(Edited July 27, 2022 to add: Since we posted this and the July Patch Tuesday recap, Microsoft has identified a private-sector offensive actor, called “Knotweed,” using CVE-2022-22047 in targeted attacks. Customers are encouraged to expedite deployment of the July 2022 Microsoft security updates to protect their systems against exploits using CVE-2022-22047.)
Microsoft released patches for 55 vulnerabilities this month, trailing only February as the lightest Patch Tuesday so far in 2022. All but five of those are rated Important in severity, and once again the majority (34) affect Windows. Four of the included Important-severity information-disclosure patches actually hail from Intel. A Microsoft advisory, ADV220002, gives guidance on those four CVEs and is also included in today’s update. (Subtracting the four Intel CVEs leaves the CVE count at 51, one less than February’s Patch Tuesday set.)
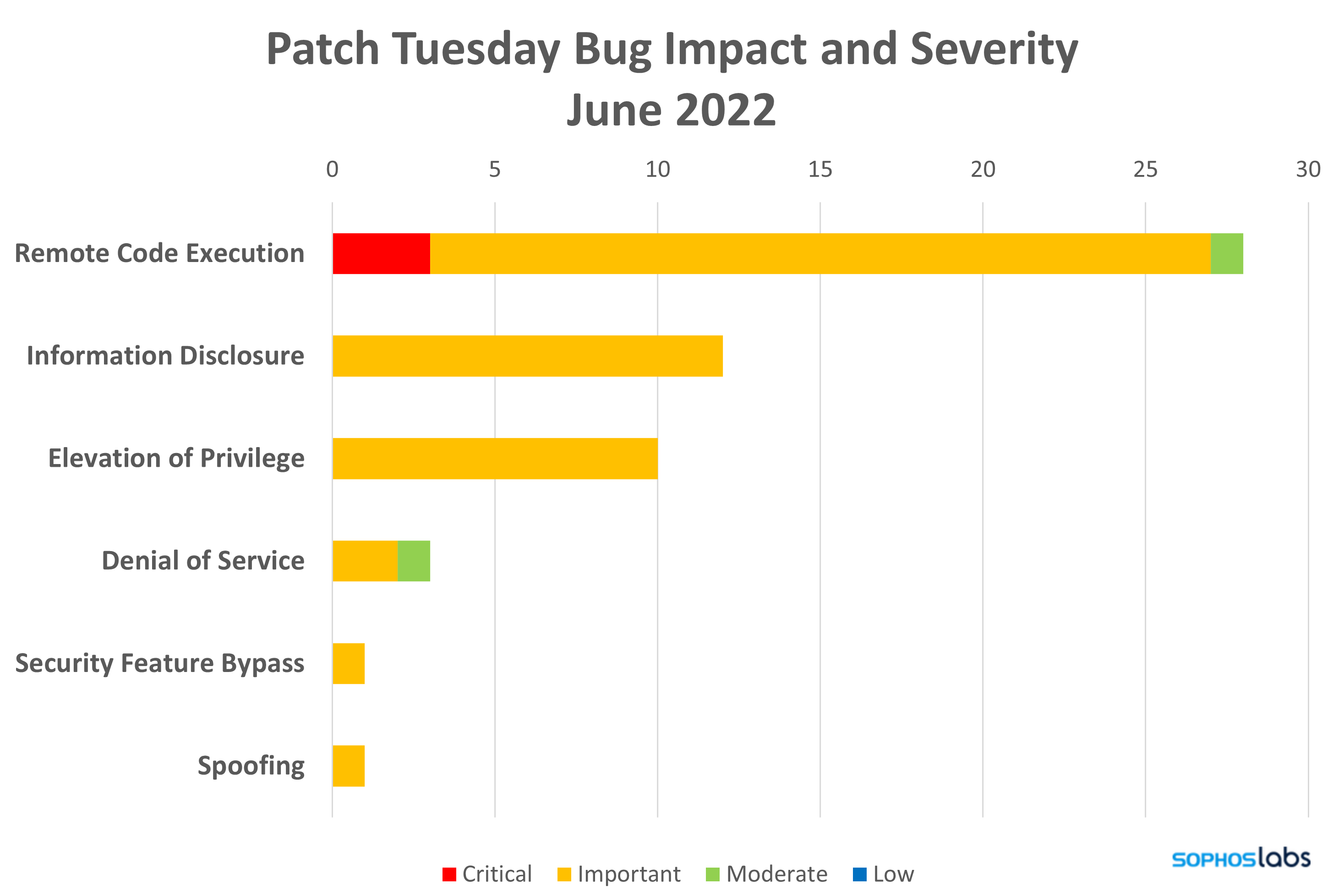
There are only three Critical-class vulnerabilities this month, but a notable two of those – affecting NFS and LDAP – are listed as more likely to be exploited. Two other Important-class Elevation of Privilege issues are also listed as more likely to be exploited. Over half of the patches (28), including all three Critical-class fixes, address RCE issues. One of the four HEVC patches this month, CVE-2022-22018, is released through the Microsoft Store rather than the usual update channels, as is the sole AV1 Video Extension fix (CVE-2022-30193).
By the Numbers
- Total new Microsoft CVEs: 51
- Total new Intel CVEs also shipping in update: 4
- Total advisories also shipping in update: 1
- Publicly disclosed: 0
- Publicly exploited: 0
- Exploitation more likely: 4 (both older and newer product versions)
- Severity
- Critical: 3
- Important: 50
- Moderate: 2
- Impact
- Remote Code Execution: 28
- Information Disclosure: 12
- Elevation of Privilege: 10
- Denial of Service: 3
- Security Feature Bypass: 1
- Spoofing: 1
- Products
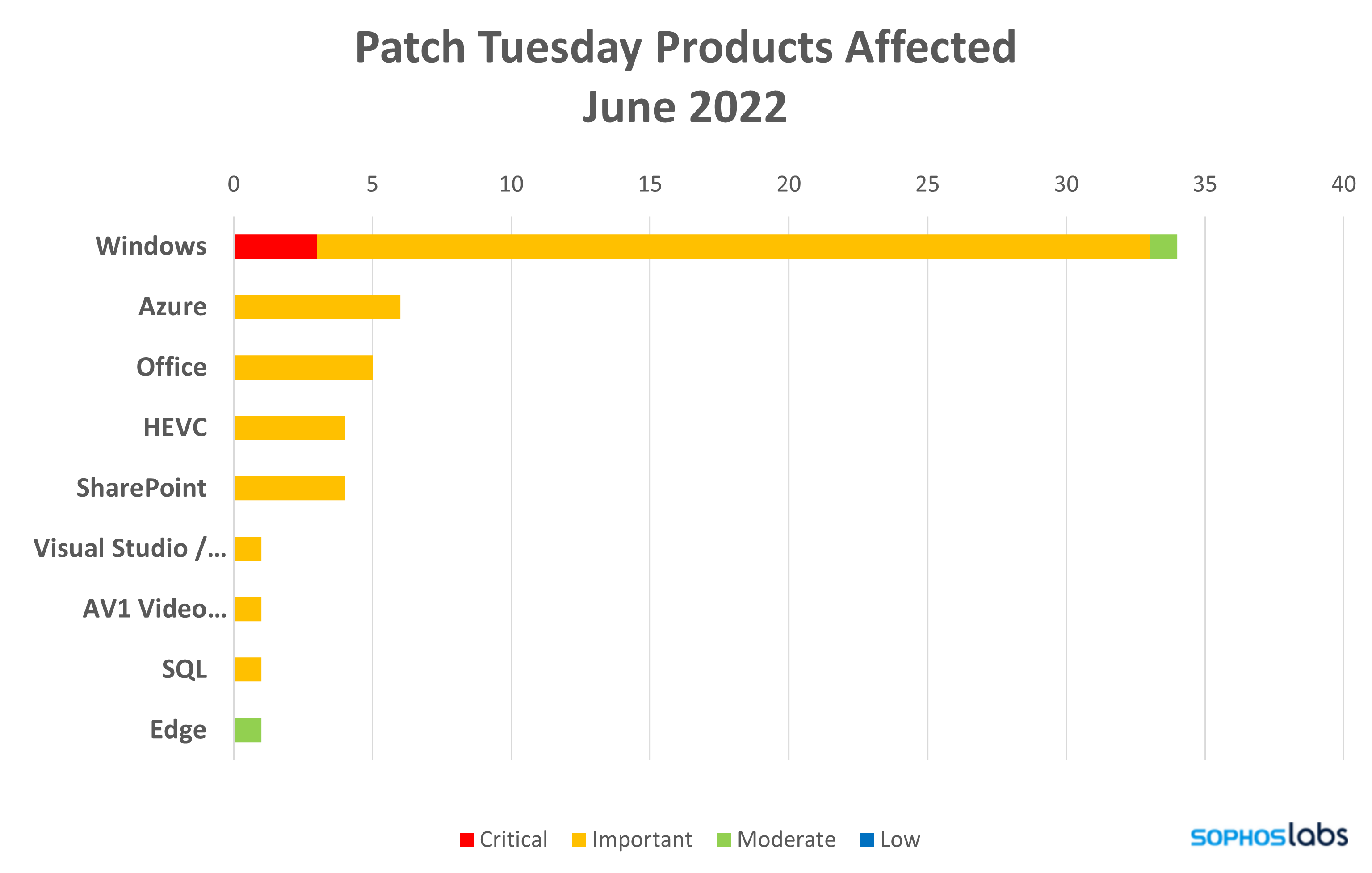
- Microsoft Windows: 34 (including 4 Intel CVEs)
- Azure: 6
- HEVC: 4
- Microsoft Office: 5 (including 2 shared with SharePoint)
- SharePoint: 4 (including 2 shared with Office)
- Visual Studio and .NET: 1
- AV1 Video Extension: 1
- Microsoft SQL: 1
- Microsoft Edge: 1
Notable Vulnerabilities
LDAP Remote Code Execution vulnerabilities (8 CVEs)
LDAP continues its rocky spring with eight more patches for vulnerabilities. One of the eight, a Remote Code Execution affecting Windows 10 / Server 2016 and later, merits both Critical-severity designation and a warning that the issue requires neither elevated privileges or user interaction to succeed, though fortunately the default setting for the affected system policy would render the vulnerability inaccessible. It should also be noted that this issue (CVE-2022-30139) technically touches Azure; specifically, the Windows Server 2022 Azure Edition Core Hotpatch.
CVE-2022-30163 Windows Hyper-V Remote Code Execution Vulnerability
After a May patch release with only Important-severity vulnerabilities for Hyper-V, June brings a Critical-class RCE to the hypervisor’s table. This issue, which affects versions of Windows and Windows Server stretching back over a decade (Windows 7 SP1, Windows Server 2008 R2 SP1), requires no user interaction nor elevated privileges. Fortunately, it’s relatively hard to exploit reliably, requiring the attacker to win a race condition. The issue is not known to be publicly disclosed or exploited at this time.
CVE-2022-30171 and CVE-2022-30172 (both named Microsoft Office Information Disclosure Vulnerability)
These sequential vulnerabilities, both Important-severity Information Disclosure issues, also affect SharePoint. (Both Office and SharePoint this month also get patches that are solely their own.) 30171 appears to have slightly greater impact potential as per Microsoft’s reported CVSS scores, but either one requires user interaction for successful exploitation.
As you can every month, if you don’t want to wait for your system to pull down the updates itself, you can download them manually from the Windows Update Catalog website (with the exception of the Microsoft Store-only HEVC patch noted above). Run the winver.exe tool to determine which build of Windows 10 or 11 you’re running, then download the Cumulative Update package for your particular system’s architecture and build number.

Leave a Reply