Have you ever had an angry customer bellow the dreaded words, “Just you wait, I’m going to report you to your manager”, or something along those lines?
We’re willing to bet that you have, and word on the street in the UK is that customer complaints, supposedly intensified by coronavirus-related frustrations, are at worryingly high levels right now.
And when someone does say, “I’m going to escalate this”, which is a confrontational, war-like expression at the best of times, it immediately becomes an uncertain, and often unpleasant, waiting game.
Will the blustery behaviour of ranting at you over the phone (or via IM, or on the support forum, or in a webchat session) provide the cathartic release the customer wanted, and bring their frustration to an end?
Or will you wake up tomorrow to a flurry of emails from your manager, or from HR, or from both, telling you about a formal complaint that’s just come in?
Well, over the past 24 hours, we, and many of our colleagues, have been on the receiving end of an email scam that preys on exactly these fears.
(At Naked Security, we receive emails for several different mail aliases along with our own personal addresses, so these bogus “Customer Complaints” have really been pouring in to our mailbox!)
Guilt + Fear = Haste
The goal of these cybercriminals is to make you feel guilty, and to convince you that through inaction on your part, you have caused serious inconvenience not only to the company as a whole, but also to someone more important than you in the organisation:
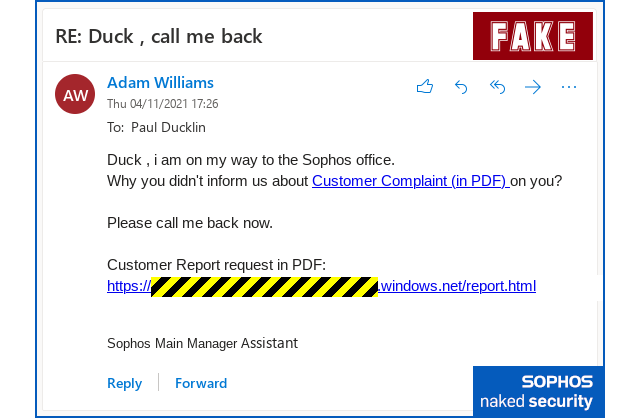
Technically, this is a targeted attack, known in the jargon as spear-phishing, because it does its best to greet you by name and to pretend to come from a manager in your company.
That makes it much more believable that an impersonal “Dear Colleague” or just a plain old “Hello”.
Yet this sort of targeting is technically trivial to do for anyone who has ever received (or acquired a copy of) an email sent by you at any time in the past.
For example, my emails almost always contain a line of text in the headers that looks like this:
From: Paul Ducklin <duck@sophos.com>
From that text alone, it’s a fair guess that:
- My email client addresses me as Paul Ducklin.
- My colleagues call me Duck. (And other things, but Duck is one.)
- My employer is an organisation called Sophos.
After all, once you’ve filtered out outlook.com, gmail.com, yahoo.com and other domains associated with well-known webmail services, the email addresses left behind are quite likely to be company-related email identities.
Junior staff at particular risk
As you can see, spear-phishing doesn’t have to be a high-tech cybercrime that only ever targets high-fliers and individuals worth spending lots of time researching, stalking, pretexting and socially engineering for personal details.
Even if all the crooks had was a text string of the form $YOURNAME <$YOU@$BIZNAME.example>, it would be easy for crooks to fit it to a template like this:
Attention: $YOURNAME Dear $YOU, You're in big trouble. I suggest you bring your coat when you come to the meeting. Yours sincerely, S. O. Meone $BIZNAME Outsourcing Manager
That alone would be enough to make it into the sort of message you might be inclined to take seriously, especially if you work for an outsourced part of your company, and don’t usually liaise directly with higher-ups in the main company itself.
Worse, of course, is that junior staff in commonly outsourced jobs such as first-line support, where time pressure is always high, are the most likely to have been threatened with complaints by aggressive callers determined to get their way.
And, let’s be perfectly honest, if you’ve ever worked in support, you’ll rarely ever have “reported yourself to management” when a caller shouted at you and complained, unless the call was so aggressive or threatening that you wanted to ensure it was placed on the record for your own safety.
You just assume that the complaints that they threatened to send won’t materalise, although you also know that sometimes they do.
In other words, receiving an email from a “colleague” whom you don’t know, and who doesn’t know you, but who seems to have been dragged into a customer “dispute” that you weren’t even aware of yet…
…well, it’s pretty much par for the course if you work in front-line support or a busy call centre.
In fact, one of the variants of this scam we received early on took exactly that approach, signing off as someone in the outsourcing team.
We aren’t sure whether the word cpomplaint in the subject line was a simple typo, because it was never repeated, or a deliberate response to some recipients temporarily blocklisting the word complaint in their email filters:

Watch for mistakes
The good news in this case is that the crooks weren’t on top of their game in the first of these emails we received, because the link took us here:

It looks as though they’d mixed up the emails and the web links of two different spear-phishing campaigns, one to do with customer complaints, and the other to do with accounts receivable or finance.
Also, the website was hosted on a Microsoft cloud service, as was obvious from the URL, but had Google Drive branding on the page.
But the criminals soon got their act back together, sending several more emails with a similarly threatening tone but with rather more believable links.
The next few phishing messages ripped off Adobe’s logo, presumably knowing that it’s a good visual match with the PDF file extension, and offered us a copy of the alleged “complaint”:

If you download the file, it turns out not to be a PDF, but it isn’t the usual sort of well-known suspicious substitute that the crooks often use, such as a VBS file (Visual Basic Script) or a JS file (JavaScript) file.
This one is a Microsoft App Bundle.
Like .apk files for Android or .pkg files for macOS, .appxbundle files are Microsoft’s answer to providing a single download for all sorts of platforms and devices.
You need to remember that these files are really just good old .EXE files in disguise, but many Windows users may not be familiar with them yet, especially if they’ve never had reason to download work apps from the Microsoft Store.
There are numerous file formats used by so-called Univeral Windows Platform (UWP) apps. UWP packages are a bit like Apple’s “fat binaries” or Android’s multi-platform APK files, built and provided by vendors so that you don’t need to remember whether you are 32-bit or 64-bit, or if you have an Intel/AMD or ARM processor, every time you install the same program to a new device. File extensions to watch out for include: .msix, .appx, .msixbundle and .appxbundle. If you aren’t familiar with these, think of them as wolf-in-sheep’s-clothing files and avoid them unless they come from a known and trusted source.
Adobe brand hijack
The App Bundle itself, if you allow it to download and run, continues hijacking Adobe’s brand by claiming to be a needed component:

As you can see, the file is reported as a Trusted App, with a vendor name given as Adobe Inc., but that’s as bogus as the original email.
If you click on [Trusted App], you’ll see that what purports to be a software bundle from Adobe in the USA has an unlikely digital signature from an accounting firm in South-East England.
We’re guessing that the crooks acquired a copy of this company’s signing key, or bought it on the dark web, as the after-effect of a cyberintrusion at that company. Many cyberattacks these days include a stage where the crooks steal as many useful-looking files as they can along the way. Often, those stolen files are used by ransomware criminals as extra leverage to blackmail you into paying “hush money”. But data from thefts of this sort has many more uses than just extortion, and files such as signing keys or password lists have value of their own when sold individually for further cybercriminality.
What happens next?
We won’t describe the technical details of the malware here – for the step-by-step details of how it performs its treachery in multiple stages, see this Twitter thread from @SophosLabs:
Hey everyone. @threatresearch here with a little news about how my day's been going.
Seems a lot of people are dealing with an outbreak of #BazarBackdoor that starts with an email that sounds like it's coming from someone who is annoyed you didn't report a complaint about you. pic.twitter.com/EYrQHBAiXO
— Sophos X-Ops (@SophosXOps) November 4, 2021
Amongst the actions that the malware performed immediately were:
- Telling the crooks your external IP address by consulting a public “find my IP” server. Ironically, the crooks ought to be able to tell your external IP number anyway, because that’s where the callhome data from their malware will originate from. Nevertheless, they make double-sure by finding out how your own computer thinks it connected to the internet.
- Reporting the specifications of your computer. The crooks want to know how much disk space you have available, how much RAM you’ve got, and what motherboard you’re using.
Like most backdoor programs of this sort, also known as bots or zombies, this malware also includes a “feature” to download and install yet more malware.
In other words, if you are unfortunate enough to get infected, this may look and feel like the end of an attack chain…
…when in fact it is merely the begining of the next one.
And as pedestrian as some of the data that this zombie malware steals at the start, such as how much RAM you’ve got, it’s an excellent and simple hint to the criminals of the type of tasks your now-backdoored computer is best suited to.
For example, some cryptocurrency mining processes (and various types of password cracking operation) work best with lots of free disk space, but don’t need a lot of CPU power or RAM; some want as much processing power as they can take; and others run faster the more memory they can use.
Often, zombies also try to estimate your network speed, so that the crooks who control the malware know which parts of their botnet are best suited to leasing ourtfor DDoS (distributed denial of service) attacks, or for sending spam emails containing the next wave of malware.
What to do?
- Stop. Think. Connect. That’s the motto of Cybersecurity Awareness Month, which happens in October, but acts as a reminder of cyberecurity precautions you can take all year round. Never let yourself be pressured or threatened into acting in haste, because that’s exactly what the crooks are hoping you will do. This scam is full of mistakes (spelling, grammar, incorrect web links, unlikely file downloads, digital signatures that simply don’t look right) that you would expect to notice on a good day, but could easily miss if you are acting in haste. But the signs are all there, even if you aren’t technical yourself, that this email simply doesn’t add up, and is fake.
- Always use official channels for communicating with your staff. If you’re a manager, and you really are dealing with an emergency such as a customer complaint, never take IT shortcuts or try to cajole your staff into breaking company rules about official communications. Make it clear that if there is an official complaint, then there will be an official sequence of steps that will be followed. That way, if cybercrimals try to talk your staff into taking unusual steps or downloading unexpected files, even your junior staff will have the knowledge and the self-confidence not to do it.
- Set up a single, easy-to-remember contact point for security reports. Something as simple as a
cybersecurity@company.exampleemail address, where any staff member can report anything that doesn’t add up, from a sneaky-sounding phone call to an unlikely email request, is perfect for this. Just make sure that you treat your staff with respect if they report messages that turn out to be false alarms. Get your security team to work on the principle that there is no such thing as a stupid question, only a stupid answer. - If you didn’t know about App Bundles, add them to your cybersecurity knowledgebase. For example, if you’re routinely blocking
.EXEfiles at your web gateway, consider blocking.appxbundleand friends, too (see above). Also review your email attachment filtering rules, too. Less, when it comes to email, is more. - Don’t be seduced by on-screen security promises and visual indicators. In the same way that HTTPS and a padlock on a website doesn’t mean that the website is telling the truth, so the remark about the download being a Trusted App doesn’t count for much when it comes to what the app actually does, given that all the digital signature really tells you is that the app was signed by someone’s cryptographic key. (In this case, clicking
[Trusted App]to see who signed it does help you spot the scam, because of the obvious mismatch between the signer’s name and the app’s claim to be from Adobe.)
By the way, you can extend the last warning above to all interactions in your digital life.
In particular, when you get a message from a social media friend, via a private group that you belong to, and that you are therefore inclined to trust straight off the bat…
…remember that you don’t actually know that the message came from your friend, merely that it came from your friend’s account.
If in doubt, don’t give it out!
Sophos products detect and block the malware in this attack as Troj/MSIL-RXW (on-demand and on-access scanning on all laptop, desktop and server platforms), and as Mem/BazarLd-C (behavioural detection on Windows), if you would like to check your logs.
Sophos web filtering components also identify the download pages and the command-and-control (callhome) servers as high risk sites in the SPYWARE_AND_MALWARE/MALWARE_REPOSITORY and COMMAND_AND_CONTROL/MALWARE_CALLHOME categories respectively.

Jeff
Good article, thanks! I think your article’s email is probably the best example I’ve personally seen of trying to create the need for haste. It kinda hits you in the gut. Having exposure to the example (and sharing it with others), and your suggestions about what to do, are good tools to help prevent falling for these.
Paul Ducklin
It’s a pleasure. Glad you enjoyed it and found it useful. As the article says, the first sample I received apparently related to a different scam theme (payments) and had Google branding although it was hosted on a Microsoft server, but I haven’t seen any sample emails that tie into that one…
Nathanael Tan
Always love such content and the nice humour element put into the article:
My colleagues call me Duck. (And other things, but Duck is one.)
It sounds like they definitely call you other names, as if Duck isn’t worse enough already hahahaha
As someone with prior CRM knowledge and a great plan to dive deeper into it and see where it can improve, this brought me a great fresh perspective as I never thought CRM would be a platform (not necessarily the online provider, but the very essence of managing the relationship between the company and its clients) for social engineering as well. If the company I’m going to work for doesn’t use Sophos, I’m so recommending it (or doing the honours myself when I have purchasing power hahaha).
Thank you!
Paul Ducklin
Thanks for your kind words. Glad you liked the article. As you say, social/cultural/ lifestyle/management issues are something that crooks can exploit just as much as exploiting software bugs or technical glitches.
Many recipients of this sort of scam will say, “But that’s obviously a bogus email,” because it doesn’t fit their experience or match how their company works (and it’s good that those people take the time to reach that decision!)
But for some recipients this sort of thing will be perilously close to how CRM problems sometimes do get handled in their company, and if they are more afraid of their outsourcing manager (especially if their own company got the contract by bidding down to a price, and margins are tight) than they are of cybercriminals, you can see exactly why this sort of attack might work.
After all, the criminals don’t have to trick every recipient in every company they send their spams to. For the crooks, just tricking a single person in a few companies is a good start…
Ian Spencer
Thanks for an enlightening article. I hadn’t heard of Microsoft App Bundles (I don’t often use Windows) but will note these in future.
I like the suggestion of having a formal official procedure for dealing with all complaints but this requires “buy-in” from the top and education for managers and staff alike. In too many companies, the official procedures are regarded with distrust and people find ways to avoid giving senior managers an opportunity to threaten them. Senior management must be clear that procedures are for protection of staff, as well as the company, and always support their staff whilst fairly investigating complaints.
Paul Ducklin
+1
I suspect that this attack tells us as much about the nature of contemporary “call centre” business culture as it does about malware. “Your call is so important to us that we have placed it in a lengthy queue to be answered eventually by someone who doesn’t actually work for this company and who is measured on how many calls they can close in a day, so use the holding time to get really angry and prepare a rant you can blast them with because although they are more than smart enough to answer your questions, they are even smarter at coming up with reasons to hang up on you and answer the next call, because that one might be easier to close than yours, so it will help them hit their targets and not get into trouble with their boss. Please continue to hold. You are 367th in the queue. In the meantime, here is some irritating music, interspersed with ads for the very product you just bought, although the ads might sound as though they are describing a very different and more desirable product than the one you actually received.”
As for App Bundles, they are yet another installation/software delivery “file bundle” format to be aware of, along with EXEs, MSIs, ISOs, ZIPs, cross-platform JARs, Android APKs and many more. In fact, App Bundles (just like Java JARs and Android APKs) *are* ZIP files, with some additional manifest and digital signature files included.
Plus ça change, plus c’est la même chose…
peter
Thanks Duck
that is a classic post
Saved !
Paul Ducklin
Thanks. It’s yet another classic reminder why cybersecurity is a journey and not a destination… the crooks are always coming up with new malware distribution tools and new malware distribution “cover stories”, so we need to be adaptable too…
Ian
It shows that in big companies the employees are not informed by their company who their employers are, and who the boses are who they are working for and do not even know who the people are who employs them. If they knew their names then it may help in situations like that. When I worked for a big printing company, it was the same mentality by the company’s boses back 20 years ago as well, we never knew their names either. The boses don’t know the worker and the worker doesn’t know the boses. LOL.
Richard
As always, great article Duck. You have been awarded the prize of best article of the day. Please click on the link below to accept your prize….
Paul Ducklin
Thanks… that would be a very upbeat follow-up scam. As for these crooks… it seems that their follow-up was to graduate from “You’re in trouble” to “You’ve been fired”, with a subsequent wave of scams telling people to read their termination letters. Happy days ☹️