We all know a sysadmin or two (or three, or four) who are seriously into gaming, and have the cool hardware to prove it…
…perhaps including a special chair, dedicated headphones, an ultra-hackable mouse, and an indestructible, mechanically triggered, 6-key-rollover, touch-typist’s keyboard (with multicoloured blank keycaps, configured in COLEMAK format, rather than QWERTY or even DVORAK, natch).
But what if you want to go the other way around?
What if you’re a gamer who wants to be a sysadmin? On someone else’s computer?
Well, apparently, until last week at least, gamer-centric mice and keyboards from popular vendor Razer could help you to do just that.
The problem, it seems, was a Helpful Feature that turned out also to be a bug, as noted on Twitter by a researcher going by @j0nh4t, or jonhat in full:
Need local admin and have physical access?
– Plug a Razer mouse (or the dongle)
– Windows Update will download and execute RazerInstaller as SYSTEM
– Abuse elevated Explorer to open Powershell with Shift+Right clickTried contacting @Razer, but no answers. So here's a freebie pic.twitter.com/xDkl87RCmz
— ҉j҉o҉n҉h҉a҉t҉ (@j0nh4t) August 21, 2021
At first viewing, the video above might seem a bit overwhelming, if not actually confusing, but the bug goes something like this:
- You plug in a Razer gaming mouse for the first time.
- Windows detects that this device type has special software and drivers that will make it work Even Better than a regular mouse.
- Windows finds Razer’s official addons in the Windows Update cloud.
- Windows downloads and launches the official addons so you don’t have to.
- The Razer app helpfully ends with a clickable directory name, showing you what ended up where in the installation process.
As risky as this sounds at first, you can argue that it’s better than leaving you to your own devices, literally and figuratively, as early versions of Windows did, casting around on the internet for a download that looks like a driver that might work…
…and then downloading it from a site that might be the real one, or might not…
…and then running it with Admin powers yourself, only to find it’s the wrong driver, and your device now doesn’t work at all, and that you can’t figure out how to revert the installation…
…and then wondering why your computer is slowing to a crawl and uploading hundreds of megabytes of data to a weirdly named server in [REDACTED] while at the same time sending thousands of weird emails to people throughout [REDACTED].
With that in mind, automatically getting and running an official copy of the official drivers and app from an official Microsoft server sounds not only much more more convenient but also much less likely to end badly.
When a feature turns into a bug
The problem in this case is the point at which Razer’s app helpfully displays the name of the software installation directory at the end, even though it doesn’t need to.
That’s an active link in Razer’s app, so you can right-click on it and view the directory in File Explorer.
Then, once you’re in Explorer, you can do a Shift-and-right-click and use the handy option Open PowerShell window here, giving you a command-line alternative to the existing Explorer window.
But that PowerShell prompt was spawned from the Explorer process, which was spawned from Razer’s installer, which was spawned by the automatic device installer process in Windows itself…
…which was running under the all-powerful NT AUTHORITY\SYSTEM account, usually referred to as NTSYSTEM or just System for short.
So the PowerShell window is now running as System too, which means you have almost complete control over the files, memory, processes, devices, services, kernel drivers and configuration of the computer.
In other words, if you’re a penetration tester given access to unlocked company laptops to see how long it takes you to promote yourself to get Admin superpowers via a regular user’s account, and if you have a Razer mouse with you, the answer is probably, “Not very long”.
Technically, you don’t need to take a wired mouse with you – if you have a Razer wireless mouse, plugging in just the dongle ought to be enough, whether the mouse is present or not, because the dongle is what interacts with the USB subsystem on Windows and identifies the device.
And if you have a hacker-friendly tool such as a Raspberry Pi Zero, which has two-way USB hardware configurability, you can either set it up as a USB host and plug other devices into it, or you can set it up as a USB device and plug it into other computers.
When you pretend via software to be a USB device such as a mouse or a keyboard (Razer makes keyboards, too, that come with added drivers to make them perform Even Better for avid gamers), you can pretend you are almost any sort of device made by almost any known vendor.
We tried tricking Windows 11 into thinking our Pi Zero was a Razer keyboard, a subterfuge that Windows accepted, happily taking fake keystrokes from our bogus device. However, we ran out of time to create a configuration with enough verisimilitude to convince Windows that it needed to fetch additional drivers to support the device fully. We assume that with more time, knowledge, or both, it could be done easily.
What to do?
If you’re a home user who’s an Admin on your own computer already, you don’t have anything to worry about.
For self-admins, the Elevation of Privilege (EoP) trick described here is just an expensive and roundabout way of using the regular “Run as administrator” Windows option that would give you a PowerShell or an command prompt with superpowers anyway.
But if you are looking after a computer for another family member who doesn’t have Admin powers, or you are running a corporate network where users aren’t supposed to fiddle with the underlying operating systems on their laptops, you probably want a way to stop this sort of trick.
To lock down an individual computer (we tested this on both Windows 10 and Windows 11), go to Settings > System > About, and click on the Advanced system settings option:
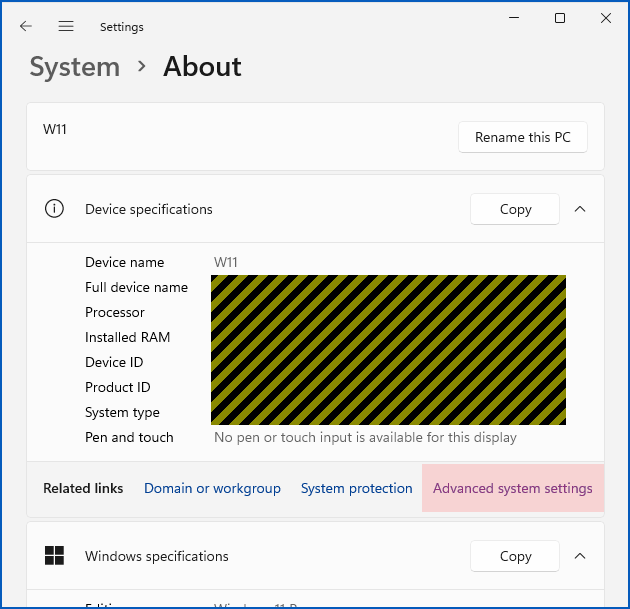
This should bring up the System Properties window:
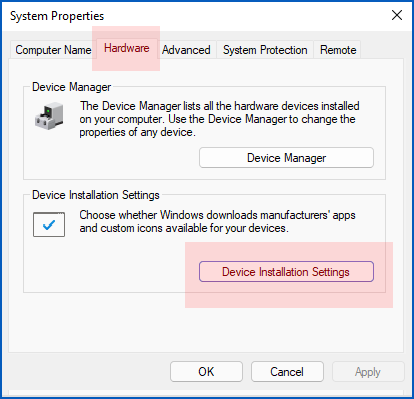
Click on Hardware > Device Installation Settings and choose No for the setting Do you want to automatically download manufacturers’ apps and custom icons available for your devices?
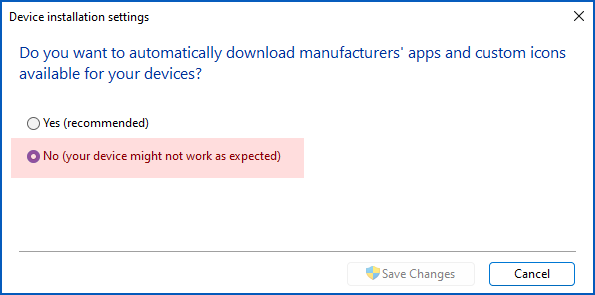
Without additional drivers, many new devices will work anyway (albeit without added features such as extra buttons on a gaming mouse, or special zoom-and-pan features on a webcam); others, however, may not work at all if Windows doesn’t already have a generic driver that supports the core functionality of the device.
To get the device to work fully, the user will need to ask a designated Admin to enable the installation of the new drivers and software for them.
Further information
On a corporate network, you may also want to look at taking broader control over who’s allowed to add what sort of device, and where.
For Windows networks in general, you might want to review Microsoft’s own advice for regulating device installation with Group Policy.
If you are a Sophos customer, please take a look at Sophos Central Peripheral Control, for additional security and control.

Haemish Edgerton
I’m sorry, but this is SO STUPID of Microsoft. It’s one thing to automatically download and install basic hardware drivers that have previously been assessed and “blessed” by Microsoft… but to have the OS automatically trigger the install of 3rd-party SOFTWARE utility packages for that hardware? No, that’s just dumb.
Basic, approved driver functionality is *enough* for auto-install. Let the user download and run any extra tools software themselves after that.
Paul Ducklin
I see where you are coming from there, but if you have a device that really needs a driver/app kernel/userland software bundle to work well, then everyone is going to want or need those “extra tools” you speak of anyway… so you can still argue that providing them from a well-managed source is better than serving up the drivers in a trusted download and them requiring/risking people to match them up with the right software app later on.
Perhaps an option to “require Admin password when bundled driver/app tools are installed automatically” would be an option? That would at least help to close the door on EoP holes of this sort.
Haemish Edgerton
My issue is that Microsoft is placing a *lot of trust* in the 3rd-party software install… while running as SYSTEM. Trust that can easily be misplaced, as it shows here for Razer, or possibly even intentionally abused by a small-scale hardware vendor if they manage to hide their true intent with their associated software tools that “look” innocent.
IMO, the best option they could have done is automatically install basic (and verified) driver functionality only… and then present the user with a separate link to download the additional utility software, in a system alert (i.e. “Toast”-style) message – that when clicked, downloads & runs that software under the *user’s* context, not SYSTEM… or yes, prompts for UAC elevation if Admin rights are necessary for the software.
Paul Ducklin
I think I agree, mostly, but apart from the extra step getting of a UAC prompt or an admin password (and see my comment above), the rest of what you describe is mostly just “security hassle”, given that the end result is the same (with the exception that the link won’t go to a site that’s as secure as Microsoft’s).
The problem with making the basic driver installation frictionless but requiring the user to mess about fetching the rest of the stuff and then running it anyway (assuming it needs NTSYSTEM, which I’ll assume it will) is that it’s actually *less* likely that a full and correct install will take place, and so users will end up with a device that mostly works, after which they are on their own again, searching the web for the extra stuff they need, and we’re back to the Old Days described above.
You have to give all the same approvals as in your system, but the potential for additional trouble (e.g. wrong link, hacked server, mismatched kernel and userland parts) is removed.
Haemish Edgerton
I should add… there is a Group Policy control to manage this:
Computer Configuration > Administrative Templates > System > Device Installation > Prevent device metadata retrieval from the Internet
…set to Enabled.
Per the GPME Help Text:
If you enable this policy setting, Windows does not retrieve device metadata for installed devices from the Internet. This policy setting overrides the setting in the Device Installation Settings dialog box (Control Panel > System and Security > System > Advanced System Settings > Hardware tab).
Paul Ducklin
I saw that one… can you confirm that this really does prevent any installers from autorunning? The name of this option is a bit vague. You’d assume that if Windows can’t fetch “device metadata” then that would preclude the OS from knowing which drivers to download… but is “downloading a needed driver” really a subset of “downloading metadata”?
I was going to add this to the article but it doesn’t explitly say, “To turn off autoinstallation of drivers for new devices, use this option.” (Indeed, the wording here implies that you can have an “installed device”, which to me means it’s got all the driver support it needs to work properly, and yet ask not to have “metadata”, whatever that might be, downloaded to go with it. To me, once a device is installed, you’re already past “the right drivers are now present” stage and the “metadata” is another layer on top of that…
Haemish Edgerton
I can confirm (tested personally on multiple computers) that the GPO setting I listed above locks down the Device installation settings dialog box as shown in your screenshot (i.e. “No (your device might not work as expected)”), only it is also grayed out so that end users cannot subsequently change it.
Yes, like you I interpret the metadata as “extra” on top of the basic drivers – with an unhealthy amount of trust going to the source of that metadata (the hardware manufacturer) to provide a safe installer that is not easily exploited.
The underlying registry setting that the GPO sets (when Enabled) is:
Key: Computer\HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\Device Metadata
Value Type: DWORD (32-bit) Value
Value: PreventDeviceMetadataFromNetwork, set to 0x00000001 (1)
It’s easy to set this locally for quick testing with Local Group Policy (i.e. gpedit.msc), or you can even just set the above registry value manually, then (re-)load the Device Installation Settings dialog box to verify the result. Of course in a domain-joined environment, you’d want to use domain Group Policy instead for mass deployment.
Haemish Edgerton
Incidentally, the “Microsoft’s own advice for regulating device installation with Group Policy” link you provided at the end of the article does not include or mention the above control!
Kyle
This problem is easily solved by asking for an admin password before auto-installing drivers known to be from 3rd-parties. That way the attacker would need your password for this to work, making the attack useless outside of social engineering contexts.
You can’t account for all possible attacks, but you can start with a solid foundation. Blindly sending driver downloads to 3rd-parties without the user’s knowing, simply because Microsoft trusts people with money, is reckless.
The Driver
So I walk into a Big Box Retailer with a dongle (or get one of the shelf next to the laptops) and get admin on all the display models out. Change the system settings to play extremely annoying sound using the “at” command. The sit back an watch the fun :)
Paul Ducklin
Just to be clear to anyone who is thinking of doing just that: it’s illegal. At least, it’s *probably* illegal in many jurisdictions. Deliberately exploiting a bug to bypass a protection that would otherwise obviously be there, and where you clearly have no reasonable excuse for doing so, is not going to be considered “authorised access” by any sensible magistrate or judge. You can get five years for that sort of crime in England, which makes it a non-trivial offence to be charged with, even if the nature of your own infringement is on the mild end of the scale.
The store might not call the cops or otherwise seek to dump you in trouble, but that depends on their sense of humour. Given that “hacking” is often seen as something extra-super-duper dangerous that deserves a sharp response, even if little apparent harm was done in the “hack”, and given that sales managers (hmmmmm, how can I put this?) aren’t always the most laid-back or forgiving people in the world if you vandalise their turf…
…don’t do it. (Plus it’s not a hack if everyone knows how to it :-)