As two people for whom creating phishing emails constitutes legitimate employment (we are on the product team behind the Sophos Phish Threat phishing simulation service) we know we’re in the minority.
Like our not-so-lawful counterparts, we spend our days using social engineering techniques to trick people into opening malicious messages and clicking on links they ought to leave alone.
Understanding the attackers’ approach helps you spot a phishing email when it hits your inbox.
Having written and tracked the performance of hundreds of simulated phishing emails, we’d like to share our approach so you can raise the red flag quickly.
In general, there are four main steps phishers go through when creating convincing phishing emails, and understanding these steps helps you to spot and stop them.
Step 1: Pick your target
Different people fall for different tricks, so the more information you have about your target the easier it is to craft a convincing phishing lure.
The audience may be broad, for example users of a particular bank or people who need to do a tax return, or it may be very specific – such as a particular role within an organization or even a specific individual.
Either way, we – like our adversaries – always have an audience in mind for each attack.
Step 2: Choose emotional triggers (select your bait)
Attackers play on our emotions in order to get us to fall for their scams. Here are three emotional triggers that phishers commonly exploit to trap you – sometimes using them in combination to boost their chance of success:
- Curiosity. Humans are naturally inquisitive and phishers abuse this by making you want to know more. “Do you want to know what happened next?” All you need to do is to click the link or open the attachment…

- Hope. The abuse of hope by phishers can range from general messages about unexpected prize wins and dating opportunities to specific emails referring to job offers, pay increases and more.

- Necessity. Phishers often use a cybersecurity lure – pretending that you’ve suffered a security breach – to make it sounds as though you simply must act now.
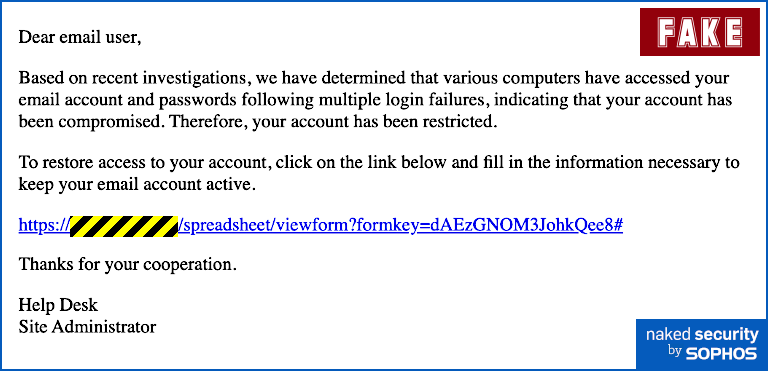
Step 3: Build the email (bait the hook)
Next up, we need to build the email. Like our criminal counterparts, we will often attempt to cloud your judgement by using one or more of the the emotional triggers we listed above to get you to perform a specific action without thinking about it first.
That action may be as simple as clicking a link or as complicated as initiating a wire transfer.
One clever trick to writing an effective phishing email is to make the action you wish the target to take inevitable, but not necessarily obvious.
For example, an attacker might send you an email that appears to contain clickable links to weight loss products. At the bottom of that same email, the attacker also includes a clickable “unsubscribe” link. Here’s the catch though: clicking on the “unsubscribe” link takes you the exact same place as clicking any other link in the email.
This way, the attacker presents you with the illusion of a choice while ensuring they get you to click the link they wanted, regardless of where in the email you do it.
Step 4: Send the email (cast the line)
Finally, the phishing email needs to be delivered to the targets. There are a variety of ways for an attacker to do this. They may simply create a new email account on a generic service like Gmail and send the message using that email address, or they could be a bit trickier about it.
Attackers sometimes purchase unregistered domain names that look similar to a legitimate domain, changing the spelling slightly in a way that isn’t obvious, such as writing c0mpany for company (letter O changed to digit zero) or vvebsite for website (two adjacent Vs used for a W).
They will then send the phishing email using this lookalike domain in the hope that users who are in a hurry won’t spot the subtle difference.
It’s also possible for attackers to compromise an email account that belongs to a legitimate source and use it to send a scam message. This is commonly referred to as Business Email Compromise (BEC), and means that even the email address of a co-worker could potentially be used by an attacker to phish you.
How to stop phishing attacks
Even if a phishing email does reach your inbox, it still requires you to take some specific action – clicking a link or opening an attachment – befores it succeeds.
So, knowing what to look out for, and what to do if you see something suspicious, has a huge impact.
Here are some steps to help reduce your phishing risk. While they are mostly written with organizations in mind, many are also equally relevant in our personal lives:
- Educate through safe exposure. In the workplace, periodically exposing users to simulated phishing attacks offers them an opportunity to interact with a realistic but harmless version of what could have been a real attack. This allows people to make mistakes and learn from them while the stakes are low, thus preparing them to handle real threats when the stakes are high. Variety is important here and we strongly recommend the messages vary in detail such as length, topic, tone, style and the time they were sent.
- Analyze your security culture. If you run phishing simulations in your workplace, collect as much data as you can, including how many samples of each message were opened, whether the recipient clicked on a link or opened an attachment, and what kind of device they were using at the time (computer or mobile). This will give you a powerful picture of overall employee awareness and where you might be particularly vulnerable to real attacks. Armed with this data you can focus your resources on supporting the areas and employees at greatest risk.
- Target your training efforts. Direct your training efforts to departments that are at the greatest risk. Staff in finance, IT and management, and those with access to customer records, are high-value targets for attackers. Don’t overlook the basics, such as reminding staff to question why an email is asking them to do something, who the email is from, and so on. Distracted, tired and busy employees can easily be caught out.
- Provide clear guidance on how to respond. Make sure not only that your staff know how to report potential phishing emails, but also that they receive a timely response when they do. Remember, if one person in your organization has received a phish there is a high chance that others have too. The earlier you can investigate and act, the better.
- Enable cultural change. Fostering a company-wide culture of awareness and support is one of the most important things you can do. Give employees the opportunity to fail safely and offer them a clear route for reporting suspicious emails. Recognize and reward people who report phishing emails (praise is important) and support employees who inadvertently fall for a scam.
Remember, the goal of phishing training is to make people more aware of potential threats, and more likely to report them.
Be supportive and understanding if you test someone and they do fall for your trick and do click through, and make it clear you are not trying to catch people out in order to get them into trouble.
One more suggestion
Sophos Phish Threat, the product we work on, makes it easy for you to run simulated phishing programs, measure results, and target training where it’s needed. You can try it for free for 30 days.


Anonymous
Sounds like fish to me
Graeme Jorgensen
Thank you for another very informative article, and concerning a topic which is a daily threat. While it’s frustrating that the best email anti-SPAM programmes don’t seem able to provide protection, it’s easy to understand why this task is so difficult.
This highlights why your articles are so valuable to everyone, whether private or in business. Awareness is at least the very first step in combating this plague.
Please keep up the great work.
Paul Ducklin
Thanks for your kind words – we appreciate them!
Steve
Thanks for this article. Good solid advice here.
I would suggest one more bit of guidance: Make sure your employees are never discouraged by sending you potential phishing messages. Only if they feel safe organizationally to send possible false positives will you catch the real positives. So thank them for the alert even if it proves to be safe.
Paul Ducklin
Yes. As we like to say in the Naked Security Podcast (by which I mean I have got away with using this saying a couple of times already :-), wen it comes to IT support for cybersecurity submissions from your users, you need to adopt the mindset that “there are no stupid questions, only stupid answers.”
Smile Kit
Tested and proven in a nascent financial services firm. Great product!
Keep up the good work, Sophos.
0Laf
Oh some of those are evil, I’ll pinch the lost puppy idea thank you very much.
In my own testing I found that the simpler the message the better, also appealing to peoples’ greed. So a plain text email from ‘IT’ to say they had an oversupply of monitors, go to this form to register your interest, first come first served.
I nailed a lot of people with that one.
But the puppy picture, that’s genius!
Paul Ducklin
Then you’ll lovehave an interest in this article too, based on Phish Threat stats:
Phishing tricks – the Top Ten Treacheries of 2020
“Someone’s got a flat tyre in car park.” I don’t even have a car and haven’t for years (fixed gear cycling FTW) but *I’d* click that one :-)
john gizzi
i think you guys are awesome. When u say that we should collect info about how many test emails were sent out and how many were opened or clicked-on and by whom, do you have some way to collect this from the baited email itself or are we just relying on our tricked employees to voluntarily divulge their gullibility? Also, can viewing the source info of an opened suspicious message provide empoyees (or any concerned party really) clues to its legitimacy? Thanks,
Paul Ducklin
Tools like Sophos Phish Threat will keep track of the “who/what/when” for you, to ensure that you can give your counselling where it’s needed.
And yes, viewing the source of the email, if you know what to look for, often provides many clues to phishiness that might not be visible in the email itself.
The headers, for example, reveal which servers the email passed through on the way, and where it originated, which is often good enough to tip you off that it’s a phony message.
Sometimes, you will notice weirdnesses in the HTML of an email that are included to split up words and phrases to throw email scanners off the scent, but which are invisible when the text is viewed in your browser. Examples include extra letters that are formatted via HTML tags so they are white-on-white or too tiny to read when displayed, or long and rambling “pseudoliterary” quotations stuffed into parts of the message that don’t get shown on screen but that dilute the dodginess of the message when it passes through a mail server.
Eddie
I would 100% click on that first example with the puppy. I should probably think before i click more often haha.
Paul Ducklin
Oh, help me find my puppy please,
He’s got me worried sick.
He’s such a fluffy little dog,
Click here to see a pic.