A scam lurks around every corner on criminal marketplaces. Way back in 2009, Microsoft pointed out that the underground economy was rife with dishonesty, and in 2017, Digital Shadows reported on a database of ‘rippers’ (fraudsters who con criminals) created by marketplace users. In our recent coverage of Genesis Market, we noted at least one scammy imitation of Genesis, designed to separate naïve would-be cybercriminals (and possibly inexperienced security researchers and journalists) from their money.
But generally, the topic hasn’t received much attention. After all, why should it? If scammers target criminals, so much the better, right? At least they’re attacking each other, not organizations or the general public.
We thought there might be more to it, so we spent a few weeks digging into scammers who scam scammers on three prominent cybercrime forums – research we don’t think has been done before. And we found five surprising things.
1. It’s big business – a sub-economy in itself. In the last 12 months, cybercriminals have lost over $2.5 million USD to scams, just on those three forums. In fact, it’s such a long-standing and prominent problem that forum administrators have created dedicated ‘arbitration rooms’ for users to report scams, attacks, and rippers.
2. Money isn’t the only motive, and it’s not just lower-tier threat actors involved. Personal beefs, rivalries, and wanting to destroy (or sometimes enhance) reputations can all result in scams. And it’s not just small-time crooks. We saw prominent threat actors either accused of scamming or falling victim to scams themselves.
3. The attacks go beyond the usual ‘rip-and-run.’ We saw referral cons, fake data leaks and tools, typosquatting, phishing, ‘alt rep’ scams (the use of sockpuppets to artificially inflate reputation scores), fake guarantors, blackmail, impersonated accounts, and backdoored malware. We even found instances where threat actors got revenge by scamming the scammers who scammed them.
4. We found examples of long-term, large-scale fraud. One of the biggest surprises came when we dug into that imitation Genesis site. With some detective work, we uncovered nineteen other sites all created by the same person or group, all imitating criminal marketplaces, and all intended to trick users into forking over a $100 ‘activation fee.’ We don’t know for sure who’s behind all those sites, but we discovered tentative links to a drug vendor who operates on several dark web sites.
So far, so schadenfreude – but the big question is still: who cares? Why does it matter if criminals attack each other? This is where things get really fascinating.
5. Scam reports are a rich, and underexplored, source of intelligence. Threat actors are aware that criminal forums are monitored, and so often employ good operational security. When they’re victims of crime themselves – well, not so much. Because forum rules demand proof to support scam allegations, wronged threat actors will often happily post screenshots of private conversations and source code, identifiers, transactions, chat logs, and blow-by-blow accounts of negotiations, sales, and troubleshooting.
This hidden sub-economy isn’t just a curiosity. It gives us insights into forum culture; how threat actors buy and sell; their tactical and strategic priorities; their rivals and alliances; their susceptibility to deception – and specific, discrete intelligence about them.
Over the next few weeks, we’ll share the findings of our extended investigation into this topic – starting with an overview of the forums involved, how they deal with scams, who’s scamming who, and the size of the sub-economy.
You can also check out our Black Hat talk on this research.
Welcome to the jungle
To kick off our investigation, we examined scams on two of the oldest and most prominent Russian-language cybercrime forums, Exploit and XSS. We also included scams from BreachForums, the successor to RaidForums, which launched in April 2022.
The forums
Exploit is relatively exclusive, and is a popular marketplace for Access-as-a-Service (AaaS) listings, where initial access brokers (IABs) sell access to compromised networks. But threat actors buy and sell a lot of other illicit content there too – malware, data leaks, infostealer logs, credentials, and more. Historically, ransomware groups and affiliates frequented Exploit, although that became more covert after the Colonial Pipeline attack in 2021, when both Exploit and XSS publicly banned ransomware discussion to avoid negative attention. Nowadays, ransomware affiliate recruitment continues on both forums, although it tends to be under the cover of euphemisms like ‘pentesters.’
XSS, formerly known as DaMaGeLaBs, is also well-established, although membership is less exclusive than Exploit. It also hosts a lot of AaaS listings and various other content.
Finally, BreachForums is the successor to RaidForums, a marketplace that ran for seven years before it was seized by law enforcement earlier in 2022. Like RaidForums, BreachForums is an English-language cybercrime forum and marketplace specializing in data leaks, including personal data, credit cards, credentials, and identity documents.
All three sites have dedicated arbitration rooms – Exploit (with approximately 2500 reported scams) and XSS (with around 760) have had them since the mid-2000s, and BreachForums since its creation in April 2022. Other criminal marketplaces, such as Verified, have them too.
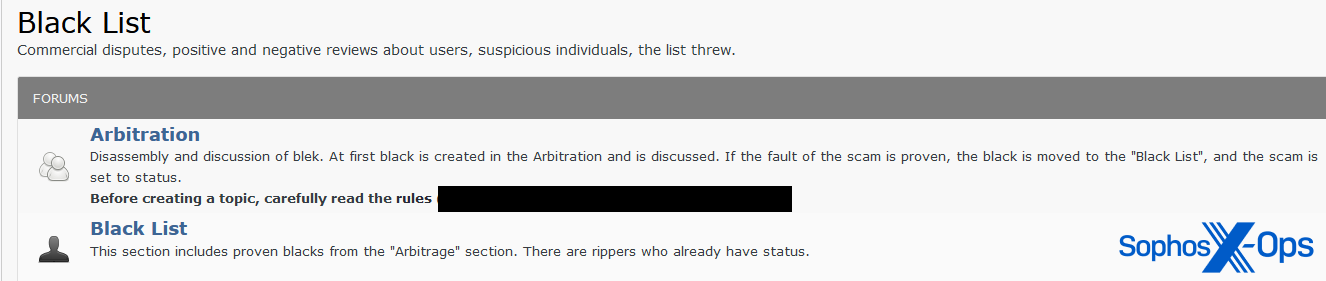
In fact, Exploit has two rooms – one for open claims, and another, called the ‘Black List,’ which documents confirmed scam cases.
Figure 1: Exploit’s arbitration section
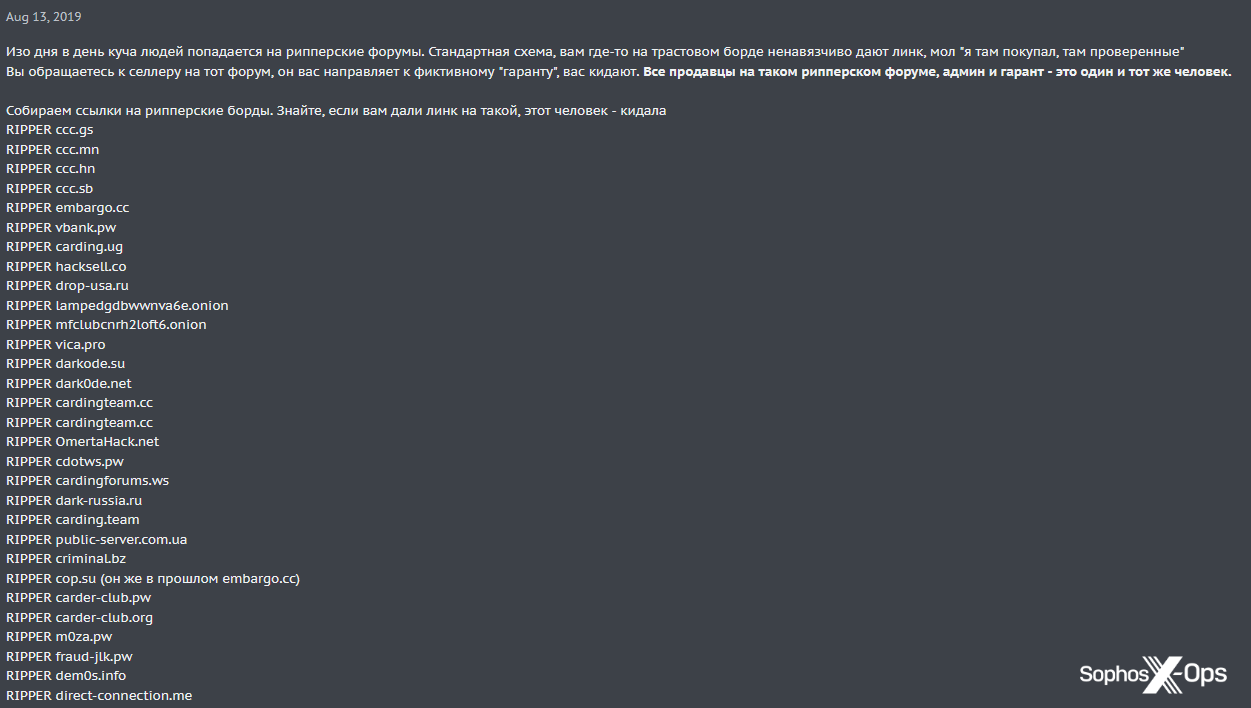
In addition to a dedicated arbitration room, XSS also maintains a long ‘ripper list,’ an index of scam sites.
Figure 2: XSS’s ripper list
An overview of scam statistics
We looked at all scam reports citing monetary amounts in the last 12 months. (With BreachForums we went back to the first recorded scam, as the forum hasn’t been around that long.)
| Exploit (open claims) | Exploit (‘Black List’) | XSS | BreachForums | |
| Claims | 211 | 236 | 120 | 21 |
| Total amount | $1,021,998 | $863,324 | $509,901 | $143,722 |
| Mean | $4,843.54 | $3,658 | $4,249.18 | $6,843.90 |
| Mode | $1000 | $500 | $150 | $500 |
| Median | $600 | $500 | $500 | $200 |
| Range | $15 – $160,000 | $5 – $150,000 | $10 – $160,000 | $2 – $134,000 |
Table 1: A summary of 12 months of scam reports (all amounts in USD)
While this is only a snapshot, it does give us some useful insights. First, the total amount lost to scams (and remember, this only involves scam reports which mention specific amounts – some don’t) is $2,538,945. That’s a significant amount, bearing in mind it’s on just three forums.
Second, Exploit is the worst for scams, both in terms of numbers of reports and money lost to scammers. It does have around twice as many members as XSS, and may also attract more scammers because of its reputation.
Third, the mean average amount reported as stolen is similar across all three forums, as is the range – which suggests that the scale of scams is consistent regardless of the forum.
Victims have filed scam reports for as little as $2; threat actors seem to be as indignant about having their money stolen as anyone else, no matter the amount.
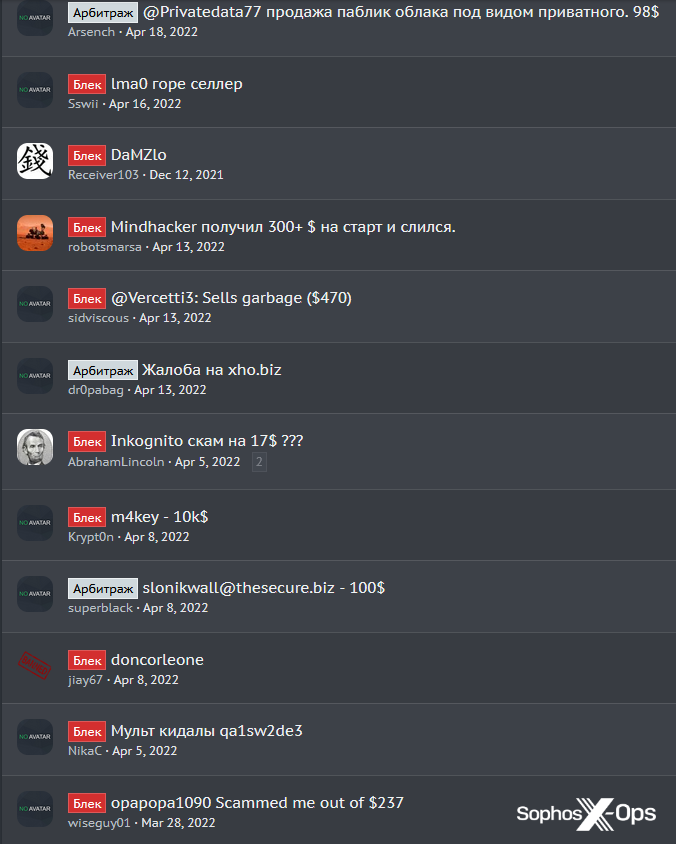
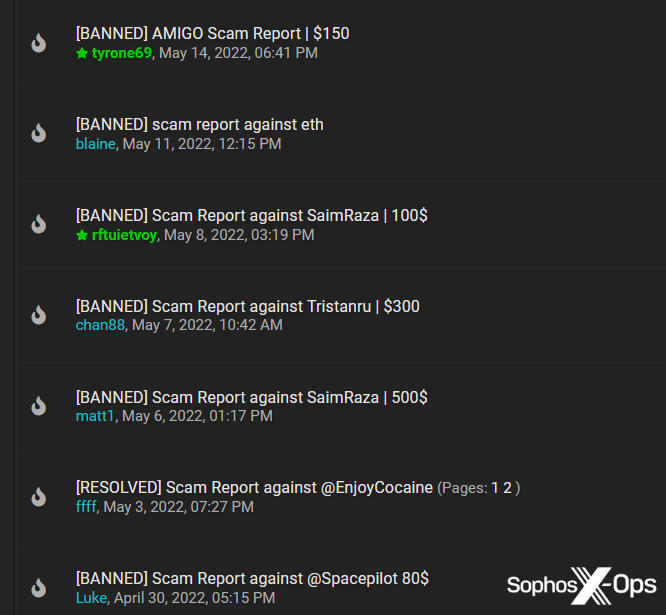
At the higher end, scams on all three marketplaces go into six figures, although these are the exceptions. Many scams net relatively insignificant amounts.
Figure 3: Low claim amounts in the XSS arbitration room
Figure 4: Low claim amounts in the BreachForums arbitration room
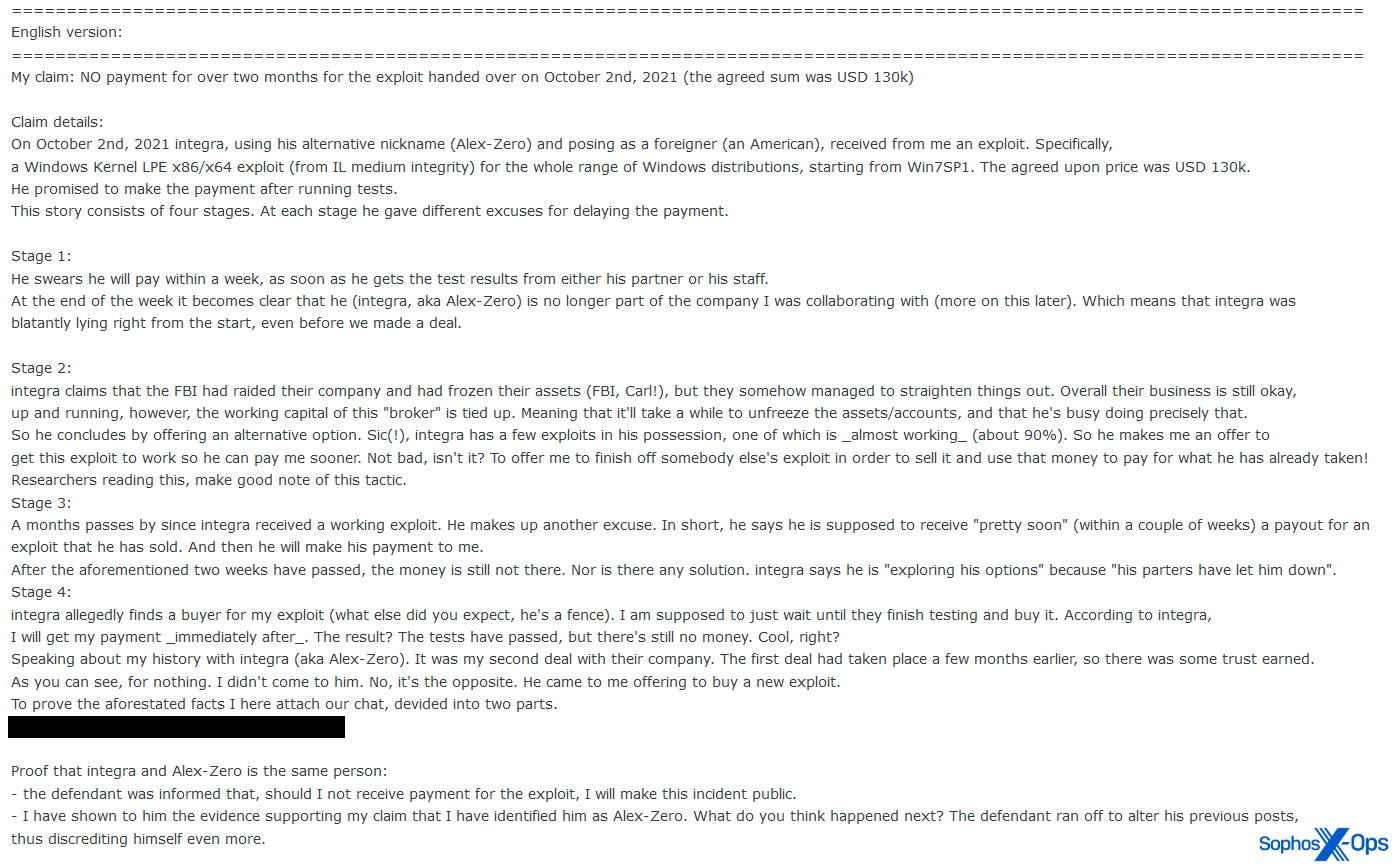
Figure 5: An example of a larger scam claim on Exploit ($130,000). Note the amount of detail in this scam claim, which includes information about negotiations and projects
Before we examine the arbitration process, it’s worth looking at why scams are so prevalent. Back in 2009, Microsoft argued that the underground cybercrime economy was not an “easy money criminal Utopia” but a “lemon market,” in which the presence of rippers effectively introduced a tax on every transaction.
While times have changed, and cybercrime is more commoditized than it was, criminal marketplaces are still the perfect breeding ground for scammers and rippers. There’s no recourse to law enforcement; it’s a (semi) anonymous culture which emphasizes privacy; sites are exclusive enough that there’s at least a degree of implicit trust; they’re populated by criminals, who are arguably unlikely to consider themselves potential victims and may therefore be less wary of scams; it’s an open market with no regulation or quality assurance; transactions are conducted with cryptocurrencies, which can be made effectively untraceable; and safeguards such as guarantors are optional (and, as we’ll see in the next part of our series, can themselves be weaponized in the service of scams).
What are criminal marketplaces doing about scams?
The administrators of criminal forums are well aware that scams are a problem. In addition to arbitration rooms, most marketplaces have visible warnings about scammers, and advocate using guarantors (sometimes called ‘middlemen’ or ‘middles’) during sales – a form of escrow.
Figure 6: A warning about scams on the front page of BreachForums
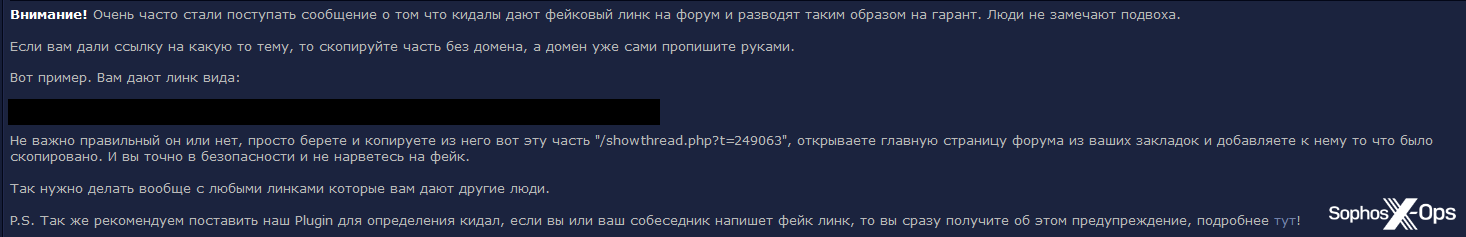
Other forums go further. Verified, for example, explicitly warns users about fake links to its forum, and advocates using a custom plugin to detect such scams:
Figure 7: Verified’s scam warning
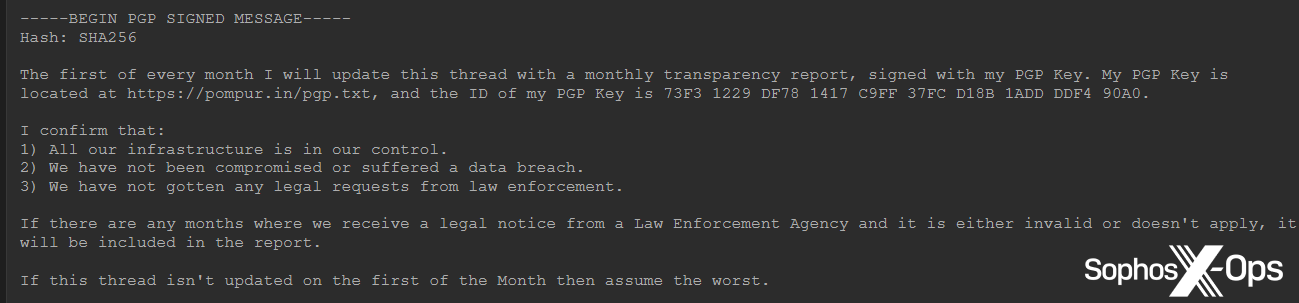
In a similar vein, BreachForums publishes a list of all its legitimate domains, as well as a monthly ‘transparency report’, to confirm that the site and related infrastructure remain under its control and have not been compromised (although this is probably also a precautionary measure because of what happened to RaidForums):
Figure 8: Details about BreachForums’ monthly transparency report
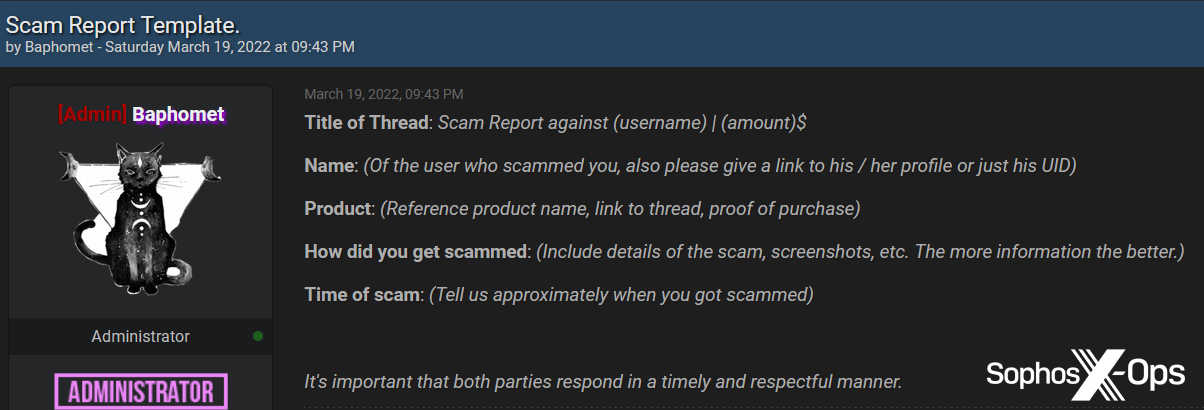
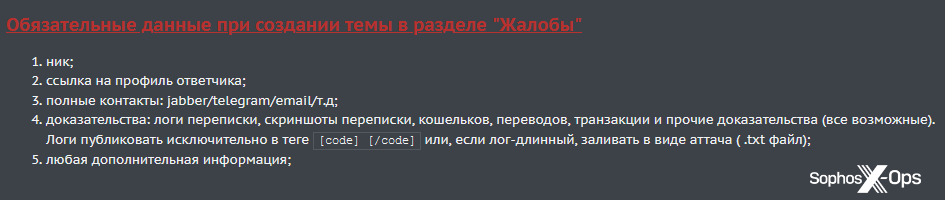
But arbitration rooms are the main method for dealing with scams. The process is relatively simple. Users who wish to report a scam must create a new thread, call out the user who allegedly scammed them, and provide as much detail as possible about the incident. BreachForums provides a template for this, whereas XSS simply lists the details needed.
Figure 9: The BreachForums scam report template
Figure 10: The data required in XSS scam reports: nick, link to profile, contact details, evidence (chat logs, screenshots, wallets, transfers), any additional information
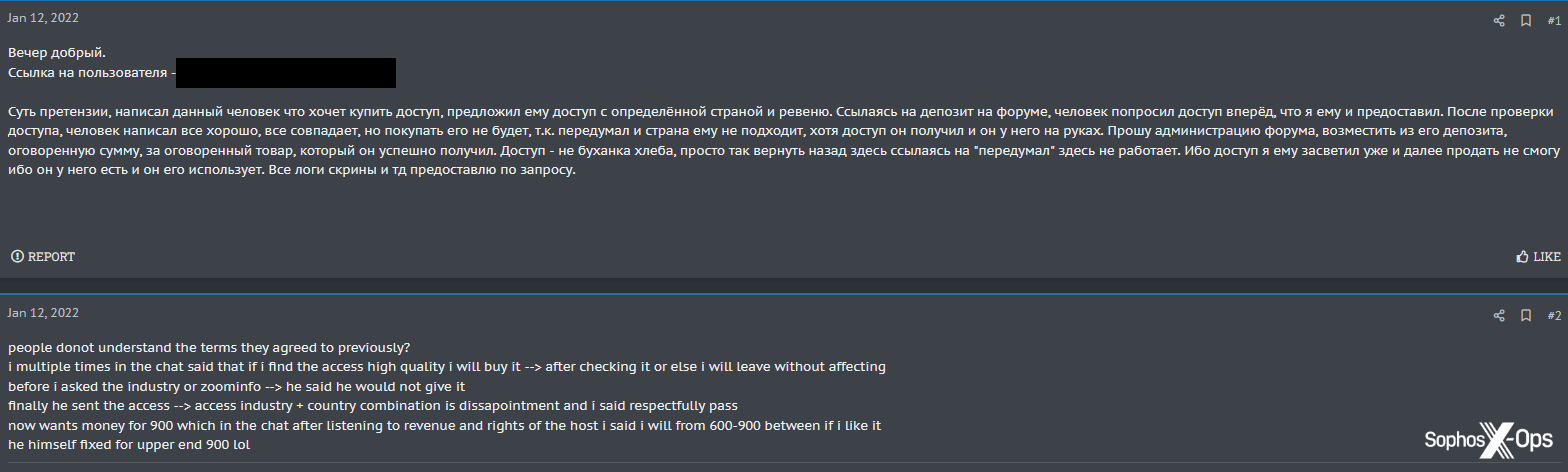
A moderator then reviews the report, asks for more information if needed, and tags the accused, giving them a deadline by which to respond (commonly 24 hours, but can be between 12 and 72 hours).
Figure 11: An Exploit moderator gives an accused scammer 24 hours to respond to an allegation
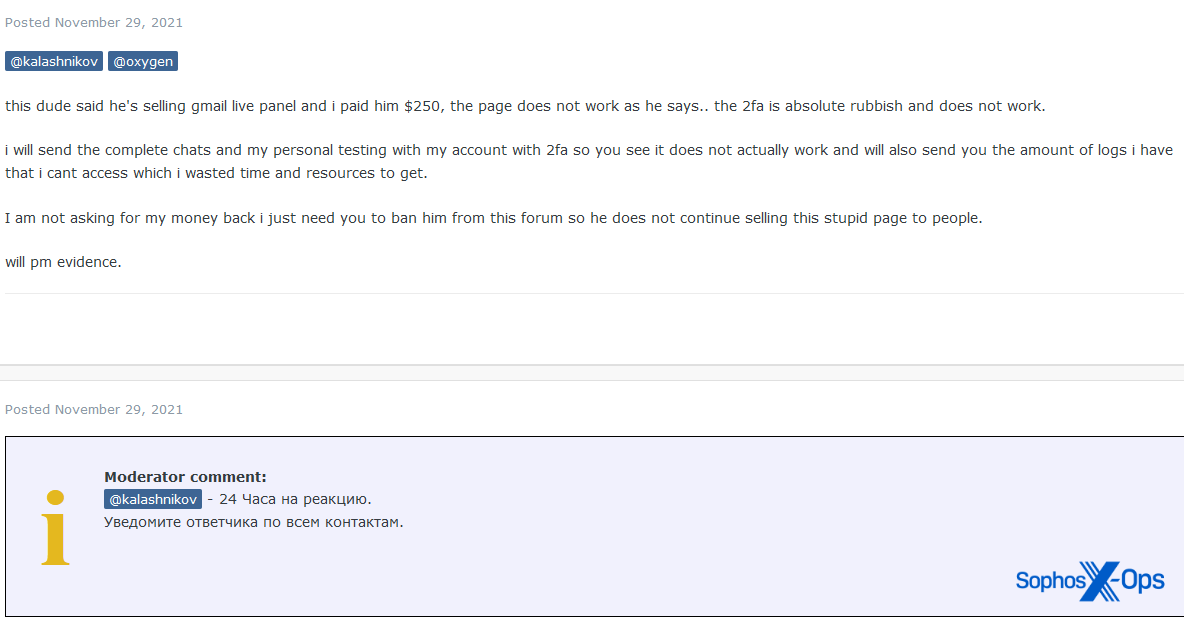
The accused may accept the claim, in which case they make restitution to the victim. This is rare. More commonly, the accused disputes the claim (in which case the moderator arbitrates) or doesn’t respond at all (in which case they may be temporarily or permanently banned from the forum).
Figure 12: A disputed claim on XSS relating to AaaS listings
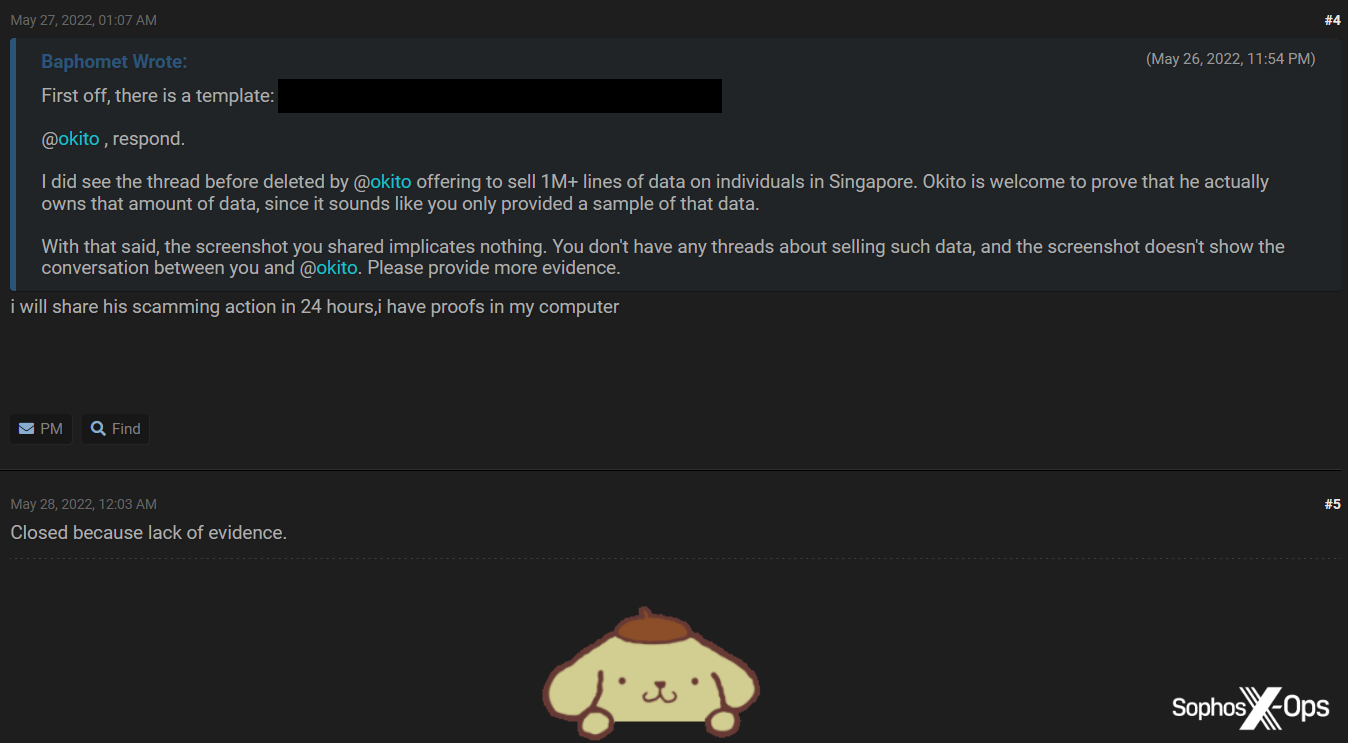
In disputed claims, the moderator may find for one party, or decide there is no case to answer due to a lack of evidence. In some cases, one or both parties will receive warnings, or temporary or permanent bans.
Figure 13: The BreachForums administrator closes a scam report due to lack of evidence
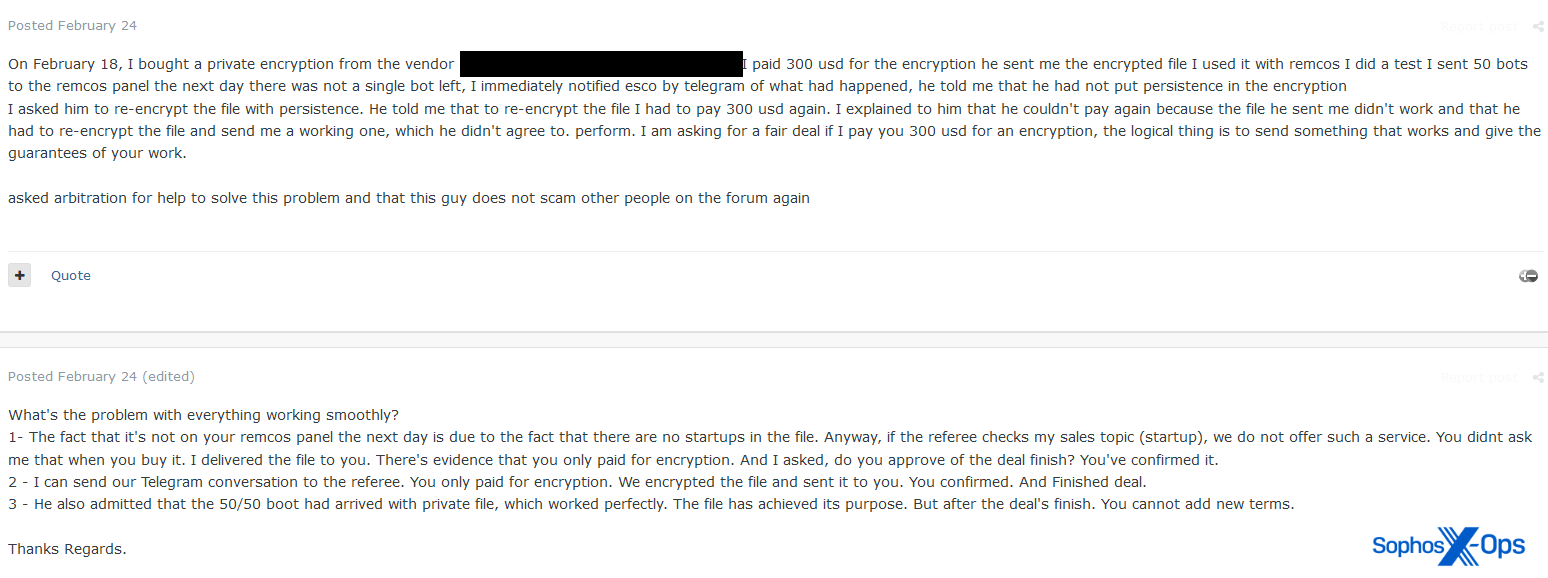
Figure 14: A disputed claim on Exploit, regarding a crypter for use with Remcos
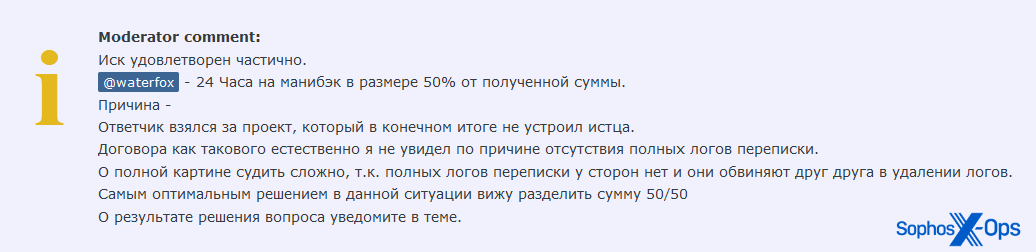
These discussions are sometimes civil, and settled amicably to the satisfaction of both parties. We noted an example where the arbiter ruled that the accused should pay back 50% of the claimed amount:
Figure 15: An Exploit moderator gives the accused 24 hours to pay back 50% of the claimed amount
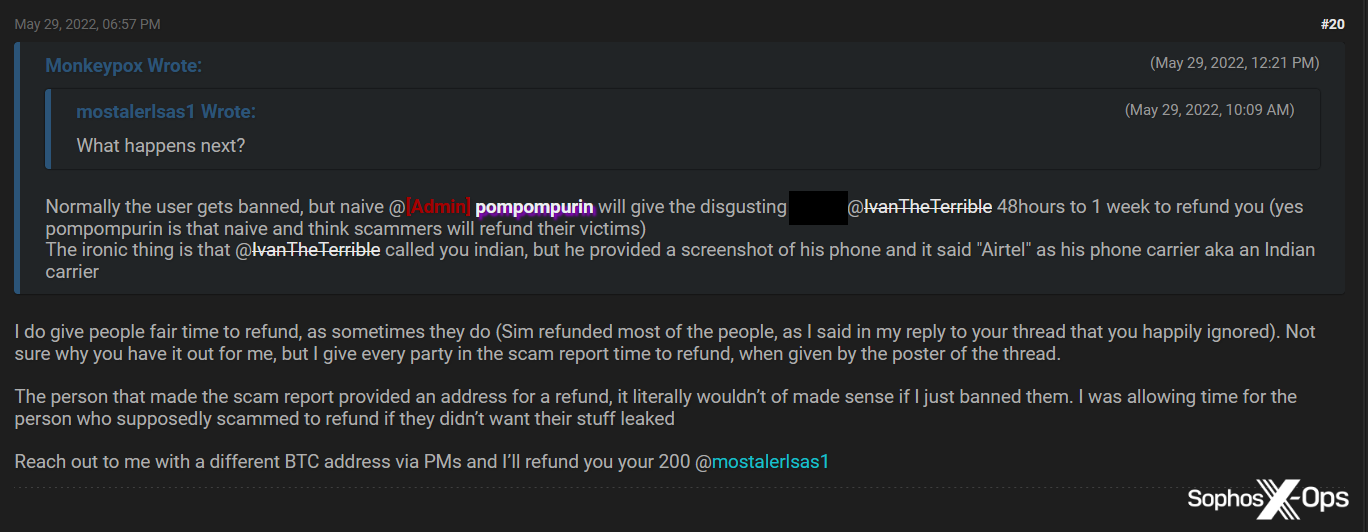
In one case, the administrator of BreachForums even compensated a scam victim out of their own pocket:
Figure 16: The BreachForums administrator personally compensates a scam victim to the tune of $200
But scam reports more commonly descend into insults and counteraccusations. In some cases, the alleged victims were themselves later banned for scamming.
Figure 17: A scam report on Exploit results in the accuser accusing the accuser of scamming
Consequences
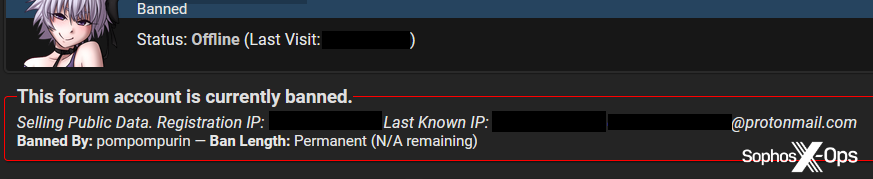
Bans (and to a lesser extent, warnings) seem to be the most common outcome in arbitrations, but BreachForums takes a slightly different approach. Perhaps to deter future scammers, its moderators publish banned users’ sign-up email addresses and registration and last-seen IP addresses, thus partially doxing them:
Figure 18: An example of a banned user, complete with published sign-up email address, and registration and last known IP addresses
We noticed a couple of cases involving serial scammers who, after being banned, simply created a new profile with a new identity, paid a new registration fee, and began scamming again.
Not just small-time crooks
We noted a few examples where more prominent threat actors were involved. For instance, here’s a curious case which wasn’t so much a scam, but involved a user who wanted to negotiate with the Conti ransomware group on behalf of a victim:
Figure 19: A user opens an arbitration claim to try and negotiate with the Conti groupabout decryption of a company’s assets
This report was closed by Exploit moderators because it related to ransomware, which is ostensibly banned on that forum. But what’s interesting is that the complainant appears to be a threat actor in their own right, and had joined the Exploit forum over three years before opening the above claim – with multiple posts expressing an interest in purchasing data. Their relationship to Conti’s victim in this case isn’t clear.
Figure 20: Some of the complainant’s previous posts on the Exploit forum
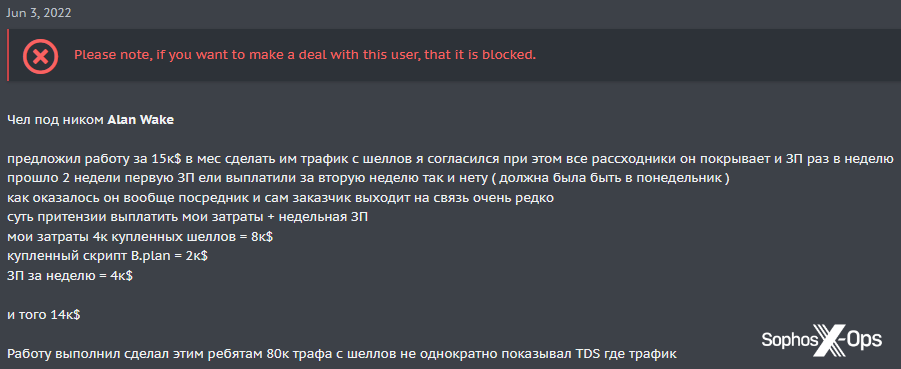
Another case involved ‘Alan Wake’ (a name taken from a video game), who sponsored the most recent contest on XSS, and was previously accused by a Lockbit operator of being the leader of the Conti and BlackBasta ransomware groups. A user accused Alan Wake of not paying their salary for ‘making traffic from shells’:
Figure 21: The XSS scam report against ‘Alan Wake’
Alan Wake disputed the allegation, and the case was closed by the administrator and the complainant banned – not for scamming, but for “insults, assaults, threats, etc’ and ‘extremely inappropriate behavior.”
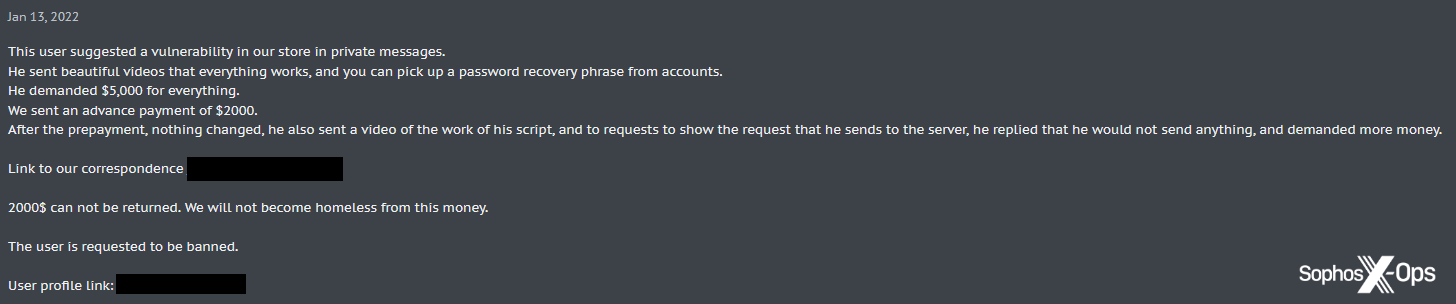
Finally, All World Cards (also a previous sponsor of XSS contests), a prominent carding group, were themselves victims of a scam involving a fake vulnerability, losing $2000 USD.
Figure 22: The All World Cards group report a scam in which they lost $2000
If there’s a takeaway from all this, it’s that no user is immune; any trade on criminal forums involves an inherent risk of scams. While there are both proactive (warnings, plugins, guarantors) and reactive (arbitration rooms) measures in place, scammers are not only common, but – judging by the data we gathered – often successful. One of the reasons for their success is the sheer diversity of the scams they pull.
In the second part of our investigation, due out this time next week (Wednesday 14 December), we’ll cover the different types of scams we observed.



Leave a Reply