The State of Ransomware 2021 report provides fresh new insights into the frequency and impact of ransomware.
Based on findings from an independent survey of 5,400 IT managers in mid-sized organizations in 30 countries across the globe, it reveals that 37% of organizations experienced a ransomware attack in the last 12 months – down from 51% in 2020.
Furthermore, fewer organizations suffered data encryption as the result of a significant attack – down from 73% in 2020 to 54% in 2021. So far, so good.
However while the number of organizations being hit by ransomware has dropped since last year, the financial impact of an attack has more than doubled, increasing from US$761,106 in 2020 to US$1.85 million in 2021. This is likely due, in part, to the move by attackers to more advanced and complex targeted attacks that are harder to recover from.
Paying up doesn’t pay off
The number of organizations paying the ransom to get their data back increased over the last year, from 26% of organizations whose data was encrypted in 2020 to 32% in 2021.
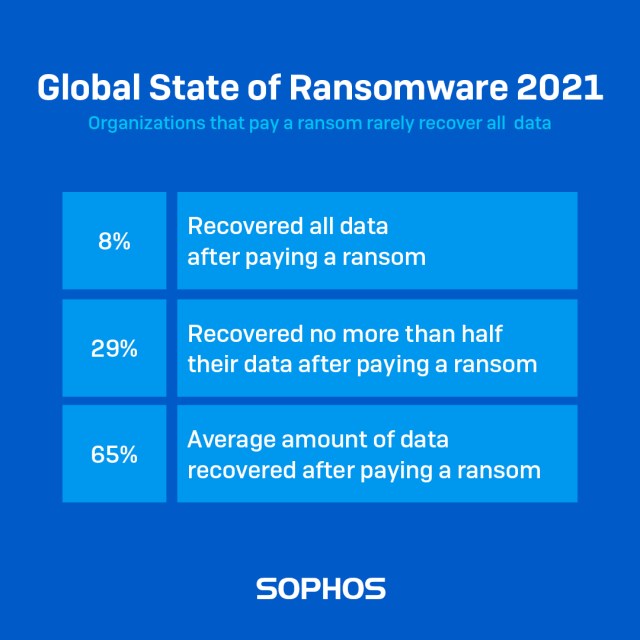
However what adversaries fail to mention in their ransom notes is that your likelihood of getting all your data back after paying up is very slim: fewer than one in ten (8%) got back all their encrypted files.
In fact, on average, organizations that paid the ransom got back only 65% of their data, with 29% getting back no more than half their data. When it comes to ransomware, it doesn’t pay to pay.
The survey also revealed that extortion without encryption is on the rise. 7% of respondents that were hit by ransomware said that their data was not encrypted, but they were held to ransom anyway, possibly because the attackers had managed to steal their information. In 2020, this figure was just 3%.
Winners and losers
The report provides insight into how different countries and sectors have been affected by ransomware over the last year, including:
- India reported the most ransomware attacks with 68% of respondents saying that they were hit last year. Conversely Poland (13%) and Japan (15%) reported the lowest levels of attack.
- Geographical neighbors Austria and the Czech Republic are poles apart when it comes to ransomware recovery costs: Austrian respondents reported the highest recovery cost of all countries surveyed while Czech respondents reported the lowest.
- Retail and education (both 44%) were the sectors that reported the highest levels of attack.
- Local government is the sector most likely to have their data encrypted in a ransomware attack (69%).
Get the full survey findings
Read the State of Ransomware 2021 to get the full findings from the survey. It includes best practice advice from Sophos defenders to help you stay safe from ransomware.
The State of Ransomware 2021 survey was conducted by Vanson Bourne, an independent specialist in market research, in January and February 2021. The survey interviewed 5,400 IT decision makers in 30 countries, in the US, Canada, Brazil, Chile, Colombia, Mexico, Austria, France, Germany, the UK, Italy, the Netherlands, Belgium, Spain, Sweden, Switzerland, Poland, the Czech Republic, Turkey, Israel, UAE, Saudi Arabia, India, Nigeria, South Africa, Australia, Japan, Singapore, Malaysia, and the Philippines. All respondents were from organizations with between 100 and 5,000 employees.
Sophos Intercept X protects users by detecting the actions and behaviors of ransomware and other attacks.

ULF MATTSSON
Is a robust data backup and/or DR plan in addition to strong, multi-layer defense posture appropriate? Should data be protected? Would this be inline with GDPR and CCPA?
Sally Adam
We recommend the use of backups to help restore data if needed, as well as a strong multi-layer defense that includes human-led threat hunting to minimize the risk of adversaries accessing your data.
A simple memory aid for backups is “3-2-1.” You should have at least three different copies (the one you are using now plus two or more spares), using at least two different backup systems (in case one should let you down), and with at least one copy stored offline and preferably offsite (where adversaries can’t tamper with it during an attack).