The ongoing hype about cryptocurrency trading and the vast sums of digital wealth some have made (and lost) in crypto markets is a strong lure for some would-be investors. But the complexity of cryptocurrency and decentralized finance (DeFi) schemes based on it have also created an environment where criminals can draw victims in, using the complexity as camouflage for fake apps, malicious contracts, and other schemes that make the victims think they’re on the road to wealth while getting them to turn over more and more currency.
We’ve already reported on one type of scheme, which we’ve labeled CryptoRom–in which potential targets are approached on mobile dating applications and lured into messaging with someone posing as a romantic interest, and then brought into a fake cryptocurrency investment scheme bolstered by fake trading applications and websites. But while we were investigating that scheme, another practically dropped into my lap: a Twitter direct message invited me to join in “liquidity mining research”.
This interaction led to an investigation uncovering a number of fraud rings based on “liquidity mining,” a form of cryptocurrency-based decentralized finance (DeFi) that even in its legitimate form is a highly complex endeavor. The mechanics of liquidity mining in its legitimate form provide the perfect cover for old fashioned swindles re-minted for the cryptocurrency age.
Criminals have used the complexity of the real thing to provide cover for a variety of scams, luring victims with the promise of extraordinary returns on investment. We found a number of these rings, operating primarily from China and using a mixture of fraudulent blockchain contracts, websites and applications to raid victims’ crypto wallets while making them believe they were making daily profits. Like the other crypto scams we follow, these have evolved from being focused on Asia into a global phenomenon. As we were researching one scam, the Washington Post reported about the victim of another liquidity mining scam that closely followed the pattern of the CryptoRom sha zhu pan scams we’ve reported about in the past.
What is Liquidity Mining?
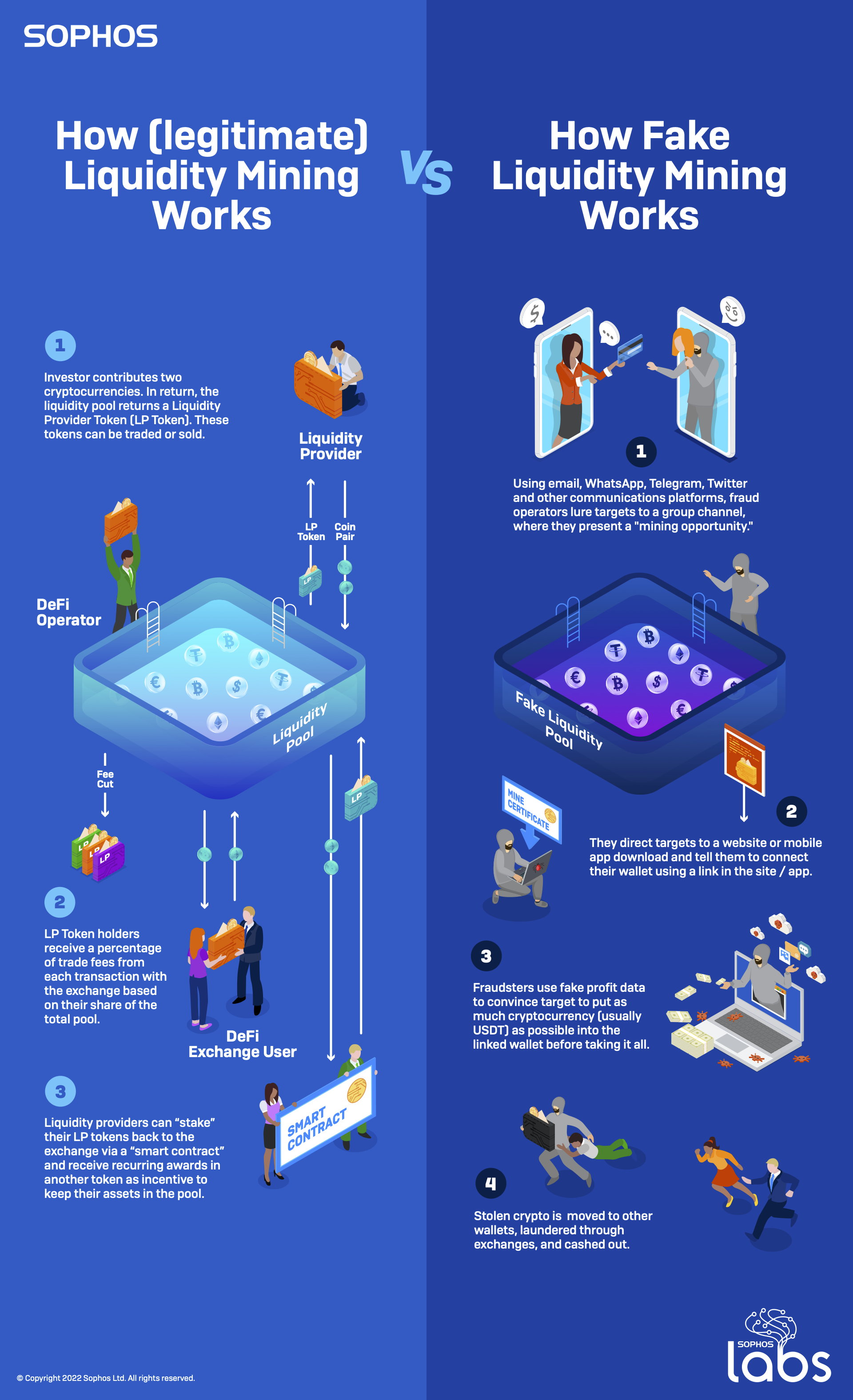
Legitimate liquidity mining exists to make it possible for decentralized finance (DeFi) networks to automatically process digital currency trades. DeFi is an emerging financial technology that uses a blockchain-based distributed ledger similar to that used by cryptocurrencies to adjudicate trades between different types of crypto—governed by trading protocols built into the ledger itself.
Centralized cryptocurrency exchanges act as “market makers” for trades out of their deposits. Coinbase and other exchanges often reward larger investors (with reduced trading fees and other benefits) for allowing portions of their deposits to be used to guarantee the exchange has enough of popularly-traded pairs of cryptocurrency to assure trades can be handled. For example, if someone wants to cash out of Ethereum and exchange it for a “stablecoin” such as Tether (USDT), the exchange needs to have enough USDT available in reserves to make that trade and fulfill the transaction. The same is true in the other direction.
DeFi exchanges do trades differently—they’re executed by a protocol built into their networks known as Automated Market Makers (AMMs). Smart contracts built into the DeFi network have to rapidly determine the relative value of the currencies being exchanged and execute the trade. Since there is no centralized pool of crypto for these distributed exchanges to pull from to complete trades, they rely on crowdsourcing to provide the pool of cryptocurrency capital required to complete a trade—a liquidity pool.
To create the liquidity pool—which usually handles transactions between a single pair of cryptocurrencies—investors commit equal values of both cryptocurrencies to the pool, tying them on the blockchain to the smart contract. In exchange for lending that crypto to the pool, the contributors get a reward based on a percentage of the trading fees associated with the DeFi protocol. The “mining” part comes from liquidity pool tokens (LP tokens)—a representation of the share of the liquidity pool contributed by the investor.
The LP tokens themselves are in essence another cryptocurrency, pegged to the value of the percentage of the pool they’re associated with.
Holding the tokens usually comes with benefits: a percentage of trading fees, and other rewards. There is also risk of loss—for example, the value of the pool of crypto may fall, and therefore the cashout value of the tokens could drop below the initial buy-in cost. But as long as the people behind the tokens don’t take the assets in the pool and run, there is at least a way for investors to get off the merry-go-round.
Unfortunately, there are several ways things can go awry if the people behind the liquidity pool are unethical—or flat-out criminal. There is no regulation of DeFi exchanges, and the only thing guaranteeing they’re on the up-and-up is the smart contract code built into the DeFi network’s (usually Ethereum-based) blockchain. But if the tokens get cancelled—or there was never really a pool backing them at all—that all goes out the window. There is ample opportunity for digital Ponzi schemes, fraudulent tokens, and flat-out theft.
Building a bank of falsehoods
Unfortunately for the crypto-curious, there are plenty of unethical and criminal “liquidity mining” schemes out there. Like the CryptoRom rings we’ve tracked, they use a variety of social media and messaging tools to approach potential victims (as well as spam emails). In some cases, they also use fake mobile applications and websites that emulate or fake connections to better-known organizations in blockchain-based trading.
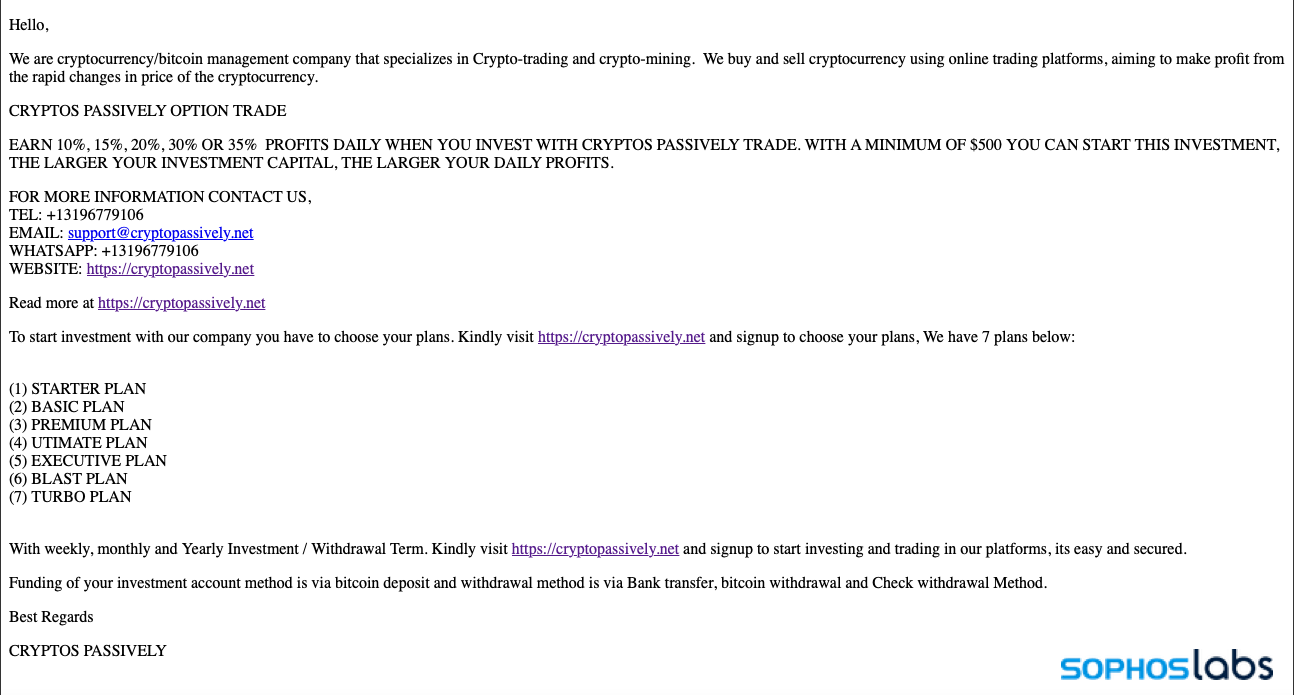
But the pitches we’ve seen have not leaned heavily on the romance angle—though they do in some cases use manufactured profiles with young women to strengthen an emotional appeal.
For example, there is the constructed profile used in the unsolicited offer I received.
The person behind this Twitter account claimed to be a young woman in “America”:
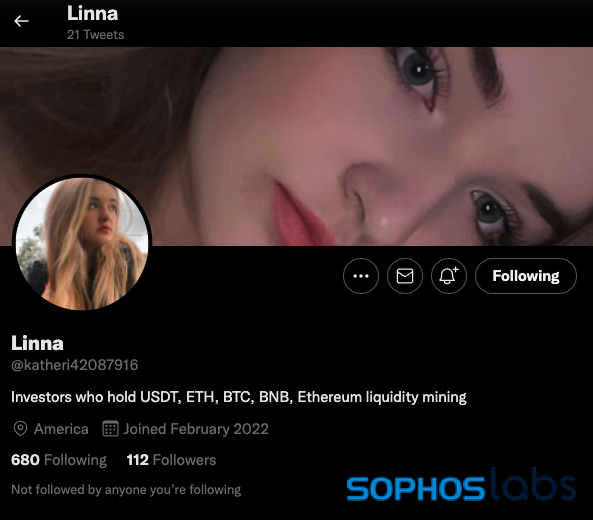
The account was set up just a few weeks before the initial direct messages I received. The timeline of the profile is packed with selfies and videos of the woman, who based on the content of some of the images and posts is in Russia. The images of the woman are used on multiple Twitter accounts with identical content.
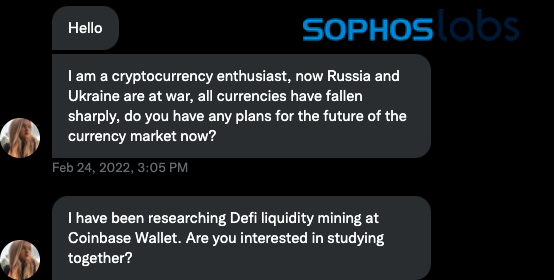
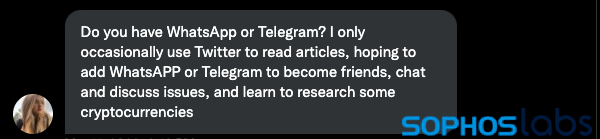
Further interaction with “Catherina” led to an invitation to continue the conversation on WhatsApp or Telegram:
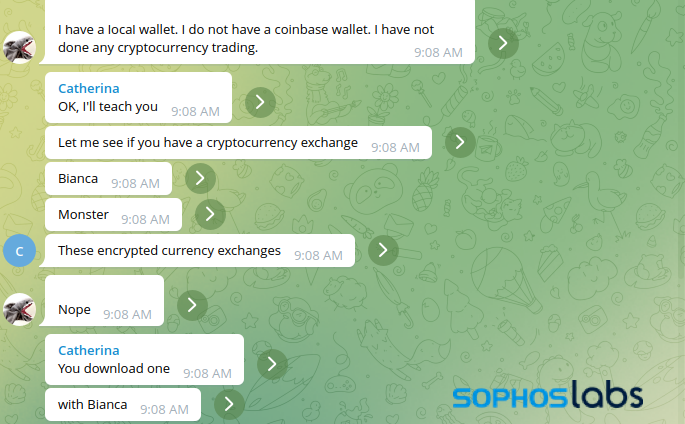
Over the course of conversation on Telegram, the fraudster tried to guide me to set up a Coinbase wallet and deposit Tether (USDT), a “stablecoin” allegedly backed by securities that roughly follows the value of the US dollar.
The Binance app store screen shot sent by the criminals showed artifacts of automatic translation and showed Chinese versions of the app. No link was provided, so this appears to be the legitimate Binance app in this case.
The screenshot of the CoinBase Wallet (another legitimate app) from the Google Play store was in Turkish:
During the course of our interaction, I managed to get “Catherine” to open a canary link—a URL tied to a server I had set up. Logs showed the person’s IP address was in Hong Kong.
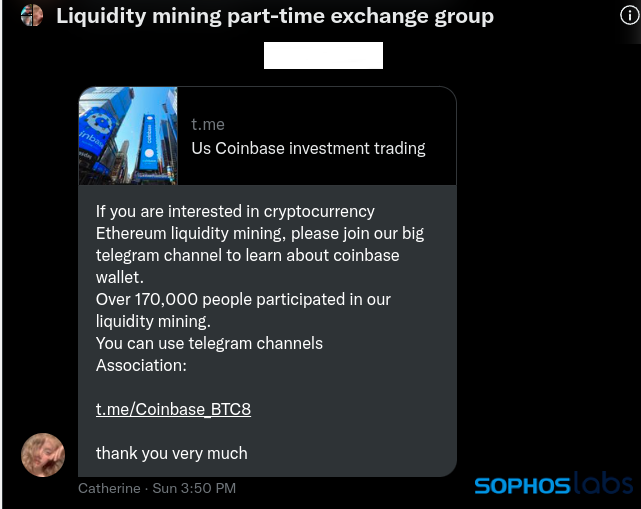
Eventually, “Catherine” pointed me to a Telegram channel called “US Coinbase Investment Trading” for more details on connecting to the “pool.” The same Telegram channel was promoted in a Twitter direct message group called “Liquidity mining part time exchange group”:
The Telegram channel shares “news” of big rewards being shared, as well as admonishments not to believe any direct messages from other forum members because of the risk of fraud. In messages purporting to be from a CoinBase administrator (@Coinbase_CarlM), the scam group directs potential victims to a URL to register their wallets on the “official block”:
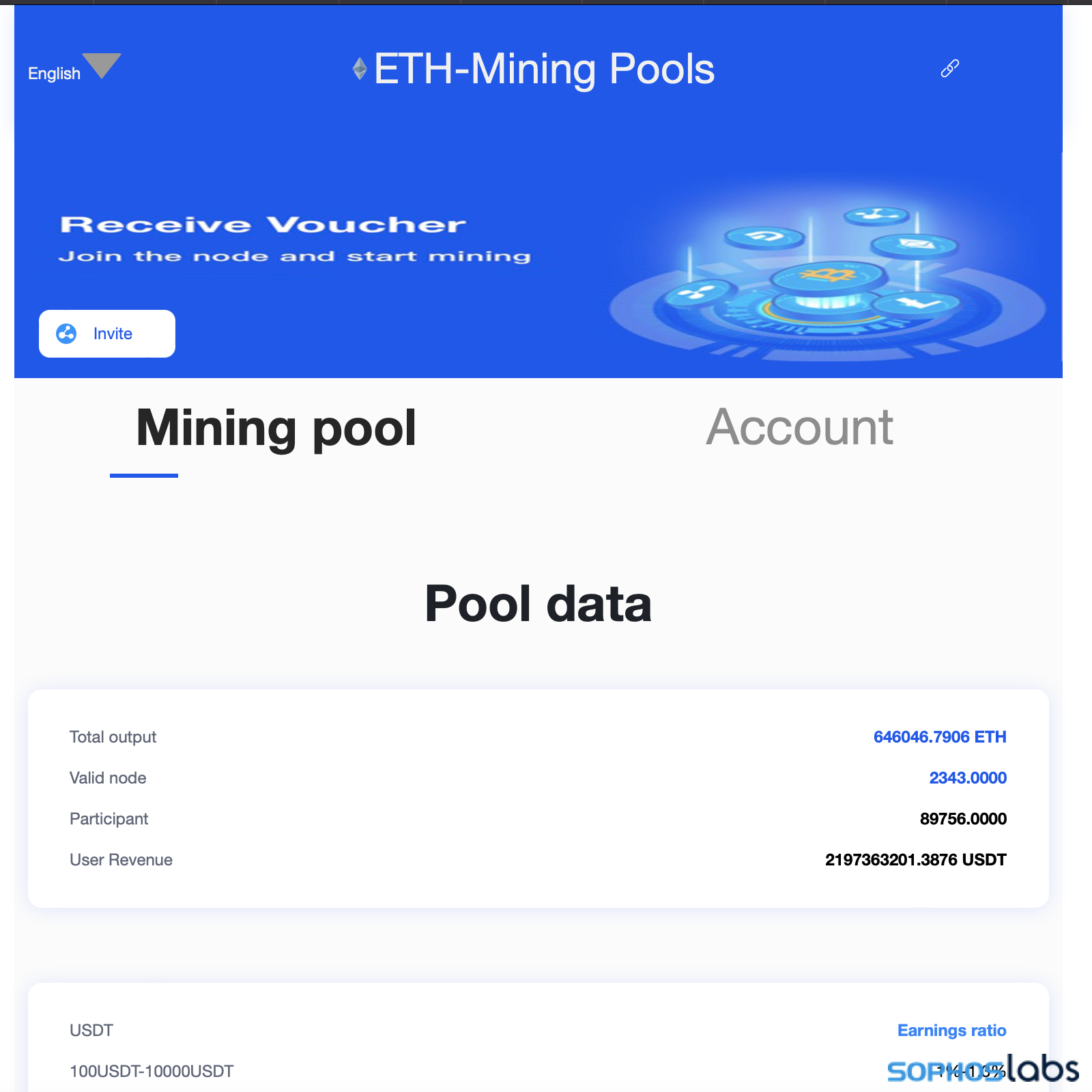
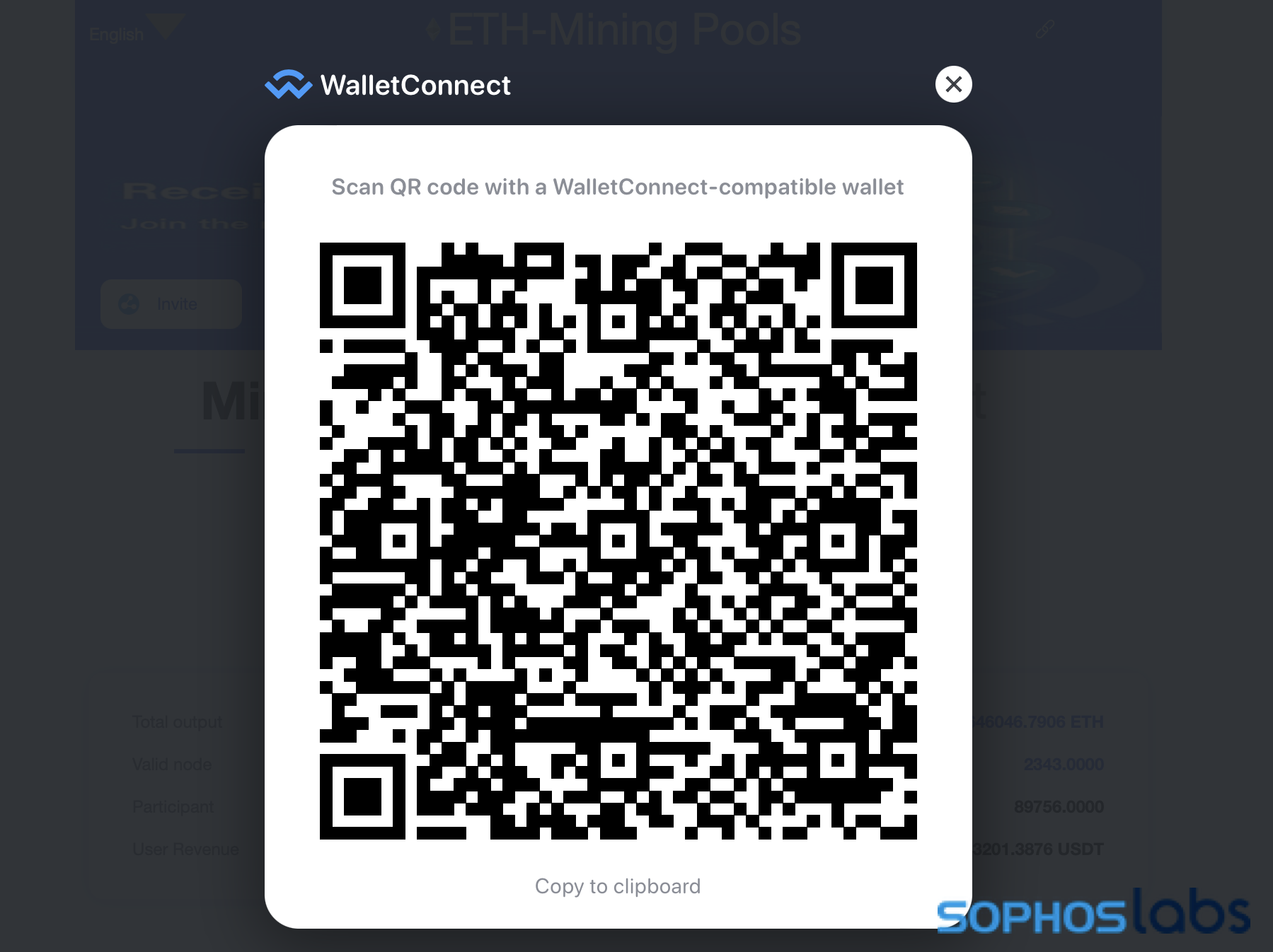
That link, coinbase-udt[.]cc, presents a mobile format website and pops up a QR code containing a link formatted specifically for crypto wallets compatible with the WalletConnect protocol. If a browser wallet extension such as MetaMask is present, it will automatically ask the user if they want to connect their wallet.
The site claims to have generated over 2 billion USDT (roughly equivalent to $2 billion US) in “user revenue,” with 2,300 “valid” wallet “nodes” in the pool. The site is hosted on Alibaba Cloud in the US, but much of its text away from the front page is in Chinese.
Once a wallet is linked, the site promises, users can invite other people to receive additional rewards. But to join, users must pay a “blockchain miner’s fee” to receive a “blockchain certificate” for their wallet to be configured as a node. Once registered, however, the user’s wallet contents can be withdrawn by the scammers at any time. The user is encouraged to deposit more and more into the wallet to increase returns, but will eventually find that they can neither withdraw their crypto nor actually cash out any alleged rewards.
An examination of domain records found a host of similar domain names pointing to the same server:
Wwv[.]trxusdt.vip
eth-usdt[.]group
trxusdt[.]vip
coinbase-usdt[.]cc
ercusdt[.]vip
cyth-usdt[.]com
We have shared details of this particular scam with Coinbase and other organizations. But this is hardly the only liquidity mining scam out there. We are continuing to collect information on other scams, including several we’ve identified that use fake mobile applications on both Android and iOS to offer a more convincing front to their fraud.
Protecting potential victims
Success has bred copycats in the crypto scam world, and each new variant of the schemes developed by those trying to expand on the CryptoRom/ sha zhu pan playbook tries to expand the pool of potential victims in different ways.
A lack of protections, regulation, reliable information on cryptocurrency investment and international cooperation by law enforcement in ending these schemes has created the perfect cover for well-run scams. With much of the world relying on social networking sites, WhatsApp and Telegram as a source for information, the scammers have turned to these platforms to lure victims and keep them engaged until as much money as possible is extracted from them—particularly targeting more vulnerable people who use these services in search of friends and companionship as well as ways to extend their wealth.
To prevent even more widespread fraud, user education is vital. People need to be made aware that these scams exist, and how to spot them. Cryptocurrency exchanges, wallet providers, and others can move to rapidly block domains and wallets associated with scams.
Unfortunately, while law enforcement can take action in some cases, it is highly unlikely that these international scams can be shut down or interdicted by law enforcement alone. International cooperation, including cooperation with the nations where these rings operate from (such as China) would be required to significantly disrupt them, and others will undoubtedly spring up to replace any that are caught. And with entire ecosystems of web and app developers available to aid criminals’ entry into these scams, the only thing that will eventually lead to their end is better defenses and education.




Pat Gilbertson
An excellent article Sean, I’m glad i read it! I’m in the process of being “lured” by a very pretty South Korean girl on WhatsApp who claims to be earning a fortune from ETH using the Coinbase wallet. She showed me a screenshot of her “earnings” so I looked up ethliquidity8, which i spotted at the top of her screenshot and it brought me to a scam investigation website.
She is very convincing, shows me lovely pictures of fancy cars, posh restaurants and expensive goods she’s bought but I’m a naturally suspicious person so I’m just going along with it for now. I haven’t, nor will I be parting with any of my hard earned cash!
I hope others read your article and take note. This is the third Chinese “girl” to attempt this. They all start by admiring my photos on Instagram and then suggest it’s better to chat on WhatsApp and from there it begins.
Once again many thanks for highlighting this plague!
Warm regards, Pat G
Issiah
Dang I think I might almost be a victim. The exact scenario this article described is happening to me right now. I have about $3000 worth of USDT connected to a so called liquidity mine, and promised the person Im talking to that I would invest more so they currently dont suspect anything. Ive been talking with them for about a month now, what should I do?
gallagherseanm
If you can move the USDT to another wallet, do it.
greg
I was lured into one, when I tried to transfer the funds it was redirected to some other wallet after about a week, just fyi
TK
Damn, I am in the same situation. Some asian girl started messaging me on Whatsapp and after some time said she was making money with a liquidity mine, showing me screenshots of her supposed earnings and showed me how to do it as well. I put 2000 USDT connected through Trust Wallet, and after some days I won a prize in an event of 20 ETH, but I needed to put another 2000 USDT in order to claim the prize. Stupid me put an extra 2000 USDT, but when the time came to withdraw, they said that since it was my first large withdrawl I had to put yet another 6000 USDT as a fee to verify my account. I’m not putting the 6000 but I am already down 4000€ and I just can´t beleive how I didn´t realise it was a scam sooner. You live and you learn
WY
this is so true. I got scammed too and felt so dumb. any idea what recourse available?
gallagherseanm
Unfortunately, there’s not much that can be done besides reporting all of the details to law enforcement and to whatever exchange platform you may have made the investment from. There are groups that claim to be able to assist with recovery of stolen cryptocurrency, but the vast majority of these are scams in themselves.
Anonymous
Is the wallet from which scam was happened at risk? Is it hacked? Delete it.?
gallagherseanm
The wallet is compromised by a smart contract. I’d abandon it.
Osman bonilla
How can I know if a platform is fake or legitimate?
gallagherseanm
There are several tell-tales.
First, if a complete stranger contacts you via a direct message on a social media platform or via a text message, invites you to a Telegram or WhatsApp conversation or channel, and then directs you to use a specific type of wallet, to acquire USDT only, and then go to a website to link your wallet, it is 99% likely that you are being targeted by a scam.
Websites associated with fake pools will have a lot of boilerplate content. Often, they will have “staff” and “testimonial” photos that are stolen generic business stock art. The safest pools are those provided through established wallet providers, such as Binance; legitimate defi networks will often require pairs of currencies to stake in order to maintain liquidity for trades between two ETH-based currencies.
Gabriel darder
bullassetguru.com- is this a scam too?
They claim to recover stolen cryptocurrency
gallagherseanm
This site appears to be cloned from https://assistassetrecovery.com/. It looks like it may be a scam.
Vinay Kumar
I know of tens of such fake profiles who are using girl pictures and finding victims on various dating and friendship groups on Facebook. They almost in every case use asian girl pictures. I think coz they are harder to search by reverse image search as they are from other Chinese websites.
RC
Shaun,
Indeed, this a pretty cool, documented article about this dangerous type of organized crypto scam. From your knowledge if someone works closer with specialized divisions on law enforcement in identifying the group of scammers and the full process details is is possible to recover the full damages for all those involved?
gallagherseanm
I have not encountered anyone who’s recovered their loss. There are organizations that will investigate and attempt recovery, but as many of these rings operating scams are in countries where law enforcement may be complicit in the activities or may not consider scams against foreigners to be crimes, it’s hard for me to recommend using any of these. Your best bet is to report the case to law enforcement and the operator of any legitimate crypto exchange you’ve used as part of moving cryptocurrency into one of these schemes.
AL
Yes I foolishly lost a lot of money in exactly this.
It was supposedly for mining the Tron coin via a decentralised App called ‘Coinfish’ which I had to access via another App called TokenPocket.
I put a small amount of USDT in and took a smaller amount out. Then I put a larger amount in and took another smaller amount out. But then I got confident and I put a lot more USDT in and then they found reasons to say that I couldn’t withdraw any funds and my account was frozen unless I put more USDT in.
An embarrassing and financially painful lesson learnt.
And yes I was contacted by a pretty Chinese girl via Tiktock…but my Chinese girl was different I said to myself. She even video chatted me a few times and chatted for 3-6 hours every day for nearly 3 months. Anyway if anyone reads this I hope it may prevent you from also being a fool.
Vash
I have one messaging me now if you wanna try to tack down the ip
DA
Sean, I had 100,000+ USDT in a wallet linked to https://binances-eth.me/mining/#/
I was transferring funds out of that wallet when I got a notice that I violated the “smart contract protection mechanism” and the funds were redirected to another wallet. I am supposedly earning twice the daily profits in this staking operation. In order to have my funds returned to the liquidity mining pool, where I will have full access to all my funds plus the profits, I need to inject an additional 200,000 usdt.
Based on what I read in your article I think I just learned a very expensive lesson and need to walk away.
Thoughts? Other than me being such a DA for falling into this trap
gallagherseanm
This sounds a lot like some of the liquidity scams we’ve seen. They use a smart contract that locks down the USDT and eventually pulls all of it. The additional “fee” is an attempt to take even more from you.
I can only add that I know how difficult it is to distinguish these scams from real liquidity mining operations, but the Bianance name spoofing is an example of one of the tactics these scams use.
Liss
I got pulled into locked mining where I invested a smaller value I get daily return. I locked another mining machine and was overdue, but I was not communicated of the T&C. After my second profit withdrawal, the platform locked my account and demand me to deposit 30,000 USD to unlock the balance. Please advice if this is something familiar.
Anonymous
Thank you for sharing this thorough article. It confirms that I am a victim to this scam. I used the Plenty of Fish dating app, and a Chinese girl gave me her telegram and lured me into investing crypto into what appeared to be a legit defi-farm. Later on I discovered that, not only did the dApp withdraw all my USDT, I could not withdraw from the dApp. I had video chatted with this girl and everything, unfortunately, she is a scammer. I believe that Karma will run its due course. I don’t believe she will prosper living this way for long.
Kayleen Welsbacher
Oct. 31st 2022, my husband received a text from an unknown caller asking, “What are you wearing?” He replied back. He told me about this text but didn’t tell me he had continued to text this woman, over the next month, who owned her own salon business (odd since she had a lot of time to text my husband between running her business and mining bitcoin) and had a daughter who currently lived with her mother (again odd since she seemed to make enough money to support her child). She apparently has a facebook page with a vivacious attractive young 20 something woman. She convinced my husband of almost 19 years to invest $10,000 to join her small bitcoin mining group. He also decided to take out a $25,000 loan and put that into bitcoin as well.
We are now currently separated.
Now I don’t know if this is a scam. To me, I feel this is a catfishing scam that won’t end well. But I also know that my red flag trigger warning bells might be more due to the status of our almost dissolved marriage.
So am I wrong to feel this uneasy about his situation with this random “woman” and her easy side job that makes her some extra cash on the side. Is this jealousy or should I stick my neck out (hard to not be concerned about his well being after 19 years) and let him know he might have just been trapped in a scam?
Personally, I would never invest money (let alone $10,000) to someone/group after only knowing them for a month… online to boot.
Vicky
Hi. I have also been a victim of Liquidity
farming . Some Japanese girl on telegram lured me into investing 9000 USDT in a course of few months. First I did not believe or trust but she kept sending me screenshots of her earnings. I was able to draw a few usdt initially as profit earnings but then they locked my wallet and withdrew all the crypto. Now they are asking for more 3000 USDT in the name of membership fees. It says it is a mobile node mining app. The customer service on telegram asks for the membership fees when I ask them to release my crypto .They say that my wallet will be unlocked once I pay the 3000 USDT for the membership. But now I am sceptical and don’t believe in investing any more . The mining app is genesis-coin.org and genesis-coin.vip .
I am new to all this so I will really
appreciate if someone who knows about
this can look up genesis-coin.Org or
genesis-coin.vip and let me know if this is a
legit liquidity mining. I really need your help . Thanks in advance for your suggestions and advice .
gallagherseanm
I’m sorry, that does appear to be a scam liquidity mining site.
Anonymous
I had lured by a Chinese girl. She sent me some ETH and I checked out that have 80mil ETH worth. So I believed I just deposit $300 to my trust wallet then link it to liquid mining web. Should I dumb that wallet?
gallagherseanm
See if you can remove the contract using the site revoke[.]cash.
Daniel Williams
Is there a way to look at the smart contracts connected to a particular wallet?
gallagherseanm
There is a tool, revoke[.]cash, that can be used to look at smart contract “allowances” associated with a wallet. If you’re lucky and USDT tokens have not yet been removed from your wallet, you may be able to use this to purge the malicious contract. But I can’t guarantee it will work.
Robert Joseph
Unfortunately I found this too late and was scammed for overt $1,000 USDT, of which I wasnt even trying to link. I linked one wallet to a pool/node and started seeing profits overnight so I thought I would start another crypto and pool to maximize profits. I didnt think you could use one wallet for more than one pool so the second pool I started was just starting with $2 of BNB, but somehow when I “joined the pool” it was able to connect to my main wallet and within an hour the entire balance was transferred. I thought I was being careful but it connected to the wallet without me doing it and then sent the balance to an address.
The person in my story is from the “Netherlands” and although many details didnt match up I overlooked some because she took time to push me into the pool. In the end after my money was scammed by someone else first she offered to help me close the Trust Wallet and start a new one with MetaMask but I didnt plan to assets just yet. While she was very understanding she mentioned “how much liquidity I had left” which wasnt something I wanted to think of.
Shortly after I was wondering who she really is anyway because even though she wasnt the one who made me setup the second node, she got me into this in the first place so I asked a strange request of her. “Can you write down this secret phrase I’m about to give you, which was just something on my desk, and take a selfie with that note. At least I would know this was someone real but didnt prove much more than that. But I knew how she reacted that she was a scammer herself and probably mad that she didnt snatch my wallet first. She refused to send a pic and started to blame me of accusing her of blame which I didnt. She continued to get mad at me, extending the idea that she was not who she said she was.
She was vague about many details btu I thought maybe it was the language barrier. One thing that stuck in my mind was her claim of having 500,000k USDT herself and making 10,000/day..but the total assets of her pool was only 50,000 USDT with just under 2,000 participants. If she had 500,000 the pool would reflect that.
Does anyone know how they couldve linked my entire wallet when I thought the Trust wallet was secure taking/transferring my balance, and that IO wasnt even linking it to the pool??? I thought I was starting the new pool with $2
Any help would be cool for me and everyone else.
Robert Joseph
gallagherseanm
They used an ETH smart contract that allowed them to access all your USDT.
T
Hi Sean,
Can u check if Ethh.life/#/ is a scam?
We are dealing with some simular story’s like the ones above.
Thanks!
gallagherseanm
Yes, it is a scam, and is identical to about 190 other scam sites.
Anonymous
My husband has fallen victim
We’ve reported it but all authorities seem to do nothing
victim
Was scammed about 60,000 USD from liquidity-mining-token.com
Was directed to download the official defi wallet by crypto.com from google appstore which brought down my guard.
Then i was asked to browsed the liquidity URL through the app browser. Why would the defi wallets allow this?
gallagherseanm
The apps are designed to allow contracts to be connected to your wallet through these links for legitimate transactions and for things like NFTs. Please contact me via email; I can try to connect you to Crypto.com’s security team.
Ivica
Hi. I experienced the same as the users above. The person’s name is Jessica Zhang. She directed me to Trust Wallet and I have to copy/paste some address she gave me to mine ETH. I invested $5,000 and earned $100 a day for 10 days. I was able to withdraw the money when I found out that I might have been scammed. Why was I able to withdraw money and an additional $1,000?? Is it possible for me to have a LEGIT smart contract?
Ivica
gallagherseanm
Scammers sometimes allow withdrawals in order to build confidence, so that you will put more crypto in. I can’t say for sure whether you’re involved in a scam or not without more details.
Tina
Bisa kah penjahat seperti ini di tangkap?
gallagherseanm
(Can criminals like this be caught?)
Only with international coordination. Unfortunately, as many of the criminals involved in these schemes are based in places without law enforcement cooperation in place, they may go unpunished.
SoupremeSama
Hi Sean,
I was on Bumble because I thought I was ready to date again. A few approached me, and I decided to chat with some of them. This one Chinese guy who claimed he was from Malaysia (he can also speak chinese and malay), hit it off with me quite well. Then he showed me his earning, to which I wasn’t interested. But slowly he convinced me to make my first deposit just to “learn”. Long story short, my trust wallet has about $29,060 USDT. I saw it make “mining profit” everyday. For some reasons, today I wanted to withdraw all of it. And now the mining pool informed me they suspected my account was hacked so my fund is temporarily pledged to the pool. In order to release the fund, I have to deposit the exact amount, which I don’t have. I realised I was being very naive and stupid. And worst, my emotions were being played hard. I feel more broken hearted than anything because right now, the guy I have been chatting with wouldn’t show me a photo of himself holding a piece of paper that says my name.
What I want to ask you is, can you help me retrieve my fund?
Kind regards,
Me
Hi Sean,
Is this website a scam? benchmark.co.com
I have invested U$ 250 and the “finance advisor” turned it in U$37K in two months. He supposed to send it to my crypto.com wallet, but in the middle blockchain.com sent me an email that I needed to provide 21% of Liquidity into my crypto.com account to have this money. I did not believe them as the email extension from Blockchain.com doesn`t appear as showed in their official website. What do you think about it?
Much appreciated.
gallagherseanm
This looks like a scam site. I’ll reach out for further details.
Ade
Has anyone heard of FATH.
They are also offering ‘rewards’ from liquidity mining.
Cannot find any information on FATH other than in the app when the wallet is connected.
drixe
Great article gallagherseanm. Thanks to you, I was able to get out of it at the last minute. The whole time I smelled something for a mile and finally I ended up here. Thank you very much for this post, God bless.
Alex
I wanted to express my admiration for your recent article; its insights are truly invaluable. It’s unfortunate that I didn’t come across it sooner, as it could have saved me from an unfortunate experience. I fell victim to a scam orchestrated by individuals I encountered through a WhatsApp group. Despite considering myself quite security-conscious and highly technical, their tactics were remarkably cunning, which makes me wonder about the vulnerability of the average person.
Frankly, the whole ordeal has left me rather unsettled. The website they used for their scam is: https://trust-farming.org/. I feel compelled to warn others about this, as I wouldn’t wish such an experience on anyone.
On that note, I’d like to ask if you have any suggestions regarding how I might contribute to preventing and dismantling scams like these. It’s disheartening to think about how many others could potentially fall into the same trap. Your guidance would be greatly appreciated.
Rushdi Felimban
Hello Sean,
I’ve been going through an almost identical routine as mentioned in the article and comments since Sunday 3rd of September 2023. So far, I just invested 200 USDT on Binance, and the Defi Liquidity Mining app is called “Trust Wallet”. I’m a retired IT professional residing in Saudi Arabia. I suspected it at the start but got carried away for the usual reasons. I’m willing to collaborate by all means to see if my case is a scam or otherwise!
Highly appreciated
Marcus
Do you know or heard of cgcoinmine.com? Are they a legitimate mining site or is it a scam website? My initial principle I invested was 1k and made a profit of 530 and I wanted to make a withdrawal but they told I first had a tax payment of 1% makes sense. But then added another $135 for a account manager to sign a transfer form of profit. After I had paid that they said that their was issues releasing the funds because my wallet address was wrong which it wasn’t. Then they messaged me Stating “your account with us has been suspended due to too many transfers trail failed and this is not done by us but from all the head office of all financial institution monetary movement policy. This will can be undone by paying 5 percent (5%) of the amount in your account to clear your account. Then your account will be unsuspended”. With all that to say it would a $76 dollar amount I owe to unsuspend my account. Which I didn’t proceed to pay. What do you think I should do? Any advice and tips would be greatly appreciated.
gallagherseanm
The site doesn’t appear to be online now. Based on its hosting and domain history, it appears to be a scam.
Strong
I have been cheated with 3500 USDT . As I read the above stories, I understand how easily I let them take my money.
It happened in a way that a whatsapp group named Liquidity mining 804 introduced itself to be from Binance Defi mining pool and guided me to download trust wallet and then gave me 2 USD BNB rewards and asked me to send my wallet details to receive BNB and then sent me a link to register and sign that smart contract to start mining.
At the begining I received 1% reward every day and I could send it to my trustwallet but I did not know that it was all fake and they had control of my wallet and one day I saw there was no money left in the wallet and they sent a text that I am going to receive a reward that is why my money is transfered to the blockchain but it exists but first I should deposit 2000 USDT to to get the reward for 1.5 ETH and my money back. This was the time I realized it was too late to get any thing back from them.
Mark
Well I come to realise how stupid I am. Have given away most of my hard earned savings. A little over a week ago, had a Binance chat group come up on WhatsApp. I watched it for a couple of days, they jiggled the lure in front of me. Asked some questions, then Anna suggests we talk private. She ran the script, I bite the bait. Next thing I know, I’ve opened a Trust Wallet account. She then gave me a binding link to be pasted into the explorer in Trust Wallet. I added some USDT,1600, had small returns for a couple of days. I guess greed took over. Then thought I put it all in, to make more. So I built it up to 5100usdt, had my first 100udst daily earnings. It was always going to be a short time investment. Then next day, earnings locked no withdrawal. I messaged them back, they said you must of won a prize, your lucky. It has been staked for 30days with some high percentage rate in returns.
Now I get silence. Never to see my money again.
These scammers make life sh💩t.
Anonymous
I wonder if your Anna is the same as my Anna, whom I’ve been chatting to for the past couple of weeks. She’s a great girl with a wonderful heart and showed me how to secure a future by mining through her defi pool. We sent each other pictures of our day, left voice messages and even planned to meet when she felt confident in 4-months’ time. My investment went from an initial £300 to £1000, then decided to make it £5000. Was about to add another £25K in USDT before something happened…some other beautiful girl from Singapore (but supposedly lives near me) messaged me and was almost giving me the same script as Anna.
Needless to say, my spidey senses were tingling. I did a quick research on these crypto scams and decided to withdraw from the defi pool immediately! Cashed in all my crypto assets for good measure, just in case. I’m still talking to Anna…she could be legit. But there won’t be any money invested in her project. I’ll make my own investments through research, rather than take a stranger’s word for it.
Moral of the story, it’s the pretty ones that get you *lol*
M
I’m in a similar situation, they took my 150k in trust wallet, i have since revoked the access to my wallet.
Now after 30days, they’re asking for another 50k in a new wallet to link up and unlock the full P&I.
I have told them they locked all my money and they blame the system, and insist i need to put more money in or i’ll lose all my funds in the pool.
Alisha B
Majority of these fraudulent investment schemes operate on the same wavelength and with similar characteristics; they will hide under the cloak of being an investment company to lure you in and after paying the initial fees, they run a facade making it seem like you are actually making progress with the investment. It suffices now to acquire more insight and knowledge in the crypto world. They operate mostly without the SEC license and no regulations whatsoever. Know more about cryptocurrency investment fraud, binary option scam here; revoltseal.tech for proper perusal of varying methods employed by these individuals and ways to counter them in defense.
King edwin
There is another site
Let me get a link
hxxps://kk1111[.]net/?inviter_id=AU6WRJDU3
They also claim they do liquidity mining u cn look them up and see if they are authentic but they use trust wallet. I donno how we can help those that Have been scammed to retrieve their usdt
gallagherseanm
This site is using a kit we’ve seen before on scam mining sites.