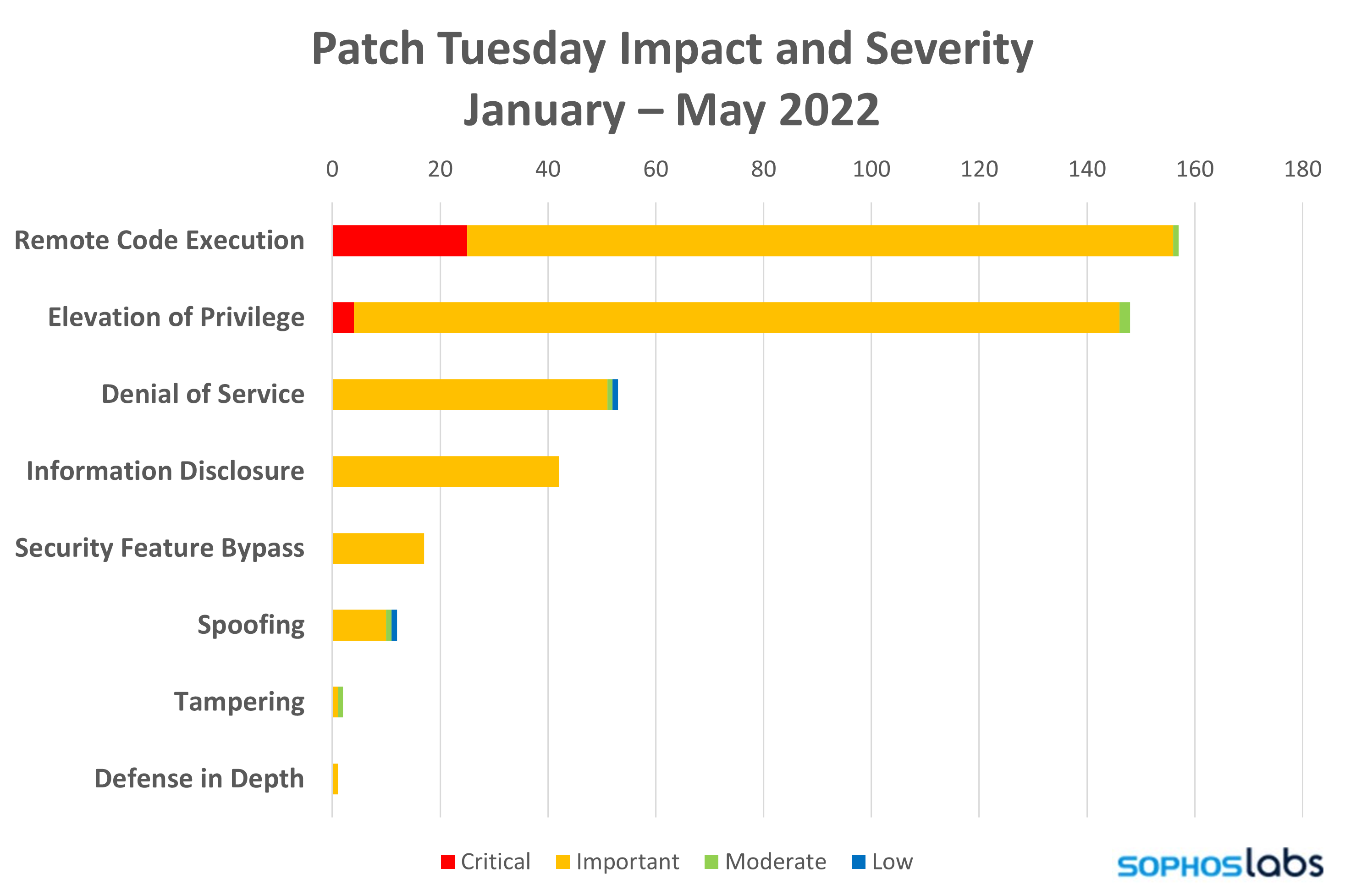
The May 2022 Patch Tuesday release is moderate in volume but relatively light in severity. Microsoft patches 74 vulnerabilities this month. The vast majority of those are rated Important, and 60 of the 74 bugs affect Windows.
Interestingly, two of the critical vulnerabilities this month are elevation of privilege issues related to Active Directory and Kerberos. Given the potential for vulnerabilities like this to be exploited as part of lateral movement attacks in network attacks, these should be treated with priority—along with the six other critical bugs, which fall into the more typical combination of critical severity with remote code execution impact.
By the Numbers
-
- Total new Microsoft CVEs: 74
- Publicly disclosed: 3
- Publicly exploited: 1
- Exploitation more likely: 11 (both older and newer)
- Severity:
- Critical: 7
- Important: 66
- Low: 1
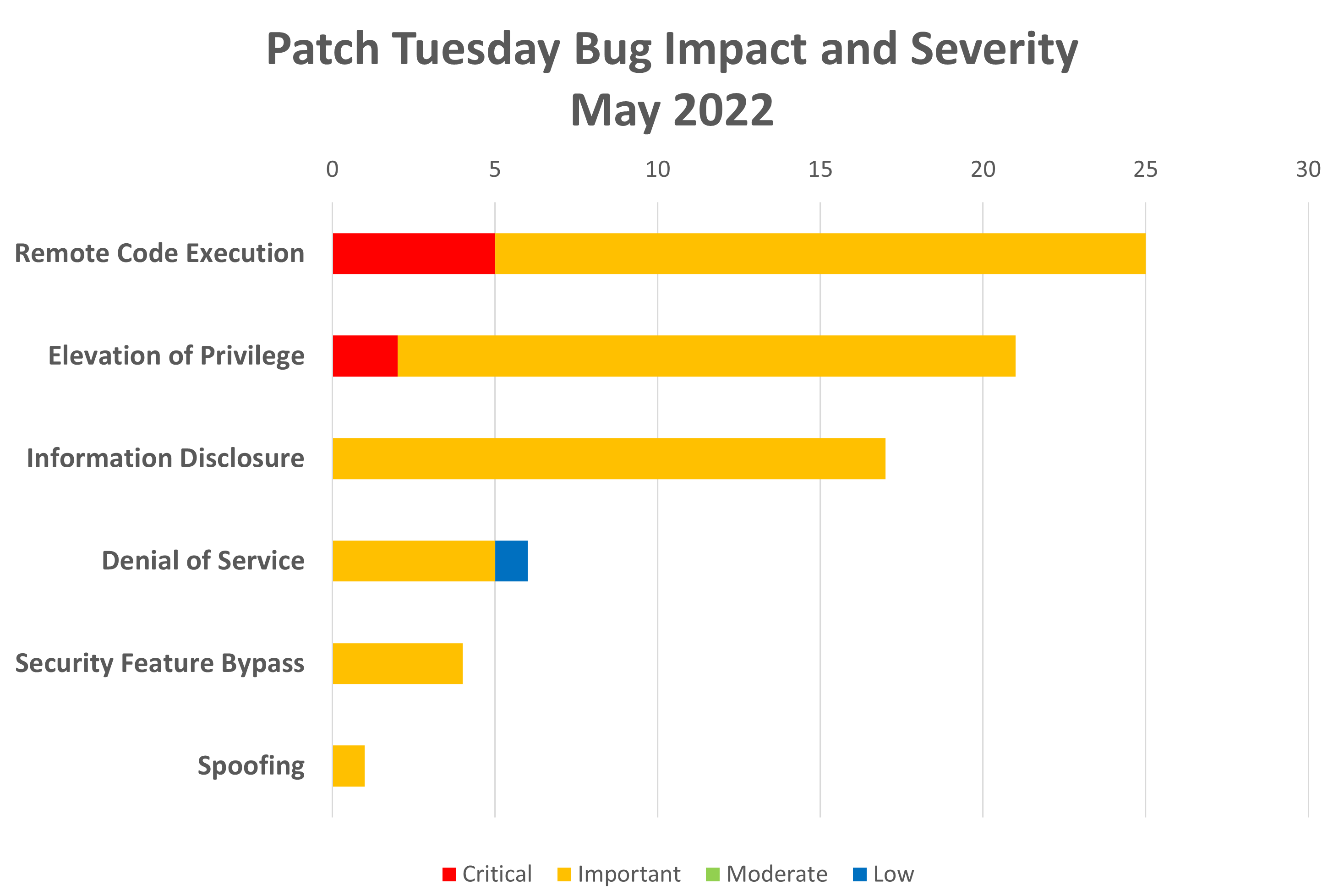
- Impact
- Remote code execution: 25
- Elevation of privilege: 21
- Information disclosure: 17
- Denial of service: 6
- Security feature bypass: 4
- Spoofing: 1
-
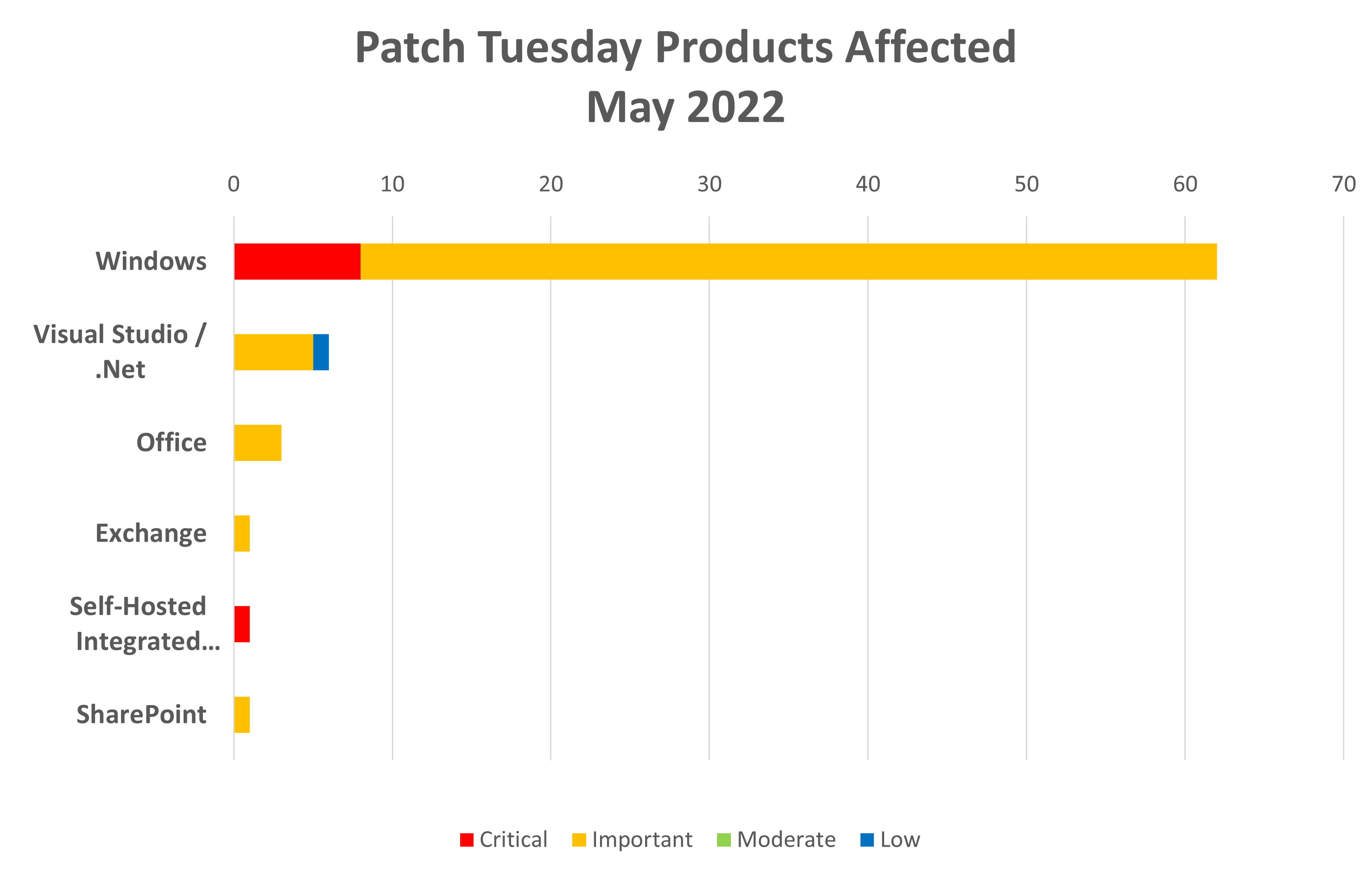
- Products
- Microsoft Windows: 62
- Visual Studio and .NET: 6
- Microsoft Office: 3
- Microsoft Exchange: 1
- Self-Hosted Integrated Runtime: 1
- SharePoint: 1
- Products
Notable Vulnerabilities
Windows Hyper-V Denial of Service Vulnerability
This vulnerability, CVE-2022-22713, is notable as it’s listed as “Publicly Disclosed but not Exploited” at time of release. It’s also listed as “Exploitation Less Likely.” It’s one of three vulnerabilities this month related to Hyper-V. All three Hyper-V vulnerabilities are rated Important. The other two are an elevation of privilege (EoP) and a security feature bypass.
CVE-2022-26923 Active Directory Domain Services Elevation of Privilege Vulnerability and CVE-2022-26931 Windows Kerberos Elevation of Privilege Vulnerability
These two vulnerabilities are notable as EoP vulnerabilities rated “Critical.” The Active Directory vulnerability, CVE-2022-26923, is also notable as one of the “Exploitation More Likely” vulnerabilities this month. While these are EoP rather than remove code execution (RCE) vulnerabilities, they’re definitely worth prioritizing because of the risks that these could be used as part of a network attack to gain control of the Active Directory environment and create high-privilege accounts that can be used to maintain persistence, engage in lateral movement and launch additional attacks on the network.
LDAP Remote Code Execution Vulnerabilities
These vulnerabilities are notable as RCE vulnerabilities affecting LDAP, which is a part of the Active Directory infrastructure. This month sees a total of 10 LDAP RCEs all rated as important. None of these are publicly disclosed or exploited and are marked “Exploitation Less Likely.” It’s also worth noting these vulnerabilities in conjunction with the previously mentioned Active Directory and Kerberos vulnerabilities. It’s also worth remembering last month’s clutch of LDAP, Active Directory, and DNS vulnerabilities.
Taken altogether, these past two months’ patch releases indicate that organizations should take special care to test and prioritize patches for their Active Directory servers and infrastructure.
Sophos protection
|
Vulnerability |
Sophos Intercept X / Endpoint IPS |
Sophos XGS Firewall |
|
CVE-2022-26925 |
AV: ATK/PetitP-A |
|
|
CVE-2022-29104 |
AV: Exp/2229104-A |
|
|
CVE-2022-23270 |
IPS: 2307166 |
IPS: 2307166 |
|
CVE-2022-26937 |
IPS: 2307169, 2307170 |
IPS: 2307169, 2307170 |
As you can do every month, if you don’t want to wait for your system to pull down the updates itself, you can download them manually from the Windows Update Catalog website. Run the winver.exe tool to determine which build of Windows 10 or 11 you’re running, then download the Cumulative Update package for your particular system’s architecture and build number.

Leave a Reply