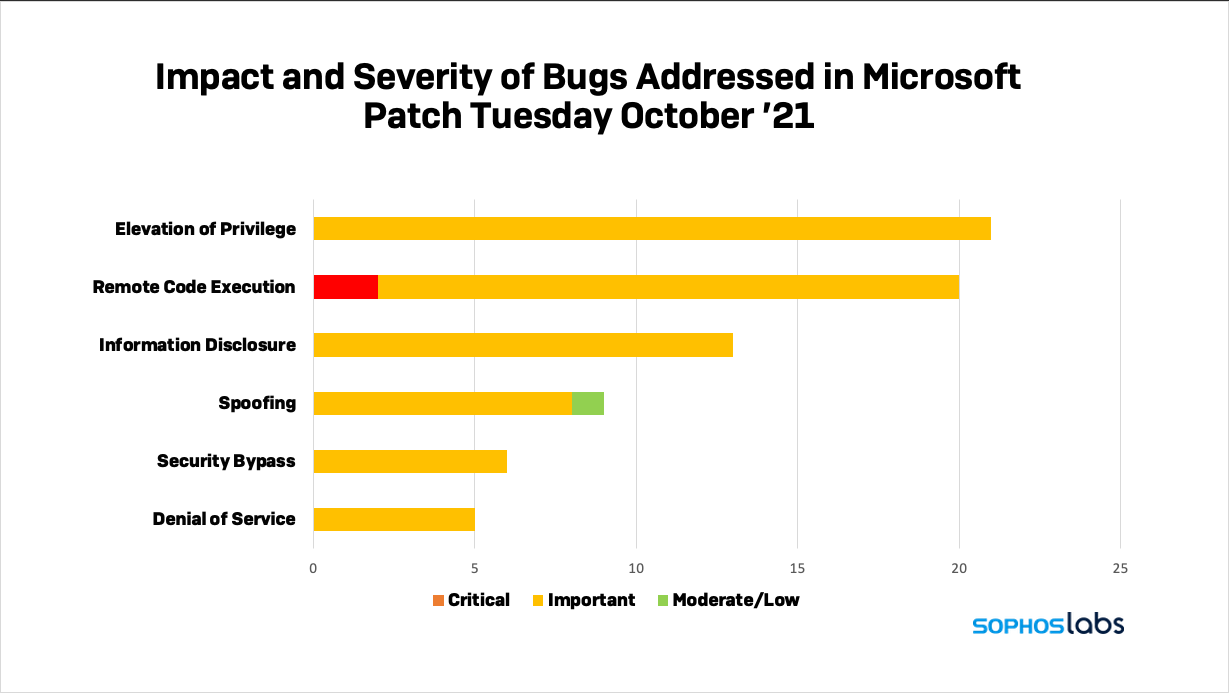
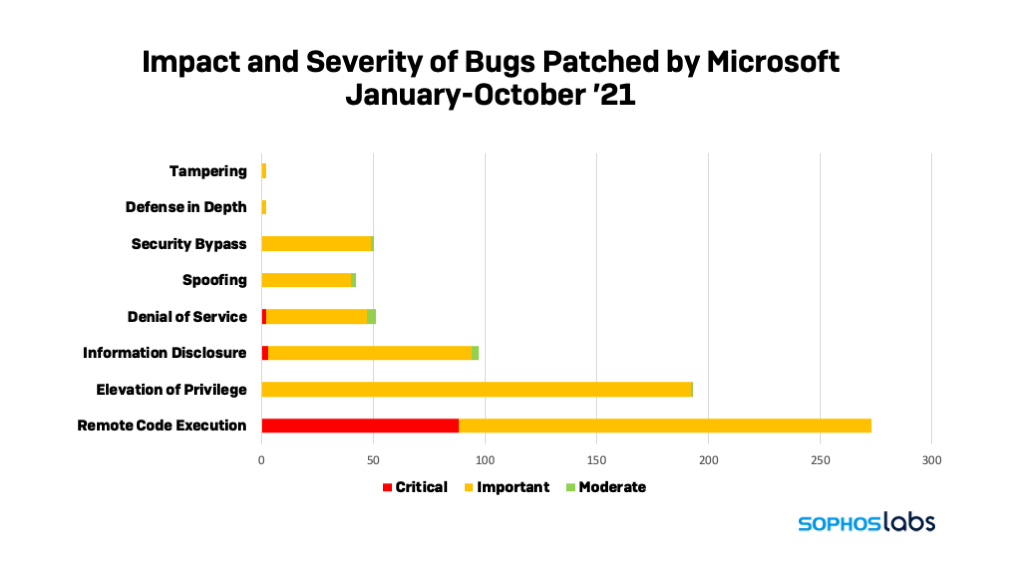
Today Microsoft released its latest round of security fixes, addressing 74 vulnerabilities in Microsoft products. Of these, Microsoft’s Security Response Center has classified only two as “critical”—both of which could allow remote code execution in Windows’ Hyper-V virtual machine hypervisor. But all but two of the remainder are classified as “important”, and one is already being exploited by attackers.
[UPDATE 16:30 EDT: Microsoft also released patches for a new remote code execution vulnerability in Exchange Server (CVE-2021-26427), a vulnerability contributed by the National Security Agency. The exploit requires access from the same local network as the Exchange Server, or from an administrative VPN or MPLS connection. Still, this is an urgent fix.]
While many of these require local access to be exploited, there are several that can be exploited across the Internet. One of them is another Print Spooler vulnerability that Microsoft considers particularly exploitable.
Most likely to be hacked
There are 10 vulnerabilities listed in this batch of fixes Microsoft believes will be exploited if left unpatched. Three of them are elevation of privilege bugs in the Win32k subsystem of Windows’ graphics device interface (gdi.exe), a component that we’ve seen numerous bug fixes for in the past. They are the already-exploited vulnerability CVE-2021-40449, and the yet-to-be-exploited CVE-2021-40450 and CVE-2021-41357.
Also among the bugs with the highest likelihood of exploitation are additional elevation of privilege vulnerabilities in yet another graphics-related component, the DirectX Graphics kernel driver (CVE-2021-40470), and in the Windows Common Log File System Driver (CVE-2021-40443, CVE-2021-40466, and CVE-2021-40467). All of these need to be exploited locally to work—either with hands-on-keyboard, an SSH connection, or via user interaction to launch them.
Additionally, there are two new remote code execution bugs with high likelihood of exploitation in Microsoft SharePoint (CVE-2021-40487 and CVE-2021-41344). While there’s no working example of an exploit of these vulnerabilities (which may be why the bug fixes are rated as “important” and not “critical”), an attacker could leverage them, without any credentials from anywhere on the Internet, if exploited
Finally, there’s a new spoofing bug in Windows’ Print Spooler (CVE-2021-36970). This isn’t as potentially threatening as the “Print Nightmare” bug from a few months ago, but it can be exploited across the Internet and could potentially be used to gain access to all the data in the print spool, or as part of a denial of service attack against print services. A proof-of-concept exploit of this vulnerability has been verified, so there’s a high likelihood that the bug will be exploited in the near future. There’s also a remotely-exploitable information disclosure bug patched this month in Print Spooler (CVE-2021-41332), but that is less likely to be exploited, according to Microsoft.
Critical hits
As mentioned earlier, the sole two vulnerabilities for October’s Patch Tuesday classified as critical are related to Windows Hyper-V (CVE-2021-38672 and CVE-2021-40461) on Windows 11, Windows 10, and Windows Server (2004, 2019, and 2022).
There is no known exploit code for these vulnerabilities, so (for now) any attack would be just theoretical, limited to exploits through Hyper-V’s network stack from shared physical or logical network or via a secure administrative domain connected by a VPN or Multi-Protocol Label Switching (MPLS).
In order to operationalize an attack, the attacker would need to have a significant amount of knowledge about the targeted network and the vulnerable instance of Hyper-V. But, if successful, an exploit could give the attacker complete access to virtual machines running within the Hyper-V environment, or the ability to stage a machine-in-the-middle attack, altering network communications.
Sophos protection
Here is a list of protection released by SophosLabs in response to this advisory to complement any existing protection and generic exploit mitigation capabilities in our products.
| CVE | SAV |
| CVE-2021-40466 | Exp/2140466-A |
| CVE-2021-40467 | Exp/2140467-A |
| CVE-2021-40449 | Exp/2140449-A |

Leave a Reply