Microsoft on Tuesday released patches for 75 vulnerabilities in 12 Microsoft product families, including eight Critical-severity issues in the Protected Extensible Authentication Protocol (PEAP), the iSCSI Discovery Service, Office, and .NET and Visual Studio. As in previous months, the lion’s share of the vulnerabilities affect Windows, with 32 fixes. Microsoft Dynamics 365 and .NET and Visual Studio have the next-largest collections, with six; followed by Office and Azure at five apiece.
The remainder are spread out among a variety of product families, including Power BI, PostScript, OLE DB, MSSQL, and ODBC. 3D Builder also features again this month, although to a lesser extent: two remote code execution bugs this time, following on from January’s 14.
However, none of the issues this month have been publicly disclosed, although three appear to have been exploited in the wild: CVE-2023-21715, an Important-grade Security Feature Bypass in Microsoft Office; CVE-2023-21823, an Important-grade Elevation of Privilege vulnerability in the Windows Graphic Component; and CVE-2023-23376, which is also an Important-grade Elevation of Privilege bug, this time in the Windows Common Log File System Driver.
By the numbers
- Total Microsoft CVEs: 75
- Total advisories shipping in update: 0
- Publicly disclosed: 0
- Exploited: 3
- Exploitation more likely in latest version: 11
- Exploitation more likely in older versions: 3
- Severity
- Critical: 8
- Important: 67
- Impact
- Remote Code Execution: 35
- Elevation of Privilege: 12
- Denial of Service: 10
- Information Disclosure: 8
- Spoofing: 8
- Security Feature Bypass: 2
Products
- Windows: 32
- .NET and Visual Studio: 6
- Dynamics: 6
- Office: 5
- Azure: 5
- ODBC: 4
- MSSQL: 4
- Exchange: 4
- PostScript: 3
- OLE DB: 3
- Defender: 2
- Power BI: 1
Notable February updates
CVE-2023-21689; CVE-2023-21690; and CVE-2023-21692: Microsoft Protected Extensible Authentication Protocol (PEAP) Remote Code Execution Vulnerabilities
Among the five PEAP-related vulnerabilities in this month’s release are three Critical-severity remote code execution vulnerabilities, all with a CVSS BaseScore of 9.8. Exploiting CVE-2023-21690 and CVE-2023-21692 would entail crafting malicious PEAP packets and sending them to a targeted server. For all three bugs, the attack complexity is low, and no privileges or user interaction are required.
CVE-2023-21808; CVE-2023-21815; and CVE-2023-23381 .NET and Visual Studio/Visual Studio Remote Code Execution Vulnerabilities
All three of these issues are Critical-severity bugs with low attack complexity, and they require no privileges or user interaction for exploitation. While the issue is categorized as Remote Code Execution, the attack itself is carried out locally. All three have a CVSS BaseScore of 8.4.
CVE-2023-21716: Microsoft Word Remote Code Execution Vulnerability
Another Critical-severity Remote Code Execution vulnerability, CVE-2023-21716 has a CVSS BaseScore of 9.8, with low attack complexity and no authentication required. To exploit this bug, an attacker could send a malicious email containing an RTF payload. The Preview Pane is an attack vector, suggesting that little or no user interaction would be required for successful exploitation. However, Microsoft rate exploitation as less likely to occur for this vulnerability. Microsoft advise that the Microsoft Office File Block policy is a workaround for this issue and will prevent Office from opening RTF documents from unknown or untrusted sources. For example, in Office 2016, this would involve setting the RtfFiles DWORD value to 2 and the OpenInProtectedView DWORD value to 0 in the subkey: HKEY_CURRENT_USER\Software\Microsoft\Office\16.0\Word\Security\FileBlock. However, users should bear in mind that directly editing the Registry comes with risks.
CVE-2023-21809: Microsoft Defender for Endpoint Security Feature Bypass Vulnerability
A vulnerability which may be particularly attractive to threat actors, CVE-2023-21809 is an Important-rated Security Feature Bypass vulnerability. If successfully exploited, an attacker may be able to bypass the Windows Defender Attack Surface Reduction (ASR) blocking feature. However, to exploit it, an attacker would need to trick a user into running malicious files.
Sophos protections
| CVE | Sophos Intercept X/Endpoint IPS | Sophos XGS Firewall |
| CVE-2023-21812 | Exp/2321812-A | |
| CVE-2023-21823 | Exp/2321823-A | |
| CVE-2023-23376 | Exp/2323376-A | |
| CVE-2023-21690 | 2308097 | 2308097 |
| CVE-2023-21706 | 2308105 | 2308105 |
| CVE-2023-21689 | 2308096 | 2308096 |
| CVE-2023-21819 | 2308084 | 2308084 |
| CVE-2023-21529 | 2307771 | 2307771 |
As you can every month, if you don’t want to wait for your system to pull down Microsoft’s updates itself, you can download them manually from the Windows Update Catalog website. Run the winver.exe tool to determine which build of Windows 10 or 11 you’re running, then download the Cumulative Update package for your particular system’s architecture and build number.

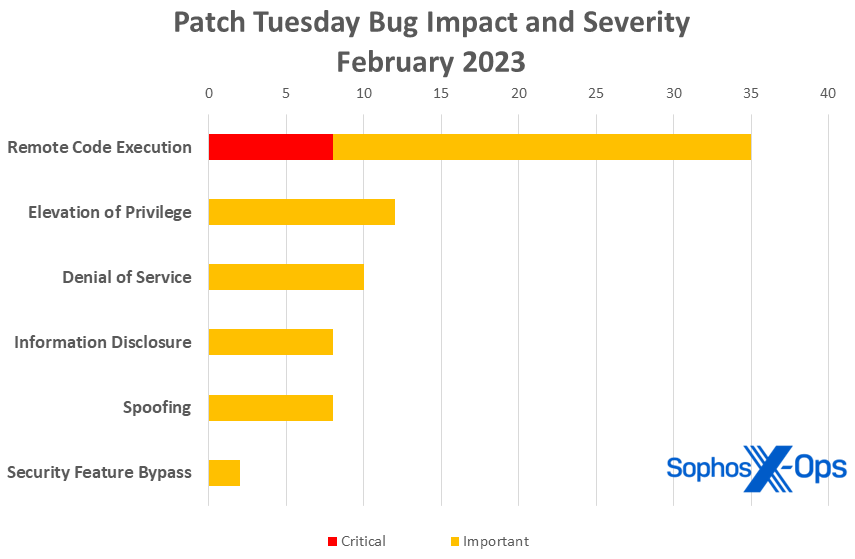 Figure 1: Remote code execution vulnerabilities have a big outing in February, accounting for nearly half of all February patches
Figure 1: Remote code execution vulnerabilities have a big outing in February, accounting for nearly half of all February patches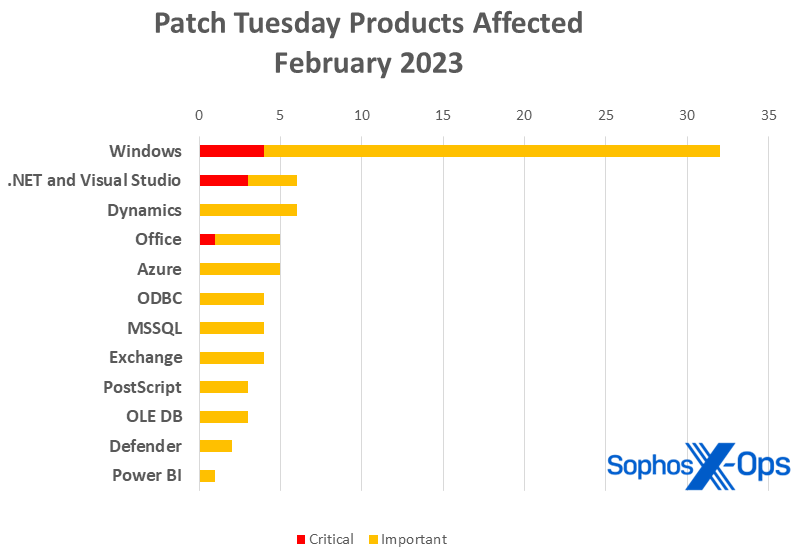 Figure 2: February’s patch set is unusually diverse, with twelve product families represented, but Windows still rules the roost
Figure 2: February’s patch set is unusually diverse, with twelve product families represented, but Windows still rules the roost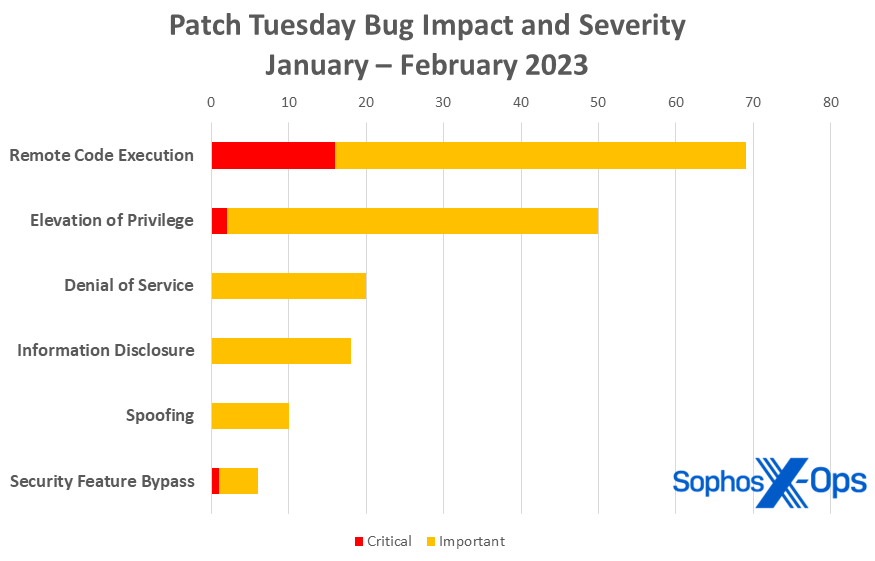 Figure 3: RCE issues account for a third of all 2023 Microsoft patches so far, with elevation of privileges issues addressed in another quarter of the patches released
Figure 3: RCE issues account for a third of all 2023 Microsoft patches so far, with elevation of privileges issues addressed in another quarter of the patches released
Mirek S.
Microsoft on its website provide only 72 CVE numbers. What are those another 3?
Thank you.
Angela Gunn
Hi Mirek — I believe you’re referring to CVE-2023-21794, CVE-2023-21720, and CVE-2023-23374 — those “extra” three CVEs were related to Chromium, and according to Microsoft’s information all three received their CVE numbers from MITRE itself. Microsoft included information on those three strictly for the sake of completeness, since they don’t require any action on anyone’s part.