Good news, everybody!
Two weeks ago, we wrote that the well-known and widely-used domain perl.com had been taken over by persons unknown.
Perl, now more than 30 years young, is amongst the most popular and prevalent programming languages out there, and websites that serve the world of Perl are therefore popular, too.
So, even though the official home of the language itself is perl.org, the perl.com website has been a well-known companion in the Perl community for many years.
You can imagine why, if the original owner had allowed their registration of the domain to lapse, either by mistake or because they felt they no longer needed it, a new owner might be keen to snap it up.
(Indeed, four-letter dot-COM domains are rare and expensive these days if they don’t spell out a well-known word, and even if they can’t be pronounced as a word at all.)
In this case, however, the domain’s takeover was as unlikely as it was unexpected.
That’s because perl.com had been registered for years to widely respected US-based Perl guru Tom Christiansen, and it hadn’t expired.
So it was difficult to figure out how any domain registrar would have been inclined to believe that Christiansen, or tchrist as he is widely known, would voluntarily have relinquished the domain…
…especially to someone who immediately redirected the domain to pretty much nothing at all:
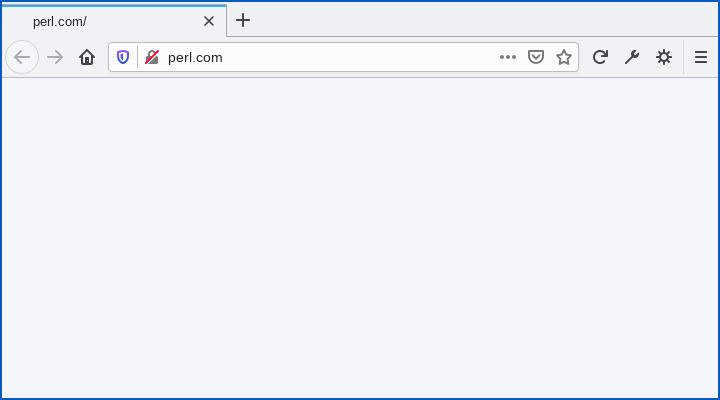
Yet that is what happened at the end of January 2021, when the domain registration suddenly switched to a privacy-protected registrant based in Moldova:
[WHOIS data for PERL.COM, retrieved 2021-01-29] Domain Name: perl.com Registry Domain ID: 432086_DOMAIN_COM-VRSN Registrar WHOIS Server: whois.rrpproxy.net Registrar URL: http://www.key-systems.net Updated Date: 2021-01-27T12:43:15Z Creation Date: 1994-08-16T04:00:00Z Registrar Registration Expiration Date: 2031-01-26T15:26:42Z Registrar: Key-Systems GmbH [...] Registry Registrant ID: REDACTED FOR PRIVACY Registrant Name: REDACTED FOR PRIVACY Registrant Organization: REDACTED FOR PRIVACY [...] Registrant City: REDACTED FOR PRIVACY Registrant State/Province: Chisinau Registrant Postal Code: REDACTED FOR PRIVACY Registrant Country: MD [Moldova] [...] Admin Name: REDACTED FOR PRIVACY Admin Organization: REDACTED FOR PRIVACY [...]] Admin City: REDACTED FOR PRIVACY Admin State/Province: REDACTED FOR PRIVACY Admin Postal Code: REDACTED FOR PRIVACY Admin Country: REDACTED FOR PRIVACY
For a short while after the domain takeover, according to reporters at IT news site The Register, domain name reseller Afternic was offering the suddenly blanked-out perl.com domain for sale for the impressive sum of $190,000.
(By the time we looked, on the day after The Register published its report, the domain was still out of tchrist‘s control but no longer up for sale on any publicly visibly domain broker’s site we could find.)
The good news
We don’t know exactly how this takeover was achieved, and what collateral was used to convince the relevant domain registrars to authorise the transfer, but we are pleased to report that normal service has been resumed.
The perl.com domain is now back under tchrist‘s control, and the registration details are no longer hidden behind a privacy shield, so you can check them out for yourself:
[WHOIS data for PERL.COM, retrieved 2021-02-07] Domain Name: PERL.COM Registry Domain ID: Registrar WHOIS Server: whois.networksolutions.com Registrar URL: http://networksolutions.com Updated Date: 2021-02-05T19:59:16Z Creation Date: 1994-08-16T04:00:00Z Registrar Registration Expiration Date: 2031-02-05T16:54:08Z Registrar: Network Solutions, LLC [...] Registry Registrant ID: Registrant Name: Tom Christiansen Perl Consultancy Registrant Organization: Tom Christiansen Perl Consultancy [...] Registrant City: BOULDER Registrant State/Province: CO Registrant Postal Code: 80304-1022 Registrant Country: US [...] Admin Name: Tom Christiansen Perl Consultancy Admin Organization: Tom Christiansen Perl Consultancy [...] Admin City: BOULDER Admin State/Province: CO Admin Postal Code: 80304-1022 Admin Country: US
And, of course, the site is back to normal:
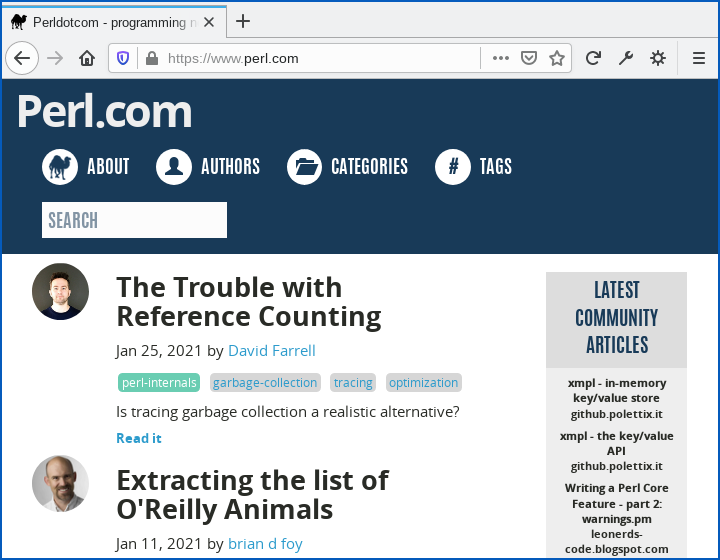
During the domain takeover, the perl.org site leapt to the rescue by serving the content of perl.com via perldotcom.perl.org (try reading that sentence out aloud quickly!), and that “emergency” URL still works, but it is once again safe to visit perl.com directly.
Result!

John
The bad news: “We don’t know exactly how this takeover was achieved, and what collateral was used to convince the relevant domain registrars to authorise the transfer”, so it is impossible to tell how to prevent this type of domain stealing.
Paul Ducklin
Ahhh, watch this space! *We* (meaning me in this case :-) don’t know because it wasn’t our domain name, and we don’t want to guess how this happened in case we point our finger in the wrong direction.
But we are hoping to bring you a special episode of the Naked Security Podcast soon in which we will be talking to the person who co-ordinated the “fetchback” (is that the inverse of a takeover?) in this particular case, so we can not only give a real-world example of how this sort of thing happens, but also explain how to react if it does.
Ed
Thanks for clarifying the “we” Paul! I too was interested if this domain take over was a practice event for other well known sites — that wouldn’t necessarily completely redirect to a blank page, rather an expected page w/malicious code added in. Does the podcast & this blog share topics? I don’t follow the podcast (who has time to listen!?), but would jump over to the podcast in the event the aftermath on this topic isn’t covered here.
Thanks!
Ed
Paul Ducklin
I don’t know the details of how the Perlers lost and regained the domain and I don’t want to guess so I am waiting until they have finished their fact-finding and write-up stages.
Having said that, the answer to “what could crooks do with a domain like this” is pretty much “whatever they liked”, e.g. shut it down and sell it on, host malware under a trusted banner, use it for trapping traffic and harvesting visitor data (including passwords) for a while, or any combination of those.
I was surprised at the blank page site that took its place – sites up for sale usually redirect to a “make an offer” or “this is the price” page. Why that didn’t happen here is something I can only guess at so far. The fact that the domain was up for sale so briefly suggests that the prompt reaction of the Perlers trying to get the domain back may have helped.
But we (which includes me!) had better wait to hear a real answer..
FWIW the minipodcasts we do are generally about 20 mins long so they only take 10 mins if you listen at 2x speed, which any decent podcast player will support. We usually, but not always, cover topics that we have already handled in a written article, so they are meant to be an additional and alternative source of info on various topics, not a replacement for written articles.
HtH
John Lord
Not knowing how it was done is very worrisome. Suppose someone managed the same trick and took over Google.com? Yikes!
Paul Ducklin
I think we can all guess at four or five ways this kind of thing could happen, e.g. phished password, turncoat colleague, corrupt registrar, lucky guess, software vulnerability, SIM swap, at gunpoint, expiration mistake, forged ID documents… OK, that’s nine ways already!
Let’s wait for the Perlers themselves to tell the story their way, as soon as they can do so without jeopardising any followup activities, e.g. with law enforcement…
…after all, they did admit to the problem right away, take steps to limit the damage, come up with a workaround and get busy fixing the issue, which they managed to do pretty quickly
David Pottage
My guess would be a SIM swap or forged ID.
Also as a perl contributor, I have an @cpan.org email address that has been getting a lot of spam for the past few months, with a higher than average number of phishing emails telling me that there are security issues with my domain or website.
I would think that it is unlikely that Tom Christiansen fell for a phish and leaked his email password, but perhaps he got a real notification from his domain registrar alerting him to a pending transfer, and he ignored it because he assumed that it was spam.
Paul Ducklin
After a bit of umming-and-ahhhing about this comment, I decided to let you speculate :-) But we’re going to wait until we can bring you a report from the camel’s mouth…
Stephen
I’m glad to hear you are hoping to do a follow up to this. However, I would request that you provide some written content as well – I never listen to the podcasts as it is just impractical for me, but I read most of the typed content you produce.
Ralph Hartwell
I agree; I find it MUCH easier to read the information rather than listen to it. Even listening at double speed is too slow for me. I read swiftly, and can easily read a ten minute script in just a minute or two. And if I like, I can print out the article, but I can’t easily do that with a podcast. Also, I find that I retain the information much better if I read the materiel rather than listen to it. But the podcasts are excellent. Thanks for continuing to bring us the latest and greatest security information.
Stay safe.