilege issues so far this year. As of today, Microsoft has patched 87 EoP issues; at this point last year, they’d patched 125. (Overall year-to-year patch tallies are about even – 359 patches in the first four months of 2022, 340 this year – with notable year-to-year increases in patches addressing spoofing or information-disclosure issues.)
By the numbers
- Total Microsoft CVEs: 97
- Total advisories shipping in update: 0
- Publicly disclosed: 0
- Exploited: 1
- Exploitation more likely in latest version: 9
- Exploitation more likely in older versions: 1
- Severity
- Critical: 7
- Important: 90
- Impact
- Remote code execution: 45
- Elevation of privilege: 20
- Information disclosure: 10
- Denial of service: 9
- Security feature bypass: 7
- Spoofing: 6
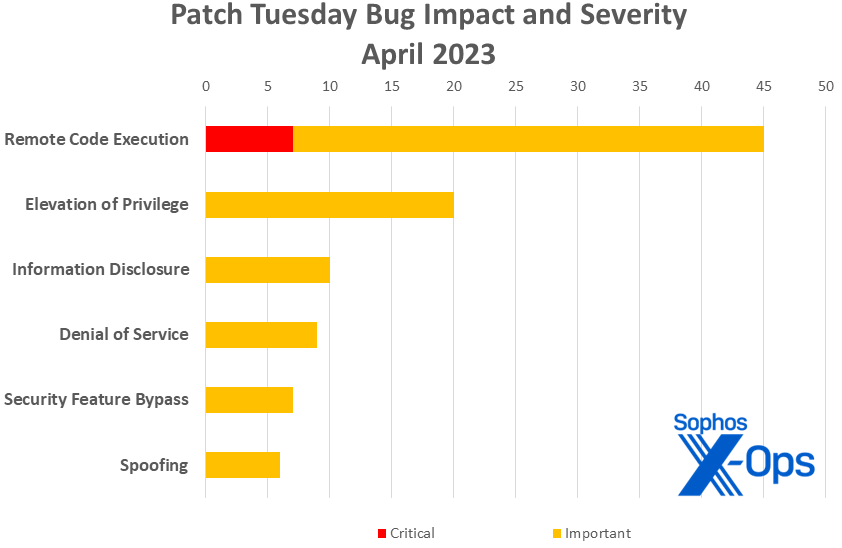 Figure 1: Remote code execution issues continue to dominate 2023’s Patch Tuesdays
Figure 1: Remote code execution issues continue to dominate 2023’s Patch TuesdaysProducts
- Windows: 77
- Visual Studio: 5 (excluding .NET; see below)
- Dynamics: 3
- SQL: 3
- Azure: 2
- Office: 2
- Publisher: 2
- Defender: 1
- .NET: 1 (excluding Visual Studio; see above)
- SharePoint: 1
Figure 2: Windows accounts for just under 80 percent of the patches released this month, and all of the Critical-severity issues.
Microsoft also makes mention in the April release of three Edge-related patches released separately, two applying only to Edge for Android; those patches are not reflected in this month’s totals. Microsoft also issued information on 15 patches released today by Adobe in support of their Adobe Reader product. None of the 15 are under active exploit in the wild.
Other notable April updates
CVE-2023-28219 and CVE-2023-28220, both titled Layer 2 Tunneling Protocol Remote Code Execution Vulnerability
Both updates address Critical-severity RCE issues with Microsoft’s Layer 2 Tunnelling Protocol (L2TP), which supports VPNs and other crucial functions. In both cases, an attacker sending a specially crafted connection request to an RAS server could achieve RCE on the target machine. In both cases they’d have to win a race condition to successfully take advantage, but since Microsoft’s asserting that these two are more likely than not to be successfully exploited within the next 30 days, network administrators should take them seriously. However, Microsoft states that both bugs are less likely to be exploited on older versions of Windows, though the patch is available for all currently supported versions of the OS.
CVE-2023-28249 and CVE-2023-28269, both titled Windows Boot Manager Security Feature Bypass Vulnerability
A pair of physical-layer issues -– in other words, if the attacker has admin privileges or physical access to a targeted machine, they can get around Secure Boot. This is possibly uninteresting in most situations, but could be very exciting indeed if, for instance, an executive’s stolen laptop ended up in clever hands.
CVE-2023-24883, CVE-2023-28243, CVE-2023-24929, CVE-2023-24928, CVE-2023-24927, CVE-2023-24926, CVE-2023-24925, CVE-2023-24924, CVE-2023-24887, CVE-2023-24886, CVE-2023-24885, and CVE-2023-24884, various titles
Independent researcher kap0k’s scrutiny of PostScript and PCL6-class printer drivers continues to bear fruit, with another 12 patches to their credit this month. These are apparently non-trivial finds, too; all are RCE, and all but one weigh in with a CVSS base score of 8.8.
Figure 3: April continued the 2023 trend toward a slowdown in Microsoft patches addressing elevation-of-privilege issues. By Patch Tuesday in April 2022, Microsoft had issued 125 EoP patches, as opposed to just 87 so far in 2023. (Remote code execution vulnerabilities are almost exactly keeping 2022’s pace – 133 as of April 2022, 137 as of April 2023.)
Sophos protections
CVE Sophos Intercept X/Endpoint IPS Sophos XGS Firewall CVE-2023-21554 2308319 2308319 CVE-2023-24912 Exp/2324912-A CVE-2023-28218 Exp/2328218-A CVE-2023-28231 2308321 2308321 CVE-2023-28266 Exp/2328266-A As you can every month, if you don’t want to wait for your system to pull down Microsoft’s updates itself, you can download them manually from the Windows Update Catalog website. Run the winver.exe tool to determine which build of Windows 10 or 11 you’re running, then download the Cumulative Update package for your specific system’s architecture and build number.


Leave a Reply