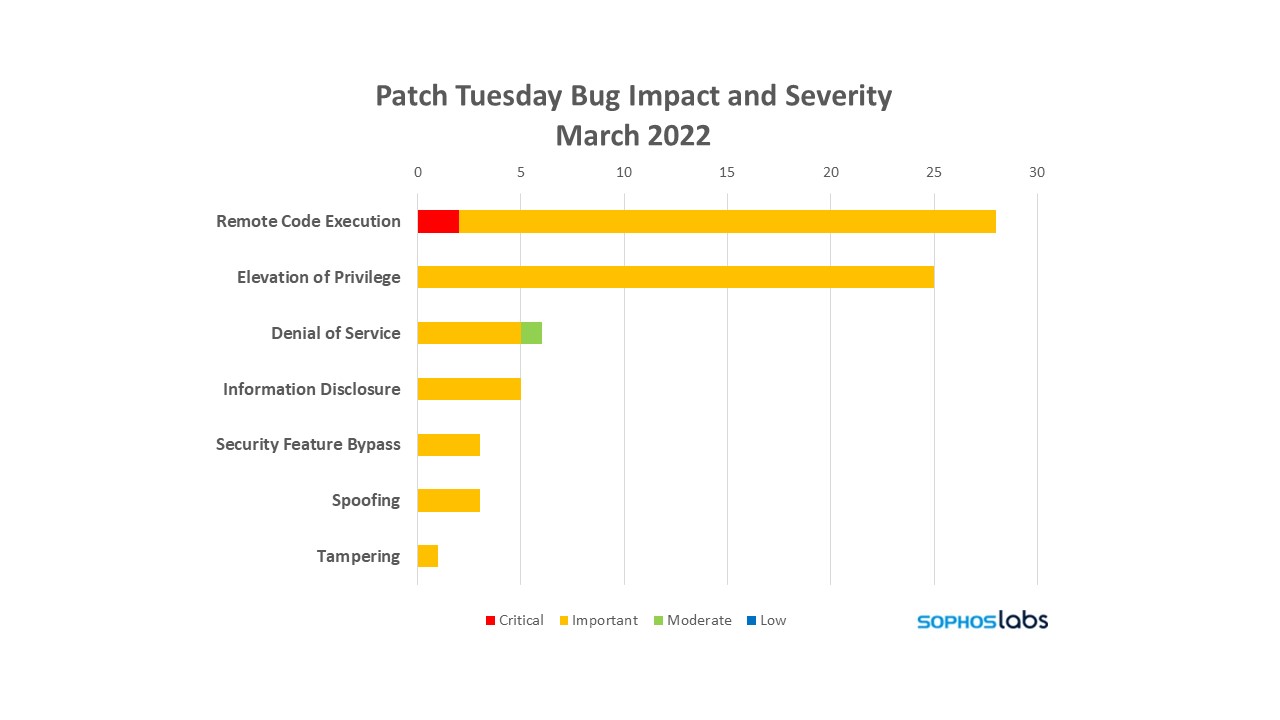
After a relatively light update load in February, this month Microsoft patches 71 vulnerabilities, covering a broad spectrum of products. Of the 71, Microsoft rated two as Critical in severity, one Moderate, and the remaining 68 are rated Important. At time of release, the company says none of the vulnerabilities are known to be under active exploitation, though there’s already a public proof-of-concept for one issue (CVE-2022-21990, a Remote Desktop Client remote code execution vulnerability).
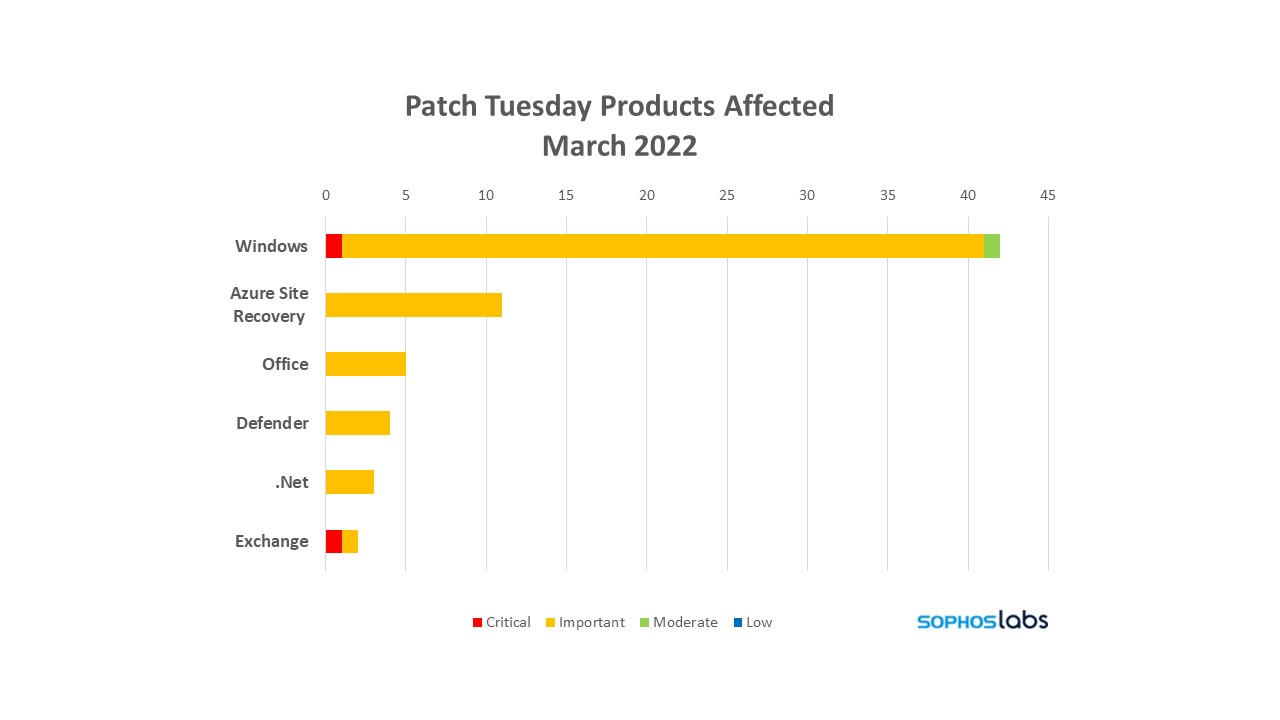
In addition to Microsoft Office, Windows, and Internet Explorer (IE), this month also has fixes for Exchange, Visual Studio, the Xbox app for Windows, Intune, Microsoft Defender, Express Logic, and Azure Site Recovery. Twenty-one of the patches affect the Chromium-based Microsoft Edge browser. No advisories were issued this month.
Below we outline some of the more important or interesting vulnerabilities in this month’s release.
You can find a complete breakdown of the vulnerabilities by severity and impact, product, and exploitability at the end in the Appendix.
Notable Vulnerabilities
Microsoft Exchange Server Remote Code Execution Vulnerability
CVE-2022-23277
One of the two Critical-severity vulnerabilities this month affects Microsoft Exchange. An important mitigating factor for this vulnerability is that authentication is required for any exploitation attempt. However, given what we’ve seen recently around attacks against Exchange vulnerabilities, the Critical severity rating and the nature of the vulnerability makes this an issue that should be patched as soon as possible.
VP9 Video Extensions Remote Code Execution Vulnerability
CVE-2022-24501
The other Critical-class vulnerability this month is a code execution vulnerability affecting the VP9 video codec. There are actually two VP9 Video Extension remote code execution vulnerabilities this month; the other, CVE-2022-24451, is rated Important. The vector for a successful attack on either VP9 vulnerability is a maliciously crafted video file. These VP9 vulnerabilities are also notable because the fixes for these, along with nine other patches addressing various other graphics and videos formats (HEIF, HEVC, and raw), are delivered through the Microsoft Store rather than through Windows Update. There’s information on how to check for those updates in the bulletin.
Remote Desktop Client Remote Code Execution Vulnerability
CVE-2022-21990
This vulnerability affects the Remote Desktop client. An attacker attempting to exploit this vulnerability would need to create a malicious Remote Desktop server and convince the intended target to attempt to connect to it. Once the target connects to the malicious server, the attacker’s code would run in the security context of the operating system, giving the attacker full control. This means this vulnerability can be used as privilege escalation for attackers by luring victims to an RDP server controlled by the attacker and then gaining SYSTEM level control of the victim’s system. It’s also important to note that this vulnerability is listed as “Exploitation Detected,” meaning that there is likely active attack code for this vulnerability. Even though this is rated as merely Important in severity, these factors plus the prevalence of Remote Desktop means this is a high-priority vulnerability for patching.
SMB Server Remote Code Execution Vulnerability
CVE-2022-24508
This vulnerability is notable because it appears likely to have an unauthenticated network-based attack vector, similar to other significant vulnerabilities such as the one that led to the EternalBlue exploit. This vulnerability is also notable because it’s listed as “Exploitation more likely.” While this vulnerability is rated Important rather than Critical, there is no public disclosure, and it’s not currently being exploited, the attack vector and likelihood of exploitation make it a candidate for possible attacks, and so this should be a high priority for patching.
Internet Explorer Security Feature Bypass Vulnerability
CVE-2022-24502
This is a vulnerability that affects IE, but it’s a patch that everyone on Microsoft Windows should apply. The specific components affected are MSHTML and EdgeHTML — browser components that the underlying Windows operating system relies on and can use, even when IE itself is not in active use on the system. This vulnerability is also marked as “Exploitation More Likely,” meaning that this is an important patch for all Windows users to apply.
Sophos protection
|
CVE |
SAV |
XG |
EPIPS |
|
CVE-2022-21990 |
ATK/RDPExpl-A |
59107,59108 |
|
|
CVE-2022-23286 |
Exp/2223286-A |
|
|
|
CVE-2022-24502 |
|
2306882 |
2306882 |
|
CVE-2022-23253 |
|
2306881 |
2306884 |
|
CVE-2022-23299 |
Exp/2223299-A |
|
|
As you can do every month, if you don’t want to wait for your system to pull down the updates itself, you can download them manually from the Windows Update Catalog website. (The exceptions this month, as noted above, are the 11 patches handled via the Microsoft Store.) Run the winver.exe tool to determine which build of Windows 10 or 11 you’re running, then download the Cumulative Update package for your particular system architecture and build number.
Vulnerability Severity and Impact
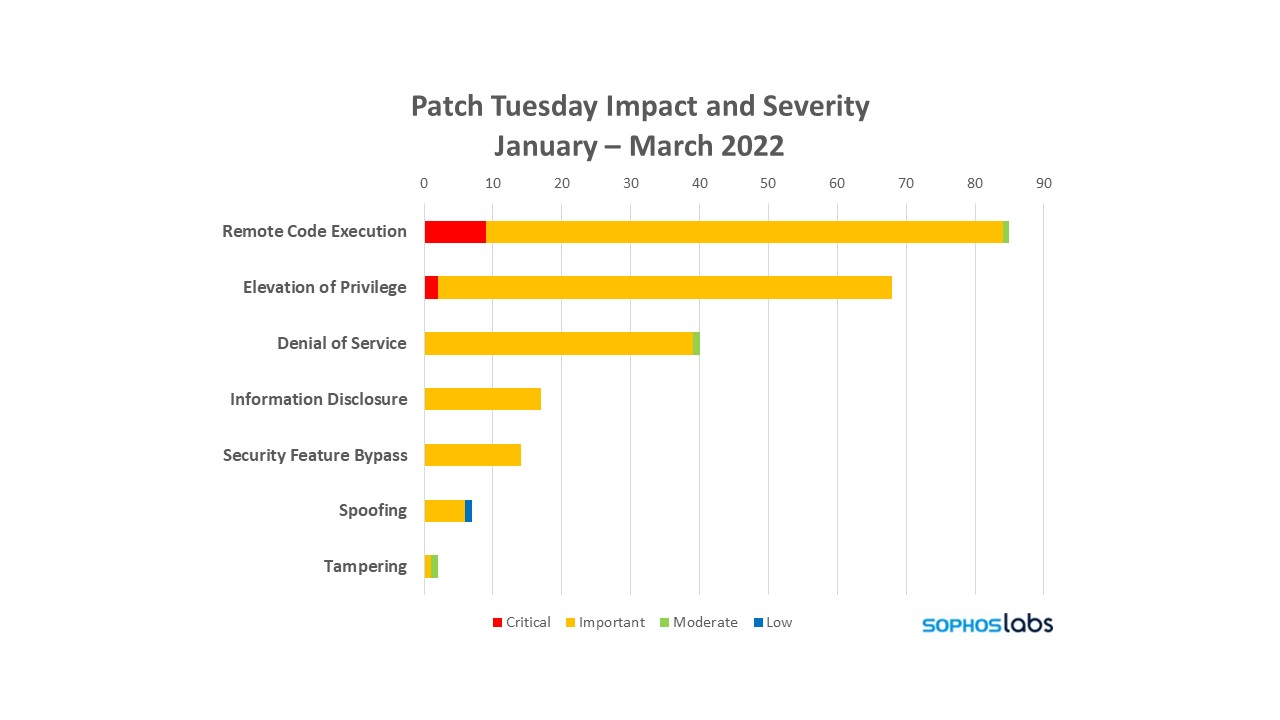
Below is a breakdown of the vulnerabilities by impact and severity.
Remote code execution (RCE)
Critical:
- CVE-2022-23277 Microsoft Exchange Server Remote Code Execution Vulnerability
- CVE-2022-24501 VP9 Video Extensions Remote Code Execution Vulnerability
Important:
- CVE-2022-22006 HEVC Video Extensions Remote Code Execution Vulnerability
- CVE-2022-22007 HEVC Video Extensions Remote Code Execution Vulnerability
- CVE-2022-23265 Microsoft Defender for IoT Remote Code Execution Vulnerability
- CVE-2022-23282 Paint 3D Remote Code Execution Vulnerability
- CVE-2022-23294 Windows Event Tracing Remote Code Execution Vulnerability
- CVE-2022-23295 Raw Image Extension Remote Code Execution Vulnerability
- CVE-2022-23300 Raw Image Extension Remote Code Execution Vulnerability
- CVE-2022-23301 HEVC Video Extensions Remote Code Execution Vulnerability
- CVE-2022-24451 VP9 Video Extensions Remote Code Execution Vulnerability
- CVE-2022-24452 HEVC Video Extensions Remote Code Execution Vulnerability
- CVE-2022-24453 HEVC Video Extensions Remote Code Execution Vulnerability
- CVE-2022-24456 HEVC Video Extensions Remote Code Execution Vulnerability
- CVE-2022-24457 HEIF Image Extensions Remote Code Execution Vulnerability
- CVE-2022-24461 Microsoft Office Visio Remote Code Execution Vulnerability
- CVE-2022-24467 Azure Site Recovery Remote Code Execution Vulnerability
- CVE-2022-24468 Azure Site Recovery Remote Code Execution Vulnerability
- CVE-2022-24470 Azure Site Recovery Remote Code Execution Vulnerability
- CVE-2022-24471 Azure Site Recovery Remote Code Execution Vulnerability
- CVE-2022-24509 Microsoft Office Visio Remote Code Execution Vulnerability
- CVE-2022-24510 Microsoft Office Visio Remote Code Execution Vulnerability
- CVE-2022-24512 .NET Framework Remote Code Execution Vulnerability
- CVE-2022-24517 Azure Site Recovery Remote Code Execution Vulnerability
- CVE-2022-24520 Azure Site Recovery Remote Code Execution Vulnerability
- CVE-2022-23285 Remote Desktop Client Remote Code Execution Vulnerability
- CVE-2022-24508 SMB Server Remote Code Execution Vulnerability
- CVE-2022-21990 Remote Desktop Client Remote Code Execution Vulnerability
Elevation of privilege (EoP),
- CVE-2022-21967 Windows XBox Elevation of Privilege Vulnerability
- CVE-2022-23266 Microsoft Defender for IOT Elevation of Privilege Vulnerability
- CVE-2022-23275 Microsoft Express Logic Elevation of Privilege Vulnerability
- CVE-2022-23283 Windows ALPC Elevation of Privilege Vulnerability
- CVE-2022-23284 Windows Print Spooler Elevation of Privilege Vulnerability
- CVE-2022-23287 Windows ALPC Elevation of Privilege Vulnerability
- CVE-2022-23288 Windows DWM Core Library Elevation of Privilege Vulnerability
- CVE-2022-23290 Windows COM Elevation of Privilege Vulnerability
- CVE-2022-23291 Windows DWM Core Library Elevation of Privilege Vulnerability
- CVE-2022-23293 Windows Fast FAT File System Driver Elevation of Privilege Vulnerability
- CVE-2022-23296 Windows Installer Elevation of Privilege Vulnerability
- CVE-2022-23298 Windows NT OS Kernel Elevation of Privilege Vulnerability
- CVE-2022-24454 Windows Security Support Provider Interface Elevation of Privilege Vulnerability
- CVE-2022-24459 Windows Fax and Scan Service Elevation of Privilege Vulnerability
- CVE-2022-24460 Tablet Windows User Interface Application Elevation of Privilege Vulnerability
- CVE-2022-24469 Azure Site Recovery Elevation of Privilege Vulnerability
- CVE-2022-24505 Windows ALPC Elevation of Privilege Vulnerability
- CVE-2022-24506 Azure Site Recovery Elevation of Privilege Vulnerability
- CVE-2022-24513 Visual Studio Elevation of Privilege Vulnerability
- CVE-2022-24515 Azure Site Recovery Elevation of Privilege Vulnerability
- CVE-2022-24518 Azure Site Recovery Elevation of Privilege Vulnerability
- CVE-2022-24519 Azure Site Recovery Elevation of Privilege Vulnerability
- CVE-2022-23286 Windows Cloud Files Mini Filter Driver Elevation of Privilege Vulnerability
- CVE-2022-23299 Windows PDEV Elevation of Privilege Vulnerability
- CVE-2022-24507 Windows Ancillary Function Driver for WinSock Elevation of Privilege Vulnerability
Denial of service (DoS)
Important:
- CVE-2022-21973 Windows Media Center Update Denial of Service Vulnerabilty
- CVE-2022-21975 Windows Hyper-V Denial of Service Vulnerability
- CVE-2022-23267 .NET Core Denial of Service Vulnerability
- CVE-2022-24464 NET Core and Visual Studio Denial of Service Vulnerability
- CVE-2022-23253 Point-to-Point Tunneling Protocol Denial of Service Vulnerability
Moderate:
- CVE-2022-24455 Windows CD-ROM Driver Elevation of Privilege Vulnerability
Information disclosure
- CVE-2022-21977 Media Foundation Information Disclosure Vulnerability
- CVE-2022-22010 Media Foundation Information Disclosure Vulnerability
- CVE-2022-23281 Windows Common Log File System Driver Information Disclosure Vulnerability
- CVE-2022-23297 Windows Kernel Memory Information Disclosure Vulnerability
- CVE-2022-24503 Remote Desktop Protocol Client Information Disclosure Vulnerability
Security feature bypass
- CVE-2022-24462 Microsoft Word Security Feature Bypass Vulnerability
- CVE-2022-24465 Microsoft Intune Security Feature Bypass Vulnerability
- CVE-2022-24502 Internet Explorer Security Feature Bypass Vulnerability
Spoofing
- CVE-2022-23278 Microsoft Defender for Endpoint Spoofing Vulnerability
- CVE-2022-24458 Microsoft Defender for Endpoint Spoofing Vulnerability
- CVE-2022-24463 Microsoft Exchange Server Spoofing Vulnerability
Tampering
- CVE-2022-24511 Microsoft Office Word Tampering Vulnerability
Below are the vulnerabilities that have been publicly disclosed:
- CVE-2022-24459 Windows Fax and Scan Service Elevation of Privilege Vulnerability
- CVE-2022-24512 .NET Framework Remote Code Execution Vulnerability
- CVE-2022-21990 Remote Desktop Client Remote Code Execution Vulnerability
Exploitability Indexes
Below are the vulnerabilities marked as “Exploitation more likely”.
Latest software:
- CVE-2022-23253 Point-to-Point Tunneling Protocol Denial of Service Vulnerability
- CVE-2022-23286 Windows Cloud Files Mini Filter Driver Elevation of Privilege Vulnerability
- CVE-2022-23299 Windows PDEV Elevation of Privilege Vulnerability
- CVE-2022-24507 Windows Ancillary Function Driver for WinSock Elevation of Privilege Vulnerability
- CVE-2022-23277 Microsoft Exchange Server Remote Code Execution Vulnerability
- CVE-2022-23294 Windows Event Tracing Remote Code Execution Vulnerability
- CVE-2022-23285 Remote Desktop Client Remote Code Execution Vulnerability
- CVE-2022-24508 SMB Server Remote Code Execution Vulnerability
- CVE-2022-24502 Internet Explorer Security Feature Bypass Vulnerability
- CVE-2022-23300 Raw Image Extension Remote Code Execution Vulnerability
Older software:
- CVE-2022-23253 Point-to-Point Tunneling Protocol Denial of Service Vulnerability
- CVE-2022-23286 Windows Cloud Files Mini Filter Driver Elevation of Privilege Vulnerability
- CVE-2022-23299 Windows PDEV Elevation of Privilege Vulnerability
- CVE-2022-24507 Windows Ancillary Function Driver for WinSock Elevation of Privilege Vulnerability
- CVE-2022-23277 Microsoft Exchange Server Remote Code Execution Vulnerability
- CVE-2022-23294 Windows Event Tracing Remote Code Execution Vulnerability
- CVE-2022-23285 Remote Desktop Client Remote Code Execution Vulnerability
- CVE-2022-24508 SMB Server Remote Code Execution Vulnerability
- CVE-2022-24502 Internet Explorer Security Feature Bypass Vulnerability
Products Affected
.NET
- CVE-2022-23267 .NET Core Denial of Service Vulnerability
- CVE-2022-24512 .NET Framework Remote Code Execution Vulnerability
- CVE-2022-24464 NET Core and Visual Studio Denial of Service Vulnerability
Azure Site Recovery
- CVE-2022-24469 Azure Site Recovery Elevation of Privilege Vulnerability
- CVE-2022-24506 Azure Site Recovery Elevation of Privilege Vulnerability
- CVE-2022-24515 Azure Site Recovery Elevation of Privilege Vulnerability
- CVE-2022-24518 Azure Site Recovery Elevation of Privilege Vulnerability
- CVE-2022-24519 Azure Site Recovery Elevation of Privilege Vulnerability
- CVE-2022-24467 Azure Site Recovery Remote Code Execution Vulnerability
- CVE-2022-24468 Azure Site Recovery Remote Code Execution Vulnerability
- CVE-2022-24470 Azure Site Recovery Remote Code Execution Vulnerability
- CVE-2022-24471 Azure Site Recovery Remote Code Execution Vulnerability
- CVE-2022-24517 Azure Site Recovery Remote Code Execution Vulnerability
- CVE-2022-24520 Azure Site Recovery Remote Code Execution Vulnerability
Microsoft Defender
- CVE-2022-23278 Microsoft Defender for Endpoint Spoofing Vulnerability
- CVE-2022-24458 Microsoft Defender for Endpoint Spoofing Vulnerability
- CVE-2022-23266 Microsoft Defender for IOT Elevation of Privilege Vulnerability
- CVE-2022-23265 Microsoft Defender for IoT Remote Code Execution Vulnerability
Microsoft Exchange
- CVE-2022-23277 Microsoft Exchange Server Remote Code Execution Vulnerability
- CVE-2022-24463 Microsoft Exchange Server Spoofing Vulnerability
Microsoft Express Logic
- CVE-2022-23275 Microsoft Express Logic Elevation of Privilege Vulnerability
Microsoft Internet Explorer
- CVE-2022-24502 Internet Explorer Security Feature Bypass Vulnerability
Microsoft Intune
- CVE-2022-24465 Microsoft Intune Security Feature Bypass Vulnerability
Microsoft Office
- CVE-2022-24461 Microsoft Office Visio Remote Code Execution Vulnerability
- CVE-2022-24509 Microsoft Office Visio Remote Code Execution Vulnerability
- CVE-2022-24510 Microsoft Office Visio Remote Code Execution Vulnerability
- CVE-2022-24511 Microsoft Office Word Tampering Vulnerability
- CVE-2022-24462 Microsoft Word Security Feature Bypass Vulnerability
Microsoft Windows
- CVE-2022-24457 HEIF Image Extensions Remote Code Execution Vulnerability
- CVE-2022-22006 HEVC Video Extensions Remote Code Execution Vulnerability
- CVE-2022-22007 HEVC Video Extensions Remote Code Execution Vulnerability
- CVE-2022-23301 HEVC Video Extensions Remote Code Execution Vulnerability
- CVE-2022-24452 HEVC Video Extensions Remote Code Execution Vulnerability
- CVE-2022-24453 HEVC Video Extensions Remote Code Execution Vulnerability
- CVE-2022-24456 HEVC Video Extensions Remote Code Execution Vulnerability
- CVE-2022-21977 Media Foundation Information Disclosure Vulnerability
- CVE-2022-22010 Media Foundation Information Disclosure Vulnerability
- CVE-2022-23282 Paint 3D Remote Code Execution Vulnerability
- CVE-2022-23253 Point-to-Point Tunneling Protocol Denial of Service Vulnerability
- CVE-2022-23295 Raw Image Extension Remote Code Execution Vulnerability
- CVE-2022-23300 Raw Image Extension Remote Code Execution Vulnerability
- CVE-2022-21990 Remote Desktop Client Remote Code Execution Vulnerability
- CVE-2022-23285 Remote Desktop Client Remote Code Execution Vulnerability
- CVE-2022-24503 Remote Desktop Protocol Client Information Disclosure Vulnerability
- CVE-2022-24508 SMB Server Remote Code Execution Vulnerability
- CVE-2022-24460 Tablet Windows User Interface Application Elevation of Privilege Vulnerability
- CVE-2022-24501 VP9 Video Extensions Remote Code Execution Vulnerability
- CVE-2022-24451 VP9 Video Extensions Remote Code Execution Vulnerability
- CVE-2022-23283 Windows ALPC Elevation of Privilege Vulnerability
- CVE-2022-23287 Windows ALPC Elevation of Privilege Vulnerability
- CVE-2022-24505 Windows ALPC Elevation of Privilege Vulnerability
- CVE-2022-24507 Windows Ancillary Function Driver for WinSock Elevation of Privilege Vulnerability
- CVE-2022-24455 Windows CD-ROM Driver Elevation of Privilege Vulnerability
- CVE-2022-23286 Windows Cloud Files Mini Filter Driver Elevation of Privilege Vulnerability
- CVE-2022-23290 Windows COM Elevation of Privilege Vulnerability
- CVE-2022-23281 Windows Common Log File System Driver Information Disclosure Vulnerability
- CVE-2022-23288 Windows DWM Core Library Elevation of Privilege Vulnerability
- CVE-2022-23291 Windows DWM Core Library Elevation of Privilege Vulnerability
- CVE-2022-23294 Windows Event Tracing Remote Code Execution Vulnerability
- CVE-2022-23293 Windows Fast FAT File System Driver Elevation of Privilege Vulnerability
- CVE-2022-24459 Windows Fax and Scan Service Elevation of Privilege Vulnerability
- CVE-2022-21975 Windows Hyper-V Denial of Service Vulnerability
- CVE-2022-23296 Windows Installer Elevation of Privilege Vulnerability
- CVE-2022-23297 Windows Kernel Memory Information Disclosure Vulnerability
- CVE-2022-21973 Windows Media Center Update Denial of Service Vulnerabilty
- CVE-2022-23298 Windows NT OS Kernel Elevation of Privilege Vulnerability
- CVE-2022-23299 Windows PDEV Elevation of Privilege Vulnerability
- CVE-2022-23284 Windows Print Spooler Elevation of Privilege Vulnerability
- CVE-2022-24454 Windows Security Support Provider Interface Elevation of Privilege Vulnerability
Visual Studio
- CVE-2022-24513 Visual Studio Elevation of Privilege Vulnerability
Xbox
- CVE-2022-21967 Windows XBox Elevation of Privilege Vulnerability