SophosLabs, the Sophos Managed Threat Response team, and the SophosAI data science group releases our 2022 Threat Report this morning. This report represents the collective wisdom of our malware analysts, the machine and network forensics specialists, and machine learning experts that make up these core teams within Sophos, and offers some analysis of the events that transpired in 2021, and how we believe they will help shape the threat landscape in 2022 and beyond.
While you can download and read the report in its entirety, we wanted to share some of the insights covered in the report to give you a taste.
The report is organized into five parts, in which we cover the ransomware epidemic and its aftermath, trends in conventional malware that targets Windows computers, malware on mobile platforms, security threats to infrastructure, and a section that covers the field of artificial intelligence, and how it applies to the practice of information security.
The fight against ransomware
Our ransomware coverage in 2021 was led by a hybrid team of analysts, some of whom reverse-engineer and study malware behavior, and others who step in to intervene in ransomware attacks targeting customers. The latter group, known as Sophos Rapid Response, had a busy year dealing with a variety of ransomware families, and the threat actor groups whose work is to break in to organizations and deliver that ransomware into their networks.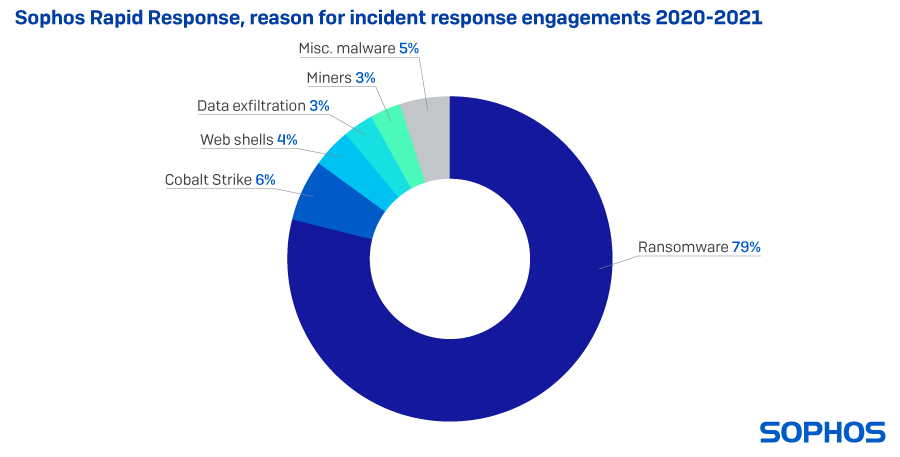 The vast majority of these customer engagements involved ransomware in 2021, but we were also asked to step in to help customers with cases involving Cobalt Strike, a commercially-marketed tool used legitimately by professional penetration testers and ‘red teams’ whose source code was leaked online in 2020. Criminals now routinely abuse these tools by delivering them as malware payloads. As a result of several high-profile vulnerabilities in Microsoft Exchange, we were called upon to deal with many more web shells than normal in 2020.
The vast majority of these customer engagements involved ransomware in 2021, but we were also asked to step in to help customers with cases involving Cobalt Strike, a commercially-marketed tool used legitimately by professional penetration testers and ‘red teams’ whose source code was leaked online in 2020. Criminals now routinely abuse these tools by delivering them as malware payloads. As a result of several high-profile vulnerabilities in Microsoft Exchange, we were called upon to deal with many more web shells than normal in 2020.
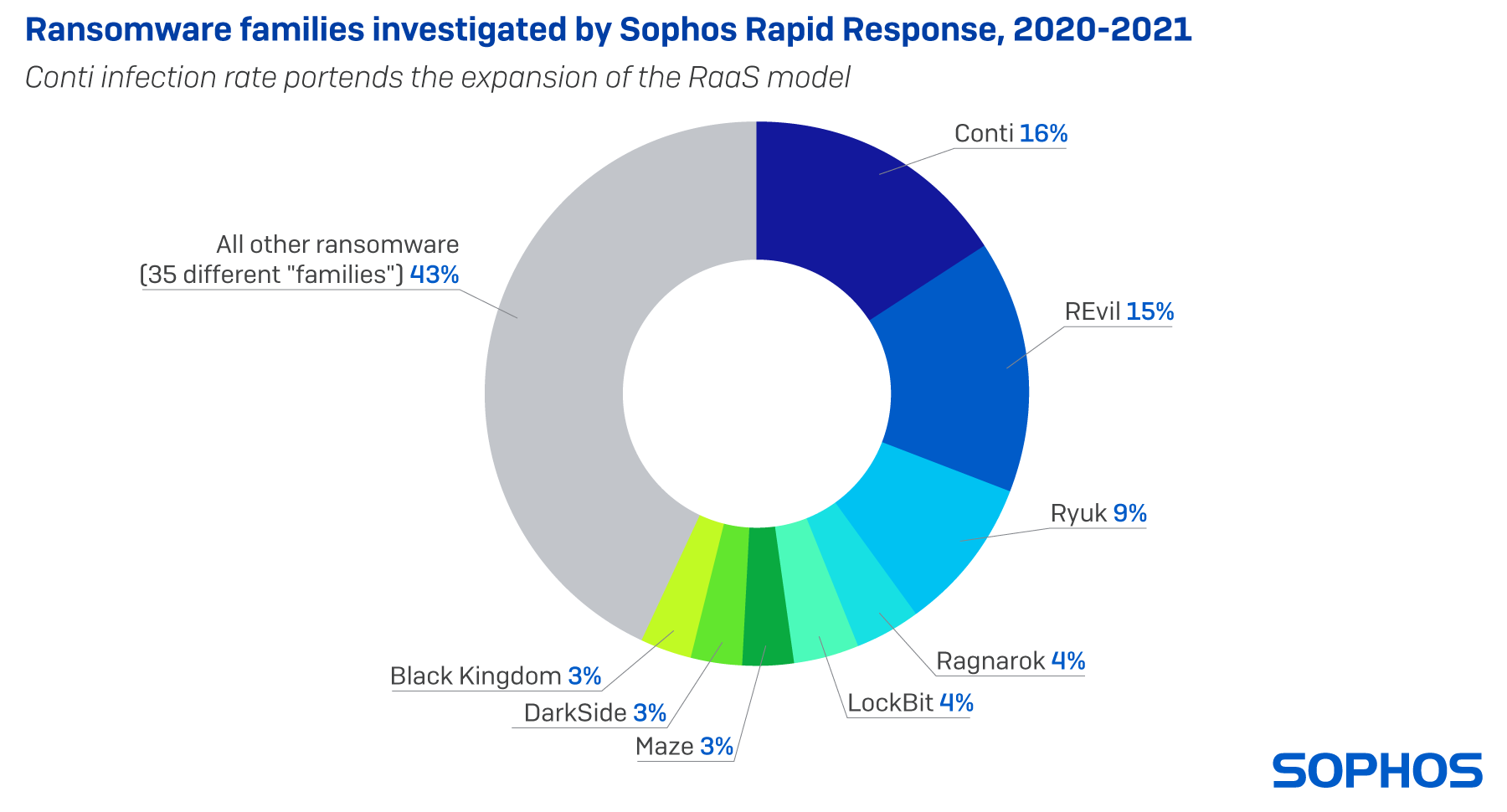 But the vast majority of cases involved ransomware, and among those, the Conti and REvil families were most frequently involved. Both Conti and REvil pioneered and developed the ransomware-as-a-service business model, where a small core team of developers built the ransomware itself, and a larger group of affiliates acted as the delivery mechanism, actively breaking in to networks by any means available: Brute-force attacks against internet-facing services; exploits of vulnerable software; and occasionally, by obtaining legitimate credentials from ‘initial access brokers,’ a type of criminal service provider.
But the vast majority of cases involved ransomware, and among those, the Conti and REvil families were most frequently involved. Both Conti and REvil pioneered and developed the ransomware-as-a-service business model, where a small core team of developers built the ransomware itself, and a larger group of affiliates acted as the delivery mechanism, actively breaking in to networks by any means available: Brute-force attacks against internet-facing services; exploits of vulnerable software; and occasionally, by obtaining legitimate credentials from ‘initial access brokers,’ a type of criminal service provider.
Countering attackers at every turn
The SophosLabs team were called upon to improve our behavioral detection capabilities in 2021, and in so doing, we found that dual-use attack tools like Cobalt Strike were most frequently a component of the kinds of hands-on-keyboards attacks preferred by ransomware groups. But we also started to see other threat actors take advantage of a wide variety of commercial software and utilities designed for IT administrators or security professionals.
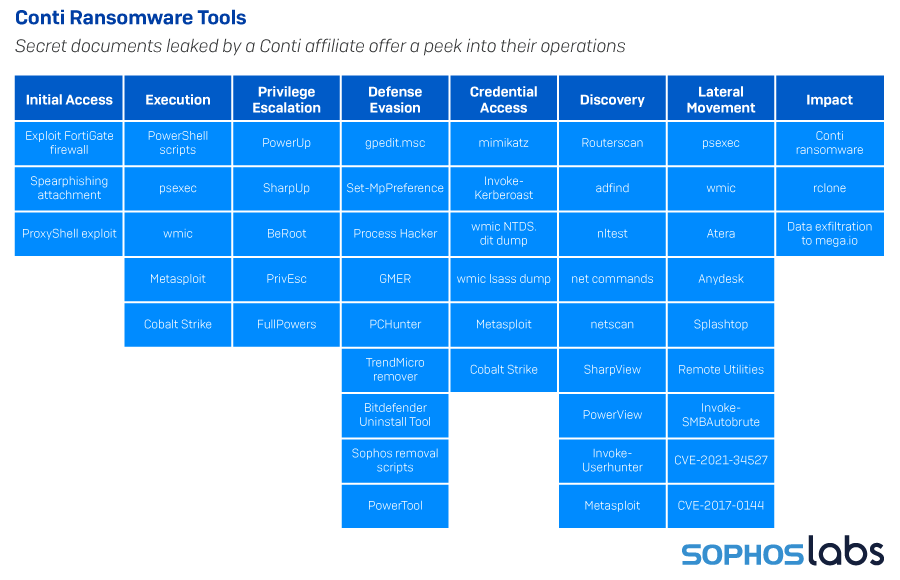 When an affiliate customer of the Conti ransomware leaked a playbook designed to help affiliates break in and steal information, we not only gained insight into the tools, tactics, and procedures of the Conti affiliates — it answered an important question about why, when we knew so many different groups had been active as Conti affiliates, their TTPs remains strikingly similar.
When an affiliate customer of the Conti ransomware leaked a playbook designed to help affiliates break in and steal information, we not only gained insight into the tools, tactics, and procedures of the Conti affiliates — it answered an important question about why, when we knew so many different groups had been active as Conti affiliates, their TTPs remains strikingly similar.
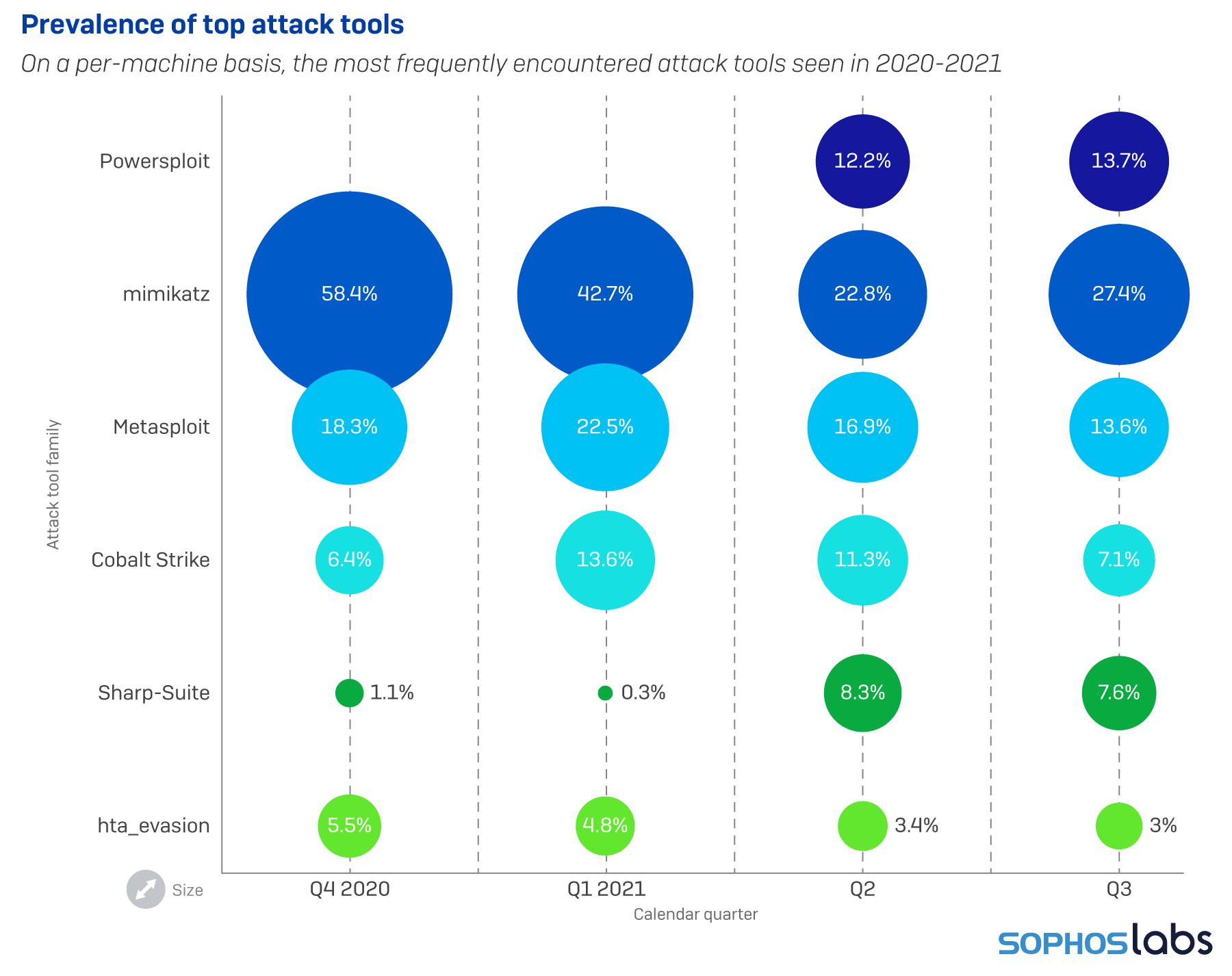 Among the attacker tools most commonly seen by our scanners, the mimikatz password sniffing and cracking tool was the one we most frequently discovered. Both the Metasploit framework and components of Cobalt Strike also came into play quite often, usually alongside a wide variety of other tools. Sophos currently tracks detections of more than 180 different software packages that fall into this grey area between explicitly malicious and completely benign software.
Among the attacker tools most commonly seen by our scanners, the mimikatz password sniffing and cracking tool was the one we most frequently discovered. Both the Metasploit framework and components of Cobalt Strike also came into play quite often, usually alongside a wide variety of other tools. Sophos currently tracks detections of more than 180 different software packages that fall into this grey area between explicitly malicious and completely benign software.
Android and iOS still under threat
Mobile platforms are increasingly under threat as we impart more of our daily computing tasks to these pocket computers. Scams and fraud account for a large part of the attacks we see on both Apple’s and Alphabet’s mobile platforms. Some of these are delivered by the platforms’ own app stores, but we’ve also seen a rise in malware that originates with a text message over SMS or a mobile chat platform like Telegram. Users on mobile devices often cannot tell where shortened links sent via these platforms will take them, and may lead the recipients into trouble.
For more on these stories, and other analysis of the threat landscape, check out the Sophos 2022 Threat Report.
